Posts
2706Following
681Followers
1504OpenSecurityTraining2
OpenSecurityTraining2@infosec.exchangeThe YouTube playlist for #OST2 “Exploitation 4011: Windows Kernel Exploitation: Race Condition + UAF in KTM” class by Cedric Halbronn @saidelike is now public for those who like to download videos: https://www.youtube.com/playlist?list=PLUFkSN0XLZ-nl4HEX4_LWG9H_d9vJKkYL
But the best way to learn the material is with the full class at https://ost2.fyi/Exp4011. This class assumes you've already taken "x86-64 OS Internals" https://ost2.fyi/Arch2001, "Windows Kernel Internals 2" https://ost2.fyi/Arch2821, and "Advanced WinDbg" https://ost2.fyi/Dbg3011
This is an advanced level class that teaches you how to exploit a race condition vulnerability leading to a use-after-free in the Kernel Transaction Manager (KTM) component of the Windows kernel. This class is meant to show the approach an exploit developer should take in attacking a previously unknown component in the Windows kernel.
Harry Sintonen
harrysintonen@infosec.exchangeRemote Unauthenticated Code Execution #Vulnerability in #OpenSSH server
Affected versions:
- OpenSSH versions earlier than 4.4p1
- Versions from 4.4p1 up to, but not including, 8.5p1 are not vulnerable
- Versions from 8.5p1 up to, but not including, 9.8p1
Details:
- https://www.qualys.com/2024/07/01/cve-2024-6387/regresshion.txt
- https://blog.qualys.com/vulnerabilities-threat-research/2024/07/01/regresshion-remote-unauthenticated-code-execution-vulnerability-in-openssh-server
lcamtuf 


lcamtuf@infosec.exchange
For loops have many uses.
[ Text link: https://godbolt.org/z/1cso144nM ]
Marcin Wichary
mwichary@mastodon.onlineThis week at Config I gave a talk about pixel fonts that I think turned out really well.
It’s called “In defense of an old pixel,” and I don’t think I ever worked harder on a talk before. Check it out here! (25 minutes)
kaoudis
kaoudis@infosec.exchangeReally appreciated @GabrielLandau’s #recon24 talk’s callout of challenges in responsible disclosure and how vendors not making a reasonable effort to work with researchers and their timelines makes those vendors less likely to receive all the security bug reports they otherwise could
This hard target full chain analysis from discovery to exploit has been added to Full Stack Web Attack. The last training for this year is at Romhack between 24th-27th of September at https://romhack.io/training/2024/full-stack-web-attack/ Student discount codes available, PM me but I only have a few left.
Charlie Balogh
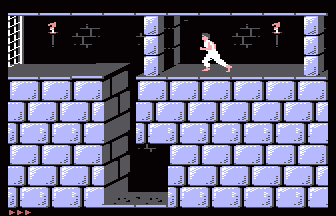
chainq@mastodon.socialHoly shit, the Hungarian Plus/4 gang strikes again at Árok Party 2024. TCFS ported Prince of Persia to the Plus/4! Runs on stock hardware (two disk sides). 😲
Wolf480pl
wolf480pl@mstdn.ioImagine software but move slow and fix things.
With decade long stability.
Bill the Lizard
lizardbill@hachyderm.io"There are two ways to do great mathematics. The first is to be smarter than everybody else. The second way is to be stupider than everybody else — but persistent." — Raoul Bott
Silent Signal
silentsignal@infosec.exchangeWe're stoked we got to present about low-level #IBMi internals today at @recon! Here you can find our detailed writeup:
https://silentsignal.github.io/BelowMI/
We also released our @kaitai definition for the *PGM serialization format:
https://github.com/silentsignal/PGM-Kaitai
...and our #Ghidra extensions:
https://github.com/silentsignal/PowerAS
Stay tuned for slides and demos!
Ange
Ange@mastodon.socialMission accomplished!
My keynote was ‘polarizing’:
Some were disappointed that it’s not a ‘standard’ keynote, while it resonated with others.
Well worth the risk: I didn’t want yet another self-gratifying write up or a threatintel PR deck.
https://speakerdeck.com/ange/a-question-of-time
Lukas Diekmann
lukasd@mastodon.onlineUB or not UB: How gcc and clang handle statically known undefined behaviour. https://diekmann.uk/blog/2024-06-25-statically-known-undefined-behaviour.html
/r/netsec
_r_netsec@infosec.exchangeBytecode Breakdown: Unraveling Factorio's Lua Security Flaws https://memorycorruption.net/posts/rce-lua-factorio/
Marco Ivaldi
raptor@infosec.exchangeThe #Windows #Registry Adventure #3: Learning resources
https://googleprojectzero.blogspot.com/2024/06/the-windows-registry-adventure-3.html
Retrograde
Retrograde@oldbytes.spaceBlue Monday on Vintage Casio Instruments. You're welcome.
❄️☃️Merry Jerry🎄🌲
jerry@infosec.exchangeToday is my last day at IBM.
I joined Netrex in February 1999 as a Unix admin
In late 1999 Internet Security Security Systems bought Netrex, largely for its managed services business.
In October 2006, when I was the director of IT, IBM bought ISS largely for its managed services business.
I was given lots of opportunities at IBM. Twice I found myself in the wrong place at the wrong time and was on a list to be let go, but other parts of IBM decided to pick me up. I once resigned to take a job at Deloitte, and at the time my manager told me that didn’t work for anyone and made it worth my while to stay. For many years, I led an incident response function for the strategic outsourcing business, which was later spun off to be what is now Kyndryl. I learned a LOT. I learned so much, in fact, that I decided to start a podcast in 2012, partly to make myself smarter, and partly in hopes that I could help the industry avoid the mistakes I was seeing our clients make on a near daily basis. I have deep scars from all the big security events of the 2010’s - heartbleed, shellshock, wannacry, notpetya, and many others.
In 2019, I was leading an internal practice around cyber regulations (in addition to the IR role) and ended up helping the cloud business out of a sticky situation. Unbeknownst to me, cloud had been looking to replace their CISO, and in March 2020, they offered me the job. My first big test was leading Cloud through Covid.
I had the extreme privilege to lead a team of 184 remarkably talented professionals. We did some cool things, but I regret the long list of things that didn’t get done.
As well published in the news, IBM took a hard line on return to office, particularly for executives. They gave people like me a choice: relocate to a key site (Atlanta was not one of them) and work from the office 3 days a week (with tight attendance tracking), or be let go. I have been working from home full time since shortly after IBM bought ISS in 2006 - nearly 18 years. I spend about 1/3 of my time at my beach place, which I was not willing to part with. Plus, I fundamentally disagree with the return to office approach and with how people have been treated, so I opted to “let it happen”, and so today is the day IBM terminates me.
I’ve saved up enough money that I can take a break for a while. It’s been 32 years since I’ve had more than a week off work, and at least 20 since I’ve had any sort of vacation that wasn’t disrupted by urgent meetings, crises, and so on. I’m going to spend some time with my family, especially my extremely patient wife, in ways that I haven’t been able to.
I have a very long list of things I’ll be doing during this downtime. I intend to get back into podcasting; I am going to write some including maybe a book; I am going to focus more on the fediverse instances I manage to ensure they are enduring; I am going to way too many baseball games with my wife (she is a mega baseball fan); and I am going to take way too many pictures and hopefully find some creative ways to make money with those pics.
TL;DR: today is the end of a long journey for me, and the start of a new one. And it’s a good day.
if you want to go to the bottom of #Assange 's case: Kevin Gosztola is the source to go to:
Cindʎ Xiao 🍉
cxiao@infosec.exchangeHello @recon attendees! My workshop, Reversing Rust Binaries: One Step Beyond Strings will be delayed by one hour, and will run from 4:30 pm to 6:30 pm today in Soprano B.