Posts
2969Following
697Followers
1542buherator
buheratorNina Kalinina
nina_kali_nina@tech.lgbtI have spend a week writing a massive article about Windows 2. It has sexy screenshots and is full of incredible trivia. Why not spend the New Year's Eve reading it? ;)
algernon ludd is not resonating
algernon@come-from.mad-scientist.clubToday is Sweetmorn, the 1st day of Chaos in the 3191st Year of Our Lady of Discord
This sounds so much better than January 1st, 2025.
Accidental CISO
accidentalciso@infosec.exchangeAs you are preparing for your annual password change, I would like to remind you that our password policy clearly states that all characters are special.
Wladimir Palant
WPalant@infosec.exchangeJohn @tuckner sent me on an interesting wild goose chase. He is investigating the Cyberhaven extension compromise, trying to find out more. And he found something that he considered another campaign compromising browser extensions, related to the sclpfybn[.]com domain: https://secureannex.com/blog/cyberhaven-extension-compromise/#a-new-thread-to-pull-on
One of the extensions that used to contain the code in question was Visual Effects for Google Meet – which brought him to me because I recently covered that extension in my Karma Connection article: https://palant.info/2024/10/30/the-karma-connection-in-chrome-web-store/
I checked my data but couldn’t find sclpfybn[.]com domain mentioned in any extensions other than the ones @tuckner found already. I then looked for similar code and immediately found it in Urban VPN Proxy.
First thought: Urban VPN Proxy has the legitimate version of a library that was trojanized elsewhere. Taking a look at the communication of Urban VPN Proxy disproved that theory almost immediately – not only was it communicating in exactly the same way, but also to an unknown domain, namely ducunt[.]com. Yet the same endpoint existed on the official urban-vpn[.]com domain as well.
So not only did Urban VPN Proxy contain essentially the same code, it was likely added there by the developers themselves. Further investigation increased the suspicion that all these extensions haven’t been compromised, that this was rather some monetization SDK.
At which point @tuckner found the sales pitch for that SDK, detailing how it would add ad blocking functionality to the extension at the cost of exfiltrating very detailed browsing data (of course anonymized and aggregated before being sold to everyone asking for it, we know the drill). And explanations on how to make sure Google won’t object.
And that explains it all: before the Visual Effects for Google Meet developer sold their extension to Karma, they tried to monetize it with this “ad blocking library.” The sales pitch doesn’t mention who develops the library but everything points to Urban VPN.
According to Urban VPN privacy policy, they are selling the data they collect from their users via BIScience Ltd. Who are most likely the hidden owners of Urban Cyber Security Inc., a company registered to a virtual address in the USA.
Alan Sguigna
alansguigna@bird.makeupPart 2 of my series on Hypervisor-Managed Linear Address Translation (HLAT) is here: https://www.asset-intertech.com/resources/blog/2024/12/vt-rp-hlat-and-my-aaeon-alder-lake-core-i7-1270pe-board-part-2/. I used SourcePoint to pinpoint where HLAT is enabled on the p-cores of my AAEON Alder Lake board. Many thanks to @yarden_shafir, @aall86 and @standa_t for inspiration.
buherator
buheratorhttps://seclists.org/fulldisclosure/2024/Dec/21
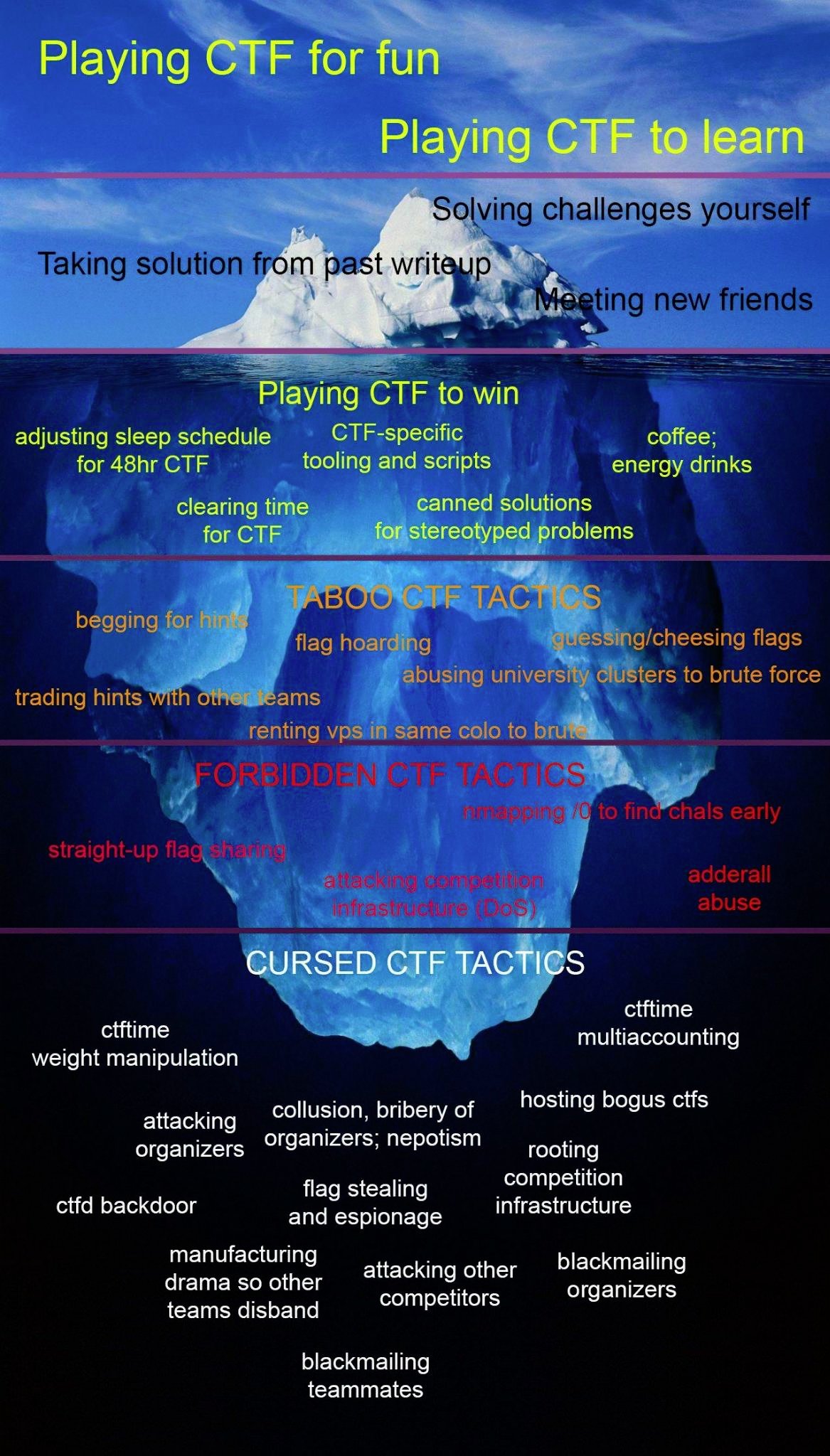
Do these count as Cursed CTF tactics?
buherator
buheratorhttps://hyp3rlinx.altervista.org/advisories/IBMi_Navigator_Server_Side_Request_Forgery_CVE-2024-51463.txt
https://hyp3rlinx.altervista.org/advisories/IBMi_Navigator_HTTP_Security_Token_Bypass-CVE-2024-51464.txt
(CVE-2024-51463, CVE-2024-51464)
buherator
buheratorhttps://www.ibm.com/support/pages/node/7180036?myns=swgother&mynp=OCSSPHQG&mynp=OCSWG60&mync=A&cm_sp=swgother-_-OCSSPHQG-OCSWG60-_-A
buherator
buheratorhttps://u1f383.github.io/linux/2024/12/28/remote-memory-access-in-linux.html
buherator
buheratorhttps://u1f383.github.io/linux/2024/12/29/the-feasibility-of-using-hardware-breakpoints-to-extend-the-race-window.html
buherator
buheratorhttps://blog.convisoappsec.com/en/from-arbitrary-file-write-to-rce-in-restricted-rails-apps/
buherator
buheratorhttps://old.reddit.com/r/ghidra/comments/1hpom0c/what_does_mean_to_commit_paramsreturn/
Benjamin Ross
BenRossTransit@mastodon.socialWaymo (aka Google) admits that it trains its robotaxis to break the law. When WaPo reporter finds robotaxis fail to stop for pedestrians in marked crosswalk 70% of the time, Waymo says it follows "social norms" rather than laws.
Expert explains: When robotaxis obey law, they don't go fast enough to compete successfully with Uber, so Google execs ordered engineers to ignore laws.
https://wapo.st/3ZZDifm
Florian Adamsky
c1t@mastodon.socialReminder: Tomorrow, @lavados, @lunkw1ll and I will give a talk at #38c3 about #Rowhammer at 12:00. If you want to check whether your computers are vulnerable to #Rowhammer, visit https://flippyr.am. Everything is open source! You can build our ISO and flash it onto your USB stick. If you're feeling lazy and trust us, come to Hall 3 by the palm tree and get a free USB stick with the ISO already flashed.
Slashdot 
slashdot@mastodon.cloud
'International Obfuscated C Code Contest' Will Relaunch, Celebrating 40th Anniversary https://developers.slashdot.org/story/24/12/29/1730224/international-obfuscated-c-code-contest-will-relaunch-celebrating-40th-anniversary?utm_source=rss1.0mainlinkanon
buherator
buheratorIs this a known thing or my skill/material issue? If the former, how should I solder these things?
#soldering