Posts
3498Following
717Followers
1583Dare Obasanjo
carnage4life@mas.toA really “inspirational” Google ad about a young girl who’s inspired by an Olympic athlete so her dad asks Google’s Gemini AI to write the athlete a letter from his daughter.
It’s actually an effective anti-AI ad which plays to the fear AI drains the creativity and honesty out of human communication. 🤦🏾♂️
I found out quite a lot of stuff by now about the Ghidra stack depth mess up and still have no idea how to fix it... 😩
https://github.com/NationalSecurityAgency/ghidra/issues/6747
Simon Tesla 🏳️🌈🐭
SimonTesla@chitter.xyzsomeone just shared this picture with me and I am so mad this is a thing that somebody thought was a good idea, or even not a terrible idea
dwizzzle
dwizzzle@infosec.exchangeMy new blog - featuring: a technical overview of the CrowdStrike incident, why security products user kernel mode, and what this means for the future of Windows.
Shout outs to my non-Microsoft friends who gave me input and technical editing, appreciate you!
Ryan Townsend (old account)
ryantownsend@webperf.social👏 more 👏 developers 👏 need 👏 👏 hear 👏 this
I can count on one hand the number of my clients over the past couple of years who haven't either over-architected for scale or were unnecessarily concerned about it.
You don't need to understand Distributional Little's Law to figure this out, it's obvious with primary school level math.
Excerpt from https://tailscale.com/blog/new-internet
Kenn White
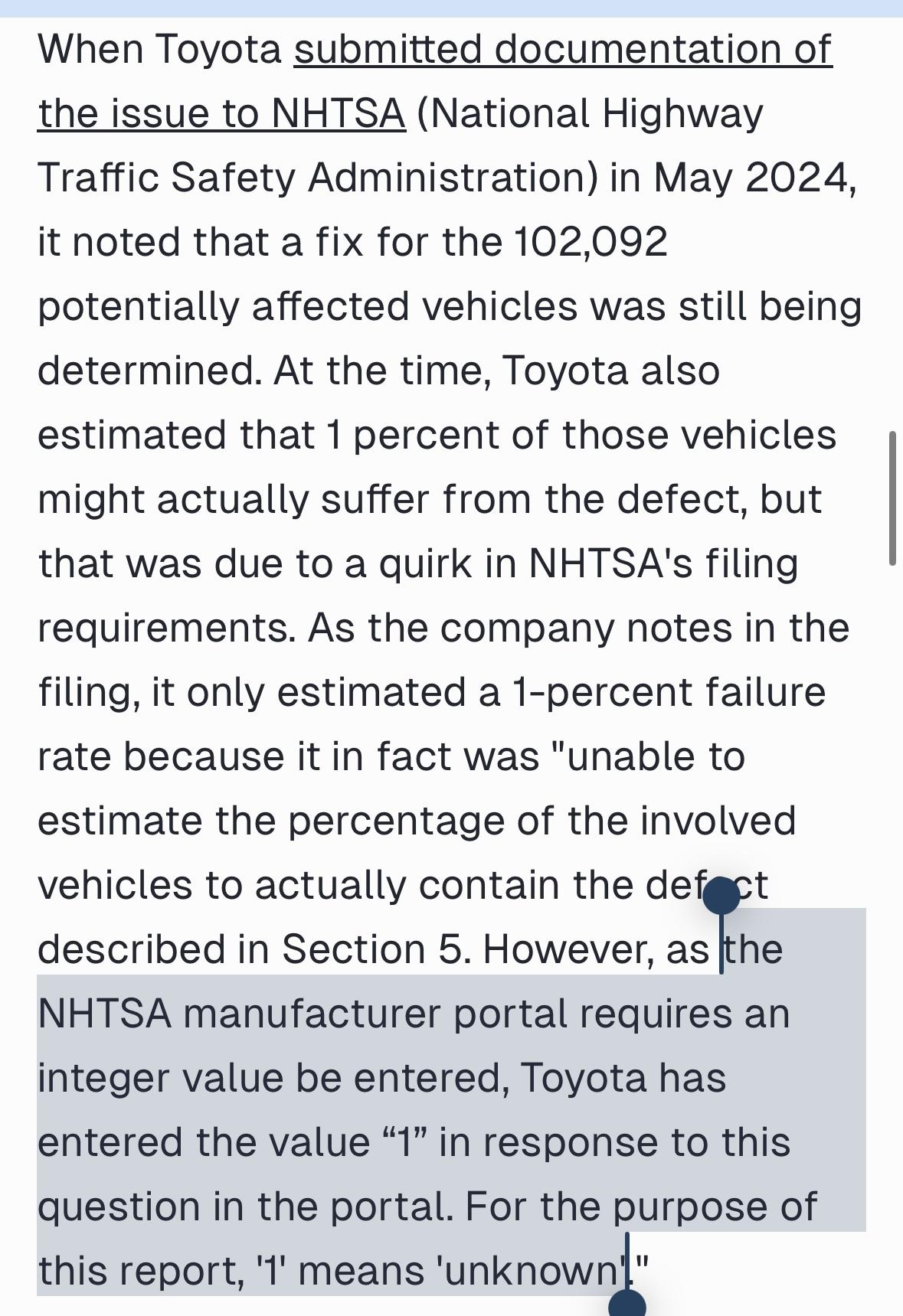
kennwhite@mastodon.socialInteresting nugget in this story on the historic mass recall to replace 100,000 engines in Toyota trucks & Lexus SUVs: When Toyota first reported the problem to the government, the total # of vehicles hadn't been determined, but NHTSA's website required an "integer value" in the percentage of vehicles impacted field, but "1" also meant "unknown". [insert Do You Even UX Bro gif]
https://www.motortrend.com/news/toyota-engine-recall-tundra-pickup-lexus-lx-suv/
AWS in GovcCoud US-East _accidentally_ upgrading MySQL from 5.7.X to 8.X.
DevOpsBorat was right. Error is human, automatically upgrading a database fleet to a new major MySQL version is #devops .
No opportunity goes to waste ;-)
https://www.theverge.com/2024/7/26/24206719/microsoft-windows-changes-crowdstrike-kernel-driver
Alberto Ruiz
aruiz@mastodon.socialI just wrote some initial ramblings on my attempt to write a Rust based bootloader for Open Firmware/ppc64le
https://siliconislandblog.wordpress.com/2024/07/25/booting-with-rust-chapter-1/
Dominic White
singe@chaos.socialI once had the pleasure of working with @mslaviero, and miss his smarts and wit. This blog post on how @ThinkstCanary architects for security is worth a read for many reasons - but the biting insight delivered with a chuckle is what I’m most enjoying.
https://blog.thinkst.com/2024/07/unfashionably-secure-why-we-use-isolated-vms.html
Daniel J. Bernstein
djb@mastodon.cr.yp.toGave a burst of new talks over the past week, including intros to (1) patents, (2) timing variations in crypto code, (3) modern tools to avoid bugs in rewriting snippets to run in constant time, and, on the more mathematical side, (4) cola cryptography: https://cr.yp.to/talks.html
Binary Ninja
binaryninja@infosec.exchangeOur UEFI support added in 3.5 continues to improve! 4.1 released last week adds TE support, platform types for SMM, PEI, and PPI and updates to EFI Resolver.
https://binary.ninja/2024/07/17/4.1-elysium.html#uefi-enhancements
And we're not done, keep an eye out for an in-progress blog post with more details.
/r/netsec
_r_netsec@infosec.exchangeNew OpenSecurityTraining2 mini-class: "Debuggers 1102: Introductory Ghidra" https://p.ost2.fyi/courses/course-v1:OpenSecurityTraining2+Dbg1102_IntroGhidra+2024_v2/about
Mr. Bitterness
wdormann@infosec.exchangeBinarly's PKFail:
Yet another way that SecureBoot is broken. This time it's due to manufacturers like Acer, Dell, Gigabyte, Fujitsu, HP, Intel, Lenovo, and SuperMicro using test/public keys to secure the kingdom. (The Platform Key (PK))
https://www.binarly.io/blog/pkfail-untrusted-platform-keys-undermine-secure-boot-on-uefi-ecosystem
Surely my no-name (Beelink) cheapo Chinese PC does the right thing, right?
Oh...
"DO NOT TRUST - AMI Test PK"
Nobody could possibly know what that could imply.
N O B O D Y
Kenn White
kennwhite@mastodon.socialCloud nerds will enjoy this. Cryptographer Tal Be'ery reverse engineered AWS session tokens and has a detailed write-up.
https://medium.com/@TalBeerySec/revealing-the-inner-structure-of-aws-session-tokens-a6c76469cba7
TrendAI Zero Day Initiative
thezdi@infosec.exchangeIn June, we disclosed several vulnerabilities in the Deep Sea Electronics DSE855. Today, ZDI analyst @infosecdj provides his in-depth analysis of the bugs and their root causes. He includes the timeline for disclosure. https://www.zerodayinitiative.com/blog/2024/7/25/multiple-vulnerabilities-in-the-deep-sea-electronics-dse855
Binary Ninja
binaryninja@infosec.exchangeRunning an ARM Linux machine but still want to do RE? Or maybe you're a sad apple silicon user who misses running native VMs you could use your regular tooling in. With Binary Ninja 4.1, our stable branch includes ARM Linux support!
https://binary.ninja/2024/07/17/4.1-elysium.html#linux-arm-builds
Nikoloz K.
nikolozk@infosec.exchangeIn the trenches, security and IT teams are the real heroes. The CrowdStrike incident crashed 8.5M Windows devices, and IT worked around the clock to restore systems. But did they get the recognition they deserved from leadership? Too often, their efforts go unnoticed while facing unrealistic expectations. As leaders, we must have their backs - publicly appreciate their work, ensure they have resources, and advocate for them to the C-suite. That's how we build resilient, high-performing teams.
screaminggoat
screaminggoat@infosec.exchangeProgress Telerik security advisories (edit: plural):
- Insecure Deserialization Vulnerability - CVE-2024-6327 (9.9 critical, disclosed 24 July 2024) In Progress Telerik Report Server versions prior to 2024 Q2 (10.1.24.709), a remote code execution attack is possible through an insecure deserialization vulnerability.
- Object Injection Vulnerability - CVE-2024-6096 In Progress Telerik Reporting versions prior to 18.1.24.709, a code execution attack is possible through object injection via an insecure type resolution vulnerability.
No mention of exploitation.
Why you should care about CVE-2024-6327: FIVE Telerik vulnerabilities are known exploited vulnerabilities, TWO specifically called Progress Telerik. One in particular, CVE-2019-18935, is a deserialization of untrusted data vulnerability. This is the same one exploited against the U.S. government last year as noted by CISA on 15 June 2023: Threat Actors Exploit Progress Telerik Vulnerabilities in Multiple U.S. Government IIS Servers. Patch your Teleriks.
cc: @cR0w @tas50 @campuscodi