Posts
2559Following
629Followers
1408j_bertolotti
j_bertolotti@mathstodon.xyzThis year #Physics #NobelPrize was given to Hopfield and Hinton for their work on neural networks and machine learning.
Currently a lot of Physicists scratching their heads and wondering how machine learning is Physics, but:
* Physicists have taken Nobel prizes in Medicine and Chemistry a lot over the years, so I don't think it is fair for us to complain.
* Hopfield networks and Bolzmann machines are probably the two most "Physics adjacent" architectures for a neural network.
Overall, unexpected but well deserved.
https://www.nobelprize.org/prizes/physics/2024/press-release/
Philippe Smet
pfsmet@mastodon.socialCurrent temperature of #physics mastodon, twitter et al. ;-)
daniel:// stenberg://
bagder@mastodon.social#curl bug-bounty stats
(Including 84,260 USD payouts and 15.4% being valid reports.)
https://daniel.haxx.se/blog/2024/10/09/curl-bug-bounty-stats/
buherator
buheratorhttps://blog.adafruit.com/2024/10/08/letters-reveal-the-quiet-genius-of-ada-lovelace-ald24-findingada/
buherator
buheratorhttps://hackaday.com/2024/10/08/barbies-video-has-never-looked-so-good/
buherator
buheratorhttps://blog.amberwolf.com/blog/2024/october/cve-2024-37404-ivanti-connect-secure-authenticated-rce-via-openssl-crlf-injection/
Have I Been Pwned
haveibeenpwned@infosec.exchangeNew sensitive breach: "AI girlfriend" site Muah[.]ai had 1.9M email addresses breached last month. Data included AI prompts describing desired images, many sexual in nature and many describing child exploitation. 24% were already in @haveibeenpwned. More: https://www.404media.co/hacked-ai-girlfriend-data-shows-prompts-describing-child-sexual-abuse-2/
Patrick C Miller 
patrickcmiller@infosec.exchange
Ivanti warns of three more CSA zero-days exploited in attacks https://www.bleepingcomputer.com/news/security/ivanti-warns-of-three-more-csa-zero-days-exploited-in-attacks/
Trend Zero Day Initiative
thezdi@infosec.exchangeIt's the spooky season, and #Microsoft and #Adobe have released their spookiest patches yet. Two bugs from Microsoft are under attack, and one looks strangely familiar. @TheDustinChilds breaks down the release and points out some deployment priorities. https://www.zerodayinitiative.com/blog/2024/10/8/the-october-2024-security-update-review
screaminggoat
screaminggoat@infosec.exchangeHappy #PatchTuesday from Microsoft: 5 ZERO-DAYS (2 exploited, all of them publicly disclosed)
- CVE-2024-43573 (6.5 medium) Microsoft Windows MSHTML Platform Spoofing Vulnerability (PUBLICLY DISCLOSED, EXPLOITED)
- CVE-2024-43572 (7.8 high) Microsoft Management Console Remote Code Execution Vulnerability (PUBLICLY DISCLOSED, EXPLOITED)
- CVE-2024-43583 (7.8 high) Winlogon Elevation of Privilege Vulnerability (PUBLICLY DISCLOSED)
- CVE-2024-20659 (7.1 high) Windows Hyper-V Security Feature Bypass Vulnerability (PUBLICLY DISCLOSED)
- CVE-2024-6197 (8.8 high) Open Source Curl Remote Code Execution Vulnerability (PUBLICLY DISCLOSED)
cc: @goatyell @mttaggart @hrbrmstr @ntkramer @iagox86 @zackwhittaker @dreadpir8robots @TheDustinChilds @neurovagrant @xorhex @campuscodi @briankrebs (remember to remove the mentions to avoid ReplyAll madness)
Molly White
molly0xfff@hachyderm.ioWe can build the web that we want to see. Watch the recording of my talk from #XOXOFest!
Sonar Research
SonarResearch@infosec.exchangeFrom HTTP request to ROP chain in Node.js! 🔥
Our latest blog post explains how to turn a file write vulnerability in a Node.js application into RCE – even though the target's file system is read-only:
buherator
buheratorhttps://blog.convisoappsec.com/en/automatically-renaming-functions-with-ghidra/
lcamtuf 


lcamtuf@infosec.exchange
In response to my earlier post, some Twitter folks asked why I'm "so afraid of telemetry".
For one, it's because I've seen first-hand what ends up in it. Crash reporting is particularly bad: it's nearly impossible to reliably scrub of sensitive info - URLs, auth tokens, etc.
Worse, a lot of other "telemetry" is deliberately privacy-violating. "Don't worry, we only collect anonymized GPS routes". Except, you know, a buyer of this data can filter by tracks originating from my home.
But above all, I just don't want the mental burden of figuring this out for every piece of software I install, so I hate that it's the new norm.
If you want a peek at how I'm using your software, meaningfully ask, instead of sneaking it in on page 38 of the EULA.
buherator
buheratorTIL: AVX-512 supports an instruction implementing binary logic defined by a 3-input LUT. Sounds super handy.
Rodrigo
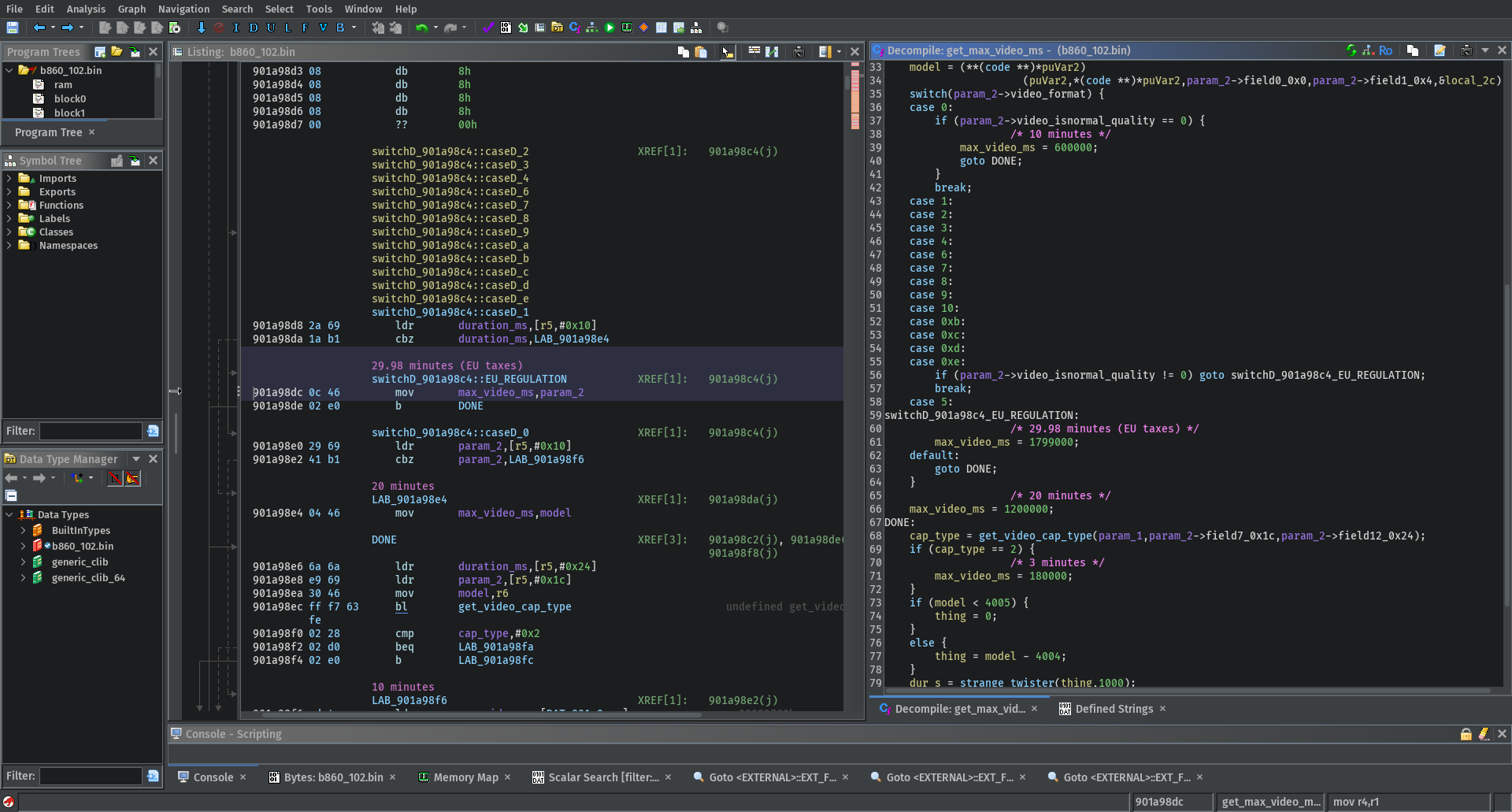
rdg@fosstodon.org#Nikon video limit of 30 minutes? Let see if I can patch this bad boi.
buherator
buheratorhttps://www.da.vidbuchanan.co.uk/blog/dram-emfi.html
screaminggoat
screaminggoat@infosec.exchangeCisco security advisories:
- Cisco UCS B-Series, Managed C-Series, and X-Series Servers Redfish API Command Injection Vulnerability CVE-2024-20365 (6.5 medium)
- Cisco Small Business RV042, RV042G, RV320, and RV325 Routers Denial of Service and Remote Code Execution Vulnerabilities
- CVE-2024-20516, CVE-2024-20517, CVE-2024-20522, CVE-2024-20523 and CVE-2024-20524 (6.8 medium) Cisco Small Business RV042, RV042G, RV320, and RV325 Denial of Service Vulnerabilities
- CVE-2024-20518, CVE-2024-20519, CVE-2024-20520 and CVE-2024-20521 (6.5 medium) Cisco Small Business RV042, RV042G, RV320, and RV325 Remote Command Execution Vulnerabilities
- Cisco Small Business RV340, RV340W, RV345, and RV345P Dual WAN Gigabit VPN Routers Privilege Escalation and Remote Command Execution Vulnerabilities CVE-2024-20393 (8.8 high) CVE-2024-20470 (4.7 medium)
- Cisco Nexus Dashboard Orchestrator SSL/TLS Certificate Validation Vulnerability CVE-2024-20385 (5.9 medium)
- Cisco Nexus Dashboard and Nexus Dashboard Fabric Controller Unauthorized REST API Vulnerabilities
- CVE-2024-20438 (6.3 medium) Cisco NDFC Unauthorized REST API Endpoints Vulnerability
- CVE-2024-20441 (5.7 medium) Cisco NDFC Unauthorized REST API Endpoint Vulnerability
- CVE-2024-20442 (5.4 medium) Cisco Nexus Dashboard Unauthorized REST API Endpoints Vulnerability
- CVE-2024-20477 (5.4 medium) Cisco NDFC Unauthorized REST API Endpoint Vulnerability
- Cisco Nexus Dashboard Hosted Services Information Disclosure Vulnerabilities CVE-2024-20490 and CVE-2024-20491 both 6.3 medium
- Cisco Nexus Dashboard Fabric Controller REST API Command Injection Vulnerability CVE-2024-20444 (5.5 medium)
- Cisco Nexus Dashboard Fabric Controller Remote Code Execution Vulnerability CVE-2024-20449 (8.8 high)
- Cisco Nexus Dashboard Fabric Controller Arbitrary Command Execution Vulnerability CVE-2024-20432 (9.9 critical) 🥵
- Cisco Nexus Dashboard Fabric Controller Configuration Backup Information Disclosure Vulnerability CVE-2024-20448 (6.3 medium)
- Cisco Meraki MX and Z Series Teleworker Gateway AnyConnect VPN Session Takeover and Denial of Service Vulnerability CVE-2024-20509 (5.8 medium)
- Cisco Meraki MX and Z Series Teleworker Gateway AnyConnect VPN Denial of Service Vulnerabilities
- CVE-2024-20498, CVE-2024-20499, CVE-2024-20501 (8.6 high) Cisco Meraki MX and Z Series Teleworker Gateway AnyConnect VPN DoS Vulnerability
- CVE-2024-20500 (5.8 medium) Cisco Meraki MX and Z Series Teleworker Gateway AnyConnect VPN DoS Vulnerability
- CVE-2024-20502 (5.8 medium) Cisco Meraki MX and Z Series Teleworker Gateway AnyConnect VPN DoS Vulnerability
- CVE-2024-20513 (5.8 medium) Cisco Meraki MX and Z Series Teleworker Gateway AnyConnect VPN Targeted DoS Vulnerability
- Cisco Identity Services Engine Information Disclosure Vulnerability CVE-2024-20515 (6.5 medium)
- Cisco Expressway Series Privilege Escalation Vulnerability CVE-2024-20492 (6.0 medium)
At a glance no mention of exploitation:
The Cisco PSIRT is not aware of any public announcements or malicious use of the vulnerabilities that are described in this advisory.
Neither the Cisco Product Security Incident Response Team (PSIRT) nor the Cisco Meraki Incident Response Team is aware of any malicious use of the vulnerabilities that are described in this advisory.