Posts
3013Following
699Followers
1547.NET
dotnet@dotnet.social📰 BinaryFormatter removed from .NET 9
Starting with .NET 9, we no longer include an implementation of BinaryFormatter in the runtime. This post covers what options you have to move forward.
https://devblogs.microsoft.com/dotnet/binaryformatter-removed-from-dotnet-9/ #dotnet
0patch
0patch@infosec.exchangeMicropatches were released for Windows DWM Core Library Elevation of Privilege Vulnerability (CVE-2024-30051)
0patch
0patch@infosec.exchangeMicropatches were released for "FakePotato" Local Privilege Escalation (CVE-2024-38100)
A-Dub 🥝
adub@kolektiva.socialmy university has converted our office telephones to Microsoft Teams. when i grumbled about this to a favourite sysadmin, this is how they responded 🔥
“Microsoft has actually brilliantly leveraged the lousy security landscape -- for which they are in no small part responsible -- to capture even larger market-share, as we now need commercial entities to produce the software required to protect us from their failures, and therefore need a more uniform environment to achieve the necessary scale. The uniformity then guarantees an ever greater scale for the inevitable conflagration. Monocultures guarantee one big fire instead of a bunch of small survivable ones. We really have no interest in learning from evolution, in no small part because it would produce fewer billionaires.
— Local Cranky IT Guy” [shared with permission]
Jonathan Schofield
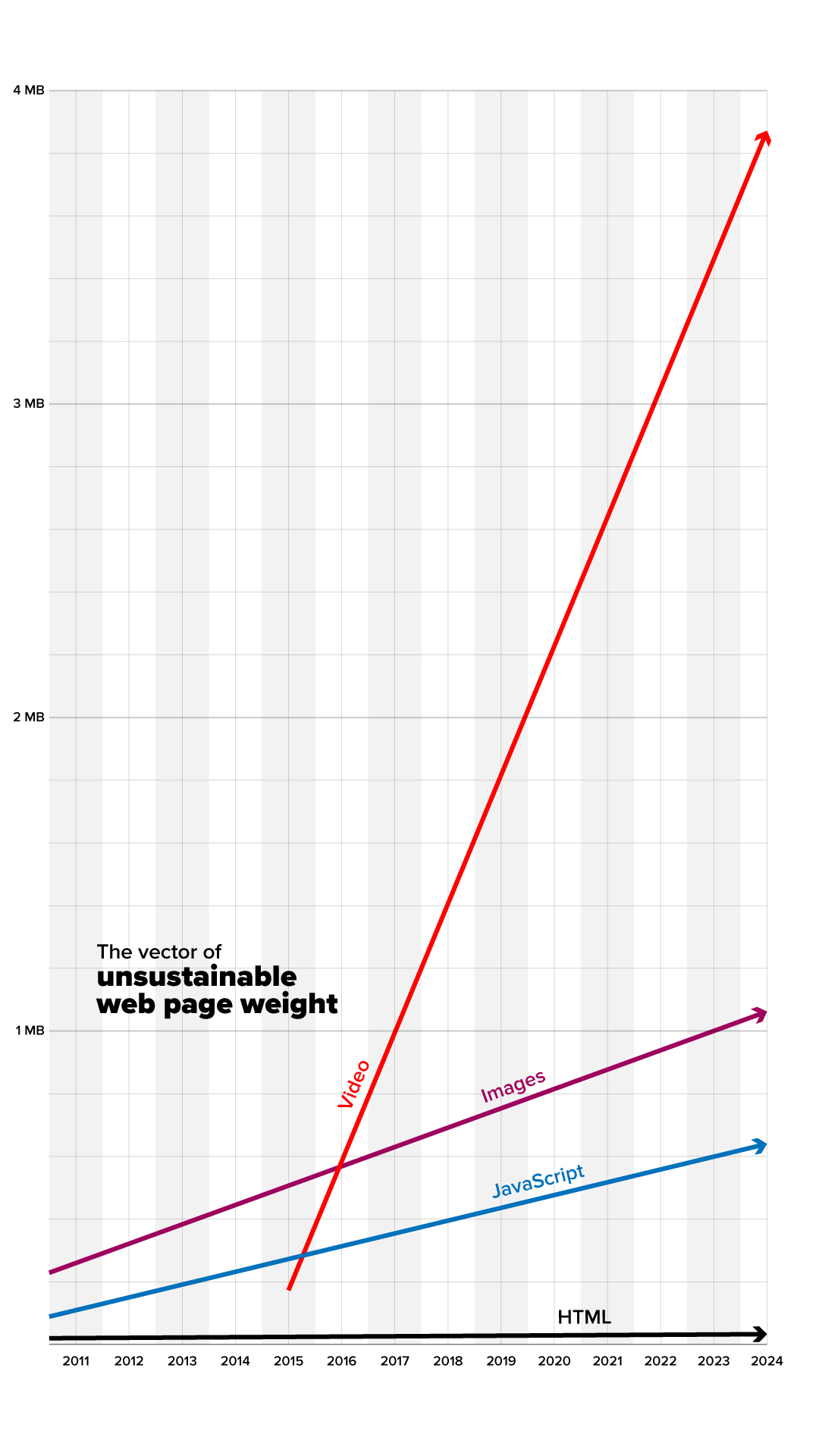
urlyman@mastodon.socialAccording to https://httparchive.org/reports/page-weight, the median weight in KB for web page tech on desktop:
Over the last 14.5 years:
HTML
2010: 20KB;
mid 2024: 33KB;
Increase of 65%.
Images
2010: 229KB;
mid 2024: 1,062KB;
Increase of 464%.
JavaScript
2010: 89KB;
mid 2024: 640KB;
Increase of 719%.
- - -
Over the last 9 years:
Video
mid 2015: 173KB;
mid 2024: 3,872KB;
Increase of 2,238%.
I reckon that in the era of AI the JS gradient is gonna steepen significantly
VirtualWolf
virtualwolf@aus.socialHoly shit, the Rijksmuseum used a 100MP Hasselblad camera to take almost eight and a half THOUSAND photos of the whole of Rembrandt's The Night Watch, for a total image size of 717 GIGAPIXELS. 😳
It's on their website as a zoomable image and you can zoom in so far you can see the individual cracks in the paint: https://www.rijksmuseum.nl/en/stories/operation-night-watch/story/ultra-high-resolution-photo
screaminggoat
screaminggoat@infosec.exchangeCISA: CISA Adds One Known Exploited Vulnerability to Catalog
Hot off the press! CISA adds CVE-2024-38856 (CISA-ADP: 8.1 high) Apache OFBiz Incorrect Authorization Vulnerability to the Known Exploited Vulnerabilities (KEV) Catalog based on evidence of active exploitation.
#CVE_2024_38856 #vulnerability #CVE #Apache #ofbiz #kev #cisa
Trail of Bits
trailofbits@infosec.exchangeWe provisioned cloud infrastructure the Max Power way, showing that AI tools often generate code that works but has terrible security properties.
https://buff.ly/3X54ZSN
Alec Muffett
alecmuffett@mastodon.socialMy understanding of the charges against Pavel Durov & Telegram
https://alecmuffett.com/article/110316
#EndToEndEncryption #PavelDurov #france #telegram
CERT-EU
cert_eu@infosec.exchangeUPDATE: Chrome ZeroDay Vulnerabilities (CERT-EU Security Advisory 2024-088)
A critical zero-day vulnerability, CVE-2024-7971, has been identified and patched in Google Chrome. This marks the ninth such vulnerability discovered in 2024. The flaw, which has been actively exploited in the wild, is rooted in a type confusion issue within Chrome's V8 JavaScript engine. This vulnerability allows attackers to potentially execute arbitrary code on affected systems.
[New] On August 26, Google announced that it patched the tenth zero-day vulnerability in Chrome. This vulnerability is also reported as being exploited.
https://www.cert.europa.eu/publications/security-advisories/2024-088/
/r/netsec
_r_netsec@infosec.exchangeBack to School - Exploiting a Remote Code Execution Vulnerability in Moodle https://blog.redteam-pentesting.de/2024/moodle-rce/
CERT-EU
cert_eu@infosec.exchangeCritical Vulnerability in SonicWall SonicOS (CERT-EU Security Advisory 2024-089)
On August 23, 2024, SonicWall issued a security advisory regarding a critical access control vulnerability (CVE-2024-40766) in its SonicOS. This flaw could allow attackers to gain unauthorised access to resources or cause the firewall crash.
It is recommended updating as soon as possible.
https://www.cert.europa.eu/publications/security-advisories/2024-089/
Miloš
ynwarcs@infosec.exchangeI released a poc & some details for CVE-2024-38063, a RCE vuln in tcpip.sys patched by MS last week: https://github.com/ynwarcs/CVE-2024-38063
Marcus Hutchins 
malwaretech@infosec.exchange
Analyzing and Exploiting CVE-2024-38063, an RCE Vulnerability In the Windows TCP/IP Stack
https://malwaretech.com/2024/08/exploiting-CVE-2024-38063.html
Silent Signal
silentsignal@infosec.exchangeIBM issued a fix to CVE-2024-27275 that mitigates an #IBMi privilege escalation technique we published last year:
🥷https://blog.silentsignal.eu/2023/03/30/booby-trapping-ibm-i/
🧑🏭https://ibm.com/support/pages/node/7157637
The PTF restricts the use of the ADDPFTRG command - this is a breaking change documented in the Memo to Users.
Alec Muffett
alecmuffett@mastodon.socialLiterally 20 years ago we said that French regulations to restrict cryptography without state approval would eventually bite; and we were right…
https://alecmuffett.com/article/110312
#EndToEndEncryption #PavelDurov #backdoors #france #telegram
Lukasz Olejnik
LukaszOlejnik@mastodon.socialCharges against P. Durov (of Telegram). ... Telegram failed to obtain a State permit or registration to use encryption and other cryptography technology? Among others: "Supply of cryptology services to ensure confidentiality functions without functions without a declaration of conformity,
- Supply of a cryptographic means that does not exclusively provide authentication or authentication or integrity control functions without prior declaration,
...
Full text (french): https://www.tribunal-de-paris.justice.fr/sites/default/files/2024-08/2024-08-26%20-%20CP%20TELEGRAM%20.pdf
Mike Sheward
SecureOwl@infosec.exchangeApparently the Polaris Dawn crew are going to be the highest humans have been since the Apollo program, which is surprising given some of the kids I went to high school with.
Dominic White
singe@chaos.socialThis was a keynote I gave to our first BSides in Johannesburg recently. It covers what I think a community needs to do to create great hackers and warns of the dangers of racing to the bottom. While it focuses on South Africa - it’s, I think, more widely useful.
https://youtube.com/watch?v=Ri5DoRRnGWs (or on invidious https://yewtu.be/watch?v=Ri5DoRRnGWs)
cynicalsecurity 
cynicalsecurity@bsd.network
On  but is actually important:
but is actually important:
I quote:
“Intel HW is too complex to be absolutely secure! After years of research we finally extracted Intel SGX Fuse Key0, AKA Root Provisioning Key. Together with FK1 or Root Sealing Key (also compromised), it represents Root of Trust for SGX. Here's the key from a genuine Intel CPU.”