Posts
3412Following
713Followers
1582Piotr Bazydło
chudypb@infosec.exchangeMy SharePoint RCE got fixed: CVE-2024-38018. Site Member privs should be enough to exploit.
I also found a DoS vuln that got patched today: CVE-2024-43466.
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2024-38018
screaminggoat
screaminggoat@infosec.exchangeHappy #PatchTuesday from Microsoft: 79 new CVEs, 4 NEW EXPLOITED ZERO DAYS:
- CVE-2024-43491 (9.8 critical) Microsoft Windows Update Remote Code Execution Vulnerability (EXPLOITED)
- CVE-2024-38226 (7.3 high) Microsoft Publisher Security Feature Bypass Vulnerability (EXPLOITED)
- CVE-2024-38217 (5.4 medium) Windows Mark of the Web Security Feature Bypass Vulnerability (EXPLOITED and PUBLICLY DISCLOSED)
- CVE-2024-38014 (7.8 high) Windows Installer Elevation of Privilege Vulnerability (EXPLOITED)
EDIT: @BleepingComputer has mentioned that CVE-2024-38217 was marked publicly disclosed. Updated this to reflect it. See related reporting Microsoft September 2024 Patch Tuesday fixes 4 zero-days, 79 flaws
#microsoft #vulnerability #zeroday #eitw #activeexploitation #cve
Anderson Nascimento
andersonc0d3@infosec.exchangeMeasuring non-determinism in the Linux kernel
https://shape-of-code.com/2024/09/08/measuring-non-determinism-in-the-linux-kernel/
screaminggoat
screaminggoat@infosec.exchangeCitrix security advisory: Citrix Workspace app for Windows Security Bulletin CVE-2024-7889 and CVE-2024-7890
Happy #PatchTuesday from Citrix.
- CVE-2024-7889 (CVSSv4: 7.0 high) LPE
- CVE-2024-7890 (CVSSv4: 5.4 medium) LPE
Fixed in Citrix Workspace app for Windows 2405 and later versions, Citrix Workspace app for Windows 2402 CU1 LTSR and later versions. No mention of exploitation.
screaminggoat
screaminggoat@infosec.exchangeIvanti security advisory: September 2024 Security Update
Happy #PatchTuesday from Ivanti. There are some serious vulnerabilities. I want to emphasize that Ivanti stated they "have no evidence of these vulnerabilities being exploited in the wild." See the following advisories:
- Security Advisory EPM September 2024 for EPM 2024 and EPM 2022
- Security Advisory Ivanti Cloud Service Appliance (CSA) (CVE-2024-8190)
- Security Advisory Ivanti Workspace Control (IWC)
The big ones:
- CVE-2024-29847 (perfect 10.0 critical 🥳 cc: @cR0w) deserialization in the agent portal of Ivanti EPM before 2022 SU6/September 2024 update allows unauth RCE
- CVE-2024-32840, CVE-2024-32842, CVE-2024-32843, CVE-2024-32845, CVE-2024-32846, CVE-2024-32848, CVE-2024-34783, CVE-2024-34785: unspecified SQL injection in Ivanti EPM before 2022 SU6/September 2024 update allow remote authenticated attacker with admin privileges to RCE
Melanie Imming ✅
meliimming@akademienl.socialIt is shocking that after moving from Google workspace to Proton as the back office for our professional email adresses etc, all the major Dutch institutions are blocking us as spam. All our contacts have to whitelist us individually. So I think we are forced to go back to Google, where we had this problem occasionally but not as massively as now. It seems the reason is that Microsoft, used by almost all institutions in NL, simply blocks all Proton mail .😈 ( DNS=OK configured)
abadidea
0xabad1dea@infosec.exchangeI would like to impress upon product managers that a code security review does not consist of me sitting down with the files in alphabetical order and reading each and every line exactly once in order and checking off whether it is or isn’t secure
hanno
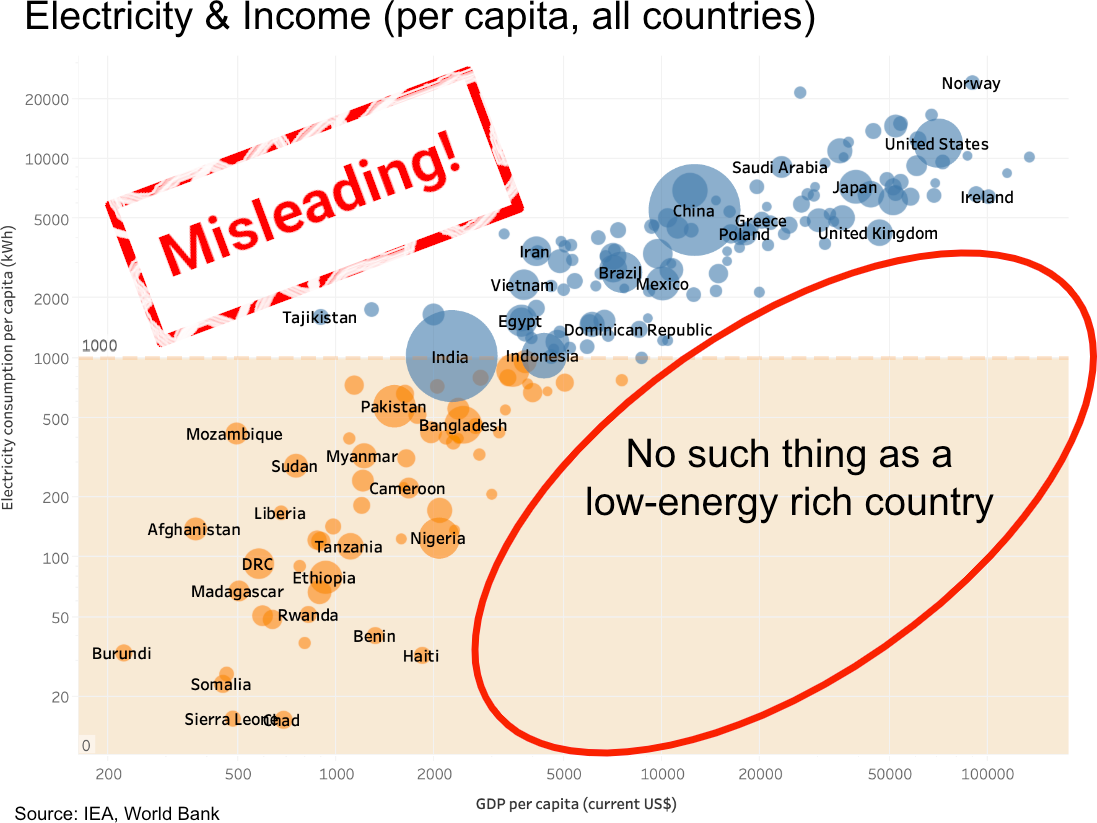
hanno@mastodon.socialThis widely shared infographic uses a trick to make its message appear much stronger than it actually is. It seems to show a strong correlation between energy consumption and the wealth of a country. By using a logarithmic scale, the correlation appears much stronger than it actually is. I covered this before in articles, and now have also uploaded a short video ⚡💸🎥 https://www.youtube.com/watch?v=2xZ6CihdKu0 🧵
Binary Ninja
binaryninja@infosec.exchangeThere is a known issue in the latest stable 4.1.5902 we wanted to make folks aware of. If you save a bndb while debugging, the database can get into an improper state and it may appear to lose user changes. The issue is resolved in the latest dev builds.
For those who are using the latest stable, you can either switch to dev or avoid saving during debugging (saving after debugging is unaffected). Impacted users can contact support (https://binary.ninja/support/) or see: https://github.com/Vector35/debugger/issues/612
screaminggoat
screaminggoat@infosec.exchangewatchTowr: Veeam Backup & Response - RCE With Auth, But Mostly Without Auth (CVE-2024-40711)
Reference: CVE-2024-40711 (9.8 critical, disclosed 04 September 2024 by Veeam) Veeam Backup & Replication: A deserialization of untrusted data vulnerability with a malicious payload can allow an unauthenticated remote code execution (RCE). This vulnerability was reported by reported by Florian Hauser @frycos with CODE WHITE Gmbh @codewhitesec.
watchTowr doing what they do best, root cause analysis of vulnerabilities and breaking it down Barney style. Veeam Backup and Replication's CVE-2024-40711 has an authenticated RCE with a 9.8? watchTowr does patch-diffing (a lot of code and rambling). They name drop James Forshaw @tiraniddo in referencing “Stupid is as Stupid Does When It Comes to .NET Remoting”
Okay in reading through this, CVE-2024-40711 is actually comprised of two separate bugs. Veeam silently patched an improper authorization bug, then the deserialisation bug 3 months later. watchTowr claims that there is a way to bypass CVE-2024-40711 (details are still under embargo). They do not release a proof of concept due to the current situation and proclivity for ransomware actors to go after Veeam backups.
#cve_2024_40711 #vulnerability #rootcauseanalysis #cve #veeam #infosec #cybersecurity
Zig Weekly
zig_discussions@mastodon.socialData-Oriented Design Revisited: Type Safety in the Zig Compiler
https://www.youtube.com/watch?v=KOZcJwGdQok
Discussions: https://discu.eu/q/https://www.youtube.com/watch?v=KOZcJwGdQok
Cedric Halbronn
saidelike@infosec.exchange3 more weeks before my Windows Kernel Exploitation training at #HEXACON2024
Don't miss out! More info on contents -> https://www.hexacon.fr/trainer/halbronn/
raptor 
raptor@infosec.exchange
Mythology Monday ✨
mythologymonday@thefolklore.cafeGreetings, Myth Lovers! In celebration of #BeerLoversDay Monday's theme is beer an other inebriating beverages! Do you know a myth that features beer or a similar drink? Is the beer helpful or a hindrance? Tell us the myth and use the hashtag #MythologyMonday for boosts.
#mythology @mythology @folklore @TarkabarkaHolgy @juergen_hubert @curiousordinary @wihtlore @FairytalesFood @bevanthomas @FinnFolklorist @Godyssey @GaymerGeek @starrytimepod @ljwrites
Sometimes when people don't want an idea interrogated they arrange words around it like a moat. Construct intricate vocabularies that make it so you can only approach it from certain directions, never from the directions where it is weak to attack. Insist you use their vocabulary, debate on their terms. Sometimes I like to just walk directly into the moat. See, it's only ankle deep. This makes people upset. You're ignorant of the theory! No, I'm standing in the middle of it. It's just water dude
Jeremi M Gosney 
epixoip@infosec.exchange
Team #Hashcat is pleased to present our much anticipated write-up for this year's #CrackMeIfYouCan contest at #Defcon32
#password #passwordcracking #redteam #ctf #defcon #hacking #infosec #cybersecurity
technomancy
technomancy@hey.hagelb.orgublock origin is great and so don't take this the wrong way but I've never understood why it doesn't have a they-live mode where instead of removing the ads altogether they get rendered as greyscale messages like "OBEY" / "CONSUME" / "DO NOT QUESTION AUTHORITY"
Brad Rosenheim
Brad_Rosenheim@climatejustice.socialCrypto is holding Texas' independent electricity grid hostage for ransom, while the conservatives who run the state realize they've been duped by the big businesses they sidle up to.
https://www.economist.com/united-states/2024/08/27/why-texas-republicans-are-souring-on-crypto
BrianKrebs
briankrebs@infosec.exchangeSomeone sent me a note the other day that a funeral service for their late friend was being used to start a new Meta group that claimed to offer live streaming of the service.
But of course, those who clicked the link were sent to fake video streaming websites that try to collect payment information before supposedly letting you watch the service.
A little digging showed that not only are there hundreds of these fake funeral streaming groups, but all of them are tied back to some brainiacs in Bangladesh who naturally exposed their identities and operation by trojaning their own PCs.
What's crazy is how the fake funeral streaming groups on Meta are just one tiny microcosm of the scams these dudes in Bangladesh are doing.
Also, now I feel like showering after spending a few hours back on Meta. Eww.