Posts
3471Following
717Followers
1584Binary Ninja
binaryninja@infosec.exchangeNeed to trigger BinExport headlessly to batch process patched binaries (using commercial and above)? First, build for a recent dev or stable: https://gist.github.com/psifertex/31d9bc3167eca91e466ebaae4382521c
Next, install the API for headless: https://docs.binary.ninja/dev/batch.html?h=install_api#install-the-api
Finally, automate your exporting using a script taking advantage of the PluginCommand and PluginCommandContext APIs, like the attached image.
screaminggoat
screaminggoat@infosec.exchangeHappy #PatchTuesday from Ivanti: January Security Update
Bottom line up front: "We have no evidence of any of these vulnerabilities being exploited in the wild."
Links:
- Security Advisory Ivanti Avalanche 6.4.7 (Multiple CVEs)
- Security Advisory - Ivanti Application Control Engine (CVE-2024-10630)
- (AC Engine is present on Ivanti Application Control, Ivanti Neurons for App Control and can integrate with Ivanti Security Controls and Ivanti Endpoint Manager)
- Security Advisory EPM January 2025 for EPM 2024 and EPM 2022 SU6
These are unrelated to the zero-day exploitation of CVE-2025-0282 inside of Ivanti Connect Security, Policy Secure and ZTA Gateways advisory from 08 January 2025.
Andrew Zonenberg
azonenberg@ioc.exchangeazonenberg@havequick:/tmp$ cat lulz.txt
2024-09-11 17:45 PDT
Successful extraction of RP2350 antifuse bits by FIB PVC
(Random text here to make hash bruteforcing harder)
fjoinzofkjpogkzpofzkpofkspofzpofkz
azonenberg@havequick:/tmp$ sha256sum lulz.txt
a76433af090ceb77b65b153285478bd615bdd51e26a3dd1d6a386b8e1f2ac362 lulz.txt
Talos Vulnerability Reports
talosvulnsWavlink AC3000 wctrls static login vulnerability
https://talosintelligence.com/vulnerability_reports/TALOS-2024-2034
CVE-2024-39754
Talos Vulnerability Reports
talosvulnsWavlink AC3000 login.cgi Unauthenticated Firmware Upload vulnerability
https://talosintelligence.com/vulnerability_reports/TALOS-2024-2036
CVE-2024-39608
Silent Signal
silentsignal@infosec.exchangeStory of a Pentester Recruitment 2025
https://blog.silentsignal.eu/2025/01/14/pentester-recruitment-2025-mushroom/
screaminggoat
screaminggoat@infosec.exchangeHappy #ZeroDay from your friends at Fortinet: Authentication bypass in Node.js websocket module
CVE-2024-55591 (CVSSv3.1: 9.8 critical) An Authentication Bypass Using an Alternate Path or Channel vulnerability [CWE-288] affecting FortiOS and FortiProxy may allow a remote attacker to gain super-admin privileges via crafted requests to Node.js websocket module.
Please note that reports show this is being exploited in the wild.
Indicators of compromise include possible log entries, IP addresses used, and admin accounts created. cc: @GossiTheDog @wdormann @cR0w @briankrebs
#zeroday #patchtuesday #fortinet #vulnerability #CVE_2024_55591 #infosec #ioc #threatintel #infosec #cybersecurity #
CFG Bot 🤖
cfgbot@mastodon.socialProject: golang/go https://github.com/golang/go
File: src/cmd/compile/internal/reflectdata/reflect.go:1708 https://github.com/golang/go/blob/refs/tags/go1.23.4/src/cmd/compile/internal/reflectdata/reflect.go#L1708
func NeedEmit(typ *types.Type) bool
SVG:
dark https://tmr232.github.io/function-graph-overview/render/?github=https%3A%2F%2Fgithub.com%2Fgolang%2Fgo%2Fblob%2Frefs%2Ftags%2Fgo1.23.4%2Fsrc%2Fcmd%2Fcompile%2Finternal%2Freflectdata%2Freflect.go%23L1708&colors=dark
light https://tmr232.github.io/function-graph-overview/render/?github=https%3A%2F%2Fgithub.com%2Fgolang%2Fgo%2Fblob%2Frefs%2Ftags%2Fgo1.23.4%2Fsrc%2Fcmd%2Fcompile%2Finternal%2Freflectdata%2Freflect.go%23L1708&colors=light
Anatoly Shashkin💾
dosnostalgic@mastodon.socialDOOM has now been ported to... a PDF!
(Works in browsers)
https://github.com/ading2210/doompdf
0patch
0patch@infosec.exchangeMicropatches Released for Windows "LDAPNightmare" Denial of Service Vulnerability (CVE-2024-49113)
https://blog.0patch.com/2025/01/micropatches-released-for-windows.html
daniel:// stenberg://
bagder@mastodon.socialTurns out snprintf() in old Windows C runtimes is documented to have the buffer overflow that no other implementations do. 🤔
/r/netsec
_r_netsec@infosec.exchangeThreat actors exploit a probable 0-day in exposed management consoles of Fortinet FortiGate firewalls https://www.orangecyberdefense.com/global/blog/cert-news/0-day-in-exposed-management-consoles-of-fortinet-fortigate-firewalls
kat
zkat@toot.catTIL \ exists in ASCII literally so that ALGOL could write its Boolean operators in ASCII
Talos Vulnerability Reports
talosvulnsOFFIS DCMTK nowindow improper array index validation vulnerability
https://talosintelligence.com/vulnerability_reports/TALOS-2024-2122
CVE-2024-47796
Talos Vulnerability Reports
talosvulnsOFFIS DCMTK determineMinMax improper array index validation vulnerability
https://talosintelligence.com/vulnerability_reports/TALOS-2024-2121
CVE-2024-52333
/r/netsec
_r_netsec@infosec.exchangeExploitation Walkthrough and Techniques - Ivanti Connect Secure RCE (CVE-2025-0282) - watchTowr Labs https://labs.watchtowr.com/exploitation-walkthrough-and-techniques-ivanti-connect-secure-rce-cve-2025-0282/
buherator
buheratorhttps://www.hoyahaxa.com/2025/01/an-ssrf-to-lfi-payload-for-pdf.html
Joxean Koret (@matalaz)
joxean@mastodon.socialDoes anybody know how to prevent #clang from issuing calls to libc functions like `memset` in this case when compiling C programs? I have tried I don't know how many command line arguments to try to disable it but none worked at all.
Here you have an example program in #godbolt: https://godbolt.org/z/jheYoPWzj
These are the command line arguments I've tried to disable it:
-ffreestanding -disable-simplify-libcalls -fno-builtin -nostdinc -nostdlib -fno-builtin-memset -nostdlib++ -nostdinc++
Any idea?
Tamir Bahar
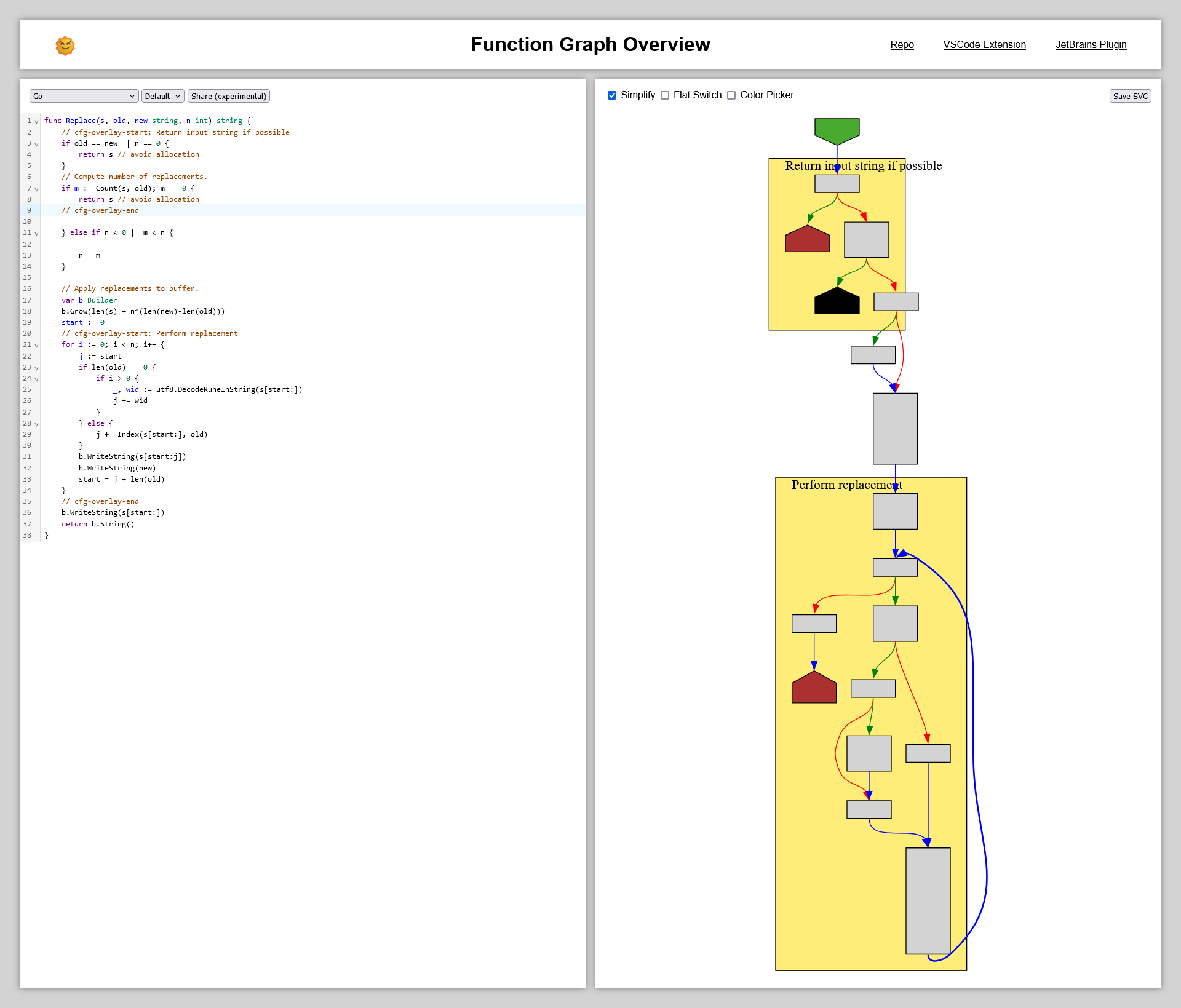
tmr232@mastodon.socialAdded the overlay-note-region-name-pending feature to the demo behind a feature-flag.
You can play with them at https://tmr232.github.io/function-graph-overview/?showRegions
Use `cfg-overlay-start: message` and `cfg-overlay-end` comments to denote the start and end of a region.
Danny Palmer
dannyjpalmer@infosec.exchangeIn one of the most "on brand" things I could write, here's an interview with Dan Keyworth, Director of Business Technology at McLaren Racing on how how the 2024 F1 World Constructor's Champions keep vast amounts of data and tech secured against cyber threats.
“We’ve got 200 people travelling around the world at any one time to 24 different races who, when they try to do something genuine, may look like they’re a threat to our organization,” says Keyworth.
“We’ve got to learn the different network behaviors they’re using when they’re on the road, for our business to recognize it as normal behavior when typically for other businesses, that’s abnormal behavior."
https://darktrace.com/the-inference/in-conversation-with-dan-keyworth-mclaren-racing