Posts
2991Following
698Followers
1545Ange
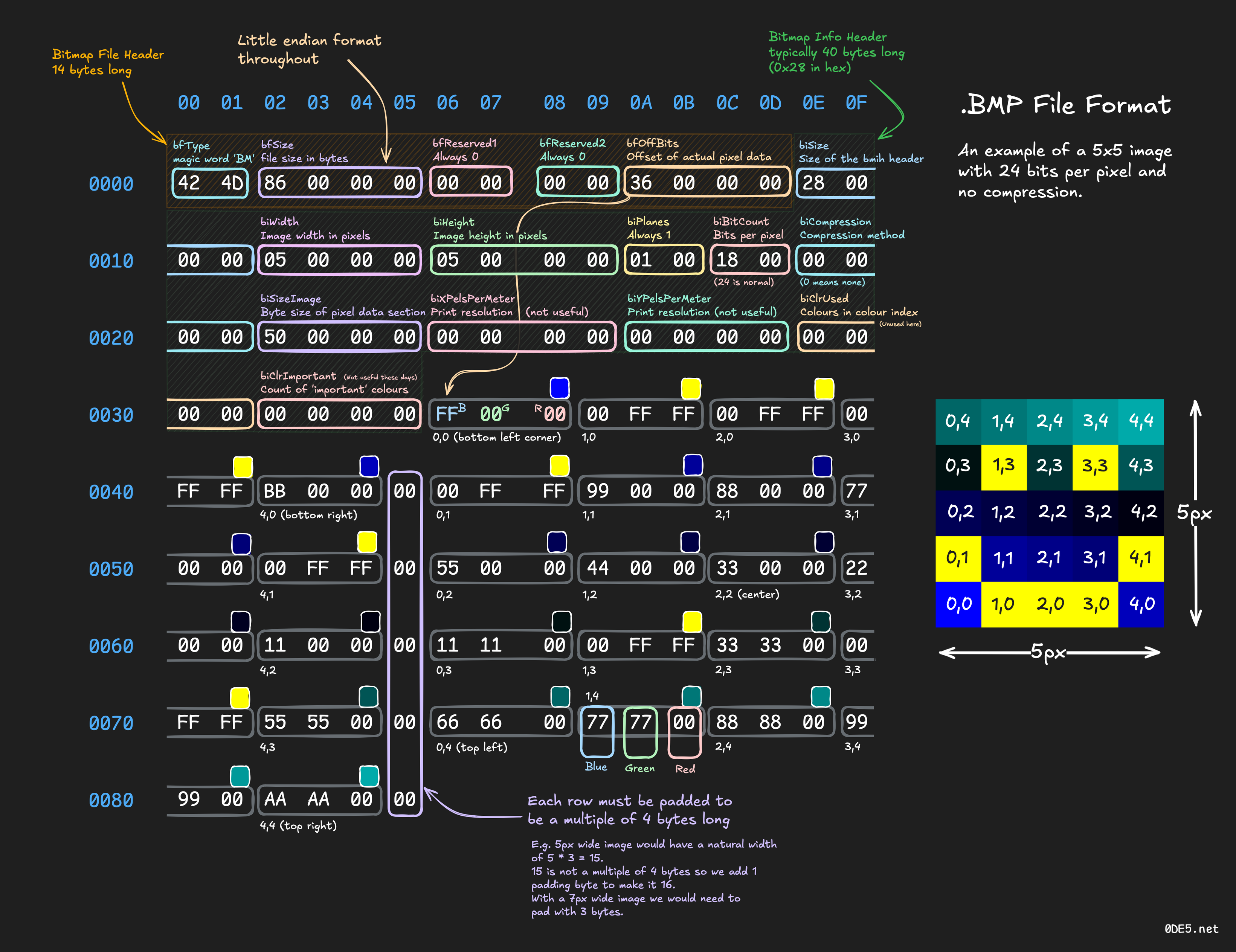
Ange@mastodon.socialICYDK Kay 'neoeno' Lack makes nice materials (blogs, posters, videos) about file formats, analysis, crafting...
Ex: https://www.0de5.net/stimuli/a-reintroduction-to-programming/memory/binary-formats-through-bitmap-images
/r/netsec
_r_netsec@infosec.exchangeIconv, set the charset to RCE: Exploiting the glibc to hack the PHP engine (part 3) https://www.ambionics.io/blog/iconv-cve-2024-2961-p3
azteclady
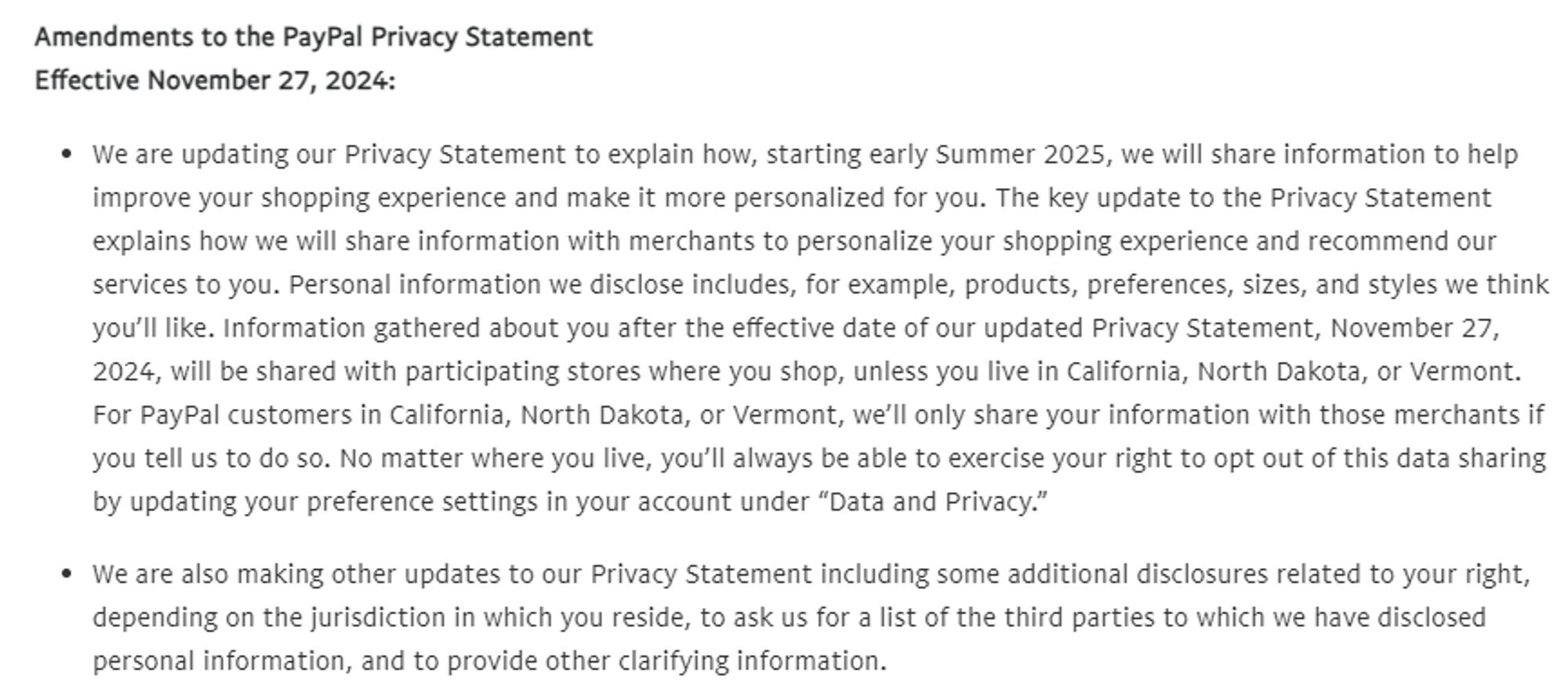
herhandsmyhands@romancelandia.club#PSA #PayPal is changing their privacy statement/terms of service starting November so that they can sell your information to merchants.
You CAN opt out, but you have to do it before they start:
Settings > Data & Privacy > Manage shared info > Personalized shopping, and toggle that shit off
ETA: this is probably country specific, due to differing privacy laws.
You can try privacy>settings>recommendations
Check replies, people have found the same toggle under a different header.
Jesus Michał "Le Sigh" 🏔 (he)
mgorny@social.treehouse.systemsNew on blog: "The perils of transition to 64-bit #time_t"
"""
In the "Overview of cross-architecture portability problems", I have dedicated a section to the problems resulting from use of #32-bit `time_t` type. This design decision, still affecting Gentoo systems using glibc, means that 32-bit applications will suddenly start failing in horrible ways in 2038: they will be getting `-1` error instead of the current time, they won't be able to `stat()` files. In one word: complete mayhem will emerge.
There is a general agreement that the way forward is to change `time_t` to a 64-bit type. Musl has already switched to that, glibc supports it as an option. A number of other distributions such as Debian have taken the leap and switched. Unfortunately, source-based distributions such as #Gentoo don't have it that easy. So we are still debating the issue and experimenting, trying to figure out a maximally safe upgrade path for our users.
Unfortunately, that's nowhere near trivial. Above all, we are talking about a breaking ABI change. It's all-or-nothing. If a library uses `time_t` in its API, everything linking to it needs to use the same type width. In this post, I'd like to explore the issue in detail — why is it so bad, and what we can do to make it safer.
"""
https://blogs.gentoo.org/mgorny/2024/09/28/the-perils-of-transition-to-64-bit-time_t/
tj usiyan
griotspeak@soc.mod-12.comThem: “This is not a paywall.”
Me: “whew”
Them: Provide your Email address”
Me: “that’s a payment, though. Personal information is a payment”
lcamtuf 


lcamtuf@infosec.exchange
Analog filters, part II: let it ring
https://lcamtuf.substack.com/p/analog-filters-part-2-let-it-ring/?1
buherator
buheratorhttp://www.righto.com/2024/09/f4-attitude-indicator.html?m=1
buherator
buheratorTom Stuart
tom@social.tomstu.artI’m happy to see that the GOV.UK Service Manual’s “Building a robust frontend using progressive enhancement” page was updated this week and made it to the top of Hacker News today. The technology industry would collectively save unimaginable quantities of time, money, energy and stress if this single page were required reading for everyone involved in building a web site. https://www.gov.uk/service-manual/technology/using-progressive-enhancement
raptor 
raptor@infosec.exchange
"Sometimes, hacking is just someone spending more time on something than anyone else might reasonably expect.”
— Jerry Gamblin
buherator
buheratorShow content
While I don't agree with the conclusion of the article (optimizing commute), this pretty much confirms my experience.
I like to stare at my nothing box.[2]
[1] https://behavioralscientist.org/are-we-too-impatient-to-be-intelligent/
[2] https://www.youtube.com/watch?v=SZ6mVumHY9I
exploits.club
exploitsclub@bird.makeup40th Weekly Vuln Research newsletter is OUT NOW 📰
iOS kernel exploitation from @alfiecg_dev
Elgato hacking from @dt_db
@_tsuro bypasses CET
RCU Internals from @u1f383
Google Teams check off their OKRs
➕ Jobs and more 👇
AttackerKB
attackerkbTopic description: "HTTP request/response smuggling vulnerability in HAProxy version 2.7.0, and 2.6.1 to 2.6.7 allows a remote attacker to alter a legitimate user's request ..."
"HAProxy's HTTP/3 implementation fails to block a **malformed HTTP header field name**, and **when deployed in front of a server that incorrectly process this malformed header**, it may be used to conduct an HTTP request/response smuggling attack ..."
Link: https://attackerkb.com/assessments/410b285d-5724-4300-bcc4-603cc4c726ac
Thijs Alkemade
xnyhps@bird.makeupWe had a short look at the buffer overflow found by fuzzing `process_browse_data` to determine its exploitability. Conclusion: this bug alone won't give you RCE, or even an info leak.
Rick de Jager
rdjgr@bird.makeupHere's my quick and dirty PoC for the CUPS vulns. I wrote it after spotting the patches in the public CUPS repo. As always, expect CTF-quality code :D