Posts
2431Following
590Followers
1309Heretek of Silent Signal
CFG Bot 🤖
cfgbot@mastodon.socialProject: python/cpython https://github.com/python/cpython
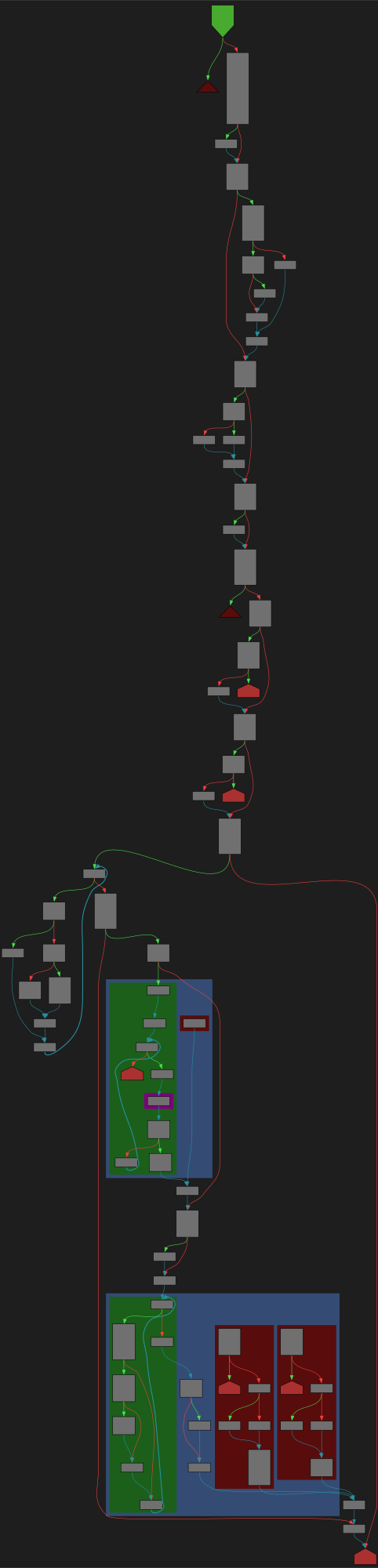
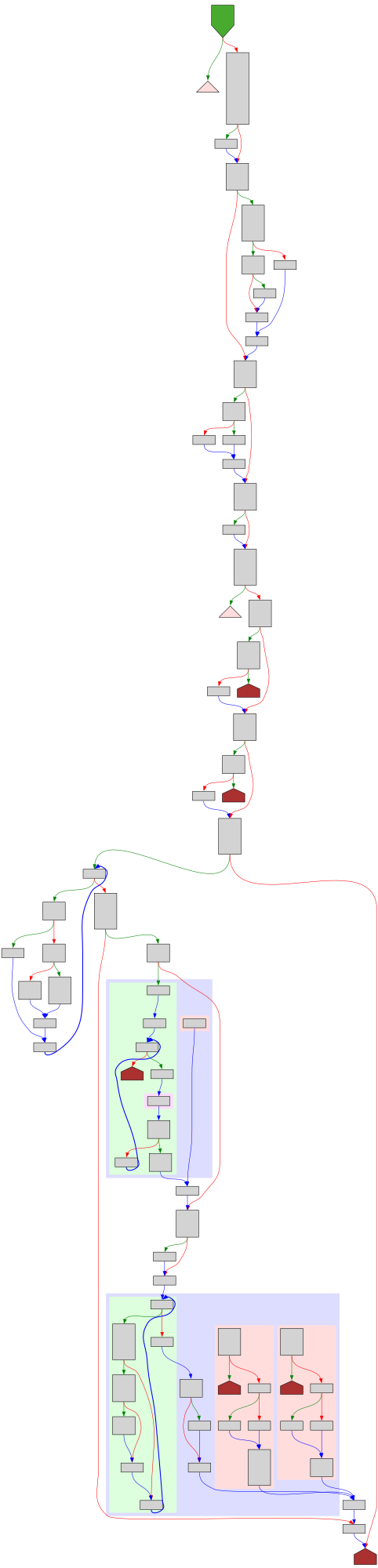
File: Lib/compileall.py:132 https://github.com/python/cpython/blob/2bd5a7ab0f4a1f65ab8043001bd6e8416c5079bd/Lib/compileall.py#L132
def compile_file(fullname, ddir=None, force=False, rx=None, quiet=0, legacy=False, optimize=-1, invalidation_mode=None, *, stripdir=None, prependdir=None, limit_sl_dest=None, hardlink_dupes=False):
SVG:
dark https://tmr232.github.io/function-graph-overview/render/?github=https%3A%2F%2Fgithub.com%2Fpython%2Fcpython%2Fblob%2F2bd5a7ab0f4a1f65ab8043001bd6e8416c5079bd%2FLib%2Fcompileall.py%23L132&colors=dark
light https://tmr232.github.io/function-graph-overview/render/?github=https%3A%2F%2Fgithub.com%2Fpython%2Fcpython%2Fblob%2F2bd5a7ab0f4a1f65ab8043001bd6e8416c5079bd%2FLib%2Fcompileall.py%23L132&colors=light
Not a Goat 🦝
screaminggoat@infosec.exchangeCISA: Closing the Software Understanding Gap
CISA, along with the Defense Advanced Research Projects Agency (DARPA), the Office of the Under Secretary of Defense for Research and Engineering (OUSD R&E), and the National Security Agency (NSA) published Closing the Software Understanding Gap (PDF) which urges the U.S. government to take decisive and coordinated action to close the software understanding gap. This gap arises from a disparity of technical investment where software production has outstripped investment in improving understanding for decades. By closing the software understanding gap, the United States will help mission owners and operators trust the system is functional, safe, and secure, and support confidence in national security and critical infrastructure systems.
#securitybestpractice #cisa #securebydesign #infosec #cybersecurity
/r/netsec
_r_netsec@infosec.exchangeMicrosoft Configuration Manager (ConfigMgr / SCCM) 2403 Unauthenticated SQL injections (CVE-2024-43468) https://www.synacktiv.com/advisories/microsoft-configuration-manager-configmgr-2403-unauthenticated-sql-injections
Joseph Cox
josephcox@infosec.exchangeNew: this OnlyFans model publishes her machine learning explainers to both YouTube and Pornhub. Although YouTube may get a million views, that'll generate around $300. The same content posted to Pornhub, with ~30k views, makes $1000. We spoke to her https://www.404media.co/why-this-onlyfans-model-posts-machine-learning-explainers-to-pornhub/
buherator
buheratorhttps://github.com/mainmatter/100-exercises-to-learn-rust/issues/245
(preferably with explanations about what the different lifetime annotations mean)
buherator
buheratorhttps://github.com/MrAle98/CVE-2024-49138-POC
Note: I did *not* verify this but it's at least not an obvious fake. Be careful!
/via @obivan
Raven
raven@bsd.cafelibvirt 11.0.0 released with VLAN support on standard Linux host bridges, support for VLAN tagging and trunking in the network, qemu and lxc drivers
Brad Spengler
spendergrsec@bird.makeupPeople finally caught on (sortof) to what I said 8 years ago ( ) that nobody knows what they're doing with the pointer hashing stuff, with %pK use for printks being the proof: https://lore.kernel.org/linux-hardening/Z4Z2TW_HaANvT4VH@smile.fi.intel.com/T/#t
Ange
Ange@mastodon.socialCurrently planned schedule for my next livestreams:
Friday 9 PM CET, the WAD (Doom's) archive.
https://www.youtube.com/live/g0VyFDYefqQ?si=Ta2p1zn0jSDCivhV
Saturday 9PM, JavaScript in PDFs.
Sunday, Doom in PDF!
CFG Bot 🤖
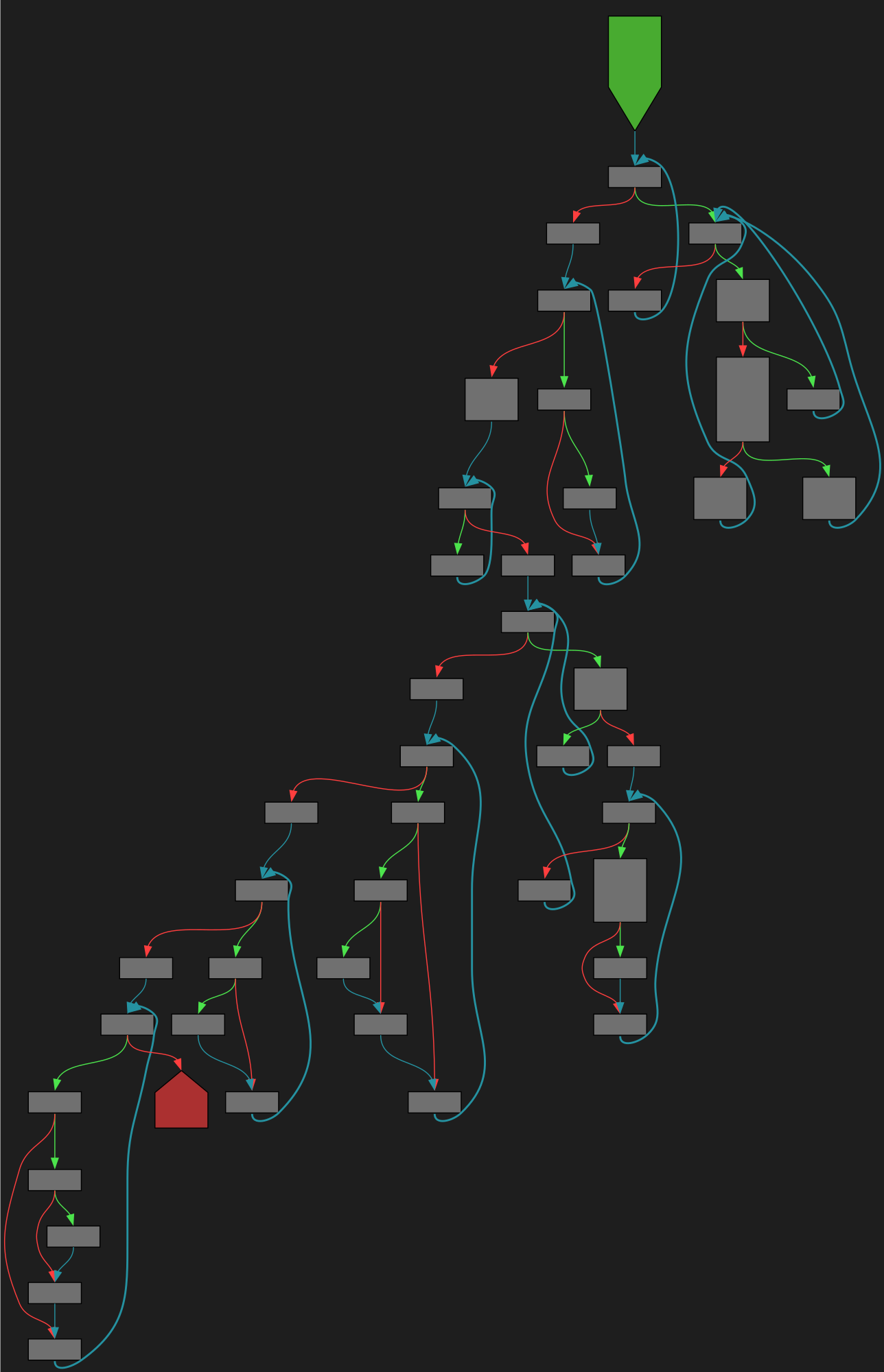
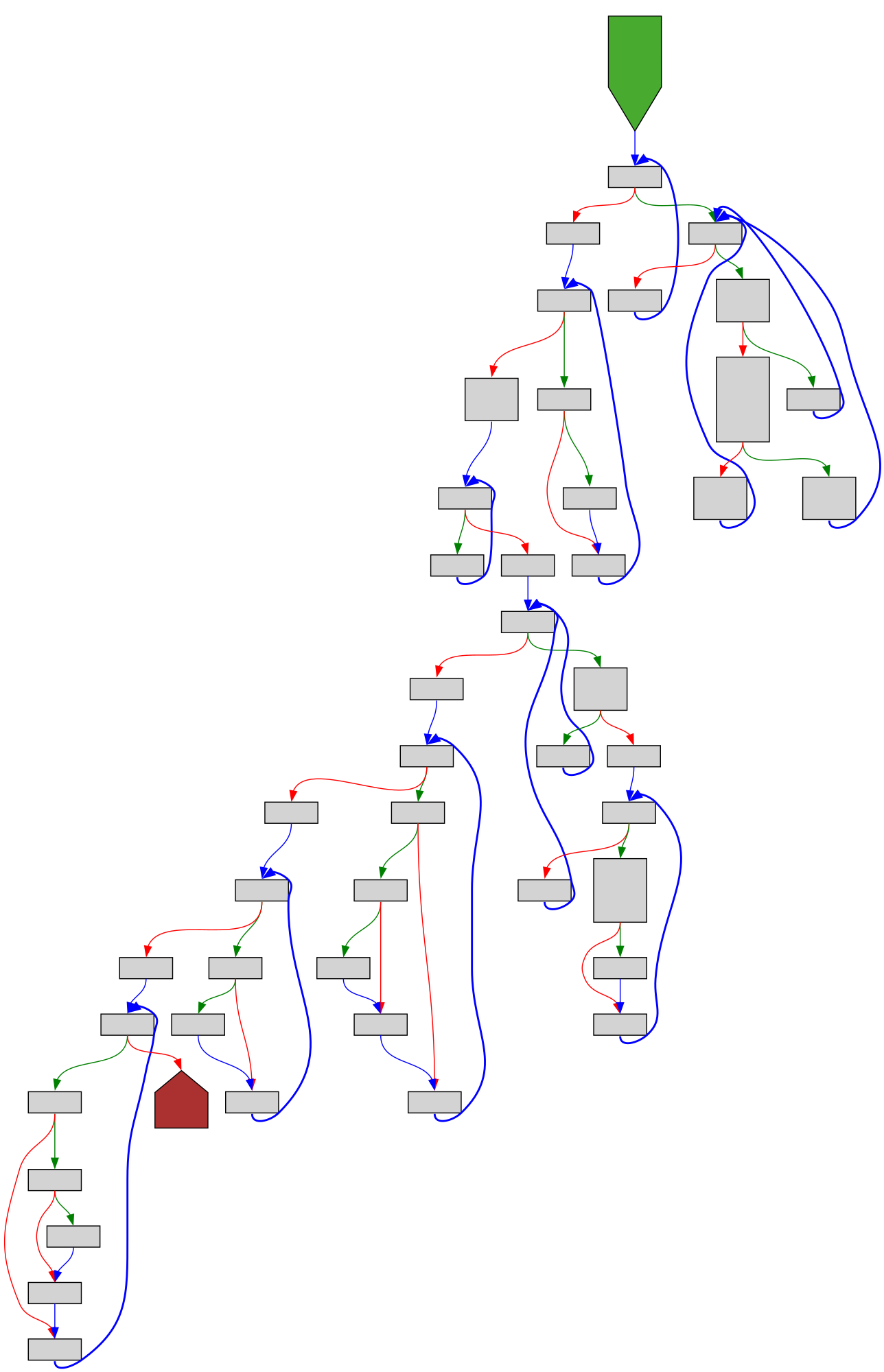
cfgbot@mastodon.socialProject: golang/go https://github.com/golang/go
File: src/cmd/cgo/godefs.go:18 https://github.com/golang/go/blob/refs/tags/go1.23.4/src/cmd/cgo/godefs.go#L18
func (p *Package) godefs(f *File, args []string) string
SVG:
dark https://tmr232.github.io/function-graph-overview/render/?github=https%3A%2F%2Fgithub.com%2Fgolang%2Fgo%2Fblob%2Frefs%2Ftags%2Fgo1.23.4%2Fsrc%2Fcmd%2Fcgo%2Fgodefs.go%23L18&colors=dark
light https://tmr232.github.io/function-graph-overview/render/?github=https%3A%2F%2Fgithub.com%2Fgolang%2Fgo%2Fblob%2Frefs%2Ftags%2Fgo1.23.4%2Fsrc%2Fcmd%2Fcgo%2Fgodefs.go%23L18&colors=light
Jason Scott
textfiles@mastodon.archive.orgAs you might imagine, recovering from rebuilding the Internet Archive systems from a new perspective took time, and the priority was super important systems, and ones merely "working" were left alone. But that's changed - we updated emulation at the Internet Archive so it's more secure, and the systems we're offering just added a few!
Does anyone use Sentry? Of course someone here uses it. Here's a sev:CRIT to allow user impersonation:
https://github.com/getsentry/sentry/security/advisories/GHSA-7pq6-v88g-wf3w
A critical vulnerability was discovered in the SAML SSO implementation of Sentry. It was reported to us via our private bug bounty program.
The vulnerability allows an attacker to take over any user account by using a malicious SAML Identity Provider and another organization on the same Sentry instance. The victim email address must be known in order to exploit this vulnerability.
offensivecon
offensive_con@bird.makeupTicket shop is live.
https://www.offensivecon.org/register.html
Jonathan Metzman
metzman@infosec.exchangeThe OSS-Fuzz team is hiring a PhD intern for this summer. Come join us and build something interesting that will have immediate impact on 1000+ open source projects. https://www.google.com/about/careers/applications/jobs/results/92969243305222854-research-intern-phd-summer-2025
tante
tante@tldr.nettime.orgCool project: "Nepenthes" is a tarpit to catch (AI) web crawlers.
"It works by generating an endless sequences of pages, each of which with dozens of links, that simply go back into a the tarpit. Pages are randomly generated, but in a deterministic way, causing them to appear to be flat files that never change. Intentional delay is added to prevent crawlers from bogging down your server, in addition to wasting their time. Lastly, optional Markov-babble can be added to the pages, to give the crawlers something to scrape up and train their LLMs on, hopefully accelerating model collapse."
Trammell Hudson
th@v.stThe original artist describes their Fortran code that rendered the Nostromo's vector landing display in "Alien": https://archive.org/details/creativecomputing-1981-06/page/n51/mode/2up?ui=embed&view=theater