Posts
2972Following
697Followers
1545Ange
Ange@mastodon.socialAn awesome video of live coding 6502 asm directly in Basic to produce music, with all the explanations on the way.
https://www.youtube.com/watch?v=ly5BhGOt2vE
/r/netsec
_r_netsec@infosec.exchangeVesta Admin Takeover: Exploiting Reduced Seed Entropy in bash $RANDOM https://fortbridge.co.uk/research/vesta-admin-takeover-exploiting-reduced-seed-entropy-in-bash-random/
bert hubert 🇺🇦🇪🇺🇺🇦
bert_hubert@fosstodon.orgPro-tip if you are searching for anything HTML, CSS or JavaScript related: add "mdn" to your query. This Mozilla project really is a work of love, maintained by hundreds of volunteers @openwebdocs and @MDN staff and contractors. https://developer.mozilla.org/en-US/docs/Learn
buherator
buheratorhttps://www.talospace.com/2024/09/music-production-on-power-adventure-in.html
:O
buherator
buheratorhttps://blog.convisoappsec.com/en/finding-classes-to-exploit-insecure-unchecked-vulnerabilities-in-java-with-joern/
buherator
buheratorhttps://www.romainthomas.fr/post/24-09-apple-lockdown-dbi-lifting/
I am wondering how many people and organisations genuinely have “opponent that can break into a cloud provider, steal hard disks, then extract coherent data from them outside of the cloud storage systems” in their threat model. Because I’m guessing in most cases such an adversary has easier and more effective ways to get at any at-rest data. Encrypting the drives a, for instance, RDS database is running on is not bad, but in most cases prioritising this over other security work seems like it’s driven by audit checkboxes rather than a full analysis. Do it, but fix the big ticket stuff first.
This may be an excessively cynical view.
Alec Muffett
alecmuffett@mastodon.socialWouldn’t it be easier to make it illegal to trick, mislead, or defraud people?
https://alecmuffett.com/article/110438
#LinaKhan #ai #cyber
Mike Siegel
mikesiegel@infosec.exchangeEveryone was up in arms about the CUPS thing but this is much more serious: CVE-2024-45200 https://github.com/latte-soft/kartlanpwn
Marcus Hutchins 
malwaretech@infosec.exchange
I bought a HTML template for a site I'm making. Typically I just pull the compiled html files out and make a standalone project which I maintain in a text editor. But, this time I figured it's time to learn modern web development so I tried using the toolchain it came with.
The toolchain consists of 3,446 dependencies, runs 15 processes, and uses 3 GB of ram. Unfortunately I can't run for president, but if I could I would run on the platform of making Node.js illegal.
screaminggoat
screaminggoat@infosec.exchangeCISA: CISA Adds Four Known Exploited Vulnerabilities to Catalog
Hot off the press! Page is now live and published on their website.
- CVE-2019-0344 (9.8 critical) SAP Commerce Cloud Deserialization of Untrusted Data Vulnerability
- CVE-2021-4043 (5.5 medium) Motion Spell GPAC Null Pointer Dereference Vulnerability
- CVE-2020-15415 (9.8 critical) DrayTek Multiple Vigor Routers OS Command Injection Vulnerability
- CVE-2023-25280 (9.8 critical) D-Link DIR-820 Router OS Command Injection Vulnerability
#cisa #kev #vulnerability #cve #eitw #activeexploitation #CVE_2019_0344 #CVE_2021_4043 #CVE_2020_15415 #CVE_2023_25280 #draytek #dlink #motionspell #sap
404 Media
404mediaco@mastodon.socialMassive e-learning platform Udemy is training its AI on instructors' classes. It gave them a short "opt-out" window to reject this. Instructors are surprised to learn that time has passed.
Kagi HQ
kagihq@mastodon.socialWe'd love your insights and feedback to improve Kagi!
Since Kagi does not track its users, we need to hear directly from you in order to better serve you and our community💡
https://docs.google.com/forms/d/e/1FAIpQLSd7F3uYX4pY4avwHIDdJGWBjnUMUPy8X8FVCSu43740OOAL2Q/viewform
(And yes, we know, Google Forms! What are some recommendations for the best alternatives?)
buherator
buheratorhttps://github.com/binarly-io/ToolsAndPoCs/blob/master/Posix/Supermicro/CVE-2024-36435.py
CVE-2024-36435
Stefano Marinelli
stefano@bsd.cafeIn recent days, I’ve observed and talked to some people.
Some responses made me reflect: "I tried Mastodon, but I didn’t know whom to follow. No system gave me targeted suggestions, and I felt lost and abandoned it."
"Purchases? Mostly online. Sometimes I don’t know what to buy, and targeted advertising suggestions help me."
"I get my information online, especially from social media. I receive all the news that interests me, while official sites are full of things I have no interest in."
One of the problems in today’s society is that people, bombarded by the sheer amount of information available, feel lost. Algorithms help them choose, decide, and orient themselves, but the issue is that if these algorithms are not calibrated positively but solely in an interested manner, the result is to produce individuals incapable of making informed decisions, conditioned exclusively by what is suggested, stated, and amplified.
It’s as if, after years of guided information, many people believe they are always right (the "famous" bubble), feel entitled to everything (advertisements), and perceive the world as hostile (conspiracy theories, etc.).
Artificial intelligence has now become another example of this system: I know people who can no longer do anything without it. They try to impose me (incorrect) IT sysadmin solutions me because "the AI said so."
At this rate, I fear the most atrophied part of our body will be our brains.
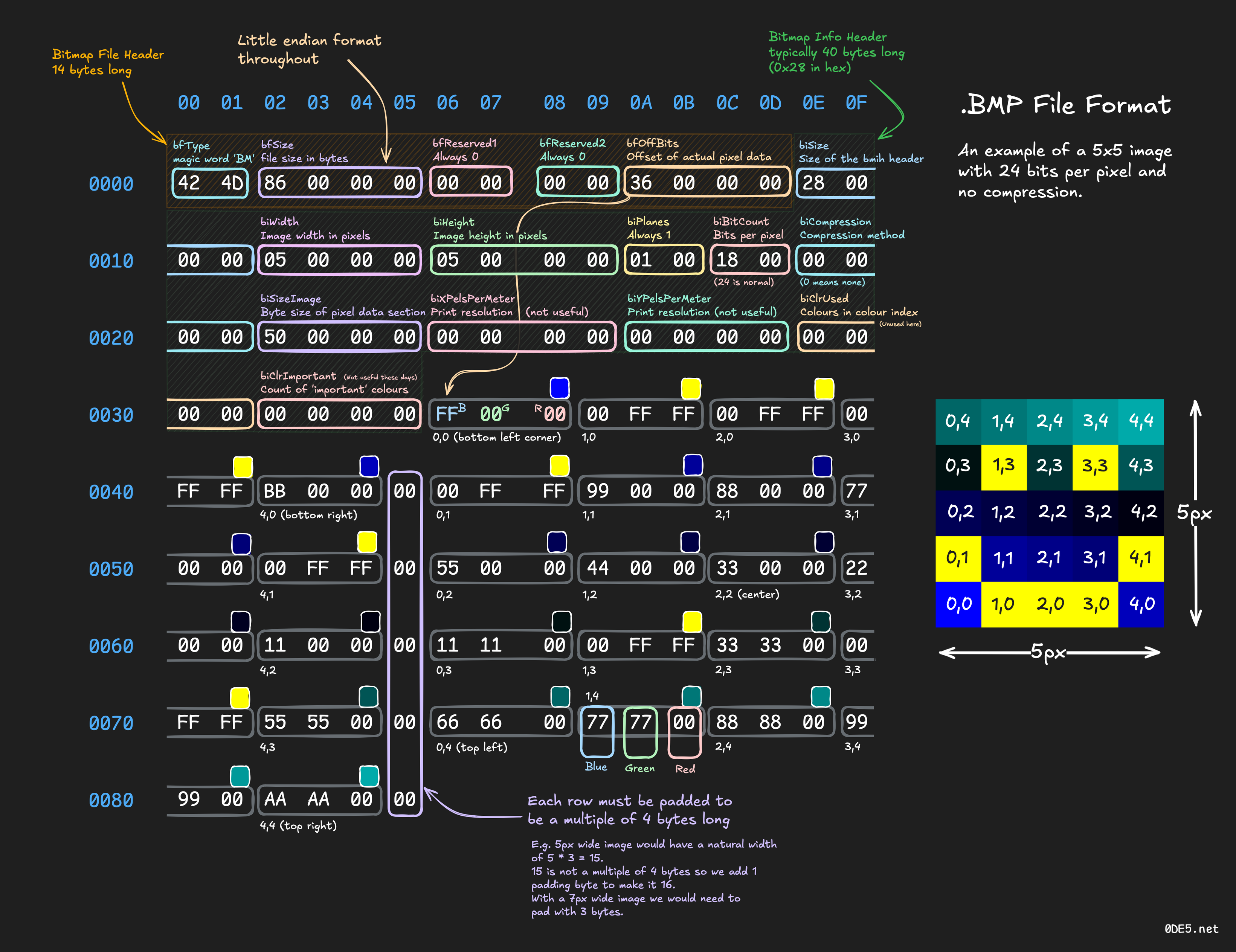
Ange
Ange@mastodon.socialICYDK Kay 'neoeno' Lack makes nice materials (blogs, posters, videos) about file formats, analysis, crafting...
Ex: https://www.0de5.net/stimuli/a-reintroduction-to-programming/memory/binary-formats-through-bitmap-images
/r/netsec
_r_netsec@infosec.exchangeIconv, set the charset to RCE: Exploiting the glibc to hack the PHP engine (part 3) https://www.ambionics.io/blog/iconv-cve-2024-2961-p3
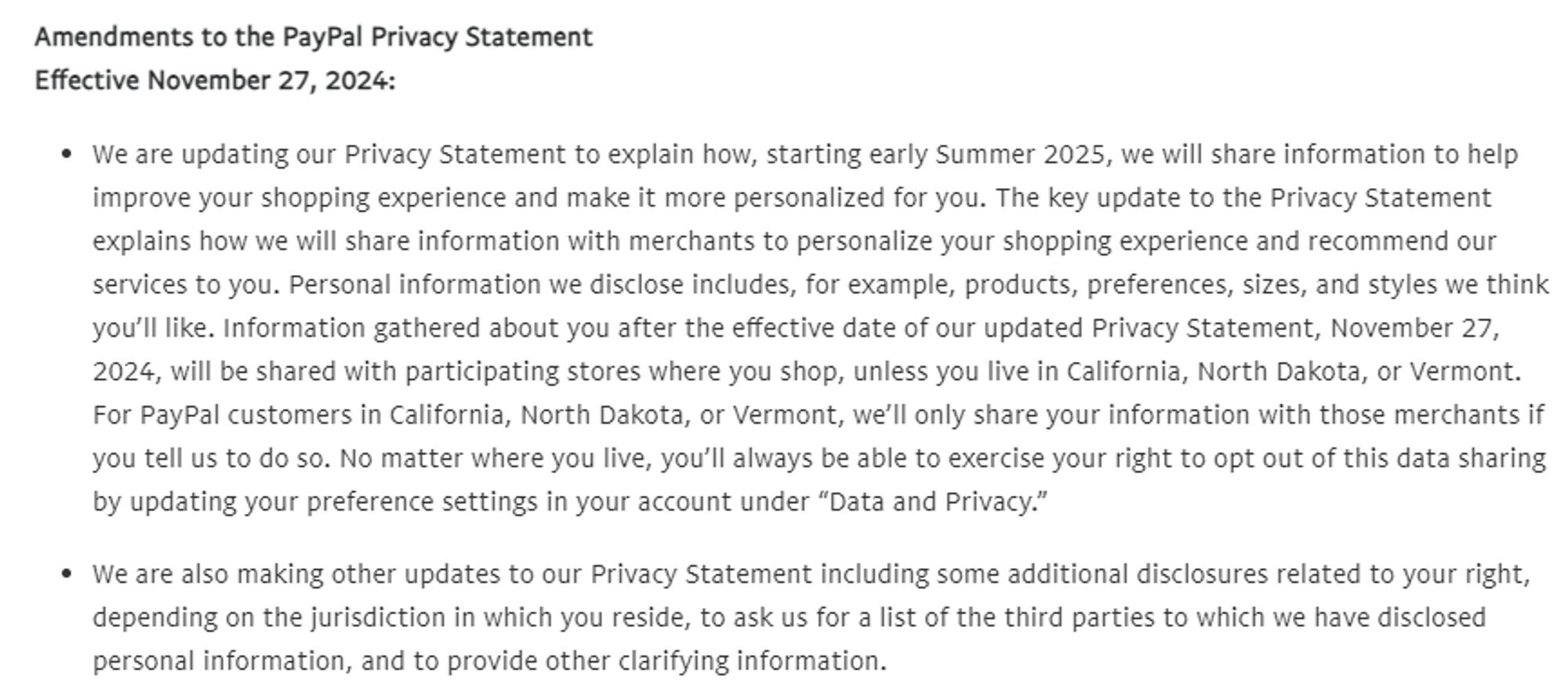
azteclady
herhandsmyhands@romancelandia.club#PSA #PayPal is changing their privacy statement/terms of service starting November so that they can sell your information to merchants.
You CAN opt out, but you have to do it before they start:
Settings > Data & Privacy > Manage shared info > Personalized shopping, and toggle that shit off
ETA: this is probably country specific, due to differing privacy laws.
You can try privacy>settings>recommendations
Check replies, people have found the same toggle under a different header.
Jesus Michał "Le Sigh" 🏔 (he)
mgorny@social.treehouse.systemsNew on blog: "The perils of transition to 64-bit #time_t"
"""
In the "Overview of cross-architecture portability problems", I have dedicated a section to the problems resulting from use of #32-bit `time_t` type. This design decision, still affecting Gentoo systems using glibc, means that 32-bit applications will suddenly start failing in horrible ways in 2038: they will be getting `-1` error instead of the current time, they won't be able to `stat()` files. In one word: complete mayhem will emerge.
There is a general agreement that the way forward is to change `time_t` to a 64-bit type. Musl has already switched to that, glibc supports it as an option. A number of other distributions such as Debian have taken the leap and switched. Unfortunately, source-based distributions such as #Gentoo don't have it that easy. So we are still debating the issue and experimenting, trying to figure out a maximally safe upgrade path for our users.
Unfortunately, that's nowhere near trivial. Above all, we are talking about a breaking ABI change. It's all-or-nothing. If a library uses `time_t` in its API, everything linking to it needs to use the same type width. In this post, I'd like to explore the issue in detail — why is it so bad, and what we can do to make it safer.
"""
https://blogs.gentoo.org/mgorny/2024/09/28/the-perils-of-transition-to-64-bit-time_t/