Posts
3083Following
704Followers
1551Tony Arcieri🌹🦀
bascule@mas.toPretty much all versions of bcrypt are vulnerable to second preimage attacks because they truncate the input to the first 72 bytes, meaning the hashes for messages longer than that will collide.
This resulted in a login bypass against Okta.
https://www.theverge.com/2024/11/1/24285874/okta-52-character-login-password-authentication-bypass
SSD Secure Disclosure
SSDSecureDisclosure@infosec.exchange🌪️Heads up speakers: Our 2025 Call for Papers is now open!
Be part of the best all-offensive security conference in Asia!
Submit your talk today at: https://typhooncon.com/call-for-papers-2025/
hikari 🌟 (fell out of the sky)
hikari@social.noyu.meoh my god you literally can't log into DigitalOcean if fonts.googleapis.com is down or (in my case) null-routed. the site literally won't load. they have made the font CSS part of the critical path with no fallback. this is horrendous
Joxean Koret (@matalaz)
joxean@mastodon.socialThis paper looks promising: "SIGMADIFF: Semantics-Aware Deep Graph Matching for Pseudocode Diffing".
https://ink.library.smu.edu.sg/cgi/viewcontent.cgi?article=9671&context=sis_research
buherator
buheratorKees Cook (old account)
kees@fosstodon.org~25M lines of code in the Linux kernel drivers/ directory. O_O
~15M LoC for everything else.
Johnathan Norman
spoofyroot@bird.makeupHello everyone, fun fact, UAC bypasses = bounty money when Administrator Protection is enabled. We checked many but we fully expect we missed some. You could simply dig up old research, try it and if it works make some cash. This feature is in an early stage, help us improve it.
buherator
buheratorhttps://googleprojectzero.blogspot.com/2024/10/from-naptime-to-big-sleep.html
"we want to reiterate that these are highly experimental results. The position of the Big Sleep team is that at present, it%27s likely that a target-specific fuzzer would be at least as effective (at finding vulnerabilities). " (still wow!)
buherator
buheratorhttps://blog.trailofbits.com/2024/10/31/fuzzing-between-the-lines-in-popular-barcode-software/
Csepp 🌢
csepp@merveilles.townhttps://netboot.xyz/ is really cool, just used it to install Debian for a relative. 
cc #netbootxyz #theWorkshop
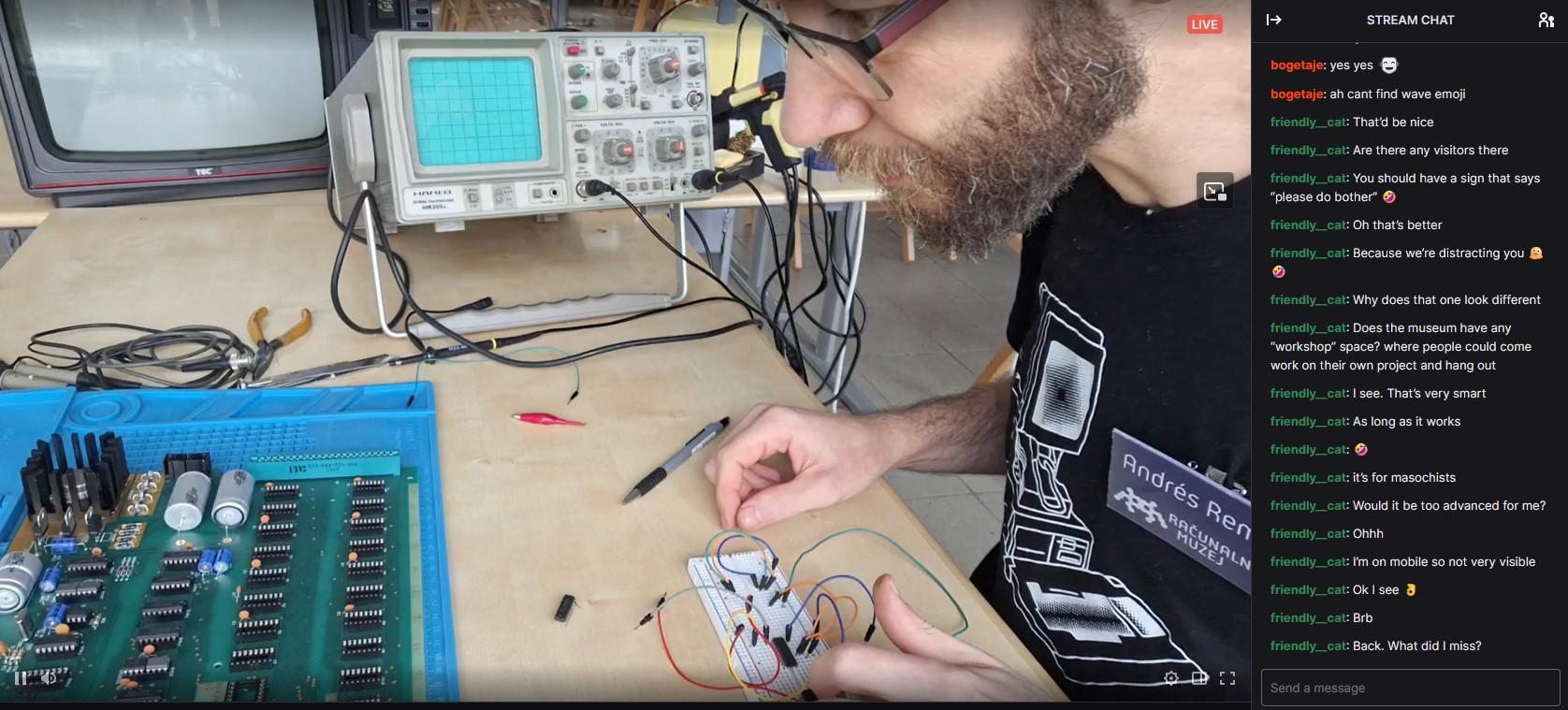
Computer History Museum 🇸🇮
muzej@mastodon.socialWe're live! Join us for a stream as we build an Apple I replica! 🛠️✨ https://www.twitch.tv/racunalniskimuzej
#computermuseum #computerhistory #slovenia #ljubljana #softwareheritage #digitalheritage #nostalgia #applei #museo #retrocomputing #Twitch #livestream #vintagecomputing #stream #SmallStreamers #applenerd #apple #streaming #live #twitchstreamer #apple1 #retrogaming #informatica
Adrian Taylor
adetaylor@mastodon.online2024 Q3 update from #googlechrome security https://www.chromium.org/Home/chromium-security/quarterly-updates/#q3-2024
Kevin Beaumont
GossiTheDog@cyberplace.socialRemember a few weeks ago when Okta dropped a critical auth bypass vuln they’d been aware of for weeks on a Friday at 11pm?
Well, they’re back again with another auth bypass dropped on a Friday at 11pm https://infosec.exchange/@SecureOwl/113409933398662230
Chris Merkel 🐀👨🏼🍳
chrismerkel@infosec.exchangeNot sure I want to open this. If Cobalt Strike had a scent, what would it be and why?
buherator
buherator"This is an overview of CVE-2024-29506, CVE-2024-29507, CVE-2024-29508, and CVE-2024-29509"
https://codeanlabs.com/blog/research/ghostscript-wrap-up-overflowing-buffers/
buherator
buheratorhttps://www.cyberark.com/resources/threat-research-blog/discovering-hidden-vulnerabilities-in-portainer-with-codeql
Wendy Nather
wendynather@infosec.exchangeAs you know, I've been talking about the #SecurityPovertyLine for over ten years now, and I'm always learning new things that add to my thinking on it. In my work with the National Academy of Sciences committee on cyber hard problems, I got to hear a presentation from @fuzztech that really opened my eyes.
It seems that US law enforcement is also below the security poverty line. Really. They struggle with protecting their own infrastructure (which includes huge amounts of digital data that now has to be stored as evidence for, like, forever -- as innocent people are still being exonerated decades later), and they also struggle with being able to help victims of cyber-enabled crime.
This presentation (which starts at 4:20 in the video) is open to the public, and I believe it needs more attention, as this problem affects not only SMBs, but also the very fabric of society. Have a look:
buherator
buheratorhttps://seclists.org/fulldisclosure/2024/Oct/18

 🌻
🌻 
