Posts
2544Following
644Followers
1452buherator
buheratorhttps://labs.watchtowr.com/we-spent-20-to-achieve-rce-and-accidentally-became-the-admins-of-mobi/
buherator
buheratorhttps://blog.scrt.ch/2024/09/10/getting-code-execution-on-veeam-through-cve-2023-27532/
buherator
buheratorhttps://blog.scrt.ch/2024/09/10/getting-code-execution-on-veeam-through-cve-2023-27532/
DCoder 🇱🇹❤🇺🇦
dcoderlt@ohai.socialAustralia really looked at GDPR and said “those fines are rookie numbers, mate”.
(from https://twitter.com/troyhunt/status/1597841957526568966 )
Talos Vulnerability Reports
talosvulnsMicrosoft Windows 10 AllJoyn Router Service information disclosure vulnerability
https://talosintelligence.com/vulnerability_reports/TALOS-2024-1980
CVE-2024-38257,CVE-2024-38257
bert hubert 🇺🇦🇪🇺🇺🇦
bert_hubert@fosstodon.orgAs @echo_pbreyer reminded us, EU member states have revived their effort to force-install a child pornography scanner on our phones again. This idea was rejected twice before, but they'll keep trying. Here's an English transcript of what I said about this in Dutch parliament last year: https://berthub.eu/articles/posts/client-side-scanning-dutch-parliament/
Piotr Bazydło
chudypb@infosec.exchangeMy SharePoint RCE got fixed: CVE-2024-38018. Site Member privs should be enough to exploit.
I also found a DoS vuln that got patched today: CVE-2024-43466.
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2024-38018
buherator
buheratorhttps://www.youtube.com/watch?v=481SI_HWlLs
buherator
buheratorMore info: https://x.com/TinySecEx/status/1833697218983080428
screaminggoat
screaminggoat@infosec.exchangeHappy #PatchTuesday from Microsoft: 79 new CVEs, 4 NEW EXPLOITED ZERO DAYS:
- CVE-2024-43491 (9.8 critical) Microsoft Windows Update Remote Code Execution Vulnerability (EXPLOITED)
- CVE-2024-38226 (7.3 high) Microsoft Publisher Security Feature Bypass Vulnerability (EXPLOITED)
- CVE-2024-38217 (5.4 medium) Windows Mark of the Web Security Feature Bypass Vulnerability (EXPLOITED and PUBLICLY DISCLOSED)
- CVE-2024-38014 (7.8 high) Windows Installer Elevation of Privilege Vulnerability (EXPLOITED)
EDIT: @BleepingComputer has mentioned that CVE-2024-38217 was marked publicly disclosed. Updated this to reflect it. See related reporting Microsoft September 2024 Patch Tuesday fixes 4 zero-days, 79 flaws
#microsoft #vulnerability #zeroday #eitw #activeexploitation #cve
andersonc0d3
andersonc0d3@infosec.exchangeMeasuring non-determinism in the Linux kernel
https://shape-of-code.com/2024/09/08/measuring-non-determinism-in-the-linux-kernel/
screaminggoat
screaminggoat@infosec.exchangeCitrix security advisory: Citrix Workspace app for Windows Security Bulletin CVE-2024-7889 and CVE-2024-7890
Happy #PatchTuesday from Citrix.
- CVE-2024-7889 (CVSSv4: 7.0 high) LPE
- CVE-2024-7890 (CVSSv4: 5.4 medium) LPE
Fixed in Citrix Workspace app for Windows 2405 and later versions, Citrix Workspace app for Windows 2402 CU1 LTSR and later versions. No mention of exploitation.
Talos Vulnerability Reports
talosvulnsAdobe Acrobat Reader Annotation Object Page Race Condition Vulnerability
https://talosintelligence.com/vulnerability_reports/TALOS-2024-2011
CVE-2024-39420
screaminggoat
screaminggoat@infosec.exchangeIvanti security advisory: September 2024 Security Update
Happy #PatchTuesday from Ivanti. There are some serious vulnerabilities. I want to emphasize that Ivanti stated they "have no evidence of these vulnerabilities being exploited in the wild." See the following advisories:
- Security Advisory EPM September 2024 for EPM 2024 and EPM 2022
- Security Advisory Ivanti Cloud Service Appliance (CSA) (CVE-2024-8190)
- Security Advisory Ivanti Workspace Control (IWC)
The big ones:
- CVE-2024-29847 (perfect 10.0 critical 🥳 cc: @cR0w) deserialization in the agent portal of Ivanti EPM before 2022 SU6/September 2024 update allows unauth RCE
- CVE-2024-32840, CVE-2024-32842, CVE-2024-32843, CVE-2024-32845, CVE-2024-32846, CVE-2024-32848, CVE-2024-34783, CVE-2024-34785: unspecified SQL injection in Ivanti EPM before 2022 SU6/September 2024 update allow remote authenticated attacker with admin privileges to RCE
Melanie Imming ✅
meliimming@akademienl.socialIt is shocking that after moving from Google workspace to Proton as the back office for our professional email adresses etc, all the major Dutch institutions are blocking us as spam. All our contacts have to whitelist us individually. So I think we are forced to go back to Google, where we had this problem occasionally but not as massively as now. It seems the reason is that Microsoft, used by almost all institutions in NL, simply blocks all Proton mail .😈 ( DNS=OK configured)
abadidea
0xabad1dea@infosec.exchangeI would like to impress upon product managers that a code security review does not consist of me sitting down with the files in alphabetical order and reading each and every line exactly once in order and checking off whether it is or isn’t secure
Project Zero Bot
p0botis_compat flag in adsprpc driver leads to access of userland provided addresses as kernel pointers
https://project-zero.issues.chromium.org/issues/42451710
CVE-2024-21455
hanno
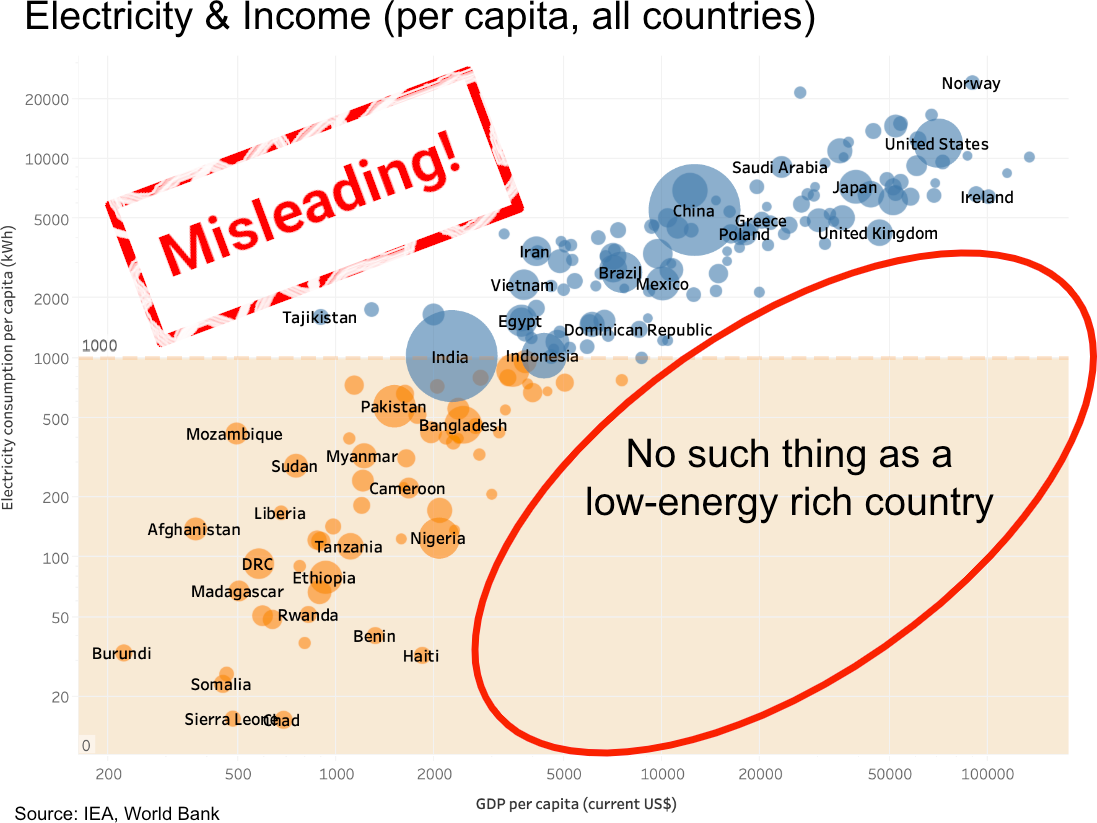
hanno@mastodon.socialThis widely shared infographic uses a trick to make its message appear much stronger than it actually is. It seems to show a strong correlation between energy consumption and the wealth of a country. By using a logarithmic scale, the correlation appears much stronger than it actually is. I covered this before in articles, and now have also uploaded a short video ⚡💸🎥 https://www.youtube.com/watch?v=2xZ6CihdKu0 🧵
buherator
buheratorhttps://www.smokescreen.io/deception-and-kerckhoffss-cryptographic-principle/
(Re: yesterdays fun little shitpost)