Posts
2969Following
697Followers
1543buherator
buheratorhttps://devblogs.microsoft.com/oldnewthing/20241108-00/?p=110490
buherator
buheratorhttps://r00tkitsmm.github.io/fuzzing/2024/11/08/Pishi.html
Gammitin (Ben) 💾
Gammitin@mastodon.socialIBM's EGA graphics (Enhanced Graphics Adapter) celebrates it's 40th anniversary this year, so here's some classic EGA games:
codecolorist
codecolorist@infosec.exchangeOne tiny goal: learn to pronounce kurwa fluently before next Warcon
Molly White
molly0xfff@hachyderm.ioFor anyone looking to adjust their media diet, now’s a great time to consider escaping The Algorithms with RSS. Here are some of the blogs, newsletters, and independent news sites I follow: https://www.mollywhite.net/blogroll/
For feed readers, I use Inoreader, but there are many other good options.
Cheeseness
Cheeseness@mastodon.socialSupport the people who make the stuff you like. There's a good chance that without that, the stuff you like won't get made.
qwertyoruiopz
qwertyoruiop@nso.groupThe offensive industry loves making shit up: the new rumor making the rounds is that my girlfriend works at NSO. As a matter of fact, my girlfriend is currently unemployed and looking for work as an event manager in Europe, so let me know if you come across interesting openings. Her only experience in the security industry is coming with me to a few conferences over the past year to look for work and learn more about this niche.
cpresser
cccpresser@chaos.socialHere is another #NameThatWare
Can you deduct or guess which device this is?
As always, hide your answer behind a CW to not spoil others.
buherator
buherator/cc @reverseics @cR0w
buherator
buheratorhttps://video.infosec.exchange/w/jtR1V9N5ghHES5oayeBrrd
Did I miss anything?
#NoCVE
buherator
buheratorShow content
https://blog.mollywhite.net/binance-script/
buherator
buheratorhttps://www.youtube.com/watch?v=dnHdqPBrtH8
Again, it's all about incentives...
Christopher
kharosx0@bird.makeupKASAN is now available for your own Windows Drivers: https://learn.microsoft.com/en-us/windows-hardware/drivers/devtest/kasan
Oh God, yes! When starting a qemu instance, you can pass it an fd on the command line for its listening socket for that chardev.
You can also tell it to listen on a TCP or UNIX socket, but as the starting process, you now need to try and connect multiple times until qemu is finally started and opened its listening socket. It also might never connect in case qemu fails to start. This is really annoying to handle properly in your code.
With the fd-passing, the parent process can create the listening socket, clear CLOEXEC on the socket, pass it to qemu and then connect to it. At that time it will either be open already or if qemu fails to start, the listening socket will be gone and the connect() fails.
I haven't tried it yet, but I need it for work and it sounds like a proper solution to a really annoying problem.
https://patchwork.kernel.org/project/qemu-devel/patch/20180205152455.12088-10-berrange@redhat.com/
leyrer
leyrer@chaos.socialUnattended children get an IBM System/370 and a Cobol starter lecture.
buherator
buheratorhttps://www.youtube.com/watch?v=piJkuavhV50
#Math
Ivan Ožić Bebek
obivan@infosec.exchangeWindows DWM Core Library Elevation of Privilege Vulnerability (CVE-2024-30051) https://www.coresecurity.com/core-labs/articles/windows-dwm-core-library-elevation-privilege-vulnerability-cve-2024-30051
Binary Ninja
binaryninja@infosec.exchangeWant to know more about the reverse engineering community? Šárka and Brent break down the 2024 results from our annual Reverse Engineering Survey in our latest blog post:
jiska 🦄
jiska@chaos.social
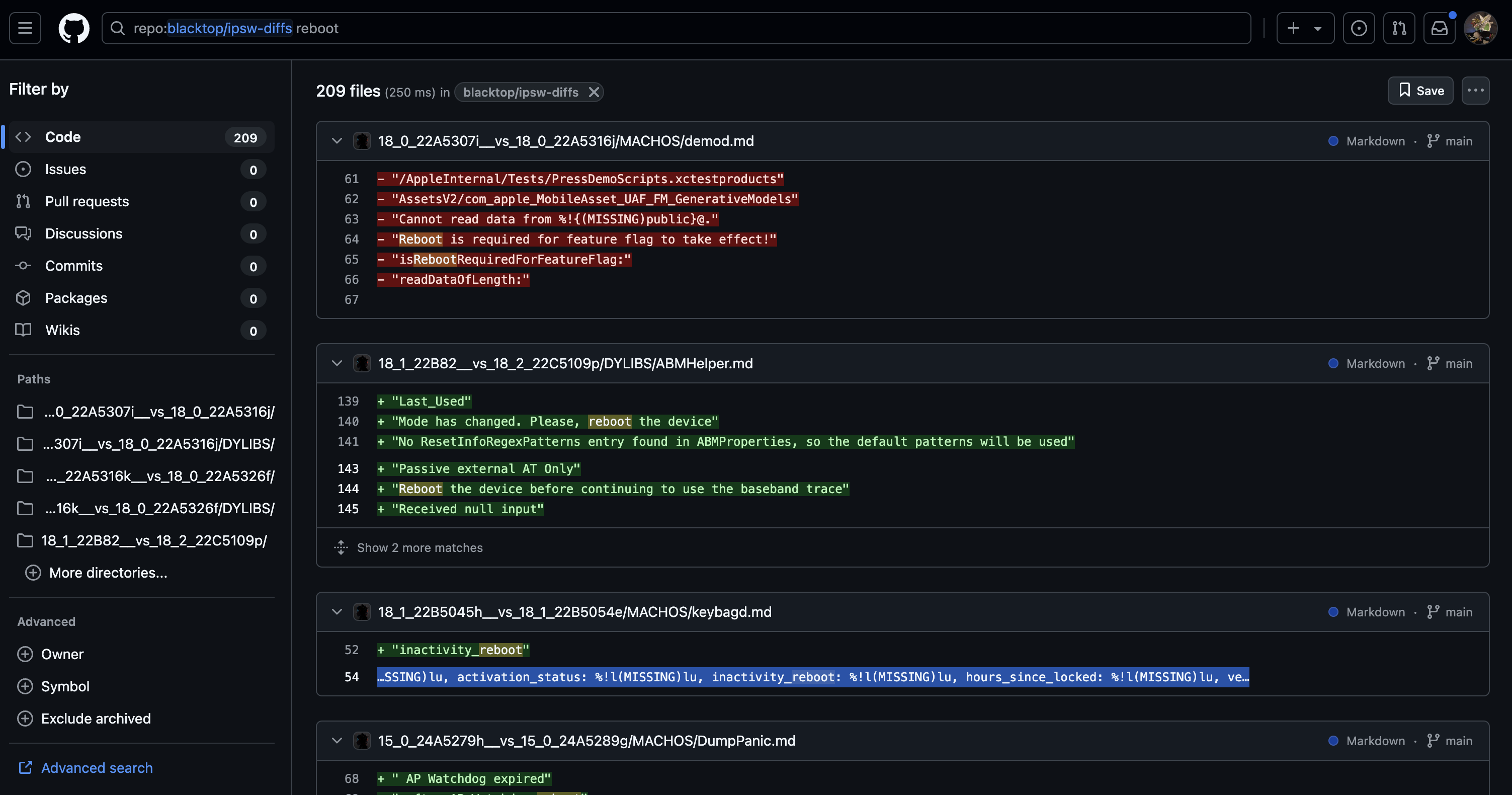
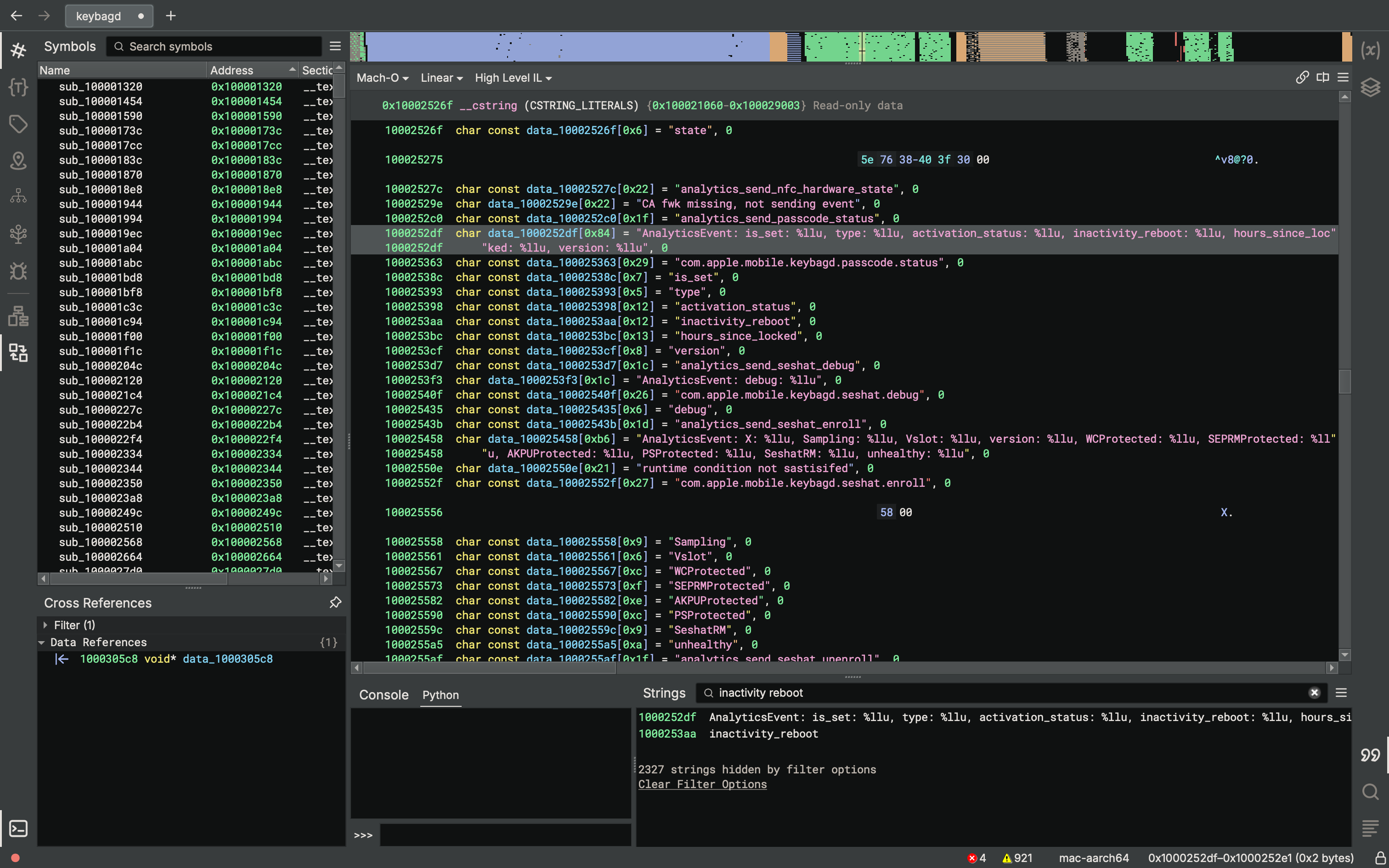
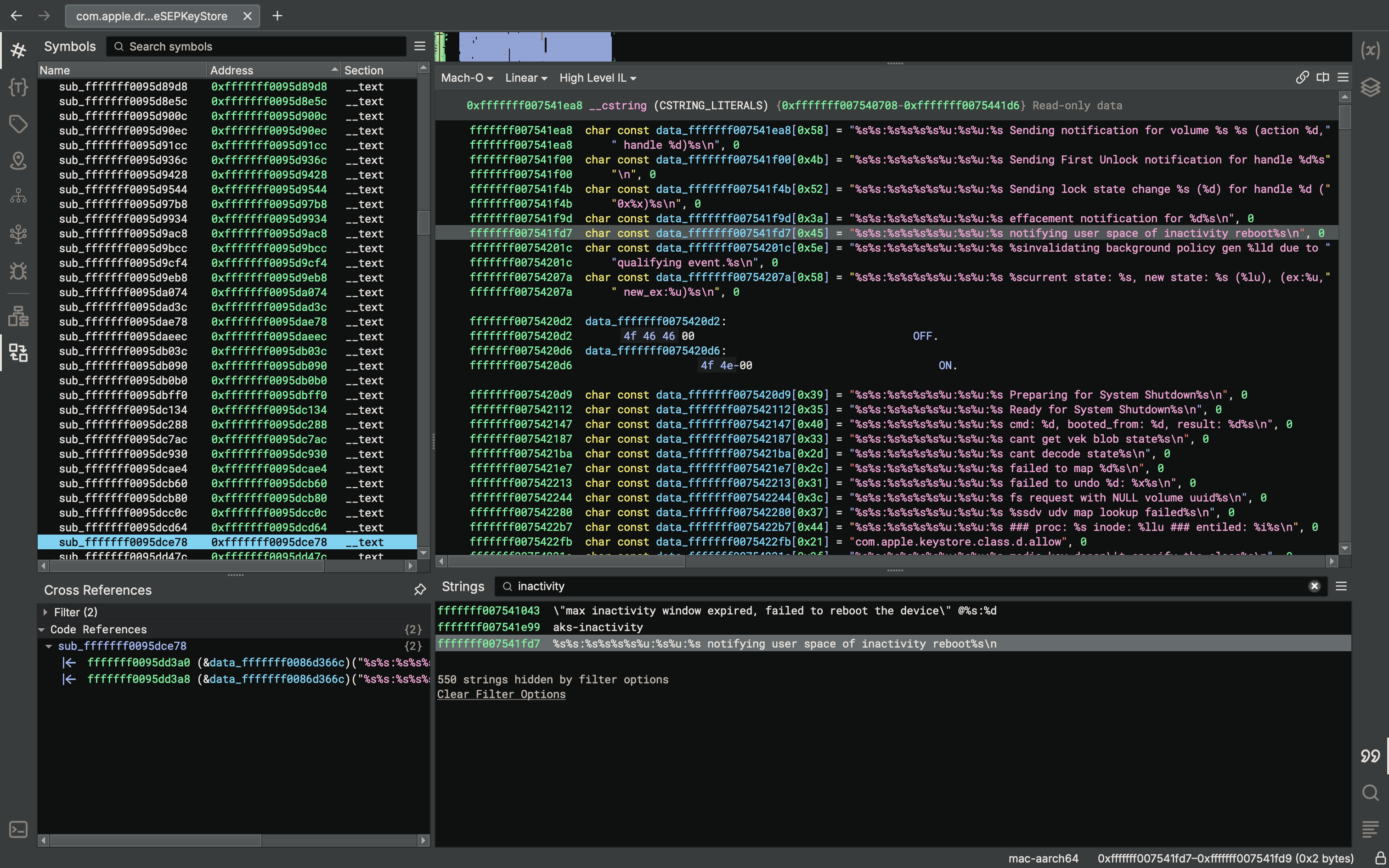
Apple added a feature called "inactivity reboot" in iOS 18.1. This is implemented in keybagd and the AppleSEPKeyStore kernel extension. It seems to have nothing to do with phone/wireless network state. Keystore is used when unlocking the device. So if you don't unlock your iPhone for a while... it will reboot!
In the news: "Police Freak Out at iPhones Mysteriously Rebooting Themselves, Locking Cops Out"
https://www.404media.co/police-freak-out-at-iphones-mysteriously-rebooting-themselves-locking-cops-out/
iOS version diffs to see yourself:
https://github.com/search?q=repo%3Ablacktop%2Fipsw-diffs%20inactivity_reboot&type=code
Csaba Fitzl
theevilbit@mastodon.social🍎🐛🎙️Following my #poc2024 talk we are releasing a blogpost series at Kandji, detailing the vulnerabilities of diskarbitrationd and storagekitd I discussed in my "Apple Disk-O Party" talk.
First part is out, and covers CVE-2024-44175.