Posts
3323Following
710Followers
1575Lukasz Olejnik
LukaszOlejnik@mastodon.socialInteresting privacy evaluation of Topics API suggesting that privacy toll may be significant. This evaluation is based on a small dataset of browsing histories (n=1027). Do you think the results would hold for realistic datasets? I have some doubts (from experience of work on 200k bigger dataset). However, such evaluations of the privacy-utility tradeoff are unambiguously needed, and good. https://arxiv.org/pdf/2403.19577v1
~swapgs
swapgs@infosec.exchangeElectron Userland just released a patch for a code signature bypass in electron-updater for Windows I found a few weeks back (CVE-2024-39698): https://github.com/electron-userland/electron-builder/security/advisories/GHSA-9jxc-qjr9-vjxq. I'll likely publish a write-up in the coming weeks, it's a fun one ;-)
Mr. Bitterness
wdormann@infosec.exchangeAt some point in the past I had outlined how "BYOVD protection" is a lie. If you're bringing your own driver, you're an admin. And if you're an admin, you can do what you want.
After much unnecessary delay, here is the second part of my blog series, which dives into the blurry lines between "vulnerable" and "not vulnerable" when it comes to Windows drivers.
TL;DR: In some future version of Windows, we may see "vulnerable driver" being able to be defined in a way that it could be protected against. But in the current world that we live in, BYOVD protection simply makes no sense.
https://vu.ls/blog/byovd-protection-is-a-lie-pt2/
Wladimir Palant
WPalant@infosec.exchangeSome great research from Germany. The journalists were able to get a “preview” from a data broker with locations of 11 million German advertising IDs over the period of two months. For free, no questions asked, merely claiming to be interested in buying a subscription.
The dataset appears to be compiled from multiple sources and has some quality issues: some locations are only approximate, occasional wrong timestamps, duplicate entries with different advertising IDs. Yet in many cases it is easily possible to find the person behind the movement profile and to learn details about their lives that definitely weren’t meant to be public knowledge.
That’s your installed apps (or rather advertising SDKs they are built with) selling whatever data they can get to anyone willing to pay. I wish I could recommend disabling GPS and the issue is solved. But even though GPS is the source of the most precise location data, it isn’t the only one. The data broker industry is out of control.
rev.ng
revng@infosec.exchange🔴 Check out our presentation at @passthesaltcon:
Path Of rev.ng-ance: From Raw Bytes To CodeQL On Decompiled Code (30 minutes)
TrendAI Zero Day Initiative
thezdi@infosec.exchangeUncoordinated Vulnerability Disclosure: After more than a decade of CVD, has it benefited vendors or researchers more? Have the number of bugs increased to where vendors simply cannot cope with CVD? @TheDustinChilds has some thoughts - & lots of questions. https://www.zerodayinitiative.com/blog/2024/7/15/uncoordinated-vulnerability-disclosure-the-continuing-issues-with-cvd
Hacker News 50
hn50@social.lansky.nameSeiko Originals: The UC-2000, A Smartwatch from 1984
Link: https://www.namokimods.com/en-ca/blogs/namokitimes/seiko-originals-the-uc-2000-a-smartwatch-from-1984
Discussion: https://news.ycombinator.com/item?id=40969808
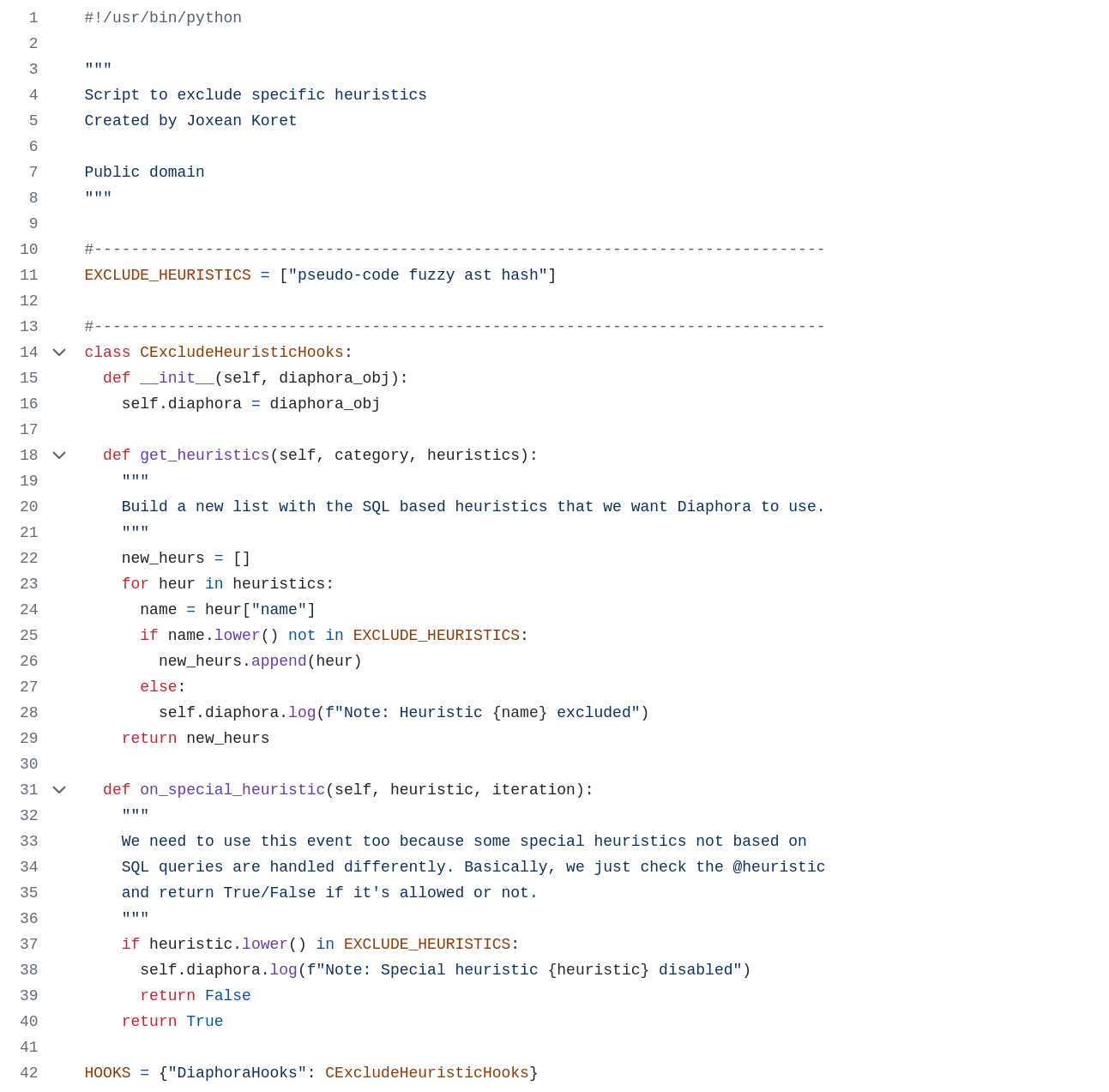
Joxean Koret (@matalaz)
joxean@mastodon.socialYesterday I wrote a script for #Diaphora for cases in which you want to disable a set of heuristics for the current two binaries being diffed for whatever reason. Here is the example script:
https://github.com/joxeankoret/diaphora/blob/master/doc/examples/hooks/exclude_heuristics.py
i'm excited to share Collateral Damage, a kernel exploit for SystemOS on Xbox One/Series consoles! this initial release is mostly intended for developers, but i hope people will enjoy playing around with it! writeup and more updates in the near future :) https://github.com/exploits-forsale/collateral-damage
BrianKrebs
briankrebs@infosec.exchangeAt least a dozen organizations with domain names at domain registrar Squarespace saw their websites hijacked last week. Squarespace bought all assets of Google Domains a year ago, but many customers still haven’t set up their new accounts. Experts say malicious hackers learned they could commandeer any migrated Squarespace accounts that hadn’t yet been registered, merely by supplying an email address tied to an existing domain.
From the story:
"...an analysis released by security experts at Metamask and Paradigm finds the most likely explanation for what happened is that Squarespace assumed all users migrating from Google Domains would select the social login options — such “Continue with Google” or “Continue with Apple” — as opposed to the “Continue with email” choice.
Taylor Monahan, lead product manager at Metamask, said Squarespace never accounted for the possibility that a threat actor might sign up for an account using an email associated with a recently-migrated domain before the legitimate email holder created the account themselves.
“Thus nothing actually stops them from trying to login with an email,” Monahan told KrebsOnSecurity. “And since there’s no password on the account, it just shoots them to the ‘create password for your new account’ flow. And since the account is half-initialized on the backend, they now have access to the domain in question.”
Wladimir Palant
WPalant@infosec.exchangeIt has been a while since I’ve written about Avast, so today I give you “How insecure is Avast Secure Browser?”
https://palant.info/2024/07/15/how-insecure-is-avast-secure-browser/
Note: This isn’t a vulnerability disclosure, merely an overview of problematic design decisions.
TL;DR from the article: I wouldn’t run Avast Secure Browser on any real operating system, only inside a virtual machine containing no data whatsoever.
Some highlights:
- Eleven pre-installed browser extensions but only two visible to users.
- Two extensions unnecessarily relax Content-Security-Policy protection.
- One of these two extensions also requesting all privileges possible, despite not actually using them.
- Two extensions accept messages from any other extension and any Avast website, the latter without enforcing HTTPS connections.
- One of these extensions, Privacy Guard (sic!), will expose information about your browser’s tabs via that messaging interface and provide updates as you browse the web.
- The “onboarding” experience is designed as an extremely flexible way to nag you into using products that benefit Avast financially.
- To make this “onboarding” work, the browser exposes internal APIs to a number of Avast domains that a huge number of third parties can put content on. Not only can each of these third parties abuse this access, a single XSS vulnerability will extend the access to any website on the internet (no effective CSP protection).
Enjoy!
Thinkst Canary
ThinkstCanary@mastodon.sdf.orgWe love Open Source contributors.
If you are a significant contributor to an Open Source project, DM us, and we will give you a full briefings pass to BlackHat USA (absolutely free).
__
* Tickets handed out totally at our discretion;
** We only have a few tickets left;
Mattias Wadman
wader@fosstodon.orgfq 0.12.0 released 🥳 nothing fancy, REPL and jpeg fixes otherwise mostly update of dependencies.
samczsun
samczsun@infosec.exchangeSpent the last four days coordinating incident response for the Squarespace domain hijackings with @tay and @AndrewMohawk. Now that it seems to be resolved, we wrote a little postmortem/retrospective
HyperDbg
hyperdbg@infosec.exchangeStarting from v0.10 (the next version), HyperDbg uses @keystone_engine as its assembler. ❤️
Thanks to our new team member @AbbasMasoumiG for adding it.
The following commands are added to assemble virtual and physical memory:
raptor 
raptor@infosec.exchange
Clever & fun technique to dump #Windows LSA secrets bypassing #EDR by @sensepost
Dumping LSA secrets: a story about task decorrelation
https://sensepost.com/blog/2024/dumping-lsa-secrets-a-story-about-task-decorrelation/
raptor 
raptor@infosec.exchange
Introduction to the Wild West of Proof of Concept #Exploit Code (#PoC) aka SSHing the Masses
https://santandersecurityresearch.github.io/blog/sshing_the_masses.html
_Veronica_
verovaleros@infosec.exchangeEveryone complains about meetings, but rarely anybody puts time before the meeting to do the work needed for the meeting to be useful.
linuzifer
linuzifer@23.socialCCC researchers had live access to 2nd factor SMS of more than 200 affected companies - served conveniently by IdentifyMobile who logged this sensitive data online without access control.
You had one job.