Posts
3055Following
703Followers
1553Open Web Docs
openwebdocs@front-end.socialLearn about XSS for XMAS!
We created a new MDN page about Cross-site scripting: https://developer.mozilla.org/en-US/docs/Web/Security/Attacks/XSS
cpresser
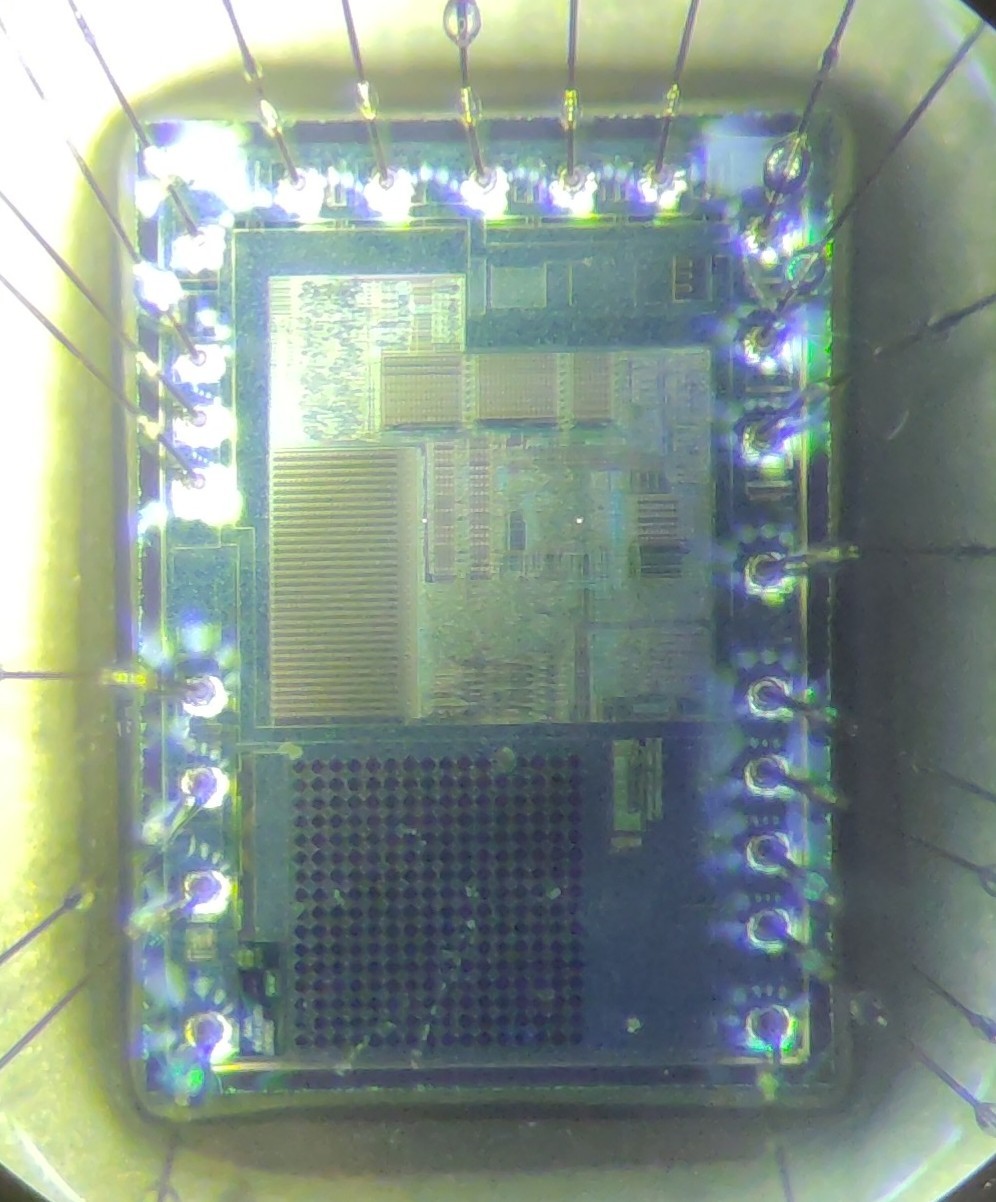
cccpresser@chaos.socialHere is another #NameThatWare challenge. This time I am quite sure that no text or marking needs to be blurred.
Do you know what this thing is? Can you name the exact part number or product name?
As always, explain your guess/deduction and hide it behind a CW to not spoil others.
buherator
buheratorhttps://www.youtube.com/watch?v=0f_TbyIIPnc
#hardstyle
✧✦Catherine✦✧
whitequark@mastodon.socialgame i would like to play: Factorio but you *only* do compliance paperwork
HalvarFlake
HalvarFlake@mastodon.socialI am mildly amused that OpenAI telemetry rollout led to a classical Kubernetes control plane DoS.
In my experience DDoSing your own control plane is the #1 way people generate large failures in K8s. What are others?
buherator
buheratorhttps://blog.wpsec.com/the-full-story-of-cve-2024-6386-remote-code-execution-in-wpml/
Frederik Braun �
freddy@security.plumbingHey y'all,
the https://madweb.work/ Program Committee was just announced (featuring yours truly).
Please remember to submit your papers about web security by January 9th 2025. We are interested in research at the junction of web & browser security. More on the website :)
buherator
buheratorhttps://binary.ninja/2024/12/16/flareon-ttd.html
buherator
buheratorhttps://outurnate.com/authentication-bypass-vulnerability-in-philips-intellispace-cardiovascular
buherator
buheratorhttps://x41-dsec.de/security/research/job/news/2024/12/16/backstage-review-2024/
CVE-2024-45815 CVE-2024-45816 CVE-2024-46976
Tim (Wadhwa-)Brown 
timb_machine@infosec.exchange
buherator
buheratorhttps://sam4k.com/linternals-exploring-the-mm-subsystem-part-1/
buherator
buheratorhttps://karmainsecurity.com/hacking-kerio-control-via-cve-2024-52875
Foone🏳️⚧️
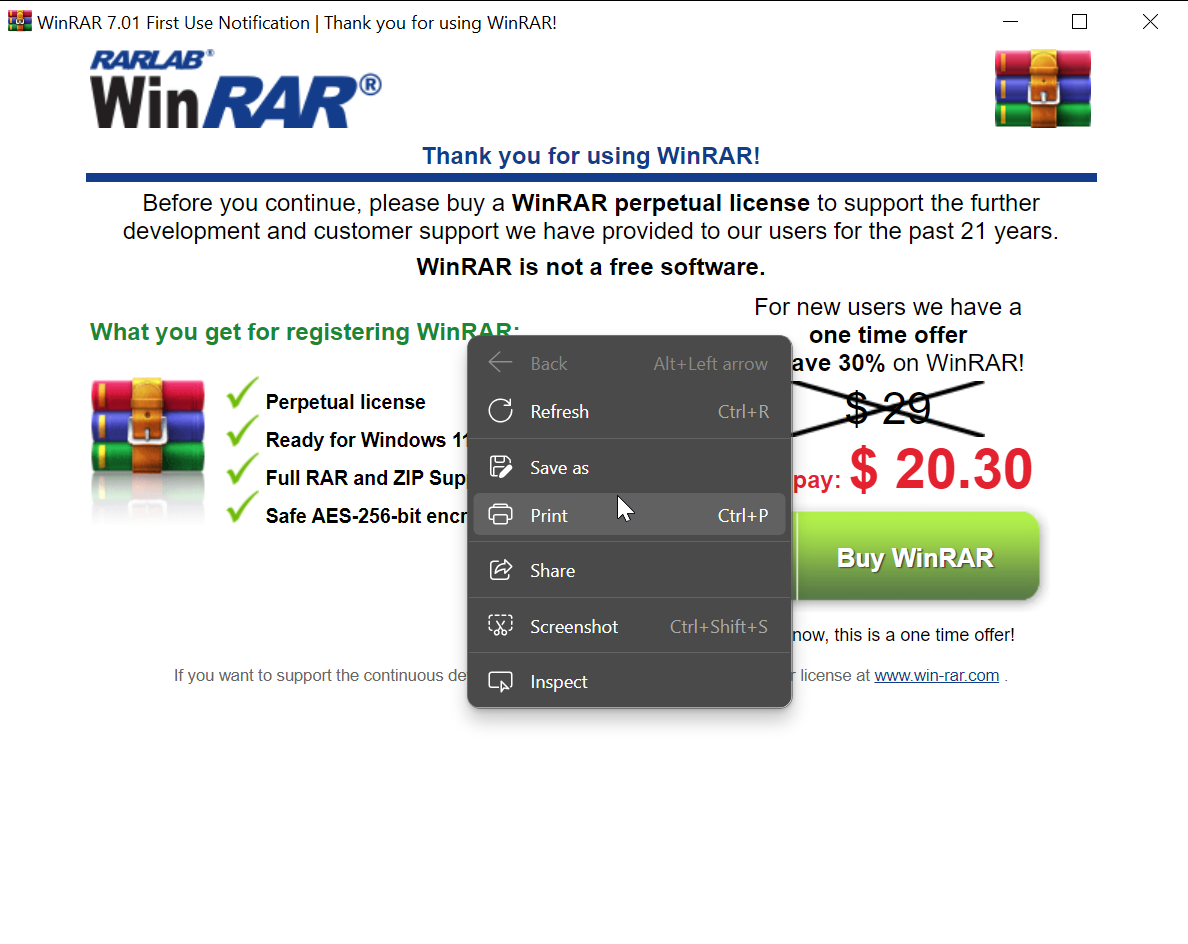
foone@digipres.clubFeel old yet? The winrar registration nag screen is Electron these days.
EDIT: Whoops, it seems I'm wrong: This is just an embedded webview, which on Win10 is apparently chromium-backed (probably because it's Edge)
Virtual Colossus
virtualcolossus@infosec.exchange#Polish researchers have discovered components of a German #Enigma cipher machine, crucial to the Nazi wartime communications system, on Sobieszewska island near the city of Gdańsk. All in all, 8 rotors and various other parts were recovered. https://tvpworld.com/84053156/fragments-of-rare-german-enigma-machine-unearthed-in-poland
buherator
buherator"[Person] will be the wall
that guides us through the night!"
buherator
buheratorhttps://www.ibm.com/support/pages/node/7179158
Emphasis mine:
"A user with authority to a *view* can alter the based-on *physical file* security attributes without having object management rights to the physical file."
I wonder what other discrepancies there may be between Db2 and other interfaces.
Stephen Rees-Carter 
valorin@phpc.social
One of the fun parts of doing my security audits is coming across unexpected code that looks exploitable, and trying it out myself to see what possibilities exist.
In a recent audit, I found myself asking... What if you hashed null?
https://securinglaravel.com/security-tip-what-if-you-hashed-null/
Prof. Emily M. Bender(she/her)
emilymbender@dair-community.socialCalling all Mystery AI Hype Theater 3000 fans! Have you found a piece of Fresh AI Hell but not known where to send it? Here's the spot:
https://thecon.ai/submit-fresh-ai-hell/
Help @alexhanna.bsky.social and me clean out the Fresh Hell by submitting it there!
💻📡🛰️ IooNag
IooNag@infosec.exchangeDevOps practices are all well and good, but beware of the configuration of the tools that access your production.
I've written a blog post sharing some dangerous ways Argo CD can be configured, detailing the security impact: https://ledger.com/argo-cd-security-misconfiguration-adventures