Posts
2717Following
681Followers
1506screaminggoat
screaminggoat@infosec.exchangeCISA: CISA Adds One Known Exploited Vulnerability to Catalog
Hot off the press! CVE-2024-51378 (perfect 10.0 critical 🥳 @cR0w) CyberPanel Incorrect Default Permissions Vulnerability
#cyberpanel #CVE #CVE_2024_51378 #cisa #kev #cisakev #knownexploitedvulnerabilitiescatalog #vulnerability #eitw #activeexploitation #infosec #cybersecurity
screaminggoat
screaminggoat@infosec.exchangeUnpatched and Exploited Zero-Days: Multiple vulnerabilities in I-O DATA routers UD-LT1 and UD-LT1/EX
Two different sets of researchers reported vulnerabilities in I-O DATA routers to JPCERT/CC.
- CVE-2024-45841 (6.5 medium) Incorrect Permission Assignment for Critical Resource
- CVE-2024-47133 (7.2 high) OS Command Injection
- CVE-2024-52564 (7.5 high) Inclusion of Undocumented Features
The developer states that attacks exploiting these vulnerabilities have been observed.
The developer states that the updates addressing these vulnerabilities (CVE-2024-45841, CVE-2024-47133) are planned to be released around December 18, 2024. Too early to speculate and no additional information provided.
cc: @cR0w @mttaggart @ntkramer @dreadpir8robots @neurovagrant @goatyell @metacurity (remember to remove the mentions to avoid ReplyAll madness)
#vulnerability #jpcertcc #cve #IODATA #eitw #activeexploitation #infosec #cybersecurity
Rust Language
rust@social.rust-lang.orgRust 1.83.0 has been released! 🦀✨
This release includes mutable references and pointers in const, references to statics in const, new `ErrorKind`s, and many new const methods on pointers, slices, floats, and more!
Check out the announcement: https://blog.rust-lang.org/2024/11/28/Rust-1.83.0.html
Taggart
mttaggart@infosec.exchangeDon't threaten me with a good time, Microsoft.
https://www.theregister.com/2024/12/04/microsoft_update_recall_bug/
buherator
buheratorhttps://bughunters.google.com/blog/6355265783201792/the-great-google-password-heist-15-years-of-hacking-passwords-to-test-our-security-and-build-team-culture
buherator
buheratorhttps://nastystereo.com/security/ruby-safe-marshal-escape.html
#Ruby
Andrea Barisani
lcars@infosec.exchangeExactly 11 (!) years ago we released an advisory for an rsync 0-day.
Two days earlier the Gentoo Linux mirror I was hosting and maintainig was compromised with it.
What a ride.
https://forums.gentoo.org/viewtopic.php?t=111779
https://lists.samba.org/archive/rsync-announce/2003/000011.html
bert hubert 🇺🇦🇪🇺🇺🇦
bert_hubert@fosstodon.orgMaybe fun to know - using #MS365 means that the US government has bulk access to your data, which matters if you are a government yourself. Supporters of Microsoft will tell you you can easily use "double key encryption" to protect your MS365 data against US government snooping. This is how easily you can do that. Hint, it involves GitHub and compiling code: https://learn.microsoft.com/en-us/purview/double-key-encryption-setup
DrWhax
drwhax@infosec.exchangeMy VirusBulletin presentation: A web of surveillance was uploaded to YouTube: https://www.youtube.com/watch?v=iERGg1dUVNE
buherator
buheratorhttps://www.404media.co/bluesky-posts-machine-learning-ai-datasets-hugging-face/
Surprise: you%27ve published them on the Internet.
buherator
buheratorhttps://therecord.media/stoli-group-usa-bankruptcy-filing-ransomware
Bastards!
buherator
buheratorhttps://devblogs.microsoft.com/oldnewthing/20241203-00/?p=110601
"It looks like the anti-malware software is interfering with our ability to debug the problem." :)
Caitlin Condon
catc0n@infosec.exchangeNew whitepaper and exploit code from @stephenfewer on 5 new vulnerabilities he chained to achieve unauthenticated RCE on Lorex 2K Indoor Wi-Fi security cameras. The exploit works in two phases and comprises an auth bypass, a stack-based buffer overflow, an out-of-bounds heap read, and a null pointer dereference — and that's just to start (because it was, like, Tuesday for Stephen or whatever) 📈
Clément Labro
itm4n@infosec.exchangeInterestingly enough, MS disabled the "Use my Windows user account" checkbox when connecting to Wi-Fi on the lock screen to address CVE-2024-38143 in the August Patch Tuesday.
This change completely remediates the "Airstrike" attack as well. 🤯
buherator
buheratorI guess I have to change my lifestyle a bit if I want to know the details...
(or hack some gov DB, which I would never ever do ofc!)
DNA Lounge Update, Wherein we negotiate with the mob
https://www.dnalounge.com/backstage/log/2024/12/03.html
The V Programming Language
vlang@mas.toThe Advent of Code for V has started, uncovering a new challenge every day! Check them out!
The V Programming Language
vlang@mas.toUnused functions are now skipped by default. This reduces generated C dramatically. Give it a try! if you have issues, use v -no-skip-unused ... and report them.
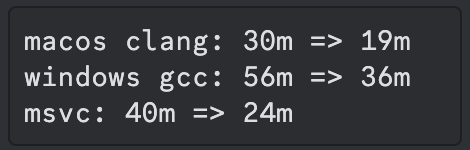
After making this option by default, CI times went down significantly: