Posts
2923Following
695Followers
1529
Łukasz 
maldr0id@infosec.exchange
I may be late to the party but today I’ve learned that ASML has installed a kill switch into an extreme ultraviolet lithography machine it has sold to TSMC, allowing it to be shut down if China invades Taiwan.
Jonathan Müller
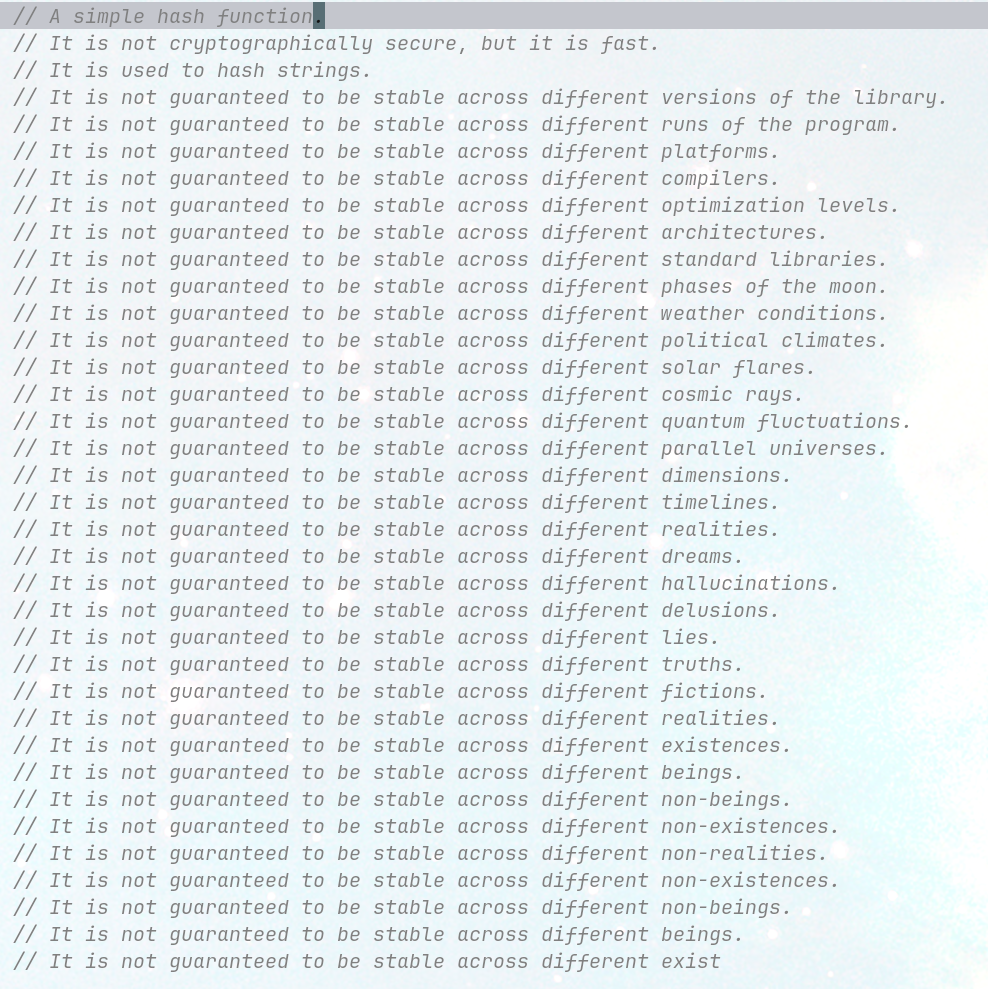
foonathan@fosstodon.orgGitHub copilot seems to be high.
I typed "A simple hash function.", then autocomplete kicked in.
Gregatron5
gregatron5@vmst.ioThis is absolutely nuts. SQL Injection 101 attack on a site authorized by DHS for TSA vetting of known crew members. I’d bet there aren’t even audit logs that would be able to show if the system was tampered with.
How many other auxiliary sites with deep ties into critical infrastructure are this poorly secured?
Dr. Zalka Csenge Virág
TarkabarkaHolgy@ohai.social"Just don't give a damn about what anybody else thinks of you!"
Well that is all nice and dandy, unless the 'anybody else' has the power and means to actively make your life harder.
Because at that point, you realize that not caring what anyone thinks is a privilege.
At the height of One Million Checkboxes's popularity I thought I'd been hacked. A few hours later I was tearing up, extraordinarily proud of some brilliant teens.
Here's my favorite story from running OMCB :)
https://eieio.games/essays/the-secret-in-one-million-checkboxes/
mistymntncop
blackeggs@infosec.exchangeIn light of the issue page for CVE-2024-5274 being made public. Me and @buptsb
have decided to make our exploit public. It's a bit different than the issue page POC.
https://github.com/mistymntncop/CVE-2024-5274/blob/main/exploit.js
Caitlin Condon
catc0n@bird.makeupI was happy to be quoted alongside security research leaders like @dustin_childs and @haifeili on the challenges with (good-faith) coordinated vulnerability disclosure. https://www.csoonline.com/article/3491353/is-the-vulnerability-disclosure-process-a-glitch-in-itself-how-cisos-are-being-left-in-the-dark.html
 radare
radare 
radareorg@infosec.exchange
You can now use the ANGR decompiler with radare2. The old angr integration was renamed to r2angr-io.
Install it like this: r2pm -ci r2angr
jiska 🦄
jiska@chaos.social
Are you living near Paris, female*, and want to learn reverse engineering for free? 📱👩💻 There'll be a 4-day @blackhoodie training at Hexacon!
I'll be giving the training on two days, teaching iOS and Android reversing basics. Register now: https://reversing.training/hc24
Karsten
grayfox@nso.groupLIKE-DBG is a great project to make Linux kernel debugging hassle-free. However, I wanted to use it without docker and I needed the ability to use an external build server. Long story short, I did a fork. Here you go https://github.com/raymontag/like-dbg
Zack Whittaker
zackwhittaker@mastodon.socialNew, by me: Google's Threat Analysis Group found evidence that a group of Russian government hackers, aka APT29, are using exploits that are "identical or strikingly similar" to those previously made by spyware makers Intellexa and NSO Group.
The exploits were found hidden on Mongolian government websites, and designed to steal cookies and passwords, most likely from government employees.
Ivan Kwiatkowski
justicerage@infosec.exchangeI wrote an op-ed today in @lemonde about Durov's arrest. It's paywalled and French-walled too, so I'll post the key points here!
1) You may have noticed that close to nobody in the infosec community (beyond Snowden) is calling for Durov's immediate release. That's because the infosec community knows Telegram has nothing to do with security and TG is not, in fact, a secure messenger. Not by a long shot.
A lot of people have written extensively about this, so I'll just summarize: most chats are only encrypted in transit, and when they are, it's with a proprietary and non-audited protocol. All your data is stored in plaintext on Telegram's servers.
2) It's actually unclear that the authorities view TG as a messenger at all. The indictment uses language that is more fitting to platforms and social media. Elon Musk understands this, which is why he's been vocal about the arrest.
This case IS NOT ABOUT FREE SPEECH. It's about whether platforms should be forced to cooperate with law enforcement (here, on drug / CP cases). EU law says that if problematic content is reported to X/Fb/Linkedin, they must delete it. If they do, they can't be held responsible.
You may disagree. But you cannot frame the situation as "the French government wants to destroy the last bastion of free speech". Also, this is not a political arrest, since prosecutors are independent in France. It's almost certain they didn't ask the government for permission.
3) Most platforms have nothing to worry about. Despite what @andyyen says, there's zero risk for him because he fully cooperates with authorities, which he knows. That was in fact the source of terrible PR for Proton.
The best thing platforms can do to protect themselves is use E2EE everywhere they can and store the least possible user data.
Crucial: don't say no to governments like Durov and go to jail. Create the conditions for your powerlessness. Say "we'd love to but we can't".
4) Maybe the most important point: the battle for free speech and encryption does go on. Telegram never was our champion for this battle and never will. Threats to encryption are still looming in 🇪🇺 and we need to be ready to fight the right battles.
Sector 7
sector7@infosec.exchangeWe have published the 2nd writeup about the EV vulnerabilities we exploited for #Pwn2Own Automotive: the JuiceBox 40.
Despite what the
@thezdi advisories say, these bugs were NOT fixed by the vendor! SiLabs has declared the product EOL and won't fix it.
https://sector7.computest.nl/post/2024-08-pwn2own-automotive-juicebox-40/
Nick Wright
nickthewright@mastodon.art1993: I use BBSes for online interaction. Each BBS is run by some random person. They connect to a federated worldwide network. I keep my notes in .TXT files.
2008-2022: I use social networks like Facebook and Twitter for online interaction. They're huge and popular. I use Evernote for my notes, which is full of features.
2023: I use Mastodon for online interaction. Each instance is run by some random person. They connect to a federated worldwide network. I keep my notes in .TXT files.
0xor0ne
0xor0ne@infosec.exchangeSpace Shuttle Interim Teleprinter reverse engineering
http://www.righto.com/2024/08/space-shuttle-interim-teleprinter.html
screaminggoat
screaminggoat@infosec.exchangeFortra security advisories:
- GoAnywhere MFT (from 14 August 2024): Authentication bypass in GoAnywhere MFT prior to 7.6.0 CVE-2024-25157 (6.5 medium)
- FileCatalyst (from 27 August 2024):
- Insecure Default in FileCatalyst Workflow 5.1.6 Build 139 (and earlier) (9.8 critical) default credentials are published in a vendor knowledgebase article
- SQL Injection in FileCatalyst Workflow 5.1.6 Build 139 (and earlier) CVE-2024-6632 (7.2 high)
No mention of exploitation. But shame on FileCatalyst for having hardcoded credentials. See related Bleeping Computer reporting: Fortra fixes critical FileCatalyst Workflow hardcoded password issue
blacktop
blacktop@mastodon.socialHigh level diff of iOS 18.0 beta 7 vs. iOS 18.0 beta 8 🎉
https://github.com/blacktop/ipsw-diffs/blob/main/18_0_22A5346a__vs_18_0_22A5350a/README.md
.NET
dotnet@dotnet.social📰 BinaryFormatter removed from .NET 9
Starting with .NET 9, we no longer include an implementation of BinaryFormatter in the runtime. This post covers what options you have to move forward.
https://devblogs.microsoft.com/dotnet/binaryformatter-removed-from-dotnet-9/ #dotnet