Posts
2965Following
697Followers
1542Trend Zero Day Initiative
thezdi@infosec.exchangeThe draw is complete and now the schedule is out! You can check out the full schedule showing all four days of #Pwn2Own Ireland madness at https://www.zerodayinitiative.com/blog/2024/10/22/pwn2own-ireland-the-full-schedule #P2OIreland
Joseph Cox
josephcox@infosec.exchangeHere is my recent DEF CON talk on Anom, the encrypted phone secretly ran by the FBI. All about the phone, the network, how Anom was structured, who used it, what this means for Signal, Telegram, more https://www.youtube.com/watch?v=uFyk5UOyNqI
Project Zero Bot
p0botLinux: temporarily dangling PFN mapping on remap_pfn_range() failure in usbdev_mmap() (and elsewhere?)
https://project-zero.issues.chromium.org/issues/366053091
CVE-2024-47674
Mark Morowczynski
markmorow@infosec.exchangeThe next blog post in the Active Directory hardening series just posted, focusing on SMB signing. https://techcommunity.microsoft.com/t5/core-infrastructure-and-security/active-directory-hardening-series-part-6-enforcing-smb-signing/ba-p/4272168. You can do this yourself and it makes a difference.
pancake 
pancake@infosec.exchange
We can finally run Doom in Quake! https://www.youtube.com/watch?v=tVOYmYUWkmE #doom
Trend Zero Day Initiative
thezdi@infosec.exchangeNow that the drawing is complete, @TheDustinChilds and Zed have a few thoughts about the upcoming #Pwn2Own Ireland contest. https://youtube.com/shorts/6l3BW94xH8E #P2OIrleand
buherator
buheratorhttp://blog.quarkslab.com/attacking-the-samsung-galaxy-a-boot-chain.html
buherator
buheratorhttp://blog.quarkslab.com/linux-kernel-instrumentation-from-qemu-and-gdb.html
buherator
buheratorhttps://devblogs.microsoft.com/oldnewthing/20241017-00/?p=110380
buherator
buheratorhttps://www.mayhem.security/blog/cve-2024-28578-test-third-party-image-libraries-with-mayhem
Kagi HQ
kagihq@mastodon.socialBy default, Kagi Image Search downranks images from websites with a high proportion of AI-generated content.
You can also use the AI images filter to completely exclude websites with AI-generated images from your image search results.
More info: https://help.kagi.com/kagi/features/exclude-ai-images.html
bitsavers.org
bitsavers@oldbytes.spaceSomehow, I don't think that 2024's richest man in the world, who also is an immigrant, would ever think of using his money to create something like this.
https://www.npr.org/2013/08/01/207272849/how-andrew-carnegie-turned-his-fortune-into-a-library-legacy
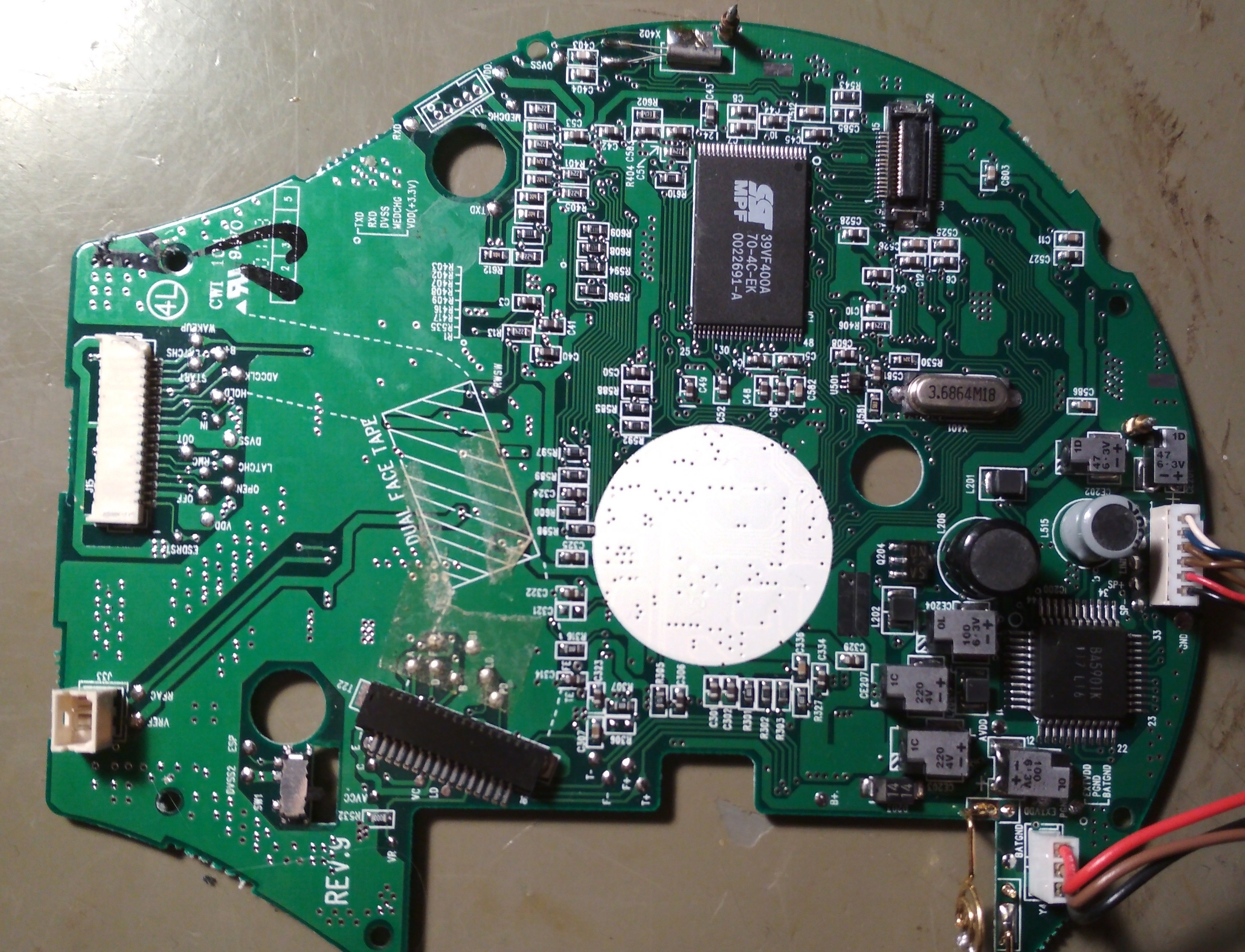
cpresser
cccpresser@chaos.socialCurrently trying to repair this device. Can you deduct or guess what it is? #NameThatWare
As always, hide your replies behind a CW to not spoil others.
buherator
buheratorhttps://digitalmarketreports.com/news/25091/microsoft-recall-feature-on-windows-11-not-removable-after-all/
[1] https://infosec.place/notice/AieooVB1w6sCv45MFE
Florian Magin
0x464d@bird.makeupTired of using outdated languages for #Ghidra scripting or a REPL that you can't even properly paste into? @tmr232 and I wrote a plugin to embed a #Jupyter #Kotlin kernel for a full Notebook environment alongside your GUI.
https://github.com/GhidraJupyter/ghidra-jupyter-kotlin
cyberresearch
cyberresearch@infosec.exchangeInternet Archive breached again through exposed access tokens https://www.bleepingcomputer.com/news/security/internet-archive-breached-again-through-exposed-access-tokens/?utm_source=dlvr.it&utm_medium=mastodon ( :-{ı▓
Paul Cantrell
inthehands@hachyderm.ioI’m a software developer with a bunch of industry experience. I’m also a comp sci professor, and whenever a CS alum working in industry comes to talk to the students, I always like to ask, “What do you wish you’d taken more of in college?”
Almost without exception, they answer, “Writing.”
One of them said, “I do more writing at Google now than I did when I was in college.”
I am therefore begging, begging you to listen to @stephstephking: https://mstdn.social/@stephstephking/113336270193370876