Posts
2706Following
681Followers
1504
cynicalsecurity 
cynicalsecurity@bsd.network
Another SolarWinds RCE vulnerability…
… I instantly had the image from Hunt for Red October when the Soviet ambassador tells the US SecState that they needed help and SecState says "Don't tell me you lost _another_ submarine!"

Mr. Bitterness
wdormann@infosec.exchangeI have some words for the developers who decided that it was completely reasonable to expect a user to be able to precisely hit a single pixel to be able to resize a window.
I've seen this on both Windows and Linux. 🤦♂️
/r/netsec
_r_netsec@infosec.exchangeGNU/Linux Sandboxing - A Brief Review https://hardenedlinux.org/blog/2024-08-20-gnu/linux-sandboxing-a-brief-review/
rostiger
rostiger@merveilles.townMost mirrors of libgen are now down. Anna's Archive is fighting to keep the lights on.
https://annas-archive.org/
daniel:// stenberg://
bagder@mastodon.socialLast year on this day the bogus #curl CVE arrived that triggered a series of events that subsequently made #curl become a CNA.
https://daniel.haxx.se/blog/2023/08/26/cve-2020-19909-is-everything-that-is-wrong-with-cves/
0xor0ne
0xor0ne@infosec.exchangeBrief intro on how to use eBPF for syscalls tracing
Carnage4Life
carnage4life@bird.makeupAndy Jassy talks about the benefits Amazon is seeing from their AI coding assistant. It’s widespread that devs are more productive with these tools.
The question is whether this is like accountants and Excel where it creates jobs or travel agents & the web where it kills them.
Linux Kernel Security
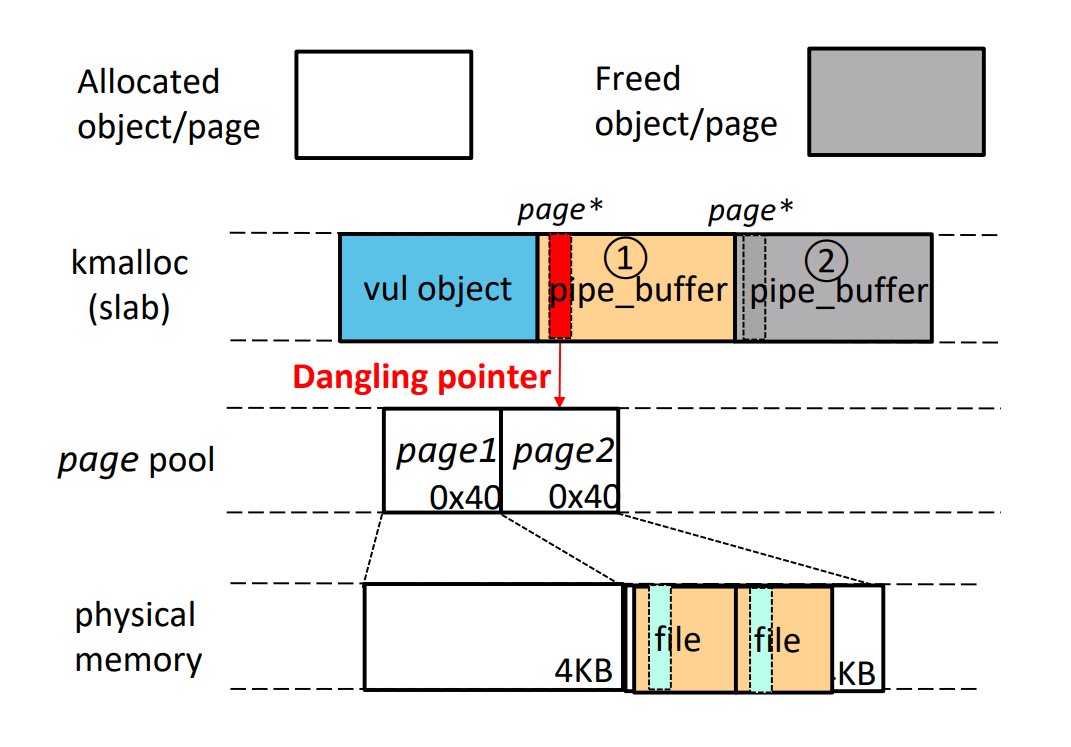
linkersec@bird.makeupPageJack: A Powerful Exploit Technique With Page-Level UAF
A talk by @pkqzy888 et al. about overwriting slab objects containing a `struct page *` field to achieve arbitrary read/write in physical memory.
Jiří Vinopal
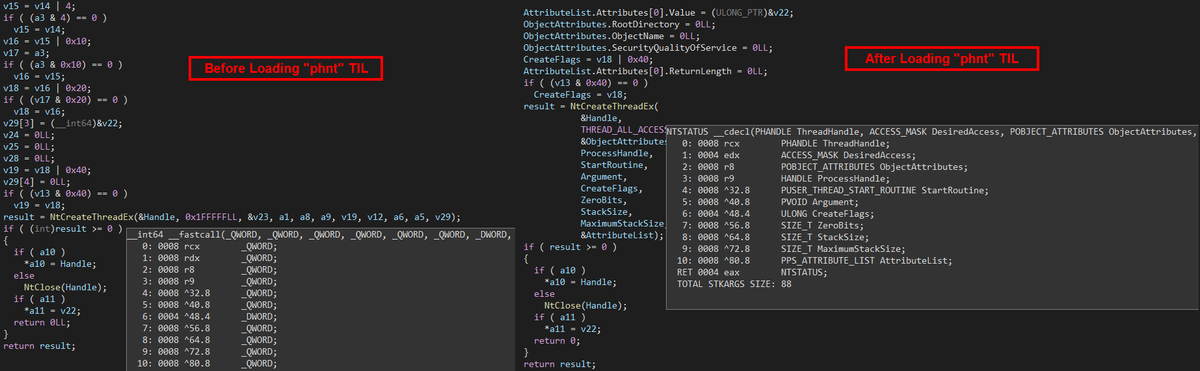
vinopaljiri@bird.makeupSo I made a thing ☺️
Converted #phnt (Native API header files from the System Informer project) to #IDA TIL, IDC.
To import "phnt" types and function definitions to IDA and help with Reverse Engineering.
@hexrayssa @mrexodia
Introducing #IDA_PHNT_TYPES:
https://github.com/Dump-GUY/IDA_PHNT_TYPES
Display Name
Teufelchen@hal9.oooBeing a C programmer in 2024 is so ridiculous, look what I need to do! Every (!) evening I have to charge my sacrifice cats, complete the ritual and pray to the gods just to be as memory safes as Ru^\x00
Programm terminated with signal SIGSEGV, Segmentation fault
Matthew Green
matthew_d_green@ioc.exchangeApropos Pavel Durov’s arrest, I wrote a short post about whether Telegram is an “encrypted messaging app”. https://blog.cryptographyengineering.com/2024/08/25/telegram-is-not-really-an-encrypted-messaging-app/
kravietz 🦇
kravietz@agora.echelon.pl#Telegram is a tricky ecosystem from security perspective, because it’s quite diverse and complex:
- Public groups and chats are widely used by both #Russia and #Ukraine. These include both publicly available and “private” (invite-only) chats neither can be really considered secret because…
- …group chats can’t be end-to-end encrypted (E2EE), so their contents are readable to at least Telegram operators, probably as easily as running a single SQL query.
- Telegram bots don’t support E2EE either.
So here’s an important distinction: while Telegram is great and highly usable for disseminating public or semi-public information (unencrypted public or invite-only groups), it’s quite poor for highly confidential communications. Yet, especially the Russian side uses it a lot for just that - there are reports of “secret groups” used for front-line command or control, correction of fire or as a channel for communication with spies and collaborators in Ukraine. Except these “secret groups” really aren’t, at least not in OPSEC and cryptographic sense (groups can’t use E2EE in Telegram).
This is one purely marketing win for Telegram, because even mainstream journalists notoriously confuse these concepts.
Yes, it is technically possible that a Russian operator opens an actual “secret chat” with each of his collaborator, but it’s highly impractical and I doubt majority of them do it.
Which is further confirmed by the panic caused by detention of Durov in Russian military channels 🤷
In any case, France taking over Telegram infrastructure is still highly speculative - the main point of the arrest is almost complete lack of moderation in Telegram, even for the most severe CSAM (child abuse) content.
While in Russia arrest of Durov would likely lead to his genitals being connected to a field telephone in order to convince him to hand over the infrastructure (that’s why he ran away from Russia in the first place), in #France he will be likely just subject to a regular, boring law enforcement process that ends with a trial and suspended sentence, at best, if he agrees to improve content moderation. Part of the panic in Russia is that Russian routinely project the practices of their own law enforcement onto everyone else.
Kevin Rothrock
kevinrothrock@infosec.exchangeCSAM = child sexual abuse material. Telegram implicitly allows it in private groups and direct messages. Telegram won't work with the police even if it's found on public channels. https://cyber.fsi.stanford.edu/io/news/addressing-distribution-illicit-sexual-content-minors-online
Ivan Kwiatkowski
justicerage@infosec.exchangeAccording to @AFP, @durov was arrested at a 🇫🇷 airport a few hours ago. Sources say he will most likely be jailed.
He is basically being held responsible for all the illegal activities taking place on Telegram and failing to cooperate with law enforcement to make it stop.
Key takeaway for software companies: E2EE protects you just as much as it protects users.
Durov can only be accused of not cooperating insofar as he technically could, if he wanted to.
Like it or don't, this could never happen with Signal.
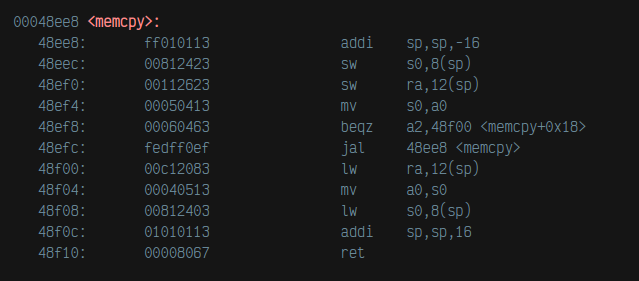
oh my fucking god. so i was having a problem when i enabled optimizations when compiling the doom port. memcpy ended up overwriting itself. so i looked into what was happening, and apparently memcpy just kept calling itself over and over. the reason? i was compiling my own version of memcpy, because i wasn't using the standard library, but i also didn't use the "-ffreestanding" flag, so gcc assumed i *did* have the standard library. so gcc, in its infinite wisdom, saw a memcpy-like pattern in my memcpy and turned it into another call to memcpy, resulting in a stack overflow.
Addison
addison@nothing-ever.worksNew rants for today:
- PCRE2 and fun testing difficulties: https://secret.club/2024/08/23/ring-around-the-regex-2.html
- Ruminations on fuzzer evaluations: https://addisoncrump.info/research/thinking-about-fuzzer-evaluation/
Ben Hawkes
hawkes@infosec.exchange"OpenSSH Backdoors" -- a few thoughts on supply-chain attacks against OpenSSH, and what we can learn from both historical and modern events. https://blog.isosceles.com/openssh-backdoors/
vga256
vga256@dialup.cafetwelve years ago, a painter by the name of anders ramsell painted 12,597 aquarelle paintings of blade runner, shot by shot, of the entire film edited down to ~35 minutes. it took two years of painstaking work, all done in his spare time after work each night.
the video circled around the web for a few years, and quietly disappeared from every single site it was hosted at.
a few months ago i spent a few hours digging for it, and finally found a copy of the original file.
i'm not sure how long it will last over at IA, so enjoy it while you can. it is a true achievement. 🙏