Posts
3368Following
712Followers
1580buherator
buheratorhttps://www.thezdi.com/blog/2024/9/25/exploiting-exchange-powershell-after-proxynotshell-part-4-no-argument-constructor
Thunderbird: Free Your Inbox
thunderbird@mastodon.onlineThunderbird for Android is coming soon! Find out how to get involved, from beta testing to localization to support and more, in our shiny new contributor guide!
(Seriously, by soon, we mean soon!)
#Thunderbird #Android #OpenSource
https://blog.thunderbird.net/2024/09/contribute-to-thunderbird-for-android/
nixCraft 🐧
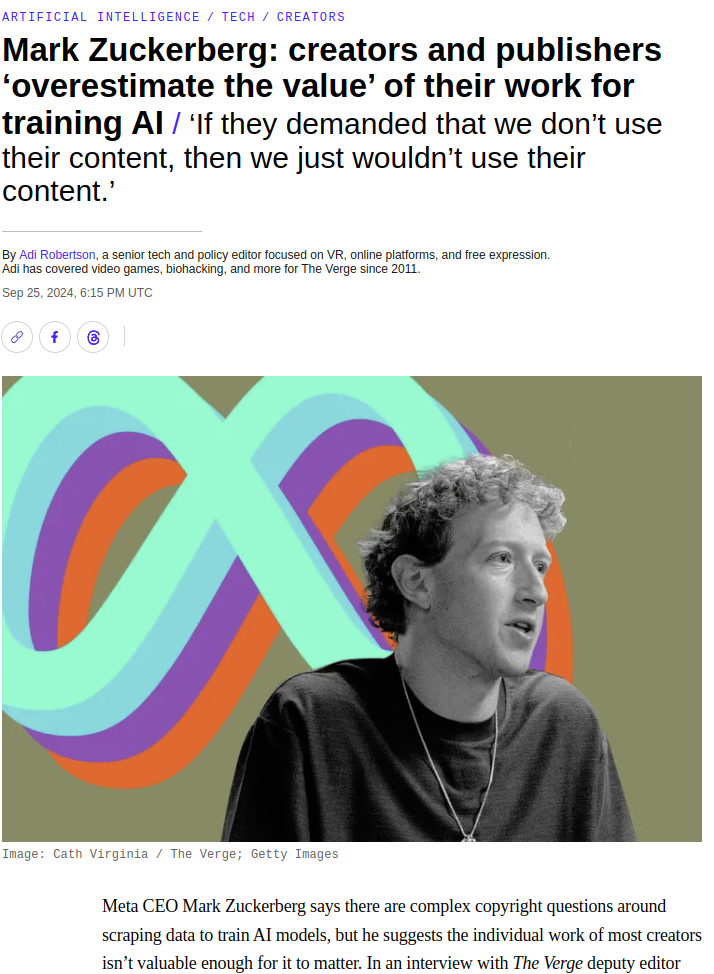
nixCraft@mastodon.socialMark Zuckerberg says the individual work of most creators isn’t valuable enough for it to matter. First of all, FUCK you, Mark. Another billionaire thinks an artist's work, such as images/art, books, music, text, and other things, has no value. People can't even browse IG or FB without downloading your shity app. Why don't you allow everyone to scrap those IG/FB posts? This guy is a menace to society and doesn't care if someone will lose their livelihood so that he can have another 100 billion.
/r/netsec
_r_netsec@infosec.exchangeUnath RCE in CUPS which triggers after a print job - affects most desktop linux flavors https://www.evilsocket.net/2024/09/26/Attacking-UNIX-systems-via-CUPS-Part-I/
Andy Greenberg
agreenberg@infosec.exchangeHackers showed me (there's video) how a website vulnerability let them locate, unlock, honk the horn, start ignition of any of millions Kias in seconds, just by reading a car's license plate.
They found similar bugs for a dozen carmakers over the last two years.
https://www.wired.com/story/kia-web-vulnerability-vehicle-hack-track/
buherator
buheratorhttps://gabrieldurdiak.github.io/clfd/
Anderson Nascimento
andersonc0d3@infosec.exchangeI am teaching a course on Linux kernel exploitation, and I mentioned the indeterminism of the objects in the physmap to the class. An example I showed is the struct task_struct of the first process, systemd. Even with KASLR disabled, that address will always differ on every boot. I said the CPU is fundamentally indeterministic, but my answer is too vague. I will read the Linux kernel initialization code to see if I discover anything interesting. Still, I would appreciate it if someone could give me a more detailed answer or point me in the right direction.
(gdb) p/x init_task->tasks->next
$76 = 0xffff888005028890
(gdb)
(gdb) p/x init_task->tasks->next
$77 = 0xffff88800502bb90
(gdb)
(gdb) p/x init_task->tasks->next
$79 = 0xffff88800502d510
(gdb)
404 Media
404mediaco@mastodon.socialA jockey who is paralyzed from the waist down lost his ability to walk after a small battery for his $100,000 exoskeleton broke and the manufacturer refused to fix it because it was more than 5 years old
Jason Scott
textfiles@mastodon.archive.orgGreetings, cool people. The Internet Archive is having our yearly celebration event in October. The announcement and the link to getting tickets to attend are here:
https://blog.archive.org/2024/08/19/celebrate-with-the-internet-archive-on-october-22nd-23rd/
#science #BlackHole #simulation #JeanPierreLuminet #c1960 #c1978
The first simulated image of a black hole was calculated with an IBM 7040 computer using 1960 punch cards and hand-plotted by French astrophysicist Jean-Pierre Luminet in 1978.
Dan Goodin
dangoodin@infosec.exchangeBy me:
Chief among them: mandatory resets, required or restricted use of certain characters, and the use of security questions
Wladimir Palant
WPalant@infosec.exchangeOk, I found the hotel on booking.com but I restarted my browser and now it shows up with a much higher price… I see, coming from the search as opposed to opening the hotel page directly gives you a discount… And pretending to be a mobile browser (via Firefox’ Responsive Mode) gives you another discount… Ah, screw booking.com and their attempts to overcharge me, I can just book directly on the hotel website which is still cheaper.
I want this LEGO Turing machine! https://ideas.lego.com/projects/10a3239f-4562-4d23-ba8e-f4fc94eef5c7
buherator
buheratorhttps://www.synacktiv.com/en/publications/fuzzing-confused-dependencies-with-depfuzzer
buherator
buheratorhttps://ssd-disclosure.com/ssd-advisory-nortek-linear-emerge-e3-pre-auth-rce/
No CVE for this one?
Project Gutenberg
gutenberg_org@mastodon.social#OTD in 1905.
Albert Einstein publishes the third of his Annus Mirabilis papers, introducing the special theory of relativity, which used the universal constant speed of light c to derive the Lorentz transformations.
There are some controversies on the question of the extent to which Mileva Marić contributed to the insights of Einstein's annus mirabilis publications
https://en.wikipedia.org/wiki/Annus_mirabilis_papers#
On the Electrodynamics of Moving Bodies at PG:
https://www.gutenberg.org/ebooks/66944
buherator
buheratorI still have to dig into the works referenced by the recent Google post, but the data is obviously based on known vulns.
https://security.googleblog.com/2024/09/eliminating-memory-safety-vulnerabilities-Android.html
Because of this I think the conclusion shouldn't be that bugs naturally die out ("half-life"). Rather, if we have a fixed set of methods to discover vulns, we will eventually find everything _we currently can_ in a fixed code base, and we will again find some in new code.
I think Orange Tsai's latest work on Apache modules is a great demonstration of how a new approach can result in a bunch of CVE's. But the "realization" about format strings also comes to mind. How much "old" code had to be fixed because of that?
What I'd like to see is some data on memory-safe languages blocking otherwise vulnerable code paths, or vulns getting discovered during integration with safe languages.
Talos Vulnerability Reports
talosvulnsMicrosoft Pragmatic General Multicast Server PgmCloseConnection stale memory dereference
https://talosintelligence.com/vulnerability_reports/TALOS-2024-2062
CVE-2024-38140
jeffvanderstoep
jeffvanderstoep@infosec.exchangeI’m super excited about this blogpost. The approach is so counterintuitive, and yet the results are so much better than anything else that we’ve tried for memory safety. We finally understand why.
https://security.googleblog.com/2024/09/eliminating-memory-safety-vulnerabilities-Android.html
Jonathan Yu
jawnsy@mastodon.social"By turning off your lights all day every day for a month, you conserved about 1 percent of the energy needed for AI to generate a picture of a duck wearing sunglasses. Isn’t he cute? Aside from the fact that he has the feet of a human man, of course."
"By dropping $7K on better, energy-efficient insulation for your home, Google AI was able to tell someone how to prepare chicken incorrectly, and they got, like, super sick—thanks to you!"