Posts
2371Following
534Followers
1243Heretek of Silent Signal
buherator
buherator"Being 'smart' is not actually about knowing all the answers. One of the biggest parts is being aware of the limits of your knowledge and not running around like a headless chicken when you don’t know what to do."
https://fgiesen.wordpress.com/2016/02/05/smart/
buherator
buherator- Shared X11 socket with the host so you can use the GUI (runs on Linux)
- Bind mounts the Binary Ninja directory to the container, so you can share your local installation
- Sets $HOME to the mounted Binary Ninja directory, so license information and plugins are stored in one location and persist across runs
- Executes Binary Ninja GUI from xterm so you can restart the GUI to apply updates
https://github.com/v-p-b/binaryninja-docker
(On a related note, it would be *so* nice if @binaryninja documented their dependencies so I wouldn't need to figure them out one-by-one based on Qt debug prints...)
WHY2025 Productiehuis
productiehuis@chaos.social1 #million views! Today is a momentous day for the #WHY2025 #MCH2022 #SHA2017 Youtube account.
The video of a talk called "Non-Euclidean Doom: what happens to a game when pi is not 3.14159…" reached 1 million views on Youtube a few minutes ago.
The video is of course also on media.ccc.de and has reached almost a hundred thousand views there.
The recommended way to watch the video is https://media.ccc.de/v/mch2022-236-non-euclidean-doom-what-happens-to-a-game-when-pi-is-not-3-14159-, but if you want proof of the milestone, check out https://youtu.be/_ZSFRWJCUY4
/r/netsec
_r_netsec@infosec.exchangeCVE-2024-41660: A Critical Vulnerability in OpenBMC https://tetrelsec.com/posts/cve-2024-41660-slpd-lite/
/r/netsec
_r_netsec@infosec.exchangeMIFARE Classic: exposing the static encrypted nonce variant https://eprint.iacr.org/2024/1275.pdf
AttackerKB
attackerkbTopic description: "Windows TCP/IP Remote Code Execution Vulnerability ..."
"On August 13, 2024, Microsoft disclosed CVE-2024-38063, an integer underflow vulnerability ([CWE-191](https://cwe.mitre.org/data/definitions/191.html)) affecting the IPv6 component of the Windows TCP/IP networking stack ..."
Link: https://attackerkb.com/assessments/92c8c4df-81fd-426e-bf53-60a08563d643
buherator
buheratorhttps://hackaday.com/2024/08/16/rebuilding-the-first-digital-personal-computer/
GrapheneOS
GrapheneOS@grapheneos.socialWired was manipulated into spreading misinformation to market Palantir and iVerify by misrepresenting a vulnerability in a disabled demo app as being a serious problem which could be exploited in the real world. They should retract the article but won't.
https://wired.com/story/google-android-pixel-showcase-vulnerability/
buherator
buheratorIt's hard to disconnect OT networks that are presumed to be segmented physically, and temporary physical control can easily translate to permanent cyber control."
https://seclists.org/dailydave/2024/q3/8
Trammell Hudson
th@v.stFor #CircuitPythonDay2024 I'm porting Micropython to the SensorWatch SAML22J18 that fits in the classic Casio FT-91W. https://www.sensorwatch.net/
It's the Freya's day today so let's run another #nakeddiefriday why don't we.
Today I got a #French classic form 1983, one of the very first chip cards. The micromodule is a very characteristic shape of those designed by Bull.
On the die itself, the EEPROM array is in the very center, with the address counter to the right, drivers above and the data multiplexer below.
Note the designer initials, C.B. and Y.G.
Hi-res: https://siliconpr0n.org/archive/doku.php?id=infosecdj:bull:et1001
Linuxiac
linuxiac@mastodon.socialClamAV Antivirus 1.4 ends 32-bit Linux support, introduces ARM64 packages for Windows, improves ALZ and LHA archive handling, and more.
https://linuxiac.com/clamav-antivirus-1-4-ends-32-bit-linux-support/
buherator
buheratorShow content
https://monumentofmisanthropydm.bandcamp.com/album/vile-postmortem-irrumatio
CERT-EU
cert_eu@infosec.exchangeZabbix Server Critical Arbitrary Code Execution Vulnerability (CERT-EU Security Advisory 2024-082)
On August 13, 2024, a critical vulnerability, CVE-2024-22116, was disclosed in Zabbix Server, allowing attackers with restricted administrative permissions to execute arbitrary code. The flaw, identified in the Ping script execution within the Monitoring Hosts section, can compromise the entire infrastructure. The vulnerability carries a CVSS score of 9.9.
https://www.cert.europa.eu/publications/security-advisories/2024-082/
Marcus Hutchins 
malwaretech@infosec.exchange
Has anyone else looked at CVE-2024-38063? I could use a sanity check here. From what I can see, the vulnerable code path can only be triggered with IPv6 Jumbograms (packets larger than 65535 bytes). Not only would the target system need to have Jumbograms enabled, but every link in the path between the attacker and target would have to both support Jumbograms and have them enabled. I can't imagine any real world scenario in which this would occur, so unless I'm missing something, this vulnerability could only be exploited on very few real world systems.
Hacker News
hkrn@mstdn.socialCartoon Network's Website Was Deleted. That Should Scare You All
L: https://slate.com/technology/2024/08/david-zaslav-warner-bros-discovery-culture-deleting-movies-tv-shows.html
C: https://news.ycombinator.com/item?id=41262878
posted on 2024.08.15 at 23:25:16 (c=0, p=5)
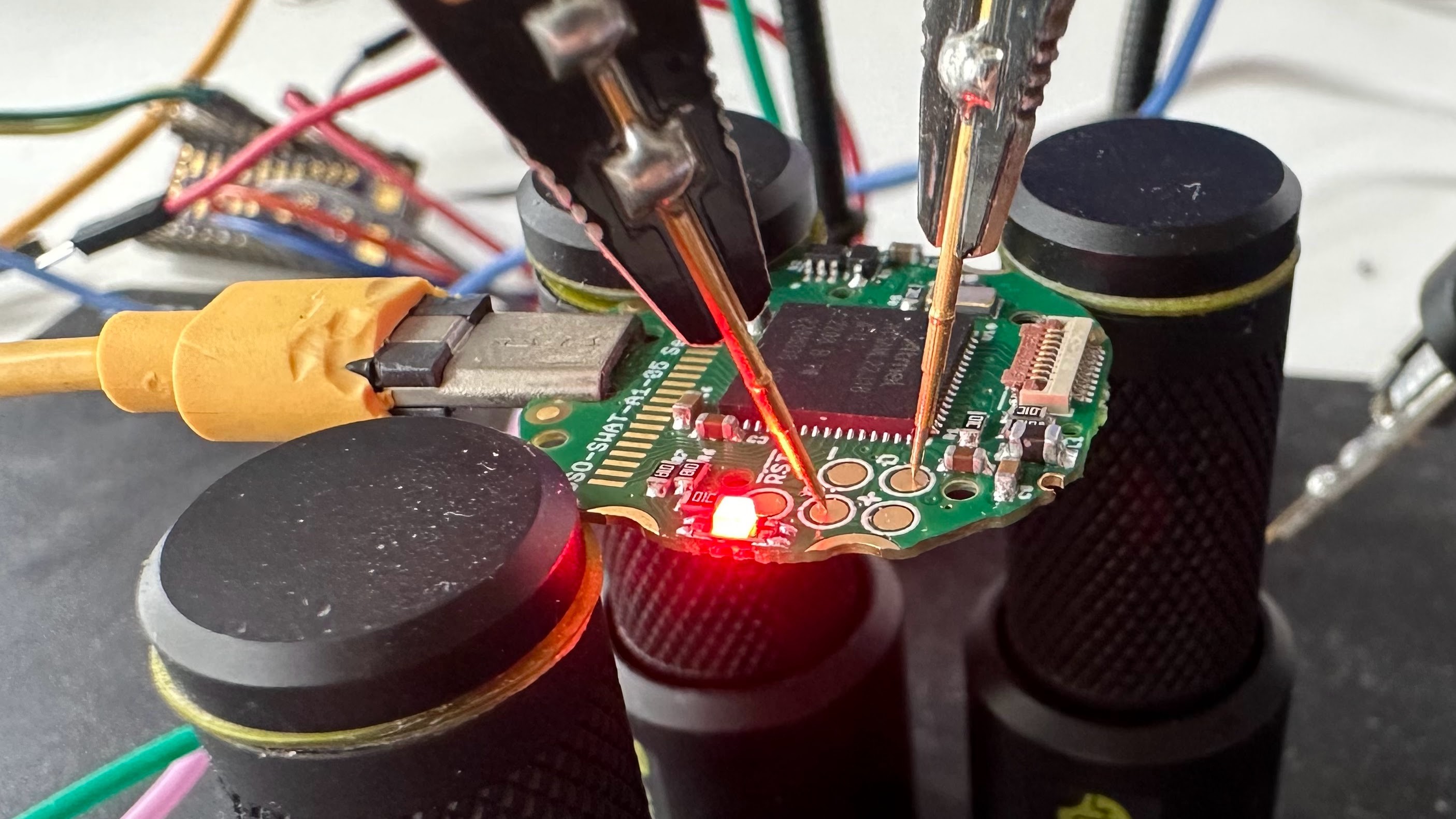
stacksmashing
stacksmashing@infosec.exchangeWhen I got started with hardware hacking etc @travisgoodspeed was (and is) one of my heroes.
Now there’s a chapter in his new (awesome) book on a vuln I found. Feels awesome.
Thanks Travis for all your contributions to our community.
Also, you should buy his book!
buherator
buheratorRE: https://infosec.exchange/@kaoudis/112966710334172131
kaoudis
kaoudis@infosec.exchangehttps://www.usenix.org/conference/usenixsecurity24/presentation/qi System-level emulation and instrumentation is generally slow, but there’s a neat insight into when instrumentation *isn’t* necessary and what basic blocks to not instrument for QEMU-based system-level concolic execution in this work!
Guy Dupont
gvy_dvpont@mastodon.socialTired of using your own tongue to test 9V batteries???
👅👅👅🔋🔋🔋 ouch!
Honored and humbled to announce my latest product: