Posts
3311Following
710Followers
1574Binary Ninja
binaryninja@infosec.exchangeWant to know more about the reverse engineering community? Šárka and Brent break down the 2024 results from our annual Reverse Engineering Survey in our latest blog post:
jiska 🦄
jiska@chaos.social
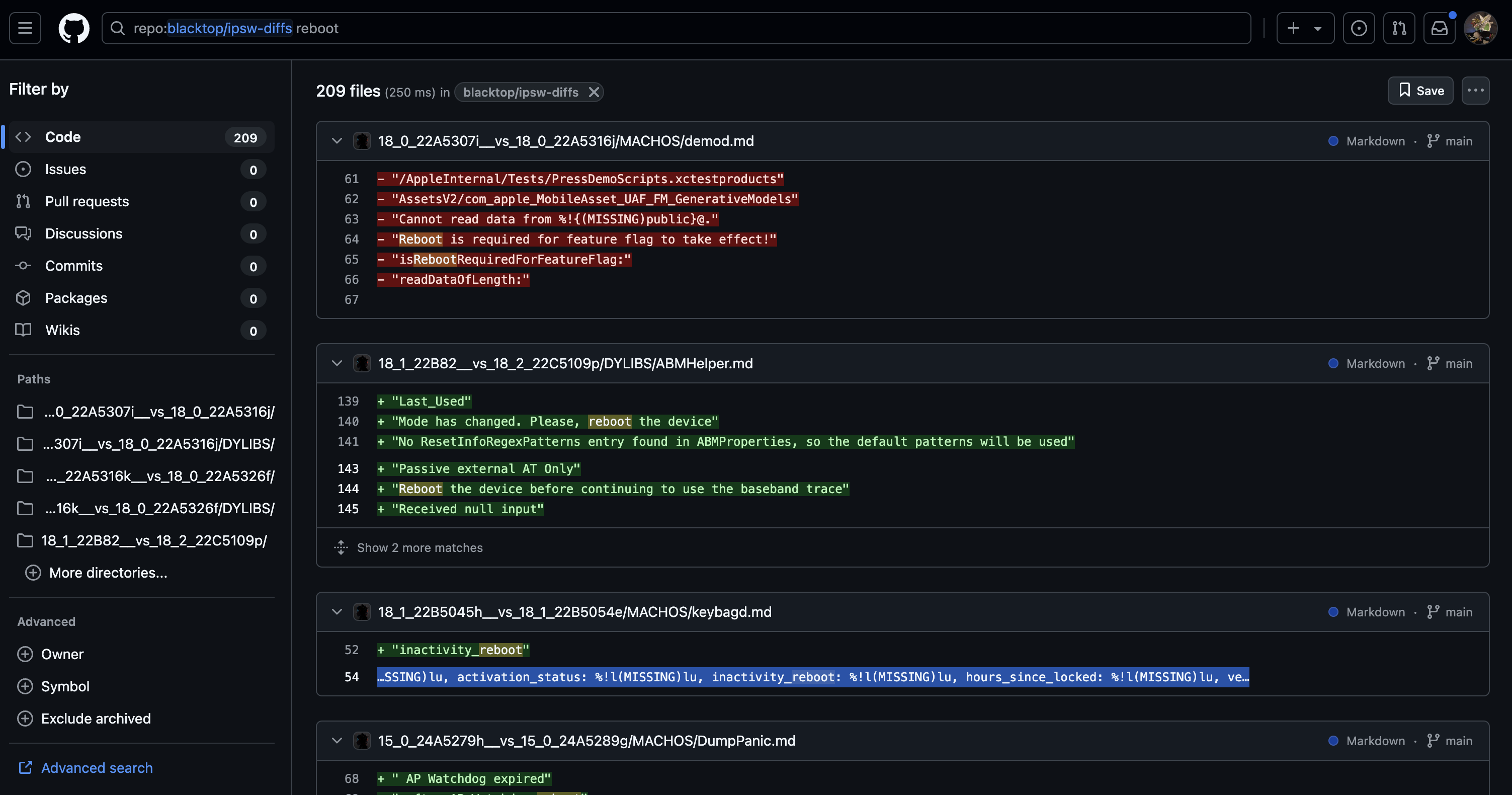
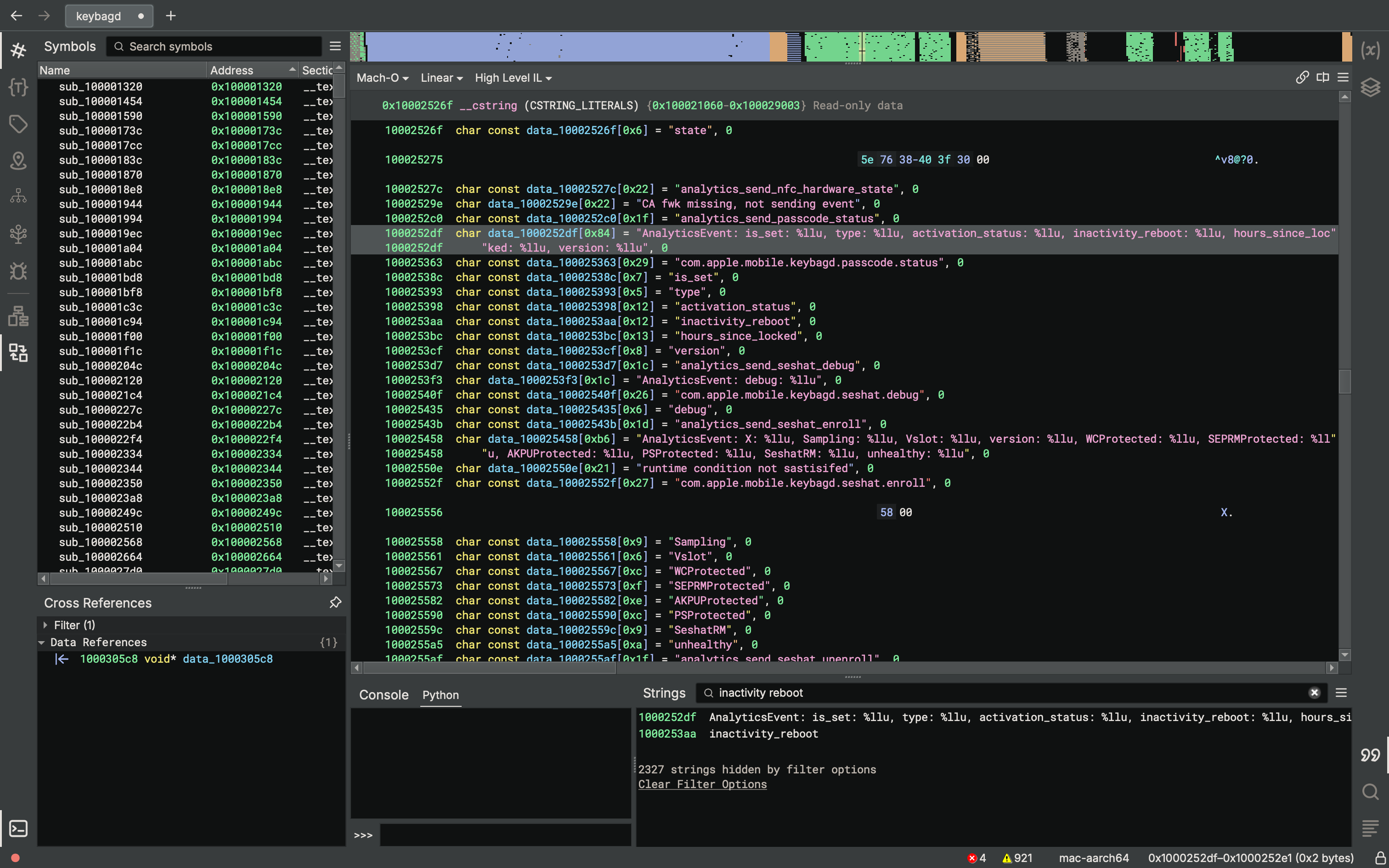
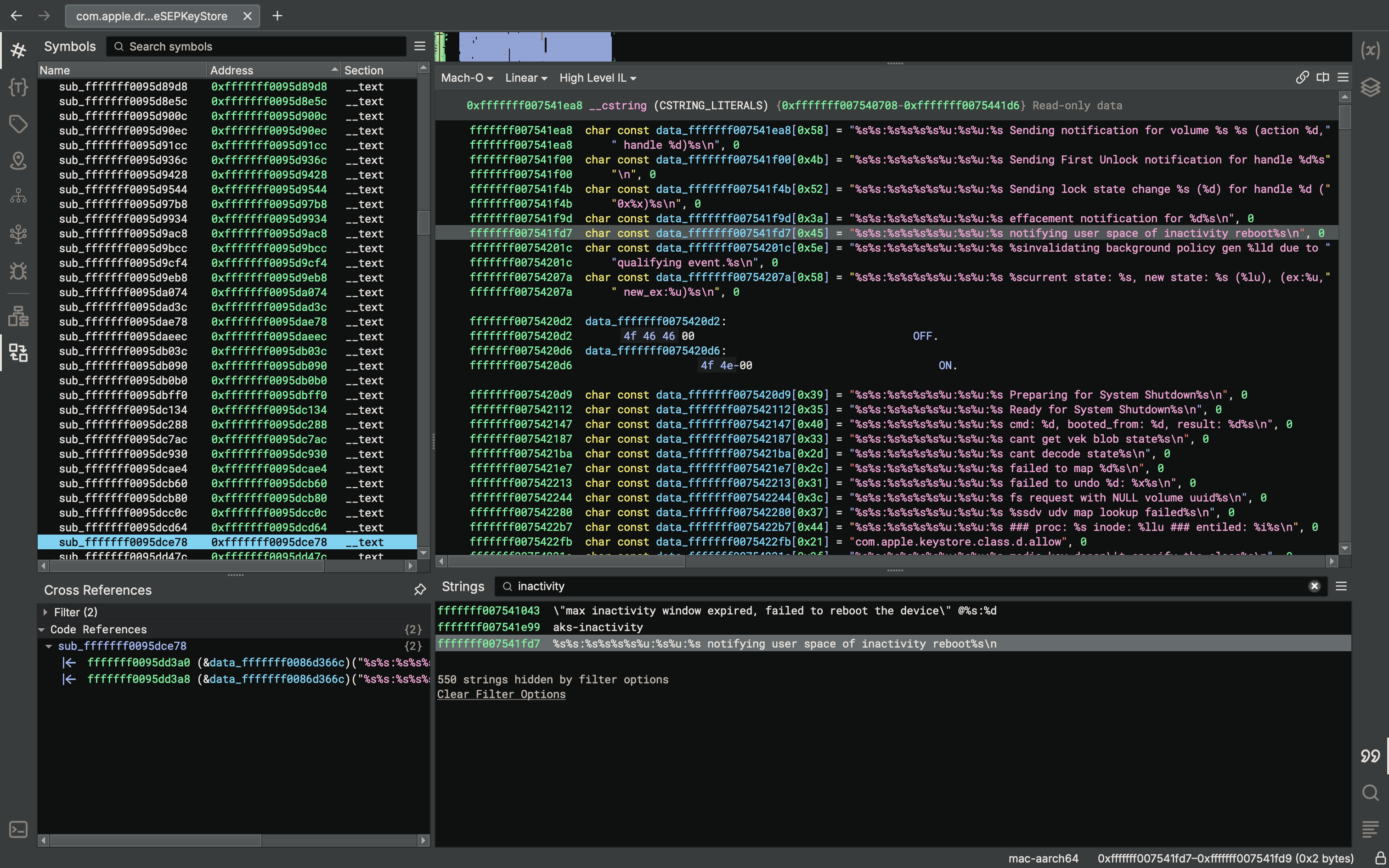
Apple added a feature called "inactivity reboot" in iOS 18.1. This is implemented in keybagd and the AppleSEPKeyStore kernel extension. It seems to have nothing to do with phone/wireless network state. Keystore is used when unlocking the device. So if you don't unlock your iPhone for a while... it will reboot!
In the news: "Police Freak Out at iPhones Mysteriously Rebooting Themselves, Locking Cops Out"
https://www.404media.co/police-freak-out-at-iphones-mysteriously-rebooting-themselves-locking-cops-out/
iOS version diffs to see yourself:
https://github.com/search?q=repo%3Ablacktop%2Fipsw-diffs%20inactivity_reboot&type=code
Csaba Fitzl
theevilbit@mastodon.social🍎🐛🎙️Following my #poc2024 talk we are releasing a blogpost series at Kandji, detailing the vulnerabilities of diskarbitrationd and storagekitd I discussed in my "Apple Disk-O Party" talk.
First part is out, and covers CVE-2024-44175.
screaminggoat
screaminggoat@infosec.exchangeVeeam security advisory from 06 November 2024 Veeam Backup Enterprise Manager Vulnerability (CVE-2024-40715)
CVE-2024-40715 (7.7 high) Veeam Backup & Replication Enterprise Manager authentication bypass. No mention of exploitation.
#cybersecurity #infosec #vulnerability #CVE #veeam #cve_2024_40715
The contrast between two CUPS vulns is amazing. This one, CVE-2024-35235, seems to have flown completely under the radar - in total contrast to CVE-2024-47176. It was an LPE with an exploit chain that sounds very reliable. I only heard about it for the first time today.
Sonar Research
SonarResearch@infosec.exchangeIn case you missed it, here's the recording of our #HEXACON2024 talk "Exploiting File Writes in Hardened Environments"!
It's a short and sweet 30-minute talk, so grab a coffee and sit back while @scryh goes from HTTP request to ROP chain in Node.js ☕
screaminggoat
screaminggoat@infosec.exchangePalo Alto Networks Security Advisory: PAN-SA-2024-0015 Important Informational Bulletin: Ensure Access to Management Interface is Secured
Palo Alto Networks is aware of a claim of a remote code execution vulnerability via the PAN-OS management interface. They do not know the specifics of the claimed vulnerability.
We strongly recommend customers to ensure access to your management interface is configured correctly in accordance with our recommended best practice deployment guidelines. In particular, we recommend that you ensure that access to the management interface is possible only from trusted internal IPs and not from the Internet. The vast majority of firewalls already follow this Palo Alto Networks and industry best practice.
#vulnerability #paloaltonetworks #paloalto #pan #panos #cybersecurity #infosec
Yarden Shafir
yarden_shafir@bird.makeupPlease make this happen. I would love nothing more than to have an image parser run during a bugcheck
buherator
buheratorhttps://jericho.blog/2024/11/07/was-it-really-gpac-no-getting-a-cve-removed-from-cisa-kev/
buherator
buheratorhttps://www.usenix.org/conference/woot24/presentation/brossard
%27In this article, we introduce the notions of "libification" and "procedural debugging" to facilitate partial debugging of binaries at the procedural level. These techniques allow the transformation of arbitrary dynamically linked ELF binaries into shared libraries, and the study of memory corruption bugs by directly calling the vulnerable functions, hence separating the memory corruption intraprocedural analysis from the reachability problem. %27
buherator
buheratorhttps://github.com/kagisearch/bangs/pull/125
buherator
buheratorAny clues?
bert hubert 🇺🇦🇪🇺🇺🇦
bert_hubert@fosstodon.orgIf as it appears likely that 🇪🇺will have to start defending itself against Russia 🇷🇺 alone it may be good to realize our IT systems and society aren’t remotely ready for that. https://berthub.eu/articles/posts/cyber-security-pre-war-reality-check/
Binary Gecko
binary_gecko@bird.makeupEkoparty 2024 Binary Gecko Challenge 🇦🇷
Complete the challenge to get a ticket to our VIP dinner/party event in Buenos Aires during the conference.
Winners will also get an interview for a Security Researcher position at Binary Gecko.
buherator
buheratorhttps://s1r1us.ninja/posts/electron-contextbridge-is-insecure/
/via exploits.club
buherator
buheratorhttps://github.com/binarly-io/idalib
/via exploits.club