Posts
3485Following
717Followers
1584Retrograde
Retrograde@oldbytes.spaceBlue Monday on Vintage Casio Instruments. You're welcome.
Jerry 🦙💝🦙
jerry@infosec.exchangeToday is my last day at IBM.
I joined Netrex in February 1999 as a Unix admin
In late 1999 Internet Security Security Systems bought Netrex, largely for its managed services business.
In October 2006, when I was the director of IT, IBM bought ISS largely for its managed services business.
I was given lots of opportunities at IBM. Twice I found myself in the wrong place at the wrong time and was on a list to be let go, but other parts of IBM decided to pick me up. I once resigned to take a job at Deloitte, and at the time my manager told me that didn’t work for anyone and made it worth my while to stay. For many years, I led an incident response function for the strategic outsourcing business, which was later spun off to be what is now Kyndryl. I learned a LOT. I learned so much, in fact, that I decided to start a podcast in 2012, partly to make myself smarter, and partly in hopes that I could help the industry avoid the mistakes I was seeing our clients make on a near daily basis. I have deep scars from all the big security events of the 2010’s - heartbleed, shellshock, wannacry, notpetya, and many others.
In 2019, I was leading an internal practice around cyber regulations (in addition to the IR role) and ended up helping the cloud business out of a sticky situation. Unbeknownst to me, cloud had been looking to replace their CISO, and in March 2020, they offered me the job. My first big test was leading Cloud through Covid.
I had the extreme privilege to lead a team of 184 remarkably talented professionals. We did some cool things, but I regret the long list of things that didn’t get done.
As well published in the news, IBM took a hard line on return to office, particularly for executives. They gave people like me a choice: relocate to a key site (Atlanta was not one of them) and work from the office 3 days a week (with tight attendance tracking), or be let go. I have been working from home full time since shortly after IBM bought ISS in 2006 - nearly 18 years. I spend about 1/3 of my time at my beach place, which I was not willing to part with. Plus, I fundamentally disagree with the return to office approach and with how people have been treated, so I opted to “let it happen”, and so today is the day IBM terminates me.
I’ve saved up enough money that I can take a break for a while. It’s been 32 years since I’ve had more than a week off work, and at least 20 since I’ve had any sort of vacation that wasn’t disrupted by urgent meetings, crises, and so on. I’m going to spend some time with my family, especially my extremely patient wife, in ways that I haven’t been able to.
I have a very long list of things I’ll be doing during this downtime. I intend to get back into podcasting; I am going to write some including maybe a book; I am going to focus more on the fediverse instances I manage to ensure they are enduring; I am going to way too many baseball games with my wife (she is a mega baseball fan); and I am going to take way too many pictures and hopefully find some creative ways to make money with those pics.
TL;DR: today is the end of a long journey for me, and the start of a new one. And it’s a good day.
if you want to go to the bottom of #Assange 's case: Kevin Gosztola is the source to go to:
Cindʎ Xiao 🍉
cxiao@infosec.exchangeHello @recon attendees! My workshop, Reversing Rust Binaries: One Step Beyond Strings will be delayed by one hour, and will run from 4:30 pm to 6:30 pm today in Soprano B.
It's finally happened! NEWAG IP Management just sued us for copyright infringement and unfair competition. This is a civil lawsuit in Warsaw, parallel to a criminal investigation that's happening in Cracow.
Of course, they got our postal addresses wrong (they could've just asked!) so we only just got a copy from the court, but hey, we now have 164 pages of content to dive into.
Jeffrey
jtig@infosec.exchange"The NCC Group Global Threat Intelligence team has been made aware of significant compromise of
the TeamViewer remote access and support platform by an APT group. Due to the widespread usage
of this software the following alert is being circulated securely to our customers."
NCC Group can't disclose the source at the time and keep investigating this. Big source, but no substance. Curious to see how this will work out. ping @campuscodi @screaminggoat
Trammell Hudson
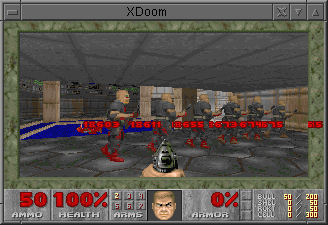
th@v.stdevops fun tip: use psdoom to manage your processes. https://www.cs.unm.edu/~dlchao/flake/doom/
scriptjunkie
sj@social.scriptjunkie.usnetstat when there's no netstat or ss
S=(- ESTABLISHED SYN_SENT SYN_RECV FIN_WAIT1 FIN_WAIT2 TIME_WAIT CLOSE CLOSE_WAIT LAST_ACK LISTEN CLOSING);hex2ipport(){ printf '%d.%d.%d.%d:%d\n' $(echo $1|awk -F: '{print $1}'|sed 's/../0x& /g'|awk '{print $4" "$3" "$2" "$1}') 0x$(echo $1|awk -F: '{print $2}');};cat /proc/net/tcp|tail -n +2|while read L;do echo $(hex2ipport $(echo $L|awk '{print $2}')) $(hex2ipport $(echo $L|awk '{print $3}')) ${S[$(( 0x$(echo $L|awk '{print $4}') ))]};done
Jon Greig
jgreig@ioc.exchangeProgress declined to answer any questions about the third-party issue that forced them to increase the CVSS score of CVE-2024-5806 to 9.1
https://therecord.media/progress-software-elevates-severity-bug
screaminggoat
screaminggoat@infosec.exchangeTenable: Fortra FileCatalyst Workflow Unauthenticated SQLi
Tenable decided to drop a same-day proof of concept for Fortra FileCatalyst Workflow SQL injection vulnerability CVE-2024-5276 (9.8 critical, disclosed 25 June 2024, see Fortra security advisory).
See Bleeping Computer reporting: Exploit for critical Fortra FileCatalyst Workflow SQLi flaw released
#CVE_2024_5276 #Fortra #vulnerability #CVE #ProofofConcept #POC
Cisco Talos
TalosSecurity@mstdn.socialVulnerability Deep Dive: Multiple vulnerabilities in TP-Link Omada system could lead to root access https://blog.talosintelligence.com/multiple-vulnerabilities-in-tp-link-omada-system/
Silent Signal
silentsignal@infosec.exchangeIt was an honor to present our #IBMi exploits at #TROOPERS24 today! You'll have to wait until @WEareTROOPERS releases the recordings for the full show (incl. live demos), until then you can find our slides here:
https://silentsignal.hu/docs/S2-TROOPERS24-IBM_i_for_Wintel_Hackers.pdf
Mr. Bitterness
wdormann@infosec.exchangeA few notes on this GrimResource .MSC thing from Elastic.
For starters, there are not one but THREE security warnings from Windows before opening a .MSC file from the internet.
Just kidding. Nobody still has Smart App Control enabled after using Windows for a day and realizing what doesn't work. 😂 So two security warnings that clearly state that you're about to do something bad. Or maybe just one if you've received the file in a ZIP or ISO or the like. But in the end, this is convincing the user to do something dangerous, and there are PLENTY of ways to accomplish this on a fully-patched system.
But perhaps more interestingly, the issue being leveraged was discovered by GPZ over 6 years ago by GPZ. Microsoft fixed it in Edge as one of CVE-2018-8463 CVE-2018-8468 and CVE-2018-8469. (Nobody can tell exactly what is what from MSRC publications). But Microsoft apparently neglected to recognize that it affects things other than Edge (e.g. MMC.EXE)
https://bugs.chromium.org/p/project-zero/issues/detail?id=1598
Dan Lockton
danlockton@mastodon.socialThe fact that Microsoft Teams 🤮 contains a feature called "Teams" where actual teams can create a Team, and at Microsoft the teams working on that feature probably have a Team to discuss the Teams feature, suggests that there exists a Microsoft Microsoft Teams Teams Teams' Microsoft Teams Team.
Ange
Ange@mastodon.socialI gave an "unusual” keynote at Troopers today:
https://speakerdeck.com/ange/a-question-of-time
Cindʎ Xiao 🍉
cxiao@infosec.exchange🦀 Hello Rust reversers! If you're at @recon in Montreal this year, come check out my workshop, Reversing Rust Binaries: One Step Beyond Strings! It will be Friday June 28th, at 2:30 pm, in Soprano B.
https://cfp.recon.cx/recon2024/talk/QCA37X/
For pre-workshop setup instructions, including a prebuilt VM, prebuilt binaries, and sample code, see https://github.com/cxiao/rust-reversing-workshop-recon-2024
Hope to see many of you there!
#REcon2024 #reconmtl #rustlang #reverseengineering #reversing #malwareanalysis
Kevin Beaumont
GossiTheDog@cyberplace.socialGood find by Elastic - possibly North Korean based threat actors using an unfixed bug in Windows to execute code, undetected across all vendors until that point (and as of writing only Elastic detect still)
They’ve named it GrimResource https://www.elastic.co/security-labs/grimresource
/r/netsec
_r_netsec@infosec.exchangeWhy nested deserialization is harmful: Magento XXE (CVE-2024-34102) https://www.assetnote.io/resources/research/why-nested-deserialization-is-harmful-magento-xxe-cve-2024-34102