Posts
2558Following
621Followers
1371BleepingComputer
BleepingComputer@infosec.exchangeMicrosoft will force install the new Outlook email client on Windows 10 systems starting with next month's security update.
Tamir Bahar
tmr232@mastodon.socialCurrently working on adding comment-overlays to Function-Graph-Overview.
The idea is to add special begin- and end- comments, and use those to draw overlays on the graph (think C#'s region thingy).
I hope this will make the CFG more viable as a code-understanding tool, as we'll be able to better document our findings.
CatSalad🐈🥗 (D.Burch) 
catsalad@infosec.exchange
AI generated content in a nutshell
(Disclaimer: This has to be one of the worst videos I've ever watched... enjoy)
CFG Bot 🤖
cfgbot@mastodon.socialProject: openssl-static-gcc-dwarf 3.4.0
File: openssl
Address: 0062b660
ossl_parse_query
SVG:
dark https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fopenssl-static-gcc-dwarf%2F0062b660.json&colors=dark
light https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fopenssl-static-gcc-dwarf%2F0062b660.json&colors=light
LavX News
lavxnews@mastodon.cloudReviving a Classic: The Journey to Reconstruct F-15 Strike Eagle II's Code
In a remarkable feat of reverse engineering, a hobbyist has successfully reconstructed the executable for the 1989 game F-15 Strike Eagle II, bringing nostalgia and technical prowess together. This mi...
#news #tech #GameReconstruction #ReverseEngineering #F15StrikeEagleII
evacide
evacide@hachyderm.io“Why don’t you take some of that ‘go to mars’ money and actually help rather than Monday morning quarterbacking during a live fire?”
The CEO of Watch Duty is bringing the energy that we need to 2025.
https://sfstandard.com/2025/01/09/wildfires-watch-duty-elon-musk-los-angeles/
Still Mad About CD Prices
guyjantic@infosec.exchangeAnother take on AI that (at least for now) kinda nails it.
David Chisnall (*Now with 50% more sarcasm!*)
david_chisnall@infosec.exchangeUse of AI tools reduces critical thinking abilities. Frank Herbert looks more prophetic every day.
/r/netsec
_r_netsec@infosec.exchangeExploiting SSTI in a Modern Spring Boot Application (3.3.4) https://modzero.com/en/blog/spring_boot_ssti/
buherator
buheratorhttps://xia0.sh/blog/overview-of-wasm-in-jsengine-exploit?ref=blog.exploits.club
Project Zero Bot
p0botSamsung S24: Out of bounds write in APE Decoder
https://project-zero.issues.chromium.org/issues/368695689
CVE-2024-49415
buherator
buheratorThis company should not exist by now.
https://labs.watchtowr.com/do-secure-by-design-pledges-come-with-stickers-ivanti-connect-secure-rce-cve-2025-0282/
RE//verse Conference
REverseConf@infosec.exchangeOur 2025 RE//verse talk schedule is now live! Talks start Friday, but don't forget to check the Thursday schedule and arrive early enough for the kick-off event!
Arne Brasseur
plexus@toot.catOne of the most useful skills you get out of doing open source comes from learning to write READMEs.
Being able to describe a piece of software clearly and concisely in terms of
- what is is
- what it does
- how it does it
- why it does it that way
- how you use it
is a superpower that will you will be able to use throughout your career.
BrianKrebs
briankrebs@infosec.exchangePowerSchool, a provider of K-12 software and cloud solutions, had a breach over the holidays. But not to worry, they paid the cybercriminals who hacked them and they have a video of the crooks deleting the data.
"PowerSchool has received reasonable assurances from the threat actor that the data has been deleted and that no additional copies exist."
Thank goodness the threat actors are so reasonable, right? SMH.
Software Freedom Conservancy
conservancy@sfconservancy.orgdaniel:// stenberg://
bagder@mastodon.socialCongratulations all crowd strike users on macOS who now get warnings about the libcurl version shipped by Apple. May you all enjoy your choices of software vendors.
It alerts about CVE-2024-9681. We said it is severity low. NVD says 6.5 medium.
Never a dull moment.
Dr. Christopher Kunz
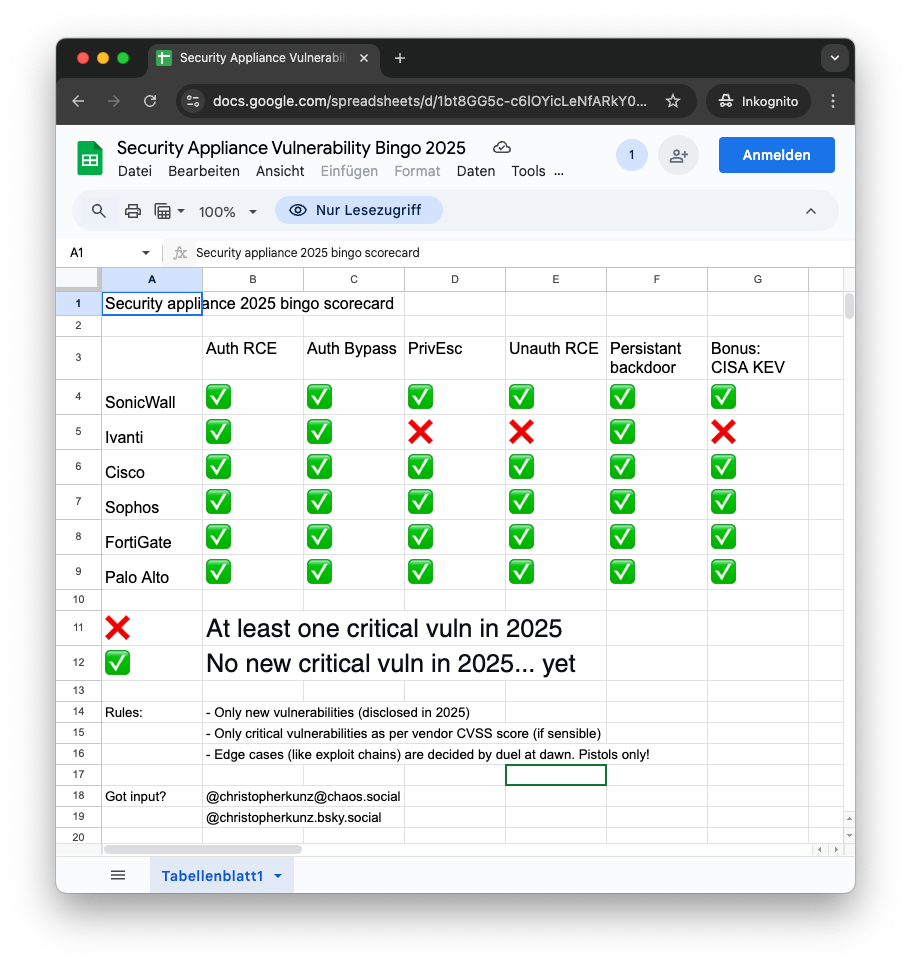
christopherkunz@chaos.socialOK, I fleshed this out a little more. You can find the (In)Security Appliance Bingo 2025 in proper, two-dimensional form here:
Suggestions and submissions very welcome.
screaminggoat
screaminggoat@infosec.exchangeCrowdStrike: Recruitment Phishing Scam Imitates CrowdStrike Hiring Process
Following CrowdStrike's successful Denial of Service attack on customers' Windows systems worldwide in July 2024, recruitment has gone up (this is a joke). CrowdStrike reports that a newly discovered phishing campaign uses CrowdStrike recruitment branding to convince victims to download a fake application, which serves as a downloader for the XMRig cryptominer. They describe the infection chain and provide Indicators of Compromise.
#crowdstrike #IOC #xmrig #cryptomining #infosec #cybersecurity #cyberthreatintelligence #CTI
buherator
buheratorhttps://devco.re/blog/2025/01/09/worstfit-unveiling-hidden-transformers-in-windows-ansi/