Posts
2520Following
647Followers
1461screaminggoat
screaminggoat@infosec.exchangeIvanti security advisory: September 2024 Security Update
Happy #PatchTuesday from Ivanti. There are some serious vulnerabilities. I want to emphasize that Ivanti stated they "have no evidence of these vulnerabilities being exploited in the wild." See the following advisories:
- Security Advisory EPM September 2024 for EPM 2024 and EPM 2022
- Security Advisory Ivanti Cloud Service Appliance (CSA) (CVE-2024-8190)
- Security Advisory Ivanti Workspace Control (IWC)
The big ones:
- CVE-2024-29847 (perfect 10.0 critical 🥳 cc: @cR0w) deserialization in the agent portal of Ivanti EPM before 2022 SU6/September 2024 update allows unauth RCE
- CVE-2024-32840, CVE-2024-32842, CVE-2024-32843, CVE-2024-32845, CVE-2024-32846, CVE-2024-32848, CVE-2024-34783, CVE-2024-34785: unspecified SQL injection in Ivanti EPM before 2022 SU6/September 2024 update allow remote authenticated attacker with admin privileges to RCE
Melanie Imming ✅
meliimming@akademienl.socialIt is shocking that after moving from Google workspace to Proton as the back office for our professional email adresses etc, all the major Dutch institutions are blocking us as spam. All our contacts have to whitelist us individually. So I think we are forced to go back to Google, where we had this problem occasionally but not as massively as now. It seems the reason is that Microsoft, used by almost all institutions in NL, simply blocks all Proton mail .😈 ( DNS=OK configured)
abadidea
0xabad1dea@infosec.exchangeI would like to impress upon product managers that a code security review does not consist of me sitting down with the files in alphabetical order and reading each and every line exactly once in order and checking off whether it is or isn’t secure
Project Zero Bot
p0botis_compat flag in adsprpc driver leads to access of userland provided addresses as kernel pointers
https://project-zero.issues.chromium.org/issues/42451710
CVE-2024-21455
hanno
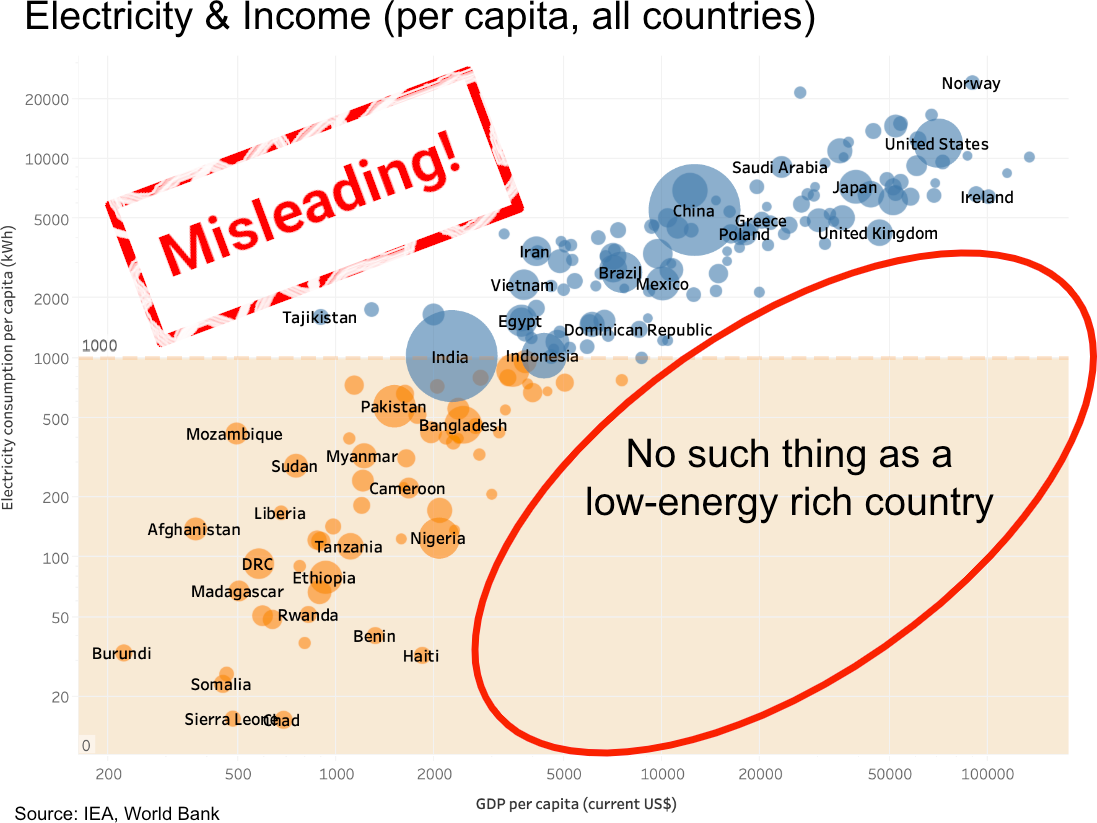
hanno@mastodon.socialThis widely shared infographic uses a trick to make its message appear much stronger than it actually is. It seems to show a strong correlation between energy consumption and the wealth of a country. By using a logarithmic scale, the correlation appears much stronger than it actually is. I covered this before in articles, and now have also uploaded a short video ⚡💸🎥 https://www.youtube.com/watch?v=2xZ6CihdKu0 🧵
buherator
buheratorhttps://www.smokescreen.io/deception-and-kerckhoffss-cryptographic-principle/
(Re: yesterdays fun little shitpost)
buherator
buheratorhttps://blog.convisoappsec.com/en/analysis-of-github-enterprise-vulnerabilities-cve-2024-0507-cve-2024-0200/
Binary Ninja
binaryninja@infosec.exchangeThere is a known issue in the latest stable 4.1.5902 we wanted to make folks aware of. If you save a bndb while debugging, the database can get into an improper state and it may appear to lose user changes. The issue is resolved in the latest dev builds.
For those who are using the latest stable, you can either switch to dev or avoid saving during debugging (saving after debugging is unaffected). Impacted users can contact support (https://binary.ninja/support/) or see: https://github.com/Vector35/debugger/issues/612
screaminggoat
screaminggoat@infosec.exchangewatchTowr: Veeam Backup & Response - RCE With Auth, But Mostly Without Auth (CVE-2024-40711)
Reference: CVE-2024-40711 (9.8 critical, disclosed 04 September 2024 by Veeam) Veeam Backup & Replication: A deserialization of untrusted data vulnerability with a malicious payload can allow an unauthenticated remote code execution (RCE). This vulnerability was reported by reported by Florian Hauser @frycos with CODE WHITE Gmbh @codewhitesec.
watchTowr doing what they do best, root cause analysis of vulnerabilities and breaking it down Barney style. Veeam Backup and Replication's CVE-2024-40711 has an authenticated RCE with a 9.8? watchTowr does patch-diffing (a lot of code and rambling). They name drop James Forshaw @tiraniddo in referencing “Stupid is as Stupid Does When It Comes to .NET Remoting”
Okay in reading through this, CVE-2024-40711 is actually comprised of two separate bugs. Veeam silently patched an improper authorization bug, then the deserialisation bug 3 months later. watchTowr claims that there is a way to bypass CVE-2024-40711 (details are still under embargo). They do not release a proof of concept due to the current situation and proclivity for ransomware actors to go after Veeam backups.
#cve_2024_40711 #vulnerability #rootcauseanalysis #cve #veeam #infosec #cybersecurity
Zig Weekly
zig_discussions@mastodon.socialData-Oriented Design Revisited: Type Safety in the Zig Compiler
https://www.youtube.com/watch?v=KOZcJwGdQok
Discussions: https://discu.eu/q/https://www.youtube.com/watch?v=KOZcJwGdQok
Cedric Halbronn
saidelike@infosec.exchange3 more weeks before my Windows Kernel Exploitation training at #HEXACON2024
Don't miss out! More info on contents -> https://www.hexacon.fr/trainer/halbronn/
Project Zero Bot
p0botPowerVR: DEVMEMXINT_RESERVATION::ppsPMR references PMRs but does not lock their physical addresses
https://project-zero.issues.chromium.org/issues/42451698
CVE-2024-34747
buherator
buheratorhttps://github.com/google/security-research/security/advisories/GHSA-3658-w6j3-w42r
buherator
buheratorhttps://3sjay.github.io/2024/09/08/Windows-Kernel-Pool-Exploitation-CVE-2021-31956-Part1.html?s=09
buherator
buheratorhttps://www.thezdi.com/blog/2024/9/4/exploiting-exchange-powershell-after-proxynotshell-part-1-multivaluedproperty
buherator
buheratorhttps://binarygecko.com/race-conditions-in-linux-kernel-perf-events/
buherator
buheratorhttps://blog.trailofbits.com/2024/09/06/unstripping-binaries-restoring-debugging-information-in-gdb-with-pwndbg/
buherator
buheratorhttps://arxiv.org/abs/2409.01841
Marco Ivaldi
raptor@infosec.exchangebuherator
buheratorhttps://en.wikipedia.org/wiki/Boyce%E2%80%93Codd_normal_form