Posts
3420Following
714Followers
1582screaminggoat
screaminggoat@infosec.exchangeJetBrains: TeamCity 2024.07 Is Here
I hate JetBrains but enough of you use TeamCity to report on this. TeamCity has a new version 2024.07 which came out today. Buried deep in their release notes is the only indication that any vulnerabilities were patched.
19 security problems have been fixed.
At this time of this toot, JetBrains' own Fixed security issues page is missing the 2024.07 dropdown option so they don't even identify any CVE IDs. A search for TeamCity on cve.mitre.org doesn't show any new CVEs since 01 July 2024.
Ever since JetBrains' feud with Rapid7 in March 2024, they are convinced that silent patching is the appropriate way to handle vulnerabilities. Now your customers don't even know why they should upgrade their TeamCity, or what n-day vulnerability they're being exploited with.
Patch your TeamCity. TeamCity vulnerabilities are known to be exploited by ransomware groups. cc: @campuscodi
TrendAI Zero Day Initiative
thezdi@infosec.exchangeAnnouncing #Pwn2Own Ireland! Our fall contest is on the move (again) as we head to Cork, Ireland. We also welcome @meta as a sponsor with #WhatsApp being a target at $300K. Plus the return of the SOHO Smashup. Read all the details at https://www.zerodayinitiative.com/blog/2024/7/16/announcing-pwn2own-ireland-2024 #P2OIreland
Joxean Koret (@matalaz)
joxean@mastodon.socialI will be speaking and doing a #Diaphora workshop at this year's #44CON conference (@44CON), in London.
https://44con.com/44con-2024-talks-and-workshops/
Haifei Li
haifeili@bird.makeupWhen I saw crash occurred in this stack trace I was in WoW..
02 Excel!RunMacro+0xxxxx
03 Excel!Run+0xxxxx
More digging showed that this seems not really as what you may think (bypassing of Office Macro warnings). :) Anyway.. MSRC has been notified.
Haroon Meer
haroonmeer@infosec.exchangeHeh.. Just discovered that some corp-phishing-simulation sites send mangled Canarytoken alerts to tempt security teams/SoC's to click..
Fate.. Irony.. etc..
/r/netsec
_r_netsec@infosec.exchangeWindows Installer Custom Actions Privilege Escalation Vulnerability https://blog.doyensec.com/2024/07/18/custom-actions.html
Binary Ninja
binaryninja@infosec.exchangeBinary Ninja 4.1 (Elysium) is now live! With new control flow recovery, improved types, decompiling two new architectures, a native linux arm client, improved types across all platforms, and many more changes, it's got something for absolutely everyone.
Andrew Zonenberg
azonenberg@ioc.exchangeI finally got around to setting up a personal website / blog again!
It's at https://serd.es because I bought the domain years ago planning to do this and only recently had the time to sit down and make it happen.
I kicked it off with a short series introducing the major parts of the embedded platform I'm building, but I'll try and do more in-depth posts in the future about stuff I'm working on that's not practical to do in a toot. Generally speaking I'll continue to post live updates here and the blog will be for slightly more finished milestones or subsystem completions.
Feedback (on content or site structure/layout) welcome, I'm not a web dev!
I went with a blog-formatted fork of the GitHub Pages "hacker" theme but changed the font to be more readable than the monospace it used, and made a few other small tweaks. Fully static with no scripting (server or client side) whatsoever, just build-time templating to generate static HTML.
Taggart 
mttaggart@infosec.town
CVE-2024-20401: Cisco Secure Email Gateway Arbitrary File Write Vulnerability
CVSS Base 9.8: Critical
A vulnerability in the content scanning and message filtering features of Cisco Secure Email Gateway could allow an unauthenticated, remote attacker to overwrite arbitrary files on the underlying operating system.
I’m sure @screaminggoat already alerted about this and I missed it, but here you go.
Actually there’s a whole slew of Cisco advisories today. Check them out here.
Dan Goodin
dangoodin@infosec.exchangeCisco just disclosed a maximum-security vulnerability in its on-premises Smart Software Manager. It allows threat actors to log into the device as an existing user. It's still not clear to me what harm the threat actor could do, since the purpose of this device is to provide a dashboard of licenses. Cisco says:
"A successful exploit could allow an attacker to access the web UI or API with the privileges of the compromised user."
But I still don't know if this means the hacker can only enumerate Cisco products used or something more harmful.
Can anyone help?
quarkslab
quarkslab@infosec.exchangeCreating an OCI image from source code that can run on any cloud could be very challenging. Quarkslab assessed the security of Cloud Native Builpacks, a tool for creating ready-to-use OCI images directly from source code. The report is available here: https://blog.quarkslab.com/audit-of-cloud-native-buildpacks.html
Lukasz Olejnik
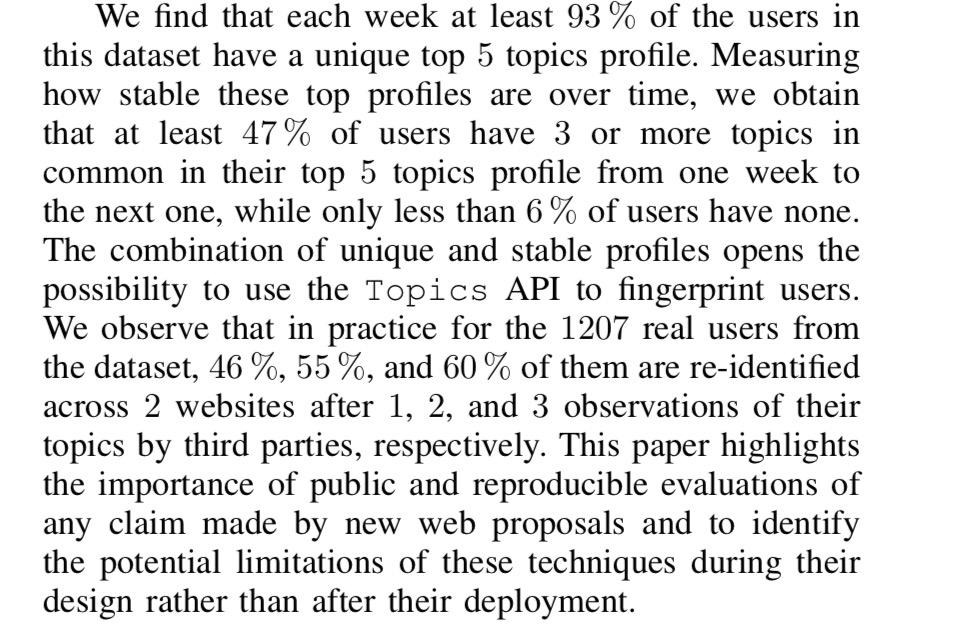
LukaszOlejnik@mastodon.socialInteresting privacy evaluation of Topics API suggesting that privacy toll may be significant. This evaluation is based on a small dataset of browsing histories (n=1027). Do you think the results would hold for realistic datasets? I have some doubts (from experience of work on 200k bigger dataset). However, such evaluations of the privacy-utility tradeoff are unambiguously needed, and good. https://arxiv.org/pdf/2403.19577v1
~swapgs
swapgs@infosec.exchangeElectron Userland just released a patch for a code signature bypass in electron-updater for Windows I found a few weeks back (CVE-2024-39698): https://github.com/electron-userland/electron-builder/security/advisories/GHSA-9jxc-qjr9-vjxq. I'll likely publish a write-up in the coming weeks, it's a fun one ;-)
Mr. Bitterness
wdormann@infosec.exchangeAt some point in the past I had outlined how "BYOVD protection" is a lie. If you're bringing your own driver, you're an admin. And if you're an admin, you can do what you want.
After much unnecessary delay, here is the second part of my blog series, which dives into the blurry lines between "vulnerable" and "not vulnerable" when it comes to Windows drivers.
TL;DR: In some future version of Windows, we may see "vulnerable driver" being able to be defined in a way that it could be protected against. But in the current world that we live in, BYOVD protection simply makes no sense.
https://vu.ls/blog/byovd-protection-is-a-lie-pt2/
Wladimir Palant
WPalant@infosec.exchangeSome great research from Germany. The journalists were able to get a “preview” from a data broker with locations of 11 million German advertising IDs over the period of two months. For free, no questions asked, merely claiming to be interested in buying a subscription.
The dataset appears to be compiled from multiple sources and has some quality issues: some locations are only approximate, occasional wrong timestamps, duplicate entries with different advertising IDs. Yet in many cases it is easily possible to find the person behind the movement profile and to learn details about their lives that definitely weren’t meant to be public knowledge.
That’s your installed apps (or rather advertising SDKs they are built with) selling whatever data they can get to anyone willing to pay. I wish I could recommend disabling GPS and the issue is solved. But even though GPS is the source of the most precise location data, it isn’t the only one. The data broker industry is out of control.
rev.ng
revng@infosec.exchange🔴 Check out our presentation at @passthesaltcon:
Path Of rev.ng-ance: From Raw Bytes To CodeQL On Decompiled Code (30 minutes)
TrendAI Zero Day Initiative
thezdi@infosec.exchangeUncoordinated Vulnerability Disclosure: After more than a decade of CVD, has it benefited vendors or researchers more? Have the number of bugs increased to where vendors simply cannot cope with CVD? @TheDustinChilds has some thoughts - & lots of questions. https://www.zerodayinitiative.com/blog/2024/7/15/uncoordinated-vulnerability-disclosure-the-continuing-issues-with-cvd
Hacker News 50
hn50@social.lansky.nameSeiko Originals: The UC-2000, A Smartwatch from 1984
Link: https://www.namokimods.com/en-ca/blogs/namokitimes/seiko-originals-the-uc-2000-a-smartwatch-from-1984
Discussion: https://news.ycombinator.com/item?id=40969808
Joxean Koret (@matalaz)
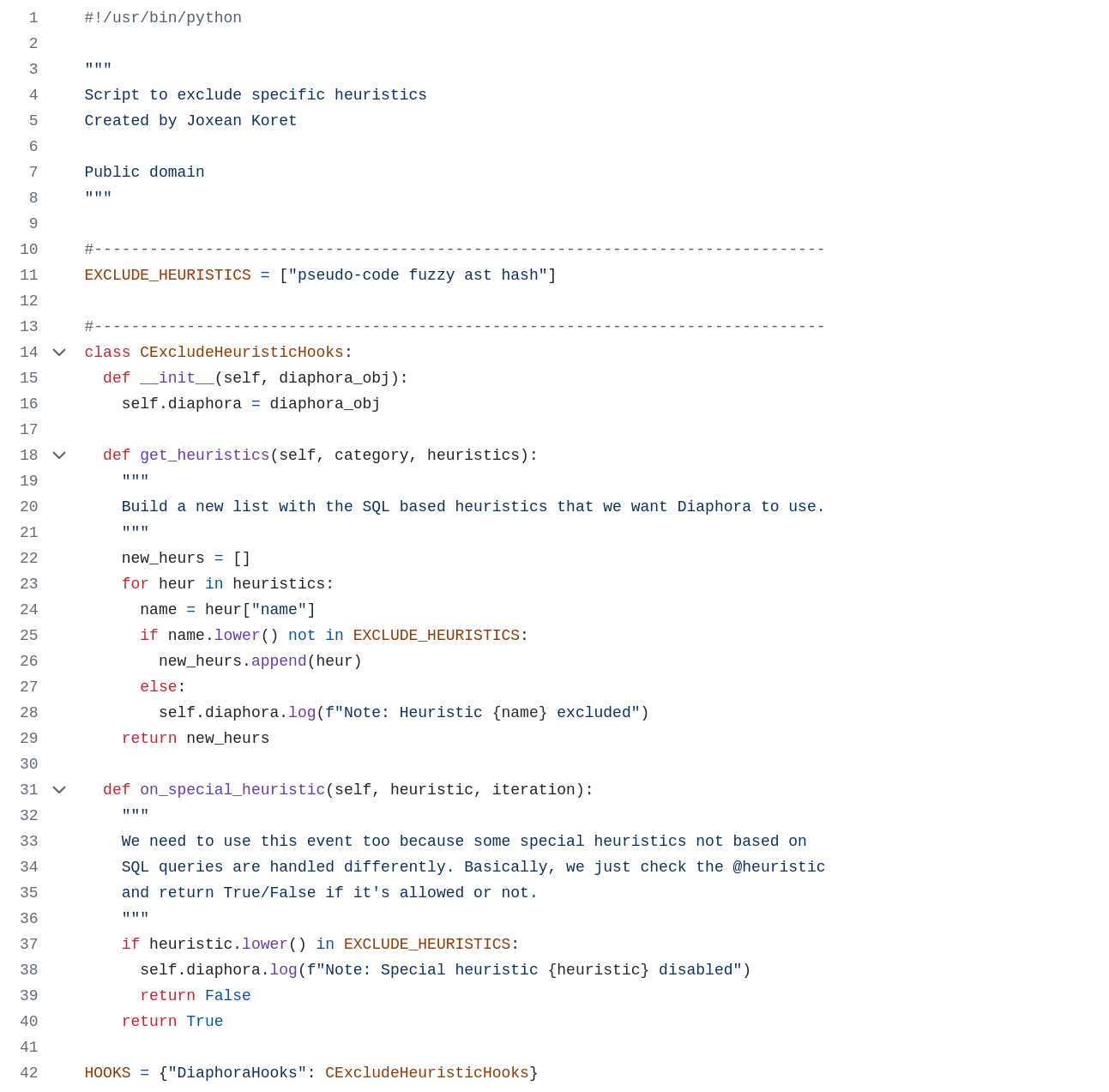
joxean@mastodon.socialYesterday I wrote a script for #Diaphora for cases in which you want to disable a set of heuristics for the current two binaries being diffed for whatever reason. Here is the example script:
https://github.com/joxeankoret/diaphora/blob/master/doc/examples/hooks/exclude_heuristics.py