Posts
2970Following
697Followers
1543Caitlin Condon
catc0n@infosec.exchangeAlmost exactly a year ago, Rapid7 put out a technical analysis of Apache #Struts 2 CVE-2023-50164 that said:
* Exploit payloads were going to need to be customized to the target
* It wasn't clear that there was any critical mass of remotely exploitable applications out of the box
* The reports of exploitation in the wild all appeared to be unsuccessful attempts rather than IRL compromises of production systems.
https://attackerkb.com/topics/pe3CCtOE81/cve-2023-50164/rapid7-analysis
Fast-forward to CVE-2024-53677 and we can repeat the above verbatim, with one pretty notable exception — the "fixed" version that ostensibly remediates the vulnerability actually doesn't, and code-level changes are required (to migrate away from the vulnerable file upload interceptor) to actually remediate it. Also the "fixed" release (6.4.0) appears to have gone out a year ago? No idea. Big ups to @fuzz for the analysis!
https://attackerkb.com/assessments/28f08c0a-702c-4ab0-99cb-eea00202fa2c
kcarruthers
kcarruthers@mastodon.socialHIV breakthrough: drug trial shows injection twice a year is 100% effective against infection
http://theconversation.com/hiv-breakthrough-drug-trial-shows-injection-twice-a-year-is-100-effective-against-infection-233295
Alexandre Dulaunoy
adulau@infosec.exchangeIf you are wondering about the unpublished CVE-2024-49848... there is a PoC.
🔗 https://vulnerability.circl.lu/comment/23fd524b-475e-4b9f-8dc2-7b67f4cec409
buherator
buheratorbuherator
buheratorhttps://www.bloomberg.com/news/articles/2024-12-18/us-probes-china-founded-router-maker-on-national-security-fears
TP-Link about join the club of Huawei&Kaspersky
#frombsky
Craig Grannell
craiggrannell@mastodon.socialUK: “It’s still illegal to rip a CD you legally own to MP3!”
Also UK: “Hey, let’s exempt those AI guys from copyright law!”
FFS.
https://www.gov.uk/government/consultations/copyright-and-artificial-intelligence
Open Web Docs
openwebdocs@front-end.socialLearn about XSS for XMAS!
We created a new MDN page about Cross-site scripting: https://developer.mozilla.org/en-US/docs/Web/Security/Attacks/XSS
cpresser
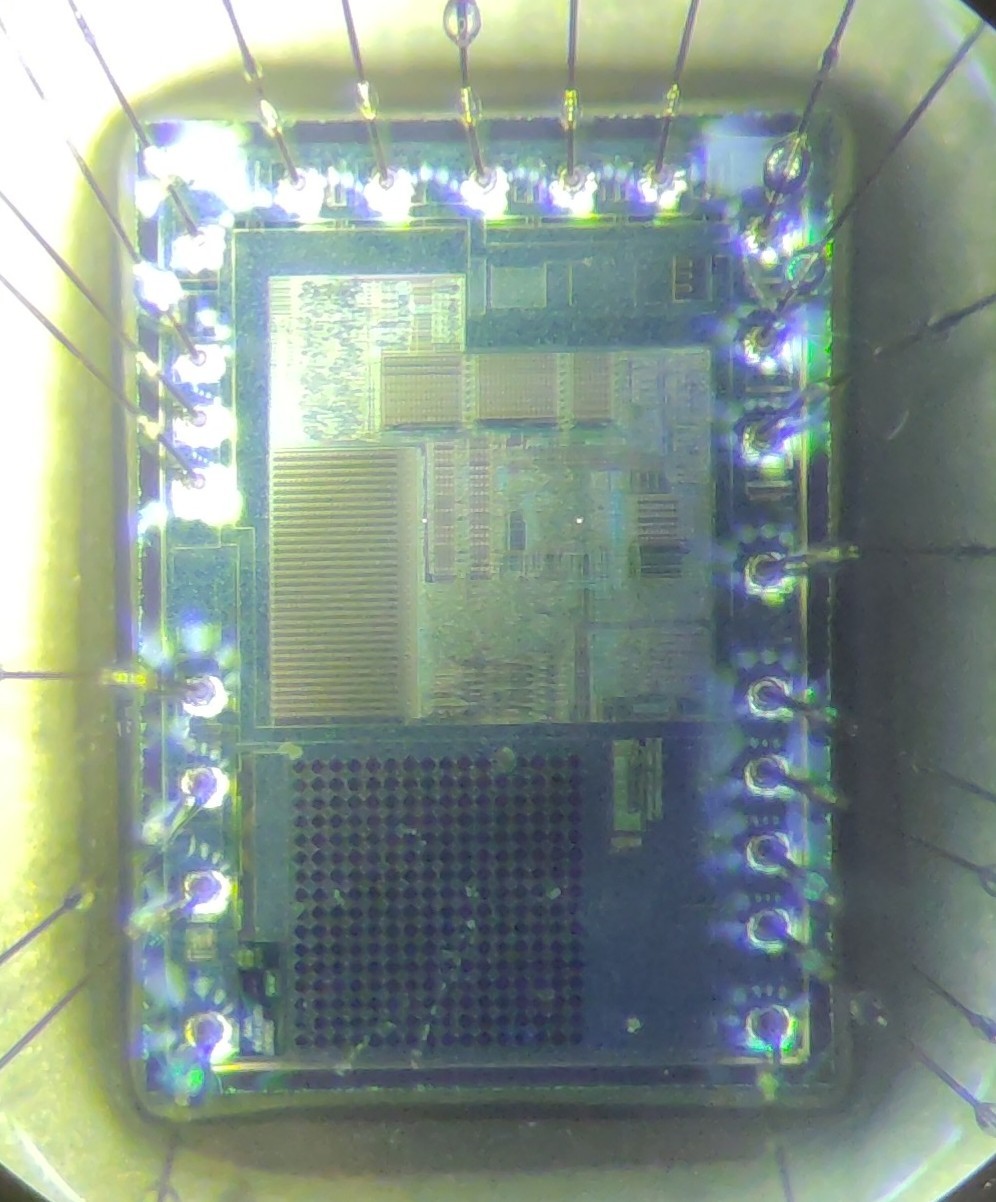
cccpresser@chaos.socialHere is another #NameThatWare challenge. This time I am quite sure that no text or marking needs to be blurred.
Do you know what this thing is? Can you name the exact part number or product name?
As always, explain your guess/deduction and hide it behind a CW to not spoil others.
buherator
buheratorhttps://www.youtube.com/watch?v=0f_TbyIIPnc
#hardstyle
✧✦Catherine✦✧
whitequark@mastodon.socialgame i would like to play: Factorio but you *only* do compliance paperwork
HalvarFlake
HalvarFlake@mastodon.socialI am mildly amused that OpenAI telemetry rollout led to a classical Kubernetes control plane DoS.
In my experience DDoSing your own control plane is the #1 way people generate large failures in K8s. What are others?
buherator
buheratorhttps://blog.wpsec.com/the-full-story-of-cve-2024-6386-remote-code-execution-in-wpml/
Frederik Braun � 🔜 #39C3
freddy@security.plumbingHey y'all,
the https://madweb.work/ Program Committee was just announced (featuring yours truly).
Please remember to submit your papers about web security by January 9th 2025. We are interested in research at the junction of web & browser security. More on the website :)
buherator
buheratorhttps://binary.ninja/2024/12/16/flareon-ttd.html
buherator
buheratorhttps://outurnate.com/authentication-bypass-vulnerability-in-philips-intellispace-cardiovascular
buherator
buheratorhttps://x41-dsec.de/security/research/job/news/2024/12/16/backstage-review-2024/
CVE-2024-45815 CVE-2024-45816 CVE-2024-46976
Tim (Wadhwa-)Brown 
timb_machine@infosec.exchange
buherator
buheratorhttps://sam4k.com/linternals-exploring-the-mm-subsystem-part-1/
buherator
buheratorhttps://karmainsecurity.com/hacking-kerio-control-via-cve-2024-52875
Foone🏳️⚧️
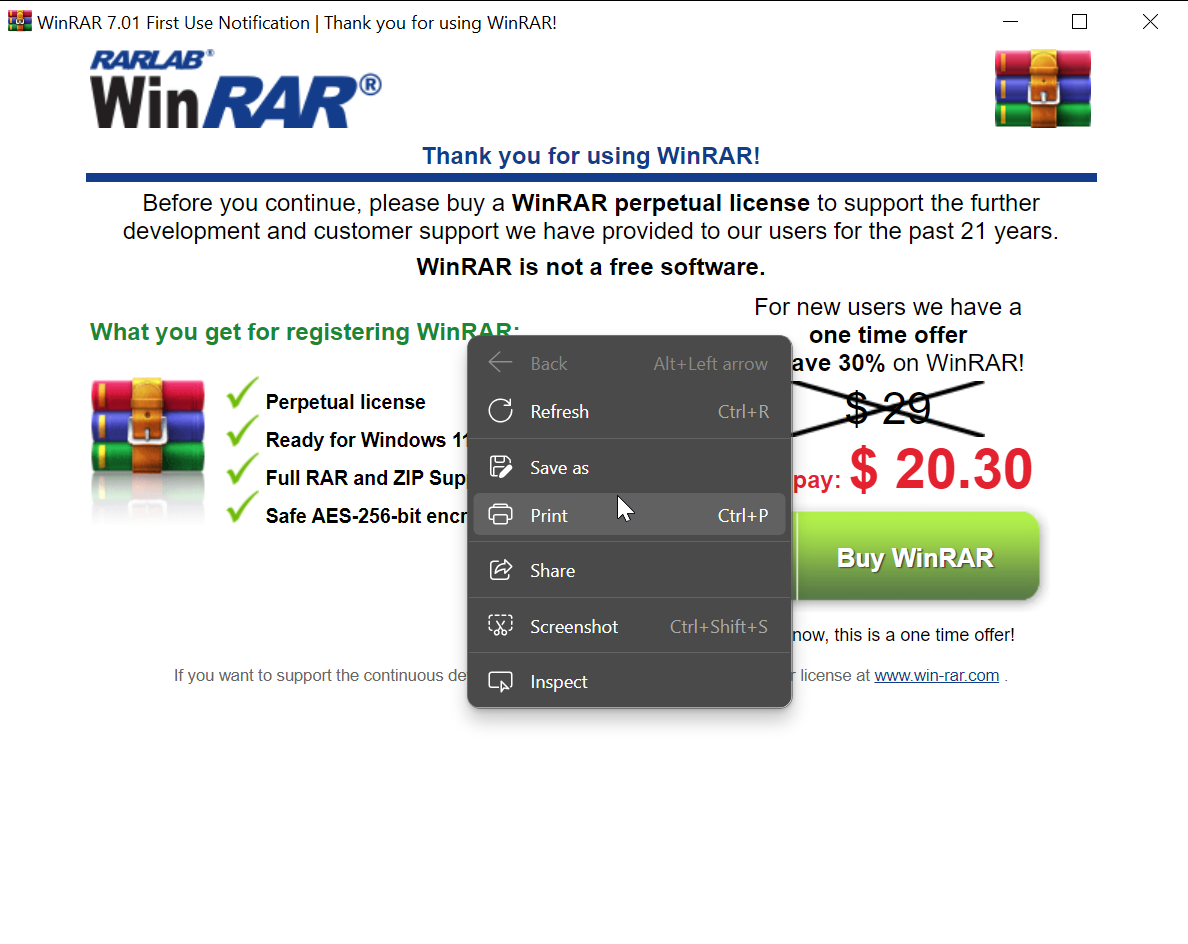
foone@digipres.clubFeel old yet? The winrar registration nag screen is Electron these days.
EDIT: Whoops, it seems I'm wrong: This is just an embedded webview, which on Win10 is apparently chromium-backed (probably because it's Edge)