Posts
2506Following
650Followers
1470screaminggoat
screaminggoat@infosec.exchangeElastic: Dismantling Smart App Control
Elastic claims that Windows Smart App Control and SmartScreen have several design weaknesses that allow attackers to gain initial access with no security warnings or popups. A bug in the handling of LNK files can also bypass these security controls. They research bypasses for reputation-based systems and develop detections to identify indicators of attack. No CVE IDs associated.
See related The Hacker News reporting: Researchers Uncover Flaws in Windows Smart App Control and SmartScreen
buherator
buheratorhttps://hvg.hu/itthon/20240805_Feltorte-a-Neptun-rendszert-es-maganak-utalta-el-a-diakok-osztondijat-a-csalo-ebx
I'd like to note that In my time we wouldn't think of stealing from broke-ass students like ourselves...also had proper RCE's :P
#Hungary #Neptun
buherator
buheratorhttps://hackaday.com/2024/07/25/pnut-a-self-compiling-c-transpiler-targeting-human-readable-posix-shell/
buherator
buheratorhttps://hackaday.com/2024/08/05/proof-that-find-mkdir-are-turing-complete/
buherator
buheratorhttps://code-white.com/blog/teaching-the-old-net-remoting-new-exploitation-tricks/
buherator
buheratorhttps://www.thezdi.com/blog/2024/7/31/breaking-barriers-and-assumptions-techniques-for-privilege-escalation-on-windows-part-3
buherator
buheratorhttps://security.humanativaspa.it/extending-burp-suite-for-fun-and-profit-the-montoya-way-part-6/
buherator
buheratorhttp://blog.quarkslab.com/heap-exploitation-glibc-internals-and-nifty-tricks.html
buherator
buheratorhttps://dustri.org/b/decrypting-vpn-traffic-via-crashdumps.html
buherator
buheratorhttps://msrc.microsoft.com/blog/2024/07/introducing-the-msrc-researcher-resource-center/
buherator
buheratorhttps://shellypalmer.com/2024/07/why-googles-dear-sydney-ad-makes-me-want-to-scream/
(The ad was revoked, but this is still a great piece about the fundamental problems it represented)
Haroon Meer
haroonmeer@infosec.exchange“Crowdstrike has made intentional architectural engineering and QA decisions that made this happen. They were negligent in their engineering decisions and their QA decisions.”
@alexstamos starts off strong on his latest @riskybiz episode.
Note to sec company CTOs/CISOs:
If u put in the work to engage with the community on topics that don’t directly affect what u are selling, it buys u some leeway when u have to discuss products that do..
Many would be flamed for taking this stance openly. He pulls it off.
Jack Daniel (often offline)
jack_daniel@mastodon.socialFifteen years ago today, a group of hackers and security pros got together and made a little thing happen, the first ever BSides @SecurityBSidesGlobal, @BSidesLV
Things took off from there.
The next BSides on the event calendar is BSides Las Vegas, and it will be event number 1002.
NetBlocks
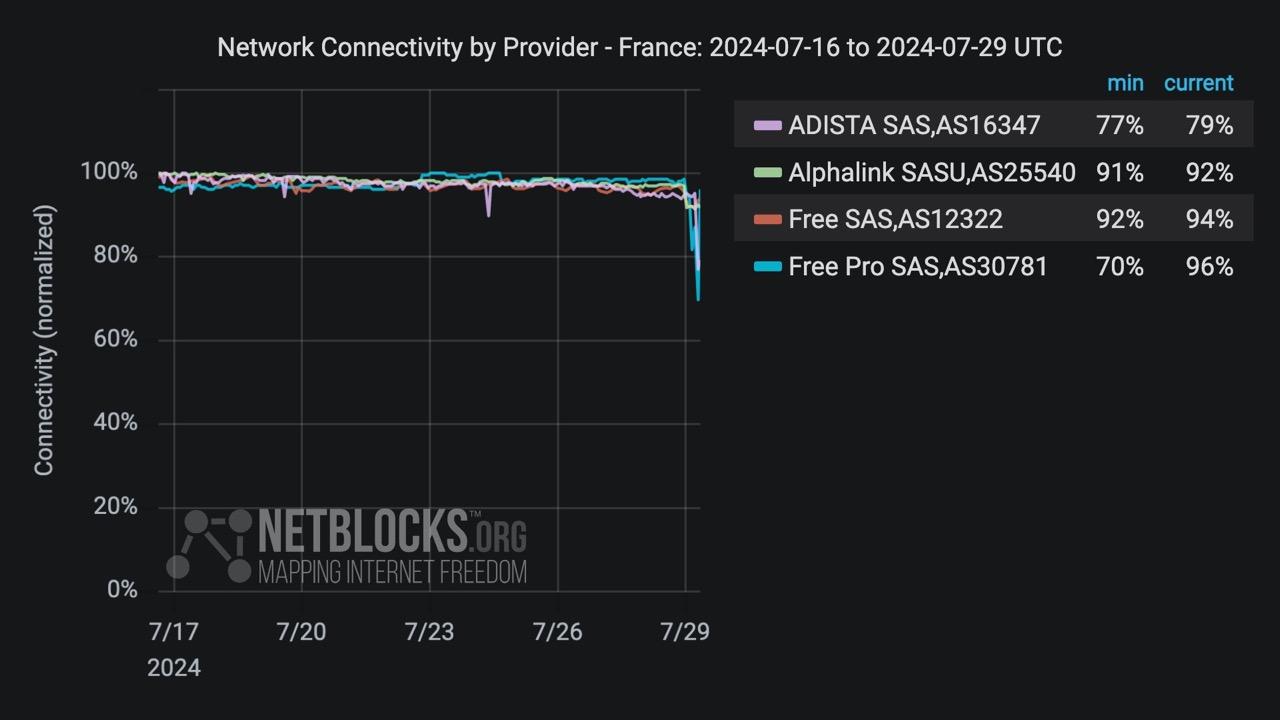
netblocks@mastodon.social⚠️ Confirmed: Network data show disruptions to multiple internet providers in #France amid reports of a fibre sabotage campaign targeting telecoms infrastructure during the Paris 2024 Olympics 📉
int*dmi;*dmi=0 // --> WHY2025
domi@donotsta.reprotip: when referring to your favourite programming language’s features, call them spells instead to sound more mysterious and cool.
 “memory safety feature”
“memory safety feature”
 “memory safety spell”
“memory safety spell”
Dare Obasanjo
carnage4life@mas.toA really “inspirational” Google ad about a young girl who’s inspired by an Olympic athlete so her dad asks Google’s Gemini AI to write the athlete a letter from his daughter.
It’s actually an effective anti-AI ad which plays to the fear AI drains the creativity and honesty out of human communication. 🤦🏾♂️
I found out quite a lot of stuff by now about the Ghidra stack depth mess up and still have no idea how to fix it... 😩
https://github.com/NationalSecurityAgency/ghidra/issues/6747
Simon Tesla 🏳️🌈🐭
SimonTesla@chitter.xyzsomeone just shared this picture with me and I am so mad this is a thing that somebody thought was a good idea, or even not a terrible idea
dwizzzle
dwizzzle@infosec.exchangeMy new blog - featuring: a technical overview of the CrowdStrike incident, why security products user kernel mode, and what this means for the future of Windows.
Shout outs to my non-Microsoft friends who gave me input and technical editing, appreciate you!