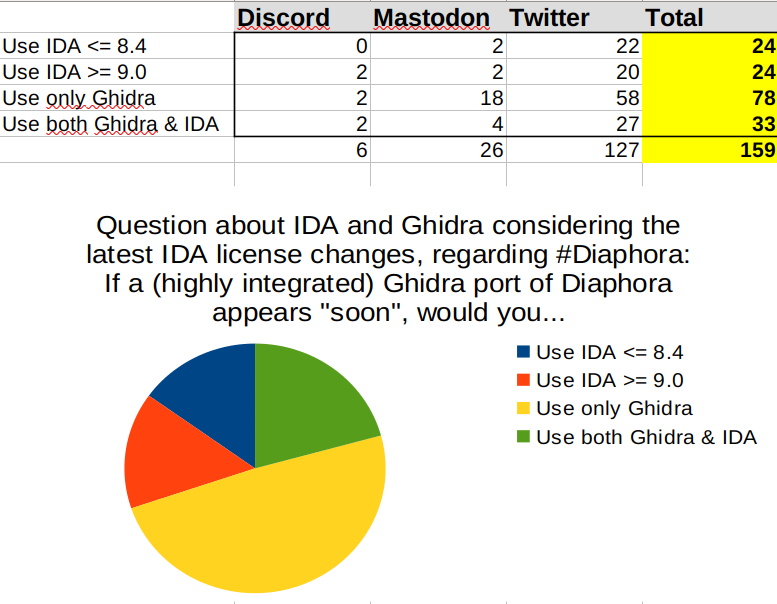
Posts
2459Following
556Followers
1265Heretek of Silent Signal
nixCraft 🐧
nixCraft@mastodon.socialAn attacker was able to achieve code execution in the content process by exploiting a use-after-free in Animation timelines. We have had reports of this vulnerability being exploited in the wild. Update your Firefox ASAP https://www.mozilla.org/en-US/security/advisories/mfsa2024-51/ #infosec #security
buherator
buheratorSomehow I didn't feel the same sense of pride with LinkedIn :)
David Meyer
dmm@mathstodon.xyzEinstein's revolutionary paper describing the equivalence of matter and energy, "Does the Inertia of a Body Depend upon its Energy-Content?", arrived at the editorial offices of the journal "Annalen der Physik" #onthisday in 1905 [1,2].
Interestingly, in Einstein’s first derivation of his famous result he did not express it with the equation E = mc². Instead, Einstein concluded that if an object, which is at rest relative to an inertial frame, either absorbs or emits an amount of energy L, its inertial mass will correspondingly either increase or decrease by the amount L/c² [3].
Why was Einstein's result so mind-blowing? Well, AFAICU in Newtonian physics inertial mass is construed as an intrinsic property of an object; it measures the extent to which an object resists changes to its state of motion. OTOH, Einstein showed that the inertial mass of an object changes if the object absorbs or emits energy. This was indeed a revolutionary idea.
References
--------------
[1] "Ist die Trägheit eines Körpers von seinem Energieinhalt abhängig?", http://info.phys.unm.edu/~alandahl/phys262f06/Einstein_Emc2paper1905.pdf
[2] "Does the Inertia of a Body Depend upon its Energy-Content?", https://www.fourmilab.ch/etexts/einstein/E_mc2/www/
[3] "The Equivalence of Mass and Energy", https://plato.stanford.edu/entries/equivME/
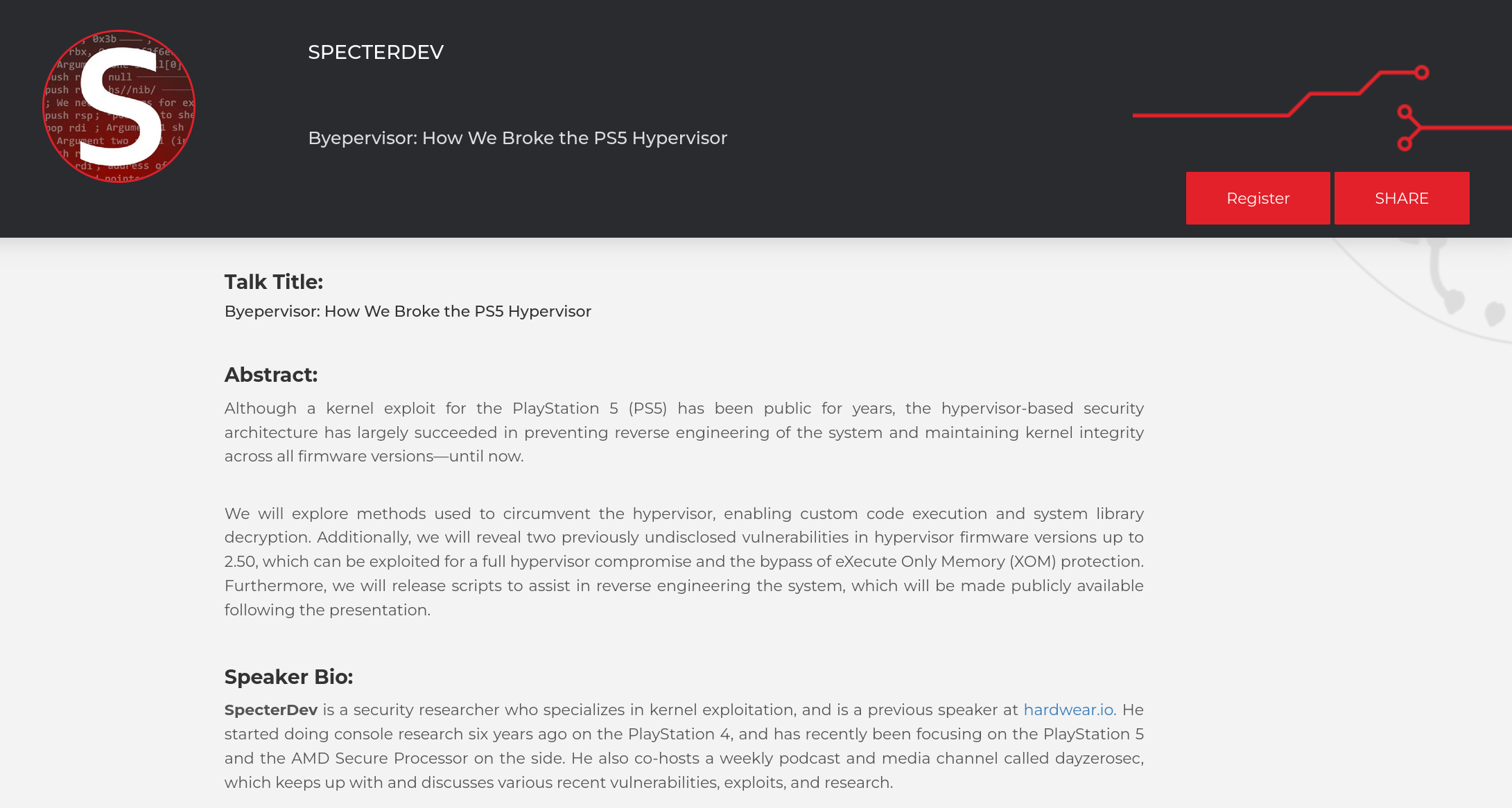
Joxean Koret (@matalaz)
joxean@mastodon.socialWow, Specter bypassed XOM and broke the PS5 hypervisor. Awesome work.
"Byepervisor: How We Broke the PS5 Hypervisor".
#ps5 #xom #hypervisor #byepervisor
https://hardwear.io/netherlands-2024/speakers/specter.php
Jeff Moss
thedarktangent@defcon.socialI remember hackers breaking in to CALEA lawful intercept boxes to spy on each other over 20+ years ago..
IIRC They were default SunOS servers connected direct to internet, no patches or updates applied over the years. Once you mapped them you could wait for a known vulnerability and visit them again.
It’s always been terrible, and always been known. I want it to be taken seriously.
Edit: It may be closer to 30 years than 20, but “a long time ago”
buherator
buheratorhttps://www.bleepingcomputer.com/news/security/internet-archive-hacked-data-breach-impacts-31-million-users/
As an IA user and donor I'm kind of glad this happened: passwords are properly hashed (bcrypt), there is a chance to improve security.
But anyone who decided they should hack IA of all things can (as we say around here) go and shit out a hedgehog.
Lesley Carhart 
hacks4pancakes@infosec.exchange
Republicans,
Democrats,
Third party voters
People driven by totally incompatible political and religious ideologies,
Pineapple on pizza people,
People who hate pineapple on pizza and are incorrect,
🤜🏻🤛🏾 hating whomever hacked the Internet Archive
buherator
buheratorShow content
https://www.youtube.com/watch?v=GKTKke-nYQk
Also, finally they found a proper live background vocalist!
Yellow Flag
WPalant@infosec.exchangeIf people loosing access to their books when the vendor goes out of business was already bad, now the same thing is happening to cars: https://arstechnica.com/cars/2024/10/connected-car-failure-puts-kibosh-on-sale-of-3300-fisker-oceans/
I know, it is happening all over the place, merely with pieces of technology not quite as expensive. Maybe, just maybe, having basic functionality depend on external components isn’t such a great idea?
And since I don’t see “the market” ever discovering this, maybe some regulation is in order? Just so the next tech startup going out of business (or merely unwilling to support “outdated” hardware) isn’t an occasion to throw away tons of products in perfect working order.
buherator
buheratorhttps://www.apologize.lol/
Also: "We formed a Super PAC and bought the personal voting records of every American citizen from a data broker we found on the internet. It’s pretty fucked up." WAT?!
Not Simon 🐐
screaminggoat@infosec.exchangeMozilla Firefox exploited zero-day: Security Advisory 2024-51 Security Vulnerability fixed in Firefox 131.0.2, Firefox ESR 128.3.1, Firefox ESR 115.16.1
CVE-2024-9680 (critical severity) Use-after-free in Animation timeline
An attacker was able to achieve code execution in the content process by exploiting a use-after-free in Animation timelines. We have had reports of this vulnerability being exploited in the wild.
See related @BleepingComputer reporting: Mozilla fixes Firefox zero-day actively exploited in attacks
#zeroday #vulnerability #firefox #mozilla #cve #CVE_2024_9680
BrianKrebs
briankrebs@infosec.exchangeHang on to your seats, because this one's a wild ride. Literally.
Lamborghini Carjackers Lured by $243M Cyberheist
The parents of a 19-year-old Connecticut honors student accused of taking part in a $243 million cryptocurrency heist in August were carjacked a week later — while out house-hunting in a brand new Lamborghini. Prosecutors say the couple was beaten and briefly kidnapped by six young men who traveled from Florida as part of a botched plan to hold the parents for ransom.
https://krebsonsecurity.com/2024/10/lamborghini-carjackers-lured-by-243m-cyberheist/
Not Simon 🐐
screaminggoat@infosec.exchangeHorizon3: Palo Alto Expedition: From N-Day to Full Compromise
References:
- CVE-2024-5910 (CVSSv4: 9.3 critical, disclosed 10 July 2024 by Palo Alto Networks) Expedition: Missing Authentication Leads to Admin Account Takeover
- CVE-2024-9464 Expedition: Authenticated Command Injection
- CVE-2024-9465 Expedition: Unauthenticated SQL Injection
- CVE-2024-9466 Expedition: Cleartext Credentials in Logs
Daaaaaaaamn @hacks_zach, Zach Hanley at it again with the Palo Alto Networks vulnerabilities. In trying to find CVE2-2024-5910 in Expedition (a configuration migration tool from a supported vendor to Palo Alto Networks PAN-OS), he found CVE-2024-9464, CVE-2024-9465 and CVE-2024-9466. It appears that CVE-2024-9465 (unauth SQL injection) leads to leaking credentials via "users" and "devices" tables which contain password hashes and device API keys. This is the CVE-2024-9466.
#paloaltonetworks #expedition #vulnerability #CVE #vulnerabilityanalysis
Project Zero Bot
p0botdav1d integer overflow leading to out-of-bounds write
https://project-zero.issues.chromium.org/issues/42451651
CVE-2024-1580
I want the same drugs Mozilla leadership is taking. They sound too good to be left out!!!! AAHAHHAHAHAHAHHAHAHA My head is spinning from so much bullshit newspeak ahahahhahahahahahahahaha
"How do we ensure that privacy is not a privilege of the few but a fundamental right available to everyone? These are significant and enduring questions that have no single answer. But, for right now on the internet of today, a big part of the answer is online advertising."
/r/netsec
_r_netsec@infosec.exchangeExploiting AMD atdcm64a.sys arbitrary pointer dereference - Part 3 https://security.humanativaspa.it/exploiting-amd-atdcm64a-sys-arbitrary-pointer-dereference-part-3/
4Dgifts
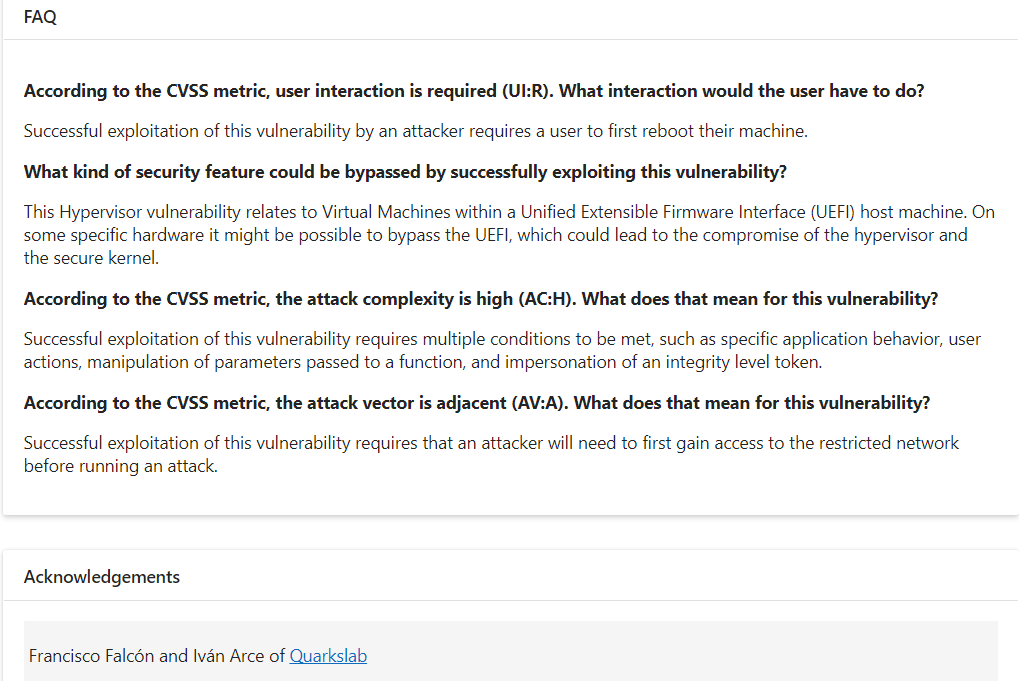
4Dgifts@mastodon.socialThis reads like RCE from the local broadcast domain to me but I am not in the MSRC hive mind so no idea why they call it "security feature bypass"
Perhaps UEFI is considered a security feature that can be bypassed?
🤔
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2024-20659