Posts
3373Following
712Followers
1579stacksmashing
stacksmashing@infosec.exchangeIn 50 minutes I’ll present some awesome hardware hacking on Apple’s new USB-C controller at #38c3 - would love to see you there!
Martin Seeger
masek@infosec.exchangeRemark concerning #Azerbaijan #Airlines #Flight #8243:
We would do well to remember the names of the pilots who died.
They fought for over an hour with a mortally wounded plane to get it as good as possible to the ground.
They had now yaw, no rudder, no ailerons, no flaps, only the power level of the engine as means of control.
Air Traffic Control denied them the use of the closest airports and sent them to cross a sea.
What they have shown is courage in the face of insurmountable odds. They knew exactly what their chances were. Their airmanship was on the highest possible level.
Their names are Igor Kshnyakin and Aleksandr Kalyaninov.
To the media: please don’t give any airtime to the obviously disinformation spreading speaker of the Kremlin and report about those who saved 29 lives.
sixteen character network interface name
algernon@come-from.mad-scientist.clubTIL that with a linker script, you can have emojis as ELF section names.
I need an opportunity to use this knowledge.
Picard Tips
PicardTips@mas.toPicard management tip: Take your leisure time seriously. A relaxed captain is a sane captain.
spaf
spaf@mstdn.socialHere's a no-cost, non-denominational, last-minute gift idea.
Reach out to people who made a positive difference in your life but with whom you have not been in touch for a while. Tell them that they were a force for good in your life. Thank them.
Be generous -- pass on this idea. Spread some joy.
screaminggoat
screaminggoat@infosec.exchangeOne the twelfth day of Christmas, the true goat gave to thee: https://infosec.press/screaminggoat/patch-tuesday , which is a list of vendors' security advisory landing pages and their #PatchTuesday schedule.
Disclaimer: Not every vendor is listed, and their patching cycle may be different than what I categorized them as, but it's a good starting point. Ideally, you'd be tracking the ones you care about using RSS anyway.
Merry Christmas Infosec Mastodon
buherator
buheratorhttps://devblogs.microsoft.com/oldnewthing/20241224-00/?p=110675
buherator
buheratorhttps://clearbluejar.github.io/posts/everyday-ghidra-symbols-automatic-symbol-acquisition-with-ghidra-part-2/
buherator
buheratorhttps://www.hoyahaxa.com/2024/12/an-initial-analysis-of-cve-2024-53961.html
buherator
buheratorhttps://www.netspi.com/blog/technical-blog/web-application-pentesting/second-order-sql-injection-with-stored-procedures-dns-based-egress/
Michael Veale
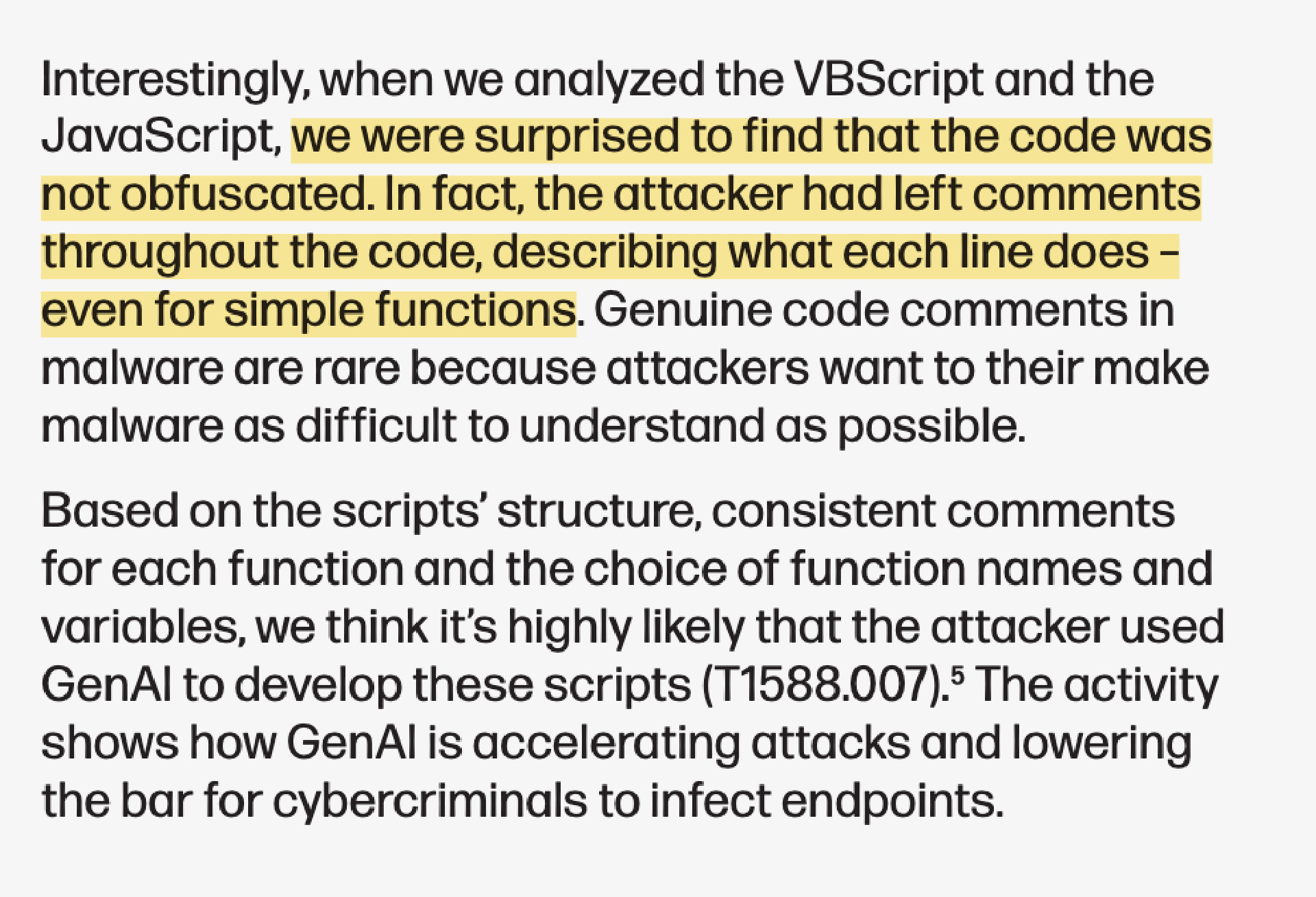
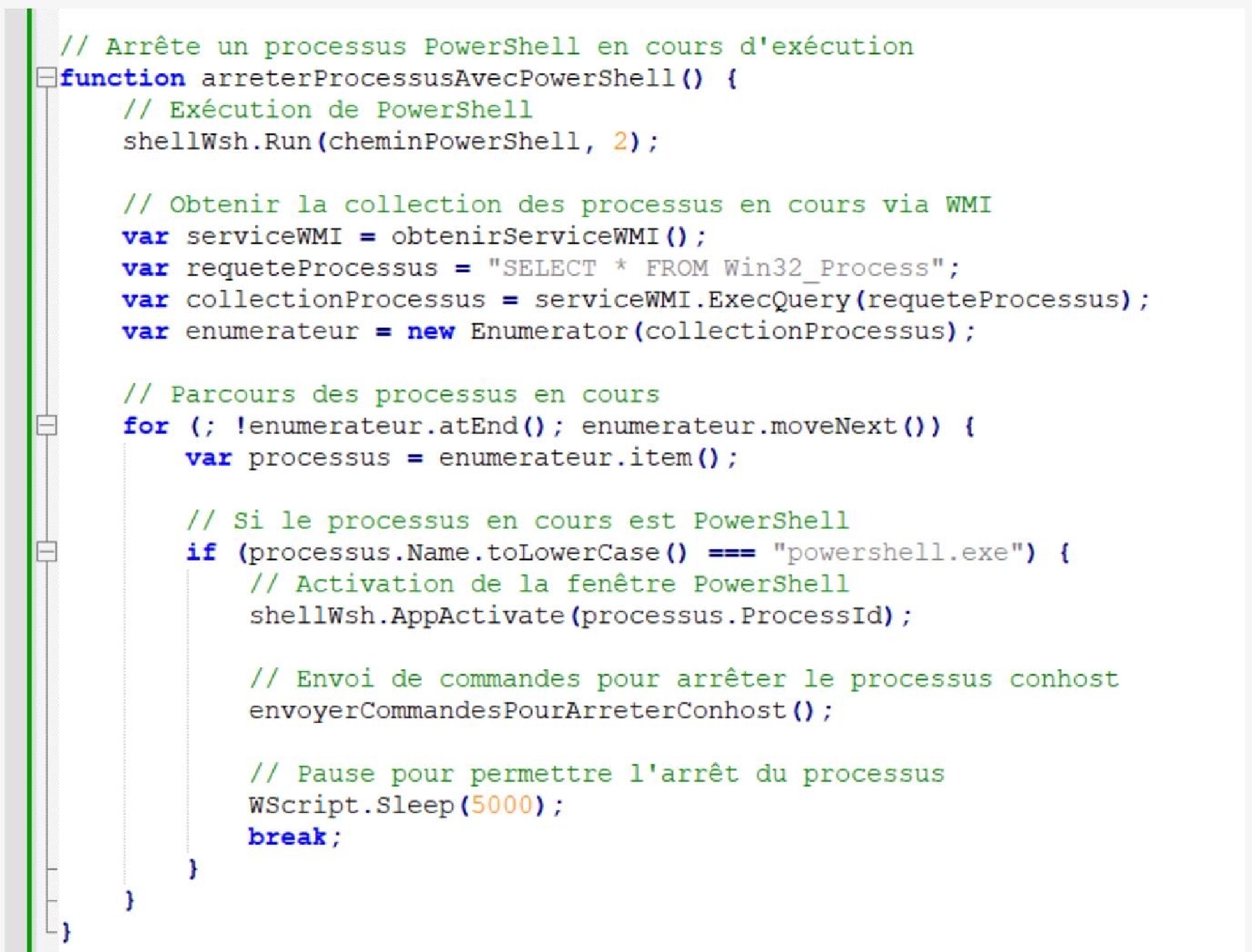
mikarv@someone.elses.computerHewlett Packard report that they are spotting AI-generated malware in the wild, not through complex analysis or watermarking, but because… it is weirdly well-commented. https://threatresearch.ext.hp.com/wp-content/uploads/2024/09/HP_Wolf_Security_Threat_Insights_Report_September_2024.pdf
buherator
buheratorBased on the analysis[1] it's a nice example of Chesterton’s Fence[2], while its discovery[3] underlines the importance of automated testing for regressions and known dangerous behavior.
[1] https://www.openwall.com/lists/oss-security/2024/12/25/2 (thx @alexandreborges for sharing!)
[2] https://fs.blog/chestertons-fence/
[3] https://gitlab.gnome.org/GNOME/libxml2/-/issues/761
Alexandre Borges
alexandreborges@infosec.exchangeCVE-2024-40896 Analysis: libxml2 XXE due to type confusion
https://www.openwall.com/lists/oss-security/2024/12/25/2
#cve #linux #libxml2 #xxe #vulnerability #exploitation #bug #typeconfusion