Posts
2956Following
697Followers
1541bitsavers.org
bitsavers@oldbytes.spaceSomehow, I don't think that 2024's richest man in the world, who also is an immigrant, would ever think of using his money to create something like this.
https://www.npr.org/2013/08/01/207272849/how-andrew-carnegie-turned-his-fortune-into-a-library-legacy
cpresser
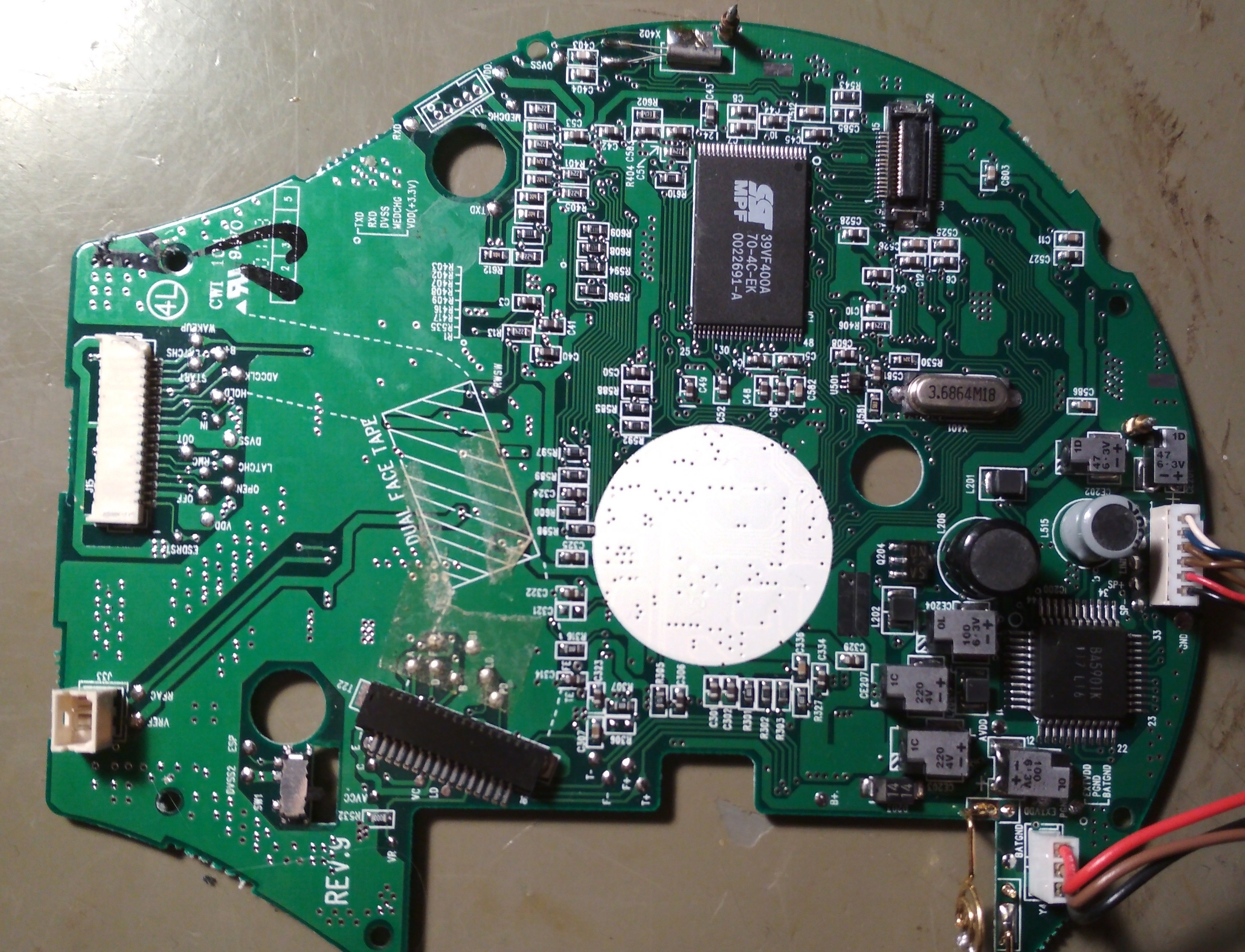
cccpresser@chaos.socialCurrently trying to repair this device. Can you deduct or guess what it is? #NameThatWare
As always, hide your replies behind a CW to not spoil others.
buherator
buheratorhttps://digitalmarketreports.com/news/25091/microsoft-recall-feature-on-windows-11-not-removable-after-all/
[1] https://infosec.place/notice/AieooVB1w6sCv45MFE
Florian Magin
0x464d@bird.makeupTired of using outdated languages for #Ghidra scripting or a REPL that you can't even properly paste into? @tmr232 and I wrote a plugin to embed a #Jupyter #Kotlin kernel for a full Notebook environment alongside your GUI.
https://github.com/GhidraJupyter/ghidra-jupyter-kotlin
cyberresearch
cyberresearch@infosec.exchangeInternet Archive breached again through exposed access tokens https://www.bleepingcomputer.com/news/security/internet-archive-breached-again-through-exposed-access-tokens/?utm_source=dlvr.it&utm_medium=mastodon ( :-{ı▓
Paul Cantrell
inthehands@hachyderm.ioI’m a software developer with a bunch of industry experience. I’m also a comp sci professor, and whenever a CS alum working in industry comes to talk to the students, I always like to ask, “What do you wish you’d taken more of in college?”
Almost without exception, they answer, “Writing.”
One of them said, “I do more writing at Google now than I did when I was in college.”
I am therefore begging, begging you to listen to @stephstephking: https://mstdn.social/@stephstephking/113336270193370876
buherator
buheratorrat (determined empirically)
rolenthedeep@rattodon.nexusIt's interesting to think that "my browser doesn't work with this website" used to mean "my browser is out of date". Now it means "someone intentionally broke this website for my browser because it supports ad blocking"
Extinction Rebellion Global
ExtinctionR@social.rebellion.globalgrsecurity
grsecurity@infosec.exchangeIn combination with the research published yesterday by ETHZ into IBPB implementation vulnerabilities on some Intel and AMD CPUs (https://comsec.ethz.ch/research/microarch/breaking-the-barrier/), Johannes Wikner has published a detailed walkthrough of the first cross-process Spectre exploit against a real target, an attack he developed in part during his internship with us last year.
Check it out here: https://grsecurity.net/cross_process_spectre_exploitation
johannes
wiknerj@bird.makeupThe first ever end-to-end cross-process Spectre exploit? I worked on this during an internship with @grsecurity! An in-depth write-up here:
https://grsecurity.net/cross_process_spectre_exploitation
Oxide Computer Company
oxidecomputer@hachyderm.ioWe're excited to announce dtrace.conf(24), the premier unconference for all things DTrace! 🎉
📅 Date: December 11th, 2024
📍 Location: Emeryville, CA
As an unconference, the agenda is driven by attendees. Come ready to actively participate!
Tim Clevenger 
timjclevenger@infosec.exchange
Free System/36 in SoCal. Today only. Please repost. #retrocomputing
HackSys Team
hacksysteam@bird.makeup🚨 We're hiring! 🚨
HackSys Inc. is looking for a full-time Vulnerability Researcher (Windows/Android/Browser) based in India! 🛡️
🔍 Skills:
- Vulnerability classes, C/C++/ASM
- Exploited n-day on Windows/Android/Browser
- Reverse Engineering (WinDbg, IDA, Ghidra)
- Passionate about VR 🔥
Interested? DM @hacksysteam on Discord or Twitter for more details! #Hiring #VulnerabilityResearch #CyberSecurity
abadidea
0xabad1dea@infosec.exchangeAs much as I've been inconvenienced by the Internet Archive being offline this long, I'm proud of them for making up their minds to just keep it down for as long as it takes to make sure everything's fixed and safe before exposing it again. I hope everyone involved is putting in reasonable hours and getting enough sleep.