Posts
3368Following
712Followers
1580Alex Gough
quidity@infosec.exchangeMy team in Chrome Platform Security is hiring for a senior Android security expert - if you're into syscalls, binder, processes and other low level stuff you'd be perfect - I do this but for Windows and didn't know Chrome or much C++ when I started.
The ad is generic but feel free to ask questions - https://www.google.com/about/careers/applications/jobs/results/104891950447895238 - you'll be a part of a wider security team that works on lots of cool stuff and protects billions of people - https://www.chromium.org/Home/chromium-security/quarterly-updates/
buherator
buheratorFilled with hex strings
These are a few of my
Favorite things🤗
Neodyme
neodyme@infosec.exchangeFollowing our #38c3 talk about exploiting security software for privilege escalation, we're excited to kick off a new blog series! 🎊
Check out our first blog post on our journey to 💥 exploit five reputable security products to gain privileges via COM hijacking: https://neodyme.io/blog/com_hijacking_1/
CFG Bot 🤖
cfgbot@mastodon.socialProject: golang/go https://github.com/golang/go
File: src/cmd/compile/internal/walk/assign.go:281 https://github.com/golang/go/blob/refs/tags/go1.23.4/src/cmd/compile/internal/walk/assign.go#L281
func ascompatee(op ir.Op, nl, nr []ir.Node) []ir.Node
SVG:
dark https://tmr232.github.io/function-graph-overview/render/?github=https%3A%2F%2Fgithub.com%2Fgolang%2Fgo%2Fblob%2Frefs%2Ftags%2Fgo1.23.4%2Fsrc%2Fcmd%2Fcompile%2Finternal%2Fwalk%2Fassign.go%23L281&colors=dark
light https://tmr232.github.io/function-graph-overview/render/?github=https%3A%2F%2Fgithub.com%2Fgolang%2Fgo%2Fblob%2Frefs%2Ftags%2Fgo1.23.4%2Fsrc%2Fcmd%2Fcompile%2Finternal%2Fwalk%2Fassign.go%23L281&colors=light
nSinus-R (@nsr@infosec.exchange)
nsinusr@bird.makeupResults of the RP2350 Hacking Challenge are now public - I'm happy that my entry qualified as one of the winning breaks!
Also huge shout out to the other winners: @aedancullen, Kévin Courdesses, @ioactive & @hextreeio - awesome work!
Thanks for the challenge @raspberry_pi!
Alex Plaskett
alexjplaskett@bird.makeupHarnessing Libraries for Effective Fuzzing by @2ourc3
https://github.com/20urc3/Publications/blob/main/Articles/LIB_HARNESS_GUIDE/README.md
Alex Plaskett
alexjplaskett@bird.makeupToo Subtle to Notice: Investigating Executable Stack Issues in Linux Systems
buherator
buheratordansup
dansup@mastodon.socialI feel like gargron in 2022, so many new users with an underfunded budget 😅
I'm in talks with a few people who can help with our growth, but we could really use some more donations to help lessen the burden on my out of pocket expenses.
(It costs about 15k a year to manage pixelfed, and we're going on 7 years)
/r/netsec
_r_netsec@infosec.exchangeFrom arbitrary pointer dereference to arbitrary read/write in latest Windows 11 https://security.humanativaspa.it/from-arbitrary-pointer-dereference-to-arbitrary-read-write-in-latest-windows-11/
Dr. Christopher Kunz
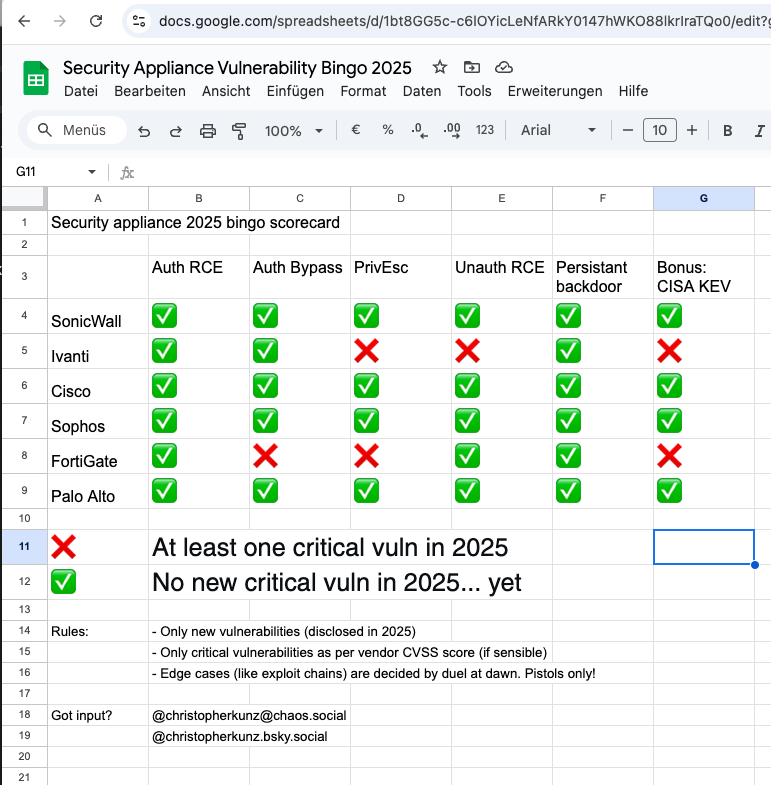
christopherkunz@chaos.socialAnyway, here we go. Latest version of the 2025 (in)security appliance bingo adds CVE-2024-55591 / FG-IR-24-535 to the list. Thanks to watchTowr for reporting it, and thanks to @wiert @nadaka and @cisacyber for alerting me to it. https://cku.gt/appbingo25
Frederik Braun �
freddy@security.plumbingForensic question as a windows-noob. I am trying to look into an OLE2 "Compound File Binary Format" file. It seems to contain multiple streams that I can enumerate with e.g., https://github.com/microsoft/compoundfilereader but the actual data are so-called "steams" containing raw hex bytes. What exactly is a *stream*? Doesn't look like a file? Are there deeper decodings I should pursue? Is there a list of known serializations for e.g., arrays? I think the database contains sensor data.
buherator
buheratorhttps://www.openwall.com/lists/oss-security/2025/01/14/3
Jeffrey Yasskin
jyasskin@hachyderm.ioJust found a great definition in a 2002 paper: "A system is secure from a given user’s perspective if the set of actions that each actor can do are bounded by what the user believes it can do."
https://digitalassets.lib.berkeley.edu/techreports/ucb/text/CSD-02-1184.pdf
And thanks @sereeena and Marian Harbach for finding it.
screaminggoat
screaminggoat@infosec.exchangeHappy #PatchTuesday from Zyxel: Zyxel security advisory for improper privilege management vulnerability in APs and security router devices
CVE-2024-12398 (8.8 high) An improper privilege management vulnerability in the web management interface of the Zyxel WBE530 firmware versions through 7.00(ACLE.3) and WBE660S firmware versions through 6.70(ACGG.2) could allow an authenticated user with limited privileges to escalate their privileges to that of an administrator, enabling them to upload configuration files to a vulnerable device.
There is no mention of exploitation.
Taggart
mttaggart@infosec.exchangeWell dang CVE-2025-21298
This bug rates a CVSS 9.8 and allows a remote attacker to execute code on a target system by sending a specially crafted mail to an affected system with Outlook. The specific flaw exists within the parsing of RTF files.
https://www.zerodayinitiative.com/blog/2025/1/14/the-january-2025-security-update-review
Eniko (moved ➡ gamedev.place)
eniko@peoplemaking.gameswho came up with january anyway? absolutely awful, useless month, 0/10
Binary Ninja
binaryninja@infosec.exchangeNeed to trigger BinExport headlessly to batch process patched binaries (using commercial and above)? First, build for a recent dev or stable: https://gist.github.com/psifertex/31d9bc3167eca91e466ebaae4382521c
Next, install the API for headless: https://docs.binary.ninja/dev/batch.html?h=install_api#install-the-api
Finally, automate your exporting using a script taking advantage of the PluginCommand and PluginCommandContext APIs, like the attached image.
screaminggoat
screaminggoat@infosec.exchangeHappy #PatchTuesday from Ivanti: January Security Update
Bottom line up front: "We have no evidence of any of these vulnerabilities being exploited in the wild."
Links:
- Security Advisory Ivanti Avalanche 6.4.7 (Multiple CVEs)
- Security Advisory - Ivanti Application Control Engine (CVE-2024-10630)
- (AC Engine is present on Ivanti Application Control, Ivanti Neurons for App Control and can integrate with Ivanti Security Controls and Ivanti Endpoint Manager)
- Security Advisory EPM January 2025 for EPM 2024 and EPM 2022 SU6
These are unrelated to the zero-day exploitation of CVE-2025-0282 inside of Ivanti Connect Security, Policy Secure and ZTA Gateways advisory from 08 January 2025.
Andrew Zonenberg
azonenberg@ioc.exchangeazonenberg@havequick:/tmp$ cat lulz.txt
2024-09-11 17:45 PDT
Successful extraction of RP2350 antifuse bits by FIB PVC
(Random text here to make hash bruteforcing harder)
fjoinzofkjpogkzpofzkpofkspofzpofkz
azonenberg@havequick:/tmp$ sha256sum lulz.txt
a76433af090ceb77b65b153285478bd615bdd51e26a3dd1d6a386b8e1f2ac362 lulz.txt