Posts
2681Following
677Followers
1504abadidea
0xabad1dea@infosec.exchange⚠️ If you use iTerm with the SSH integration functionality: some debug code accidentally shipped to production and it may be logging the entire session to /tmp... on the REMOTE server. If you SSH to shared hosts with iTerm, you'll probably want to look into deleting that as quickly as possible https://iterm2.com/downloads/stable/iTerm2-3_5_11.changelog
buherator
buheratorbuherator
buheratorhttps://github.com/radareorg/ghidra-r2web/tree/master/GhidraR2Web
As I don't have much experience with r2 I can only rely on feature requests to add functionality that makes sense, so please use the issue tracker liberally!
IMO this is also a great opportunity to discuss possible improvements of the r2web protocol to support more integrations.
/cc @pancake
Frederik Braun �
freddy@security.plumbingPlease Boost: To all Hacker Spaces in Berlin. I have a decommissioned server to give away. So far, I have been unable to find a beneficiary.
**Who wants this server?**
HP ProLiant DL360 Gen9 - 2 CPU E5-2697 v3 @ 2.60GHz, 128 GB DDR4, 2x 900GB SAS.
Pick-up in Berlin Kreuzberg.
𝕊ℍ𝔸𝕆𝕊
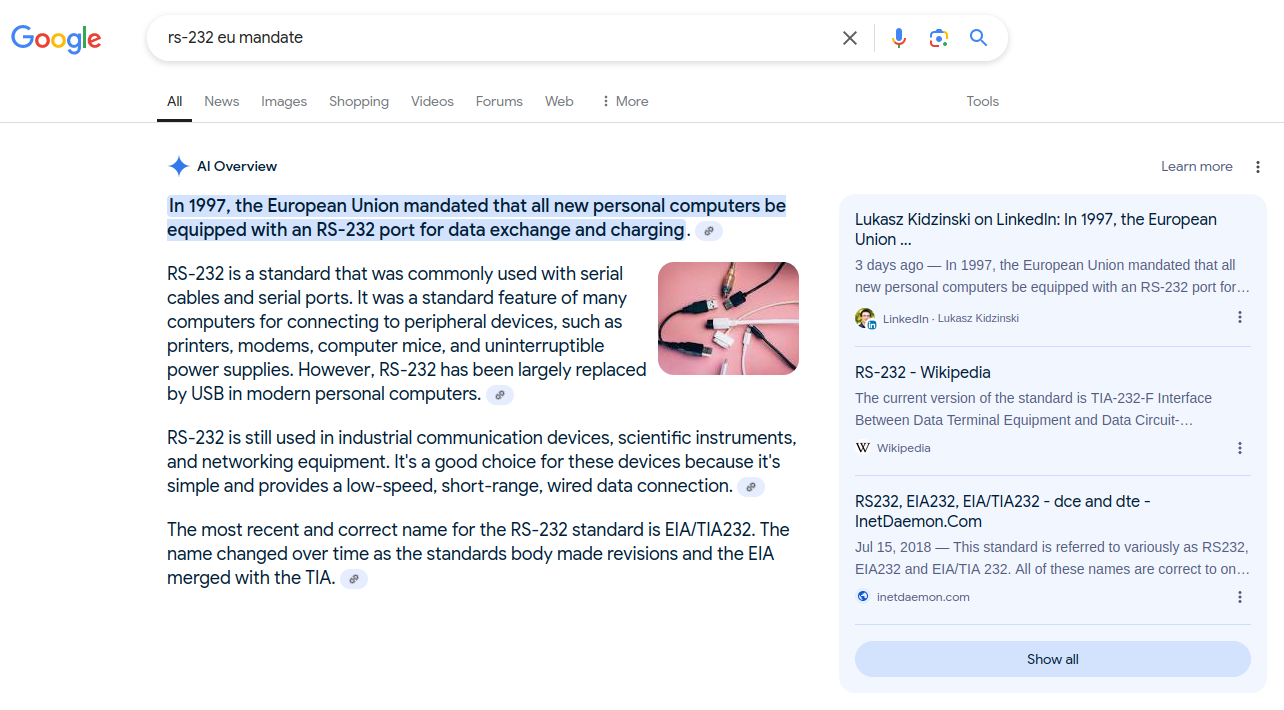
Shaos@mastodon.socialSomebody fooled Google AI to believe that EU mandated RS-232 usage in 1997 :)
#retrocomputing #rs232 #fakehistory
Micah Lee
micahflee@infosec.exchange"Apple has agreed to pay $95 million to settle a lawsuit alleging that its voice assistant Siri routinely recorded private conversations that were then sold to third parties for targeted ads." https://arstechnica.com/tech-policy/2025/01/apple-agrees-to-pay-95m-delete-private-conversations-siri-recorded/
buherator
buheratorhttps://arxiv.org/abs/2412.20324
#frombsky
Nahum Shalman
nahumshalman@hachyderm.ioI have tentatively done the work needed to get #Tailscale Taildrive sharing working on #illumos / #solaris.
It works for me. @papertigers please take a look!
https://github.com/nshalman/tailscale/releases/tag/v1.78.1-taildrive-sunos
Molly White
molly0xfff@hachyderm.ioThe world's richest man has joined a growing chorus of right-wing voices attacking Wikipedia as part of an intensifying campaign against free and open access information. Why do they hate it so much?
https://www.citationneeded.news/elon-musk-and-the-rights-war-on-wikipedia/
Viss
Viss@mastodon.socialheres a work related question for you, if you are in a position where you can hire consulting companies to help with security work (red/blue/eng/etc):
would it be handy to be able to buy a single day of effort, 7hrs of effort, 1hr reporting, and get a report worth sharing with either partners, customers, or leadership?
I'm thinking of building out a new offering. A one-day triage/best-effort assessment. internal, external, whatevs - dealers choice.
Mr. Bitterness
wdormann@infosec.exchangeSo this PoC for CVE-2024-49113 is indeed a thing.
https://www.safebreach.com/blog/ldapnightmare-safebreach-labs-publishes-first-proof-of-concept-exploit-for-cve-2024-49113/
Their writeup is confusingly worded in that it uses both the phrases "victim DC" and "any unpatched Windows Server (not just DCs)", in the same sentence nonetheless.
While the vul can be triggered by any lookup to a malicious LDAP server by any version of Windows, this particular PoC:
- Makes a MS-NRPC Netlogon Remote Protocol to talk to Windows Server, specifically DsrGetDcNameEx2, which gets info about the specified domain.
- Windows Server checks via DNS what LDAP server to talk to to get this info.
- Windows Server talks to the (malicious) LDAP server to service the request.
- The malicious LDAP server sends an unexpected LDAP referral value, causing LSASS.EXE, and subsequently Windows, to fall over.
It's perhaps important to note that CVE-2024-49113 is "just" a DoS, and CVE-2024-49112 is the more juicy RCE one. SafeBreach has indicated that they're still investigating what a full RCE chain might look like.
The fact that SafeBreach called their CVE-2024-49113 exploit "LDAPNightmare" is a bit deceptive, IMO, as CVE-2024-49112 is the thing of nightmares (CVSS 9.8). But hey, whatever gets clicks, amirite?
stacksmashing
stacksmashing@infosec.exchangeDoes someone happen to have a copy of the tangara-hw git repo and could push it to Github? The official repo is 502ing right now
Project Zero Bot
p0botWindows Kernel False File Immutability attack on registry hives via the Cloud Filter API
https://project-zero.issues.chromium.org/issues/42451734
CVE-2024-49114
Alexandre Borges
alexandreborges@infosec.exchangeDiving into ADB protocol internals:
part 01: https://www.synacktiv.com/publications/diving-into-adb-protocol-internals-12
part 02: https://www.synacktiv.com/en/publications/diving-into-adb-protocol-internals-22
#adb #mobile #protocol #informationsecurity #cybersecurity #reverseengineering
CFG Bot 🤖
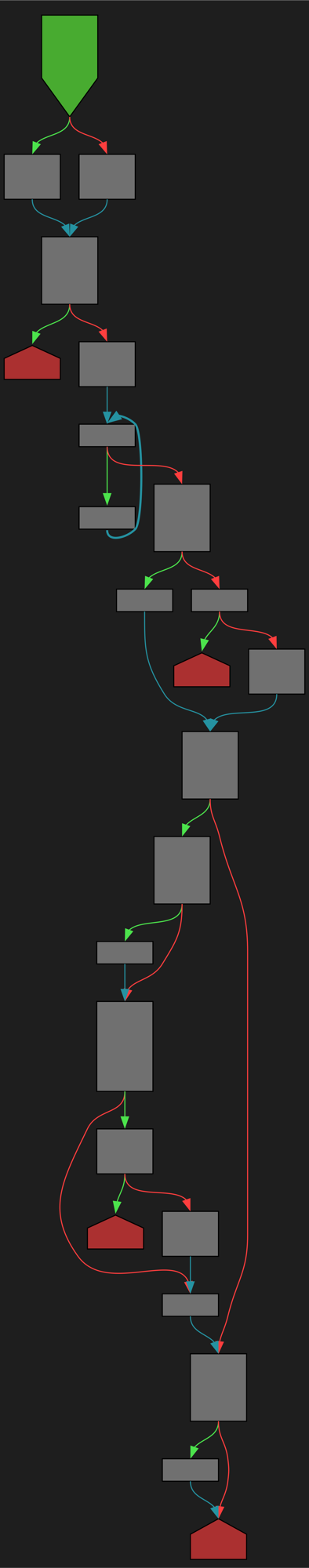
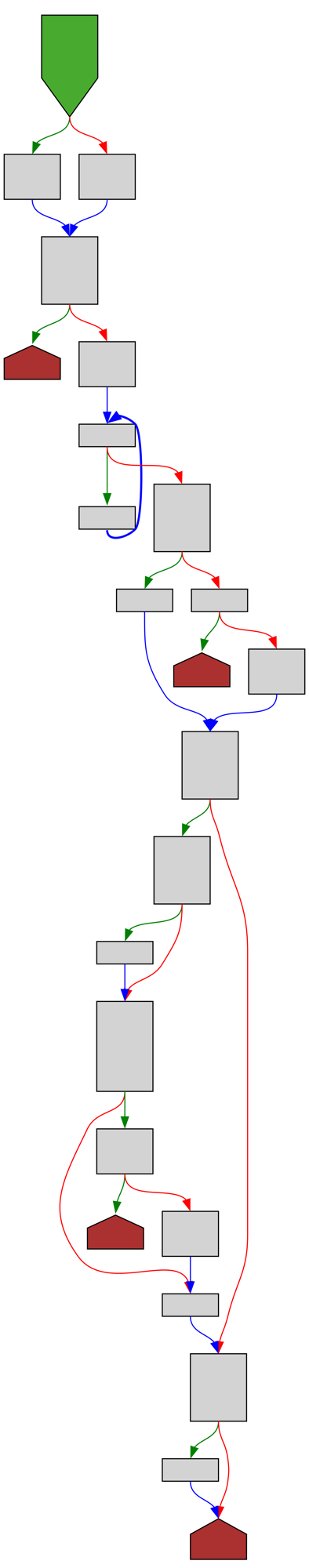
cfgbot@mastodon.socialProject: python/cpython https://github.com/python/cpython
File: Lib/ntpath.py:343 https://github.com/python/cpython/blob/2bd5a7ab0f4a1f65ab8043001bd6e8416c5079bd/Lib/ntpath.py#L343
def expanduser(path):
SVG:
dark https://tmr232.github.io/function-graph-overview/render/?github=https%3A%2F%2Fgithub.com%2Fpython%2Fcpython%2Fblob%2F2bd5a7ab0f4a1f65ab8043001bd6e8416c5079bd%2FLib%2Fntpath.py%23L343&colors=dark
light https://tmr232.github.io/function-graph-overview/render/?github=https%3A%2F%2Fgithub.com%2Fpython%2Fcpython%2Fblob%2F2bd5a7ab0f4a1f65ab8043001bd6e8416c5079bd%2FLib%2Fntpath.py%23L343&colors=light
screaminggoat
screaminggoat@infosec.exchangeProgress security advisory: WhatsUp Gold Security Bulletin December 2024
@cR0w Progress allegedly published this advisory 12 December 2024, but the page wasn't available from Google search results (thank Gemini AI ✨ for being useless) and Progress doesn't maintain a dedicated security advisories section on their website. Anyway, this page hasn't been updated with new information since 12 December so it's also useless. Here are the three vulnerabilities:
- CVE-2024-12105 (6.5 medium) authenticated information disclosure via specially crafted HTTP request
- CVE-2024-12106 (9.4 critical) unauthenticated attacker can configure LDAP settings
- CVE-2024-12108 (9.6 critical) an attacker can gain access to the WhatsUp Gold server via the public API
No mention of exploitation. Patched in WhatsUp Gold version 24.0.2
#infosec #progress #whatsupgold #cve #vulnerability #cybersecurity