Posts
3138Following
708Followers
1556sha1lan
sha1lan@infosec.exchange"Invariant inversion" in memory-unsafe languages
https://pacibsp.github.io/2024/invariant-inversion-in-memory-unsafe-languages.html
dragosr
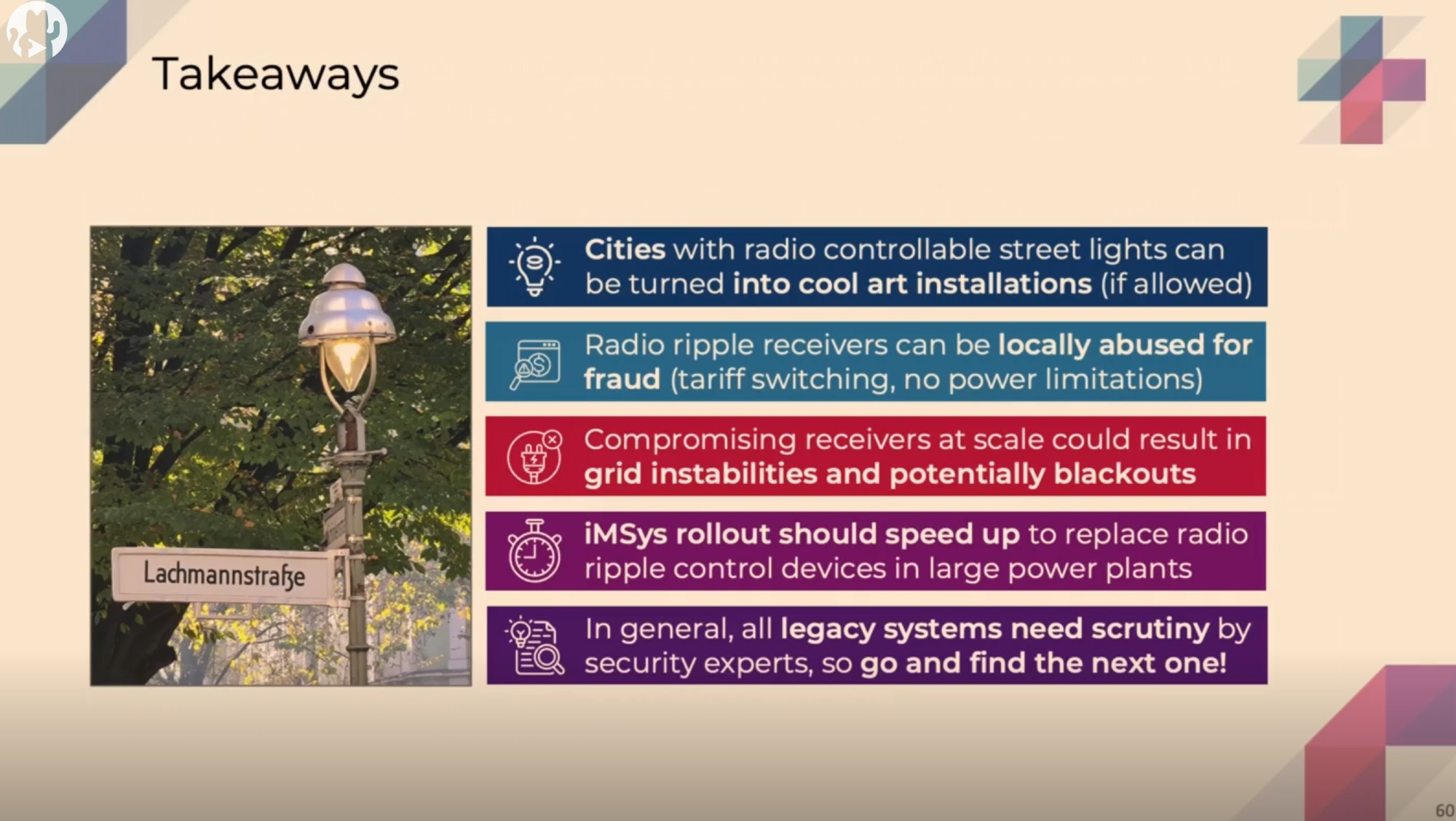
dragosr@chaos.socialThe CCC 38 Saal1 Presentation - BlinkenCity: Radio-Controlling Street Lamps and Power Plants by Fabian Bräunlein and Luca Melette
...on reversing streetlamps, ripple controls, Versacom and Semagyr, power gear, smart meters, controlling FREs with flashlights and flipper zero's(!), was a tour de force in reverse engineering, critical infrastructure risk analysis, and hacking excellence. If you use electricity or streets, you should watch it.
https://fahrplan.events.ccc.de/congress/2024/fahrplan/talk/HSNZGR/
buherator
buheratorRiddles 🏳️🌈😎😂
RIDDLES@c.imCartoon Network website officially shuts down after 32 years 💔🥹😩😩😩😩😩
buherator
buheratorhttps://blog.amberwolf.com/blog/2024/december/cve-2024-12908-delinea-protocol-handler---remote-code-execution-via-update-process/
#frombsky
Ken Shirriff
kenshirriff@oldbytes.spaceTo use the Montreal subway, you tap a paper ticket against the turnstile and it opens. But how does it work? And how can the ticket be so cheap that it's disposable? I opened up the tiny NFC chip inside to find out more... 1/15
internetarchive
internetarchive@mastodon.archive.orgThis year, we worked swiftly to save legacy media sites like https://Vice.com and MTVNews before decades worth of valuable journalism could be erased. These sites are searchable on the Wayback Machine. 📰📺
Help us in saving these resources: https://archive.org/donate/?origin=mstdn-eoy2024
Joshua J. Drake
jduck@infosec.exchangeOh! @raspberry_pi RP2350 gotcha detailed at @ccc. Does he win the prize?? https://events.ccc.de/congress/2024/hub/en/event/hacking-the-rp2350/
screaminggoat
screaminggoat@infosec.exchangeVulnCheck: Four-Faith Industrial Router CVE-2024-12856 Exploited in the Wild
CVE-2024-12856 (7.2 high) Four-Faith Industrial Router post-auth command injection is a reported exploited zero-day. Suricata rule available, no IOC though.
@todb there are still 2 more weekdays left in 2024, cram it all into the KEV!
#vulnerability #fourfaith #cve #eitw #activeexploitation #CVE_2024_12856 #infosec #cybersecurity
Simon Repp
freebliss@post.lurk.orgAfter 6 months and about 333 commits I proudly present:
Faircamp 1.0 – A static site generator for audio producers
https://simonrepp.com/faircamp/
To recap the highlights of the past months and learn what's new in the final 1.0 release, check out the blog post: https://simonrepp.com/posts/faircamp-1.0/
Development of version 1.0 was made possible through the amazing support, funding and expertise of the @NGIZero programme and coalition, led by the @nlnet foundation and financed by the European Commission's @EC_NGI initiative – thank you so much for giving me and everyone benefitting from a better Faircamp this incredible opportunity!
Also, many thanks to all faircampers, contributors, testers, translators, bloggers, podcasters and encouraging voices for supporting this journey - for the final 1.0 release specifically to @branpos for release candidate testing, @n00q for bugreporting/testing, @limebar for the external artist page feature inspiration and @Vac for their diligent translation work.
Along with this release I've published multiple new documentation resources - from an official Linux/macOS/Windows tutorial to a 1.0 migration guide, from an overhauled reference manual to a beginner's guide to publishing faircamp (or any!) static sites - check out the website and recent posts in the #faircamp hashtag to discover them!
That's all!
Ange
Ange@mastodon.socialI presented about file formats at #38C3.
Thanks for the feedback everyone!
https://speakerdeck.com/ange/fearsome-file-formats-18374bc4-b3f2-429f-862e-2177ab4d7aae
Balthasar
balthasar@infosec.exchangeUnsigned and unencrypted radio protocols control a large amount of street lamps and power plants, threatening European grid stability.
All you need is a large antenna, aka. putting a wire on a kite.
Check the research of Fabian and Luca in Saal 1 at 21:45 #38c8 or at Spiegel (paywall).
buherator
buheratorhttps://streaming.media.ccc.de/38c3/relive/492
Didn't expect this one to have a #synthdiy angle! 🤩
buherator
buheratorAt #38c3 guys from Neodyme demonstrated some more elegant exploits than my initial PoCs, nice work! My German is rusty but I think I'd have some comments about proposed solutions :)
ReLive will be available here:
https://streaming.media.ccc.de/38c3/relive/815
buherator
buheratorhttps://events.ccc.de/congress/2024/hub/event/der-schlssel-zur-compromittierung-local-privilege-escalation-schwachstellen-in-av-edrs/
This looks remarkably similar to my previous research on #antivirus privescs:
https://blog.silentsignal.eu/2018/01/08/bare-knuckled-antivirus-breaking/
https://blog.silentsignal.eu/2019/06/24/self-defenseless-exploring-kasperskys-local-attack-surface/
Can't wait to see what these guys found!
Does anybody have a tap for a keg of beer (10l, DIN 6647-1) with them? Maybe a top vent as well. We Cologne people have beer, but no way to get it out of the keg.
If you can help us out of our misery, that would be great. And you'll get beer! 🍻



 domenuk
domenuk