Posts
3139Following
708Followers
1555Plague Doctor algernon
algernon@come-from.mad-scientist.clubTIL that with a linker script, you can have emojis as ELF section names.
I need an opportunity to use this knowledge.
Picard Tips
PicardTips@mas.toPicard management tip: Take your leisure time seriously. A relaxed captain is a sane captain.
spaf
spaf@mstdn.socialHere's a no-cost, non-denominational, last-minute gift idea.
Reach out to people who made a positive difference in your life but with whom you have not been in touch for a while. Tell them that they were a force for good in your life. Thank them.
Be generous -- pass on this idea. Spread some joy.
screaminggoat
screaminggoat@infosec.exchangeOne the twelfth day of Christmas, the true goat gave to thee: https://infosec.press/screaminggoat/patch-tuesday , which is a list of vendors' security advisory landing pages and their #PatchTuesday schedule.
Disclaimer: Not every vendor is listed, and their patching cycle may be different than what I categorized them as, but it's a good starting point. Ideally, you'd be tracking the ones you care about using RSS anyway.
Merry Christmas Infosec Mastodon
buherator
buheratorhttps://devblogs.microsoft.com/oldnewthing/20241224-00/?p=110675
buherator
buheratorhttps://clearbluejar.github.io/posts/everyday-ghidra-symbols-automatic-symbol-acquisition-with-ghidra-part-2/
buherator
buheratorhttps://www.hoyahaxa.com/2024/12/an-initial-analysis-of-cve-2024-53961.html
buherator
buheratorhttps://www.netspi.com/blog/technical-blog/web-application-pentesting/second-order-sql-injection-with-stored-procedures-dns-based-egress/
Michael Veale
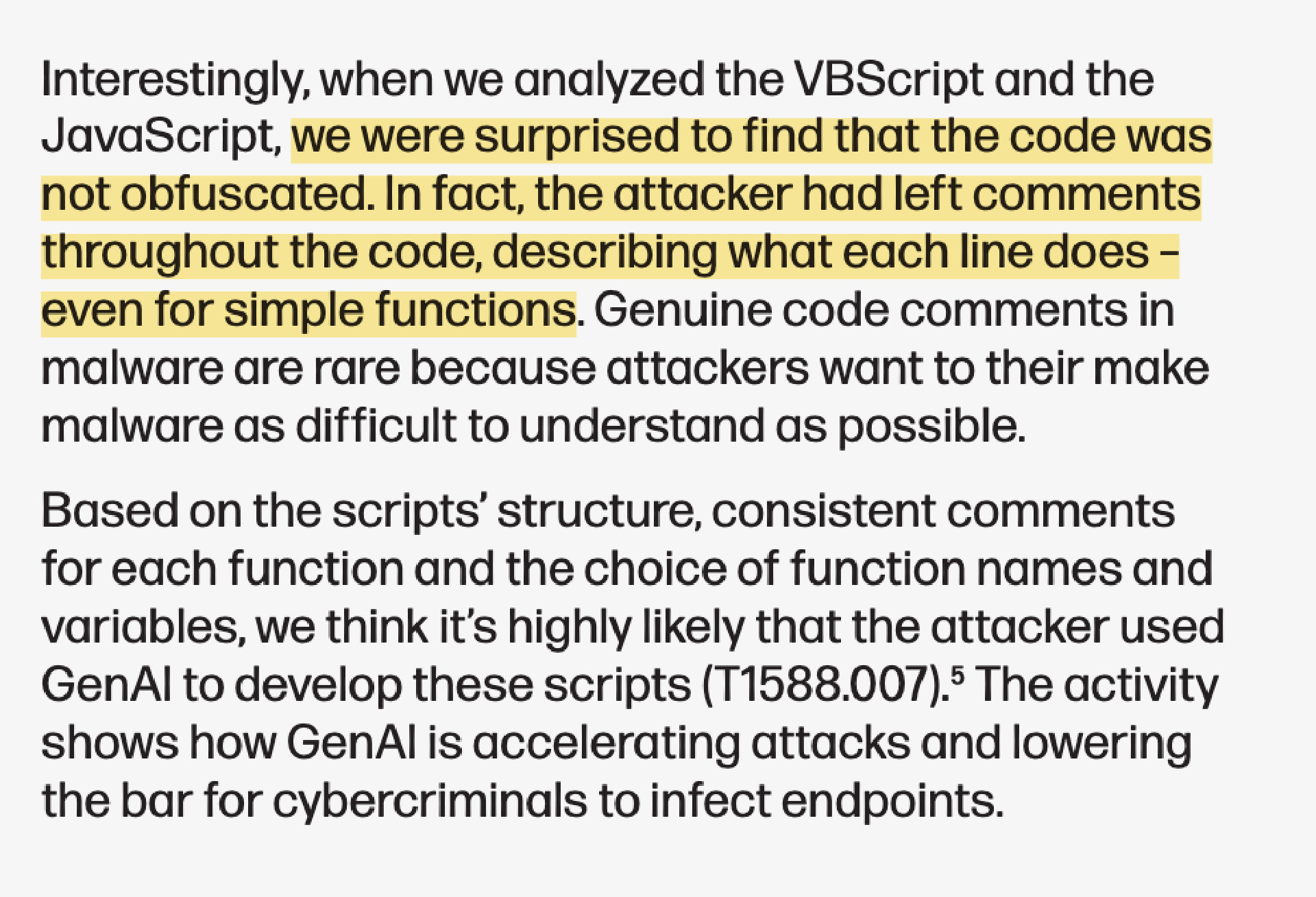
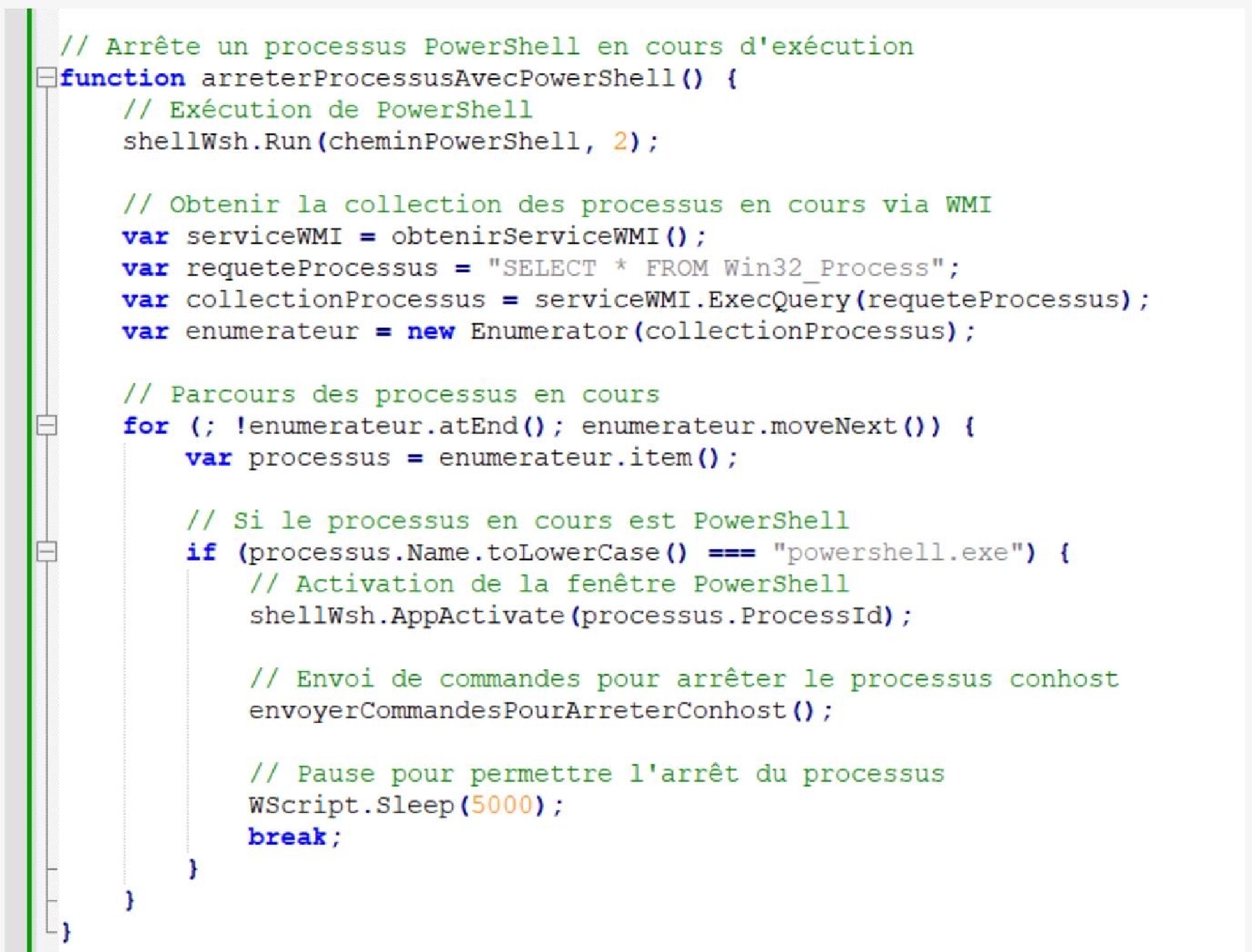
mikarv@someone.elses.computerHewlett Packard report that they are spotting AI-generated malware in the wild, not through complex analysis or watermarking, but because… it is weirdly well-commented. https://threatresearch.ext.hp.com/wp-content/uploads/2024/09/HP_Wolf_Security_Threat_Insights_Report_September_2024.pdf
buherator
buheratorBased on the analysis[1] it's a nice example of Chesterton’s Fence[2], while its discovery[3] underlines the importance of automated testing for regressions and known dangerous behavior.
[1] https://www.openwall.com/lists/oss-security/2024/12/25/2 (thx @alexandreborges for sharing!)
[2] https://fs.blog/chestertons-fence/
[3] https://gitlab.gnome.org/GNOME/libxml2/-/issues/761
Alexandre Borges
alexandreborges@infosec.exchangeCVE-2024-40896 Analysis: libxml2 XXE due to type confusion
https://www.openwall.com/lists/oss-security/2024/12/25/2
#cve #linux #libxml2 #xxe #vulnerability #exploitation #bug #typeconfusion
xvonfers
xvonfers@bird.makeup🤣🤣🤣
[CVE-2024-40896][libxml2] XXE protection broken in downstream code
https://gitlab.gnome.org/GNOME/libxml2/-/issues/761
https://gitlab.gnome.org/GNOME/libxml2/-/commit/1a8932303969907f6572b1b6aac4081c56adb5c6
"...bug should occur if you compile libraptor with the commit above and libxml2 2.11 or greater."
starlabs
starlabs_sg@bird.makeup🎄 All I Want for Christmas is a CVE-2024-30085 Exploit 🎄
As always, we at @starlabs_sg are sharing what we learnt. This time, it's brought to you by Cherie-Anne Lee
https://starlabs.sg/blog/2024/all-i-want-for-christmas-is-a-cve-2024-30085-exploit/
John Mark Ockerbloom
JMarkOckerbloom@mastodon.socialMore than funds, what Wikipedia really needs is more good editors. The number of people who regularly edit articles in English Wikipedia hasn't grown substantially in years, while the number of articles has, and editor demographics remains skewed. The foundation itself largely stays away from editing, leaving it to volunteers. While articles that get a lot of attention are often good, it's not hard to find ones with biased and promotional content in less-visited topics, and in other languages.