Posts
2465Following
661Followers
1486Mr Bouba Bouba 🧄
bean@twoot.siteWhat the absolute fuck: https://yossarian.net/til/post/some-surprising-code-execution-sources-in-bash
In short: [[ "$foo" -eq whatever ]] in bash can run arbitrary code.
That looks like something that can realistically trigger in a lot of scripts.
(also test -v, but I barely ever see that one used)
Edit: This also happens in zsh 5.9 (but the referenced variable needs to exist) and mksh
Alexandre Borges
alexandreborges@infosec.exchangeLeveling Up Fuzzing: Finding more vulnerabilities with AI:
https://security.googleblog.com/2024/11/leveling-up-fuzzing-finding-more.html
#fuzzing #google #vulnerabilities #ai #informationsecurity #cybersecurity
cts🌸
gf_256@bird.makeupIt's 2024. People spend more time looking at screens than not-screens. People spend more time in limited wavelength artificial lighting than natural light. Rather than trying to describe "real life", we should just stick to RGB, as "real life" IS mostly just RGB now
Piotr Bazydło
chudypb@infosec.exchangeMy WarCon slides about Ivanti Avalanche are public!
I tried to do some mapping of the attack-surface, show the new auth mechanism and present some research ideas (things I didn't try).
It also shows my first-ever fuzzing and memory corruption experience😆
https://github.com/thezdi/presentations/blob/main/2024_WarCon/Avalanche_WarCon24.pdf
buherator
buheratorhttps://bughunters.google.com/blog/5085111480877056/finding-bugs-in-chrome-with-codeql
Rust Weekly 🦀
rust_discussions@mastodon.socialSafety in an Unsafe World - RustConf 2024 - How to move Rust beyond memory safety to guarantee freedom from any class of bugs
https://www.youtube.com/watch?v=Ba7fajt4l1M
Discussions: https://discu.eu/q/https://www.youtube.com/watch?v=Ba7fajt4l1M
buherator
buheratorhttps://cyberscoop.com/misconfigured-jupyter-notebooks-uefa-champions-league-streaming/
buherator
buheratorhttps://www.thezdi.com/blog/2024/11/18/looking-at-the-internals-of-the-kenwood-dmx958xr-ivi
buherator
buheratorhttps://binary.ninja/2024/11/20/4.2-frogstar.html
#ReverseEngineering
buherator
buheratorhttps://blog.includesecurity.com/2024/11/spelunking-in-comments-and-documentation-for-security-footguns/
#elixir #python #go
buherator
buheratorhttps://www.synacktiv.com/en/publications/relaying-kerberos-over-smb-using-krbrelayx
David Weston (DWIZZZLE)
dwizzzlemsft@bird.makeupMy team just released a paper detailing all the security capabilites in Windows Server 2025
https://techcommunity.microsoft.com/blog/microsoftsecurityandcompliance/windows-server-2025-security-book/4283981
@mikko
mikko@bird.makeupThank You to the guests who joined the opening of the Museum of Malware Art! The museum is now open to the public. For hours and more information, see https://MuseumofMalware.Art
Kim Scheinberg
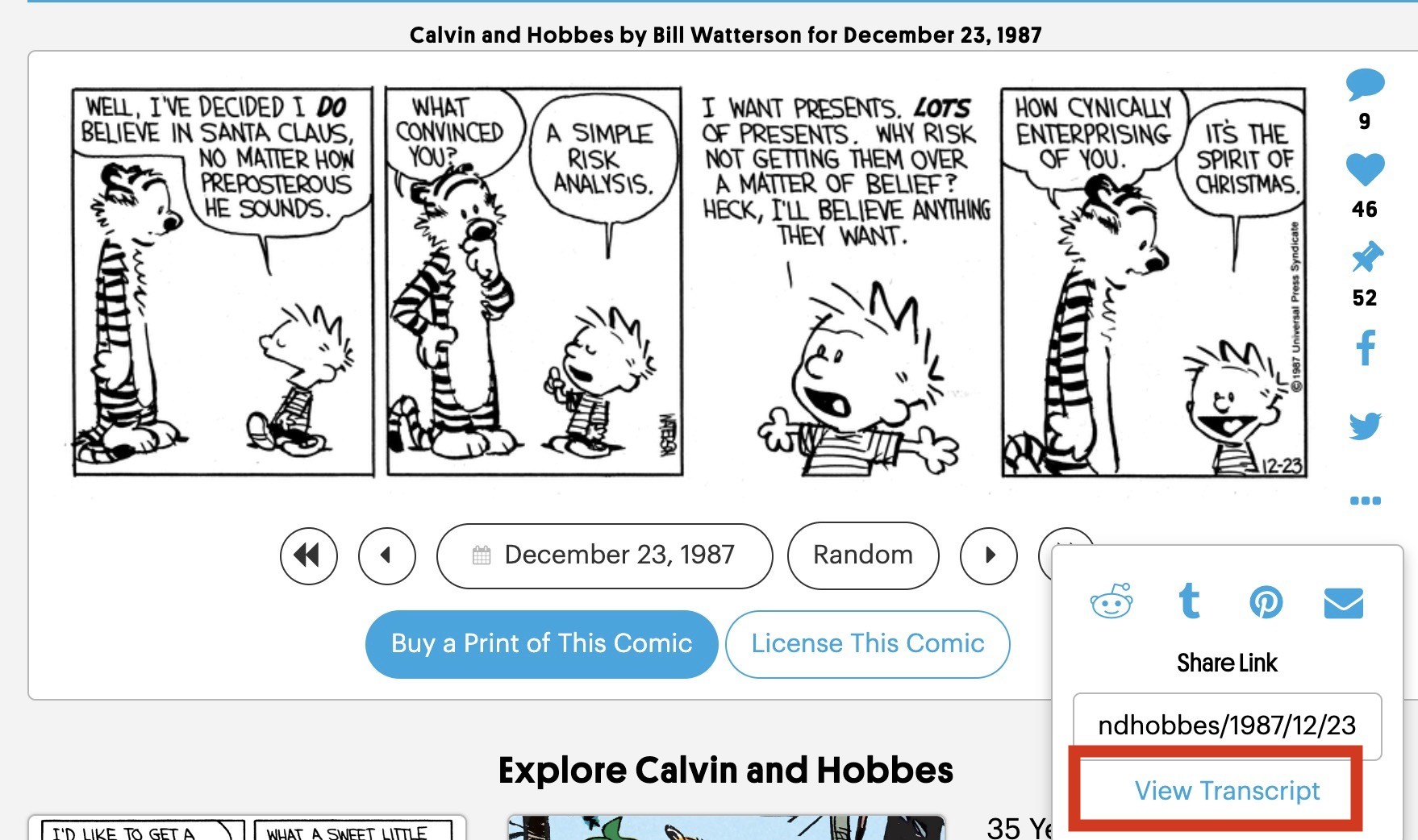
kims@mas.toSince Calvin and Hobbes are popular right now, please know that the entire archive is available online, searchable, for free. This includes ALL the strips, including some that didn't make it into the various anthologies:
https://www.gocomics.com/calvinandhobbes
And if you are insistent on using alt text but are (like me) sometimes not motivated to type out the dialogue, there's even a 'transcript' button in the three-dot submenu. It's short on describing images, but it's thorough on the text.
Alex Plaskett
alexjplaskett@bird.makeup✍️ A Ghidra nanoMIPS ISA module by @jamchamb_
https://www.nccgroup.com/us/research-blog/ghidra-nanomips-isa-module/
/r/netsec
_r_netsec@infosec.exchangeWormable XSS www.bing.com https://medium.com/@pedbap/wormable-xss-www-bing-com-7d7cb52e7a12
dragosr
dragosr@chaos.socialD-Link tells users to trash old VPN routers over bug too dangerous to identify.
Hopefully folks realize they should replace it with another vendor.
This vuln was covered at DEF CON 32 by Sam Curry. TR-069 is an admin access protocol that lets DLink work with your router remotely (reset device, etc.). Bad actors use spoofed requests to change config data, read the MAC address, monitor traffic, and use them as botnets. TR-069 is industry standard
https://www.theregister.com/2024/11/20/dlink_rip_replace_router/