Posts
2520Following
646Followers
1460buherator
buheratorhttps://threadreaderapp.com/thread/1814733681849667734.html
buherator
buheratorhttps://threadreaderapp.com/thread/1814762302337654829.html
Nicolas SAPA 
nico@ublog.byme.at
I am able to confirm that #NetBSD 10 and #Linux 4.13 are able to run as domU PV.
The journey was very long:
#pkgsrc 2018Q3 provided a lot of help and sometime tiny annoyances.
I had to build 3 compilers: gcc 4.4, gcc 4.8 and gcc 6.4.
I had to downgrade #ocaml to version 4.00.1, rewriting xentools42 Makefile to use my downgrade and kill xen' ocaml binding (because file not found in pkg install).
I had to force some version of GCC to build some packages - pkgsrc helped there.
Recent version of Linux doesn't seem to boot, the ramdisk/initrd for old Linux is broken, the xm stack seem more broken than the xl stack.
But I was able to run 2 domU PV on i386!
cynicalsecurity 
cynicalsecurity@bsd.network
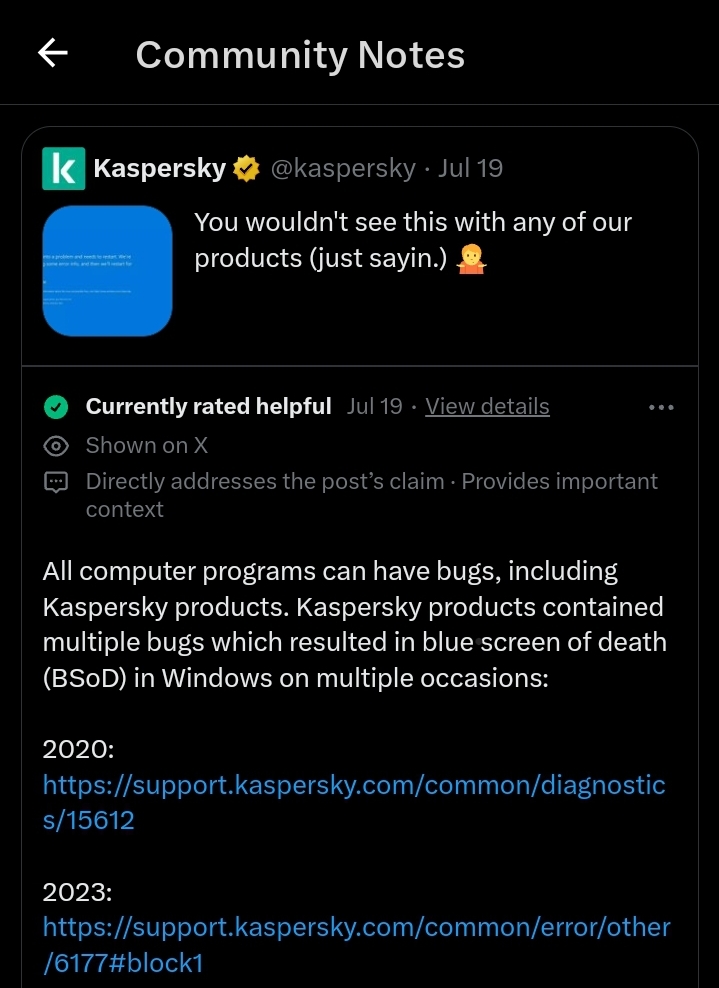
#crowdstrike T&Cs¹, paragraph 8.6 (HT: @JdeBP ), as usual the bit in caps is the best one:
TO THE MAXIMUM EXTENT PERMITTED UNDER APPLICABLE LAW, CROWDSTRIKE AND ITS AFFILIATES AND SUPPLIERS SPECIFICALLY DISCLAIM ALL IMPLIED WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE, TITLE, AND NON-INFRINGEMENT WITH RESPECT TO THE OFFERINGS AND CROWDSTRIKE TOOLS. THERE IS NO WARRANTY THAT THE OFFERINGS OR CROWDSTRIKE TOOLS WILL BE ERROR FREE, OR THAT THEY WILL OPERATE WITHOUT INTERRUPTION OR WILL FULFILL ANY OF CUSTOMER’S PARTICULAR PURPOSES OR NEEDS. THE OFFERINGS AND CROWDSTRIKE TOOLS ARE NOT FAULT-TOLERANT AND ARE NOT DESIGNED OR INTENDED FOR USE IN ANY HAZARDOUS ENVIRONMENT REQUIRING FAIL-SAFE PERFORMANCE OR OPERATION. NEITHER THE OFFERINGS NOR CROWDSTRIKE TOOLS ARE FOR USE IN THE OPERATION OF AIRCRAFT NAVIGATION, NUCLEAR FACILITIES, COMMUNICATION SYSTEMS, WEAPONS SYSTEMS, DIRECT OR INDIRECT LIFE-SUPPORT SYSTEMS, AIR TRAFFIC CONTROL, OR ANY APPLICATION OR INSTALLATION WHERE FAILURE COULD RESULT IN DEATH, SEVERE PHYSICAL INJURY, OR PROPERTY DAMAGE.
So very sorry for airports, airlines, hospitals and many other victims covered by the above… it says you shouldn't have used it even if we sold it to you.

Adrian Sanabria
sawaba@infosec.exchangeSome absolute legend figured iut how to automate the Crowdstrike fix with a combo of WinPE and PXE
buherator
buheratorhttps://threadreaderapp.com/thread/1814343502886477857.html
 radare
radare 
radareorg@infosec.exchange
Need some more info to manage your calendar?
r2con2024 will happen in Barcelona on November 8, 9.
There will be two days of competitions, workshops and presentations. Get ready to share knowledge and have fun with friends!
We can’t spoil the location yet, so stay tuned for further updates!
Martin Seeger
masek@infosec.exchangeConcerning CrowdStrike:
We are now at t+26h. Please compare how much we knew about the xz-attack after less than a day with what we know about the chain of events of giant outage yesterday.
If something similar had been caused by an OSS component, we would see congress discussing a ban on open software in critical infrastructure already.
Jonas Wisser
jwisser@wandering.shopAs a manager, one of the most valuable things you can do is to model asking "dumb" questions—that is, questions that show ignorance about things you "should" know.
"Better to remain silent and be thought a fool than to speak and remove all doubt" may be all well and good in a social context, but in a professional context you have to be willing to ask questions that unlock information you need—even if you feel self-conscious about your current ignorance.
Foone🏳️⚧️
foone@digipres.clubgood lord. I pulled a microSD card out of a Raspi inside an IoT product and it appears they had some developer use a raspi to develop/test some software, and then they just yanked the SD card out of that machine and duped it on to all of their deployed products.
it's got .bash_history of the development process! there's git checkouts of private repos! WHY WOULD YOU DO THIS?
buherator
buheratorOn the other hand we know that relevant .sys artifacts are DRM'd and user-specific.
I wouldn't be surprised if the issue was related to DRM, at least in the sense that full, DRM-enabled end-to-end testing was not implemented and/or some DRM-introduced bug.
Amit Serper  🎗️
🎗️
0xamit@infosec.exchange
The ambulance chasing by some companies (of which I used to work at) over the crowdstrike issue is disgusting.
Stuart
calamari@mastodon.socialIn an unexpected turn of events, a sensible take on #Crowdstrike from the Orange Site.
Kevin Beaumont
GossiTheDog@cyberplace.socialObvious point - the CrowdStrike worldwide IT incident is not the fault of one CrowdStrike staff member.
Whoever created the signature or pushed the button does not operate in isolation. It’s a company with a $73bn market cap.
They need to, later, go back and look at everything that went wrong.
Ernie Smith
ernie@writing.exchangeSouthwest’s tech debt hurt it back in 2022 but it seems to be doing it some favors today.
Old Windows taketh away, but sometimes old Windows giveth.
https://www.digitaltrends.com/computing/southwest-cloudstrike-windows-3-1/
EDIT: Fix date
EDIT: @peterbutler pushed me to do a little more research, and I’m more comfortable saying it the underlying software probably dates to Windows NT or XP.
Jonathan Kamens 86 47
jik@federate.socialThe thing I hope is alarming people about today's #CrowdStrike outage is that if the company can take out that much of America's tech infrastructure by accident with a single buggy update, our adversaries can do the same on purpose with a supply-chain attack against CrowdStrike, and that one probably wouldn't be as quick to recover from. #infosec
hanno
hanno@mastodon.socialLet's cut the bullshit and spell out a few things. The IT security industry is about as trustworthy as the food supplement and vitamin industry, but somehow they escaped the same reputation. Their products are overwhelmingly based on flawed ideas, and the quality of their software is exceptionally bad. And while not everyone will agree with the harshness of my words, I'll say this: Essentially everyone in IT security who knows anything in principle knows this.