Posts
3124Following
708Followers
1551Lobsters
lobsters@botsin.spaceHaifei Li
haifeili@bird.makeupI’ve said before and saying again. This is a common problem in vendors - the lack of understandings of the importance/value of new attack vector discovery research.
daniel:// stenberg://
bagder@mastodon.socialit has been nearly three months since the last valid #hackerone report against #curl
Just saying.
I bet you can't find anything to report.
🤠
Sass, David
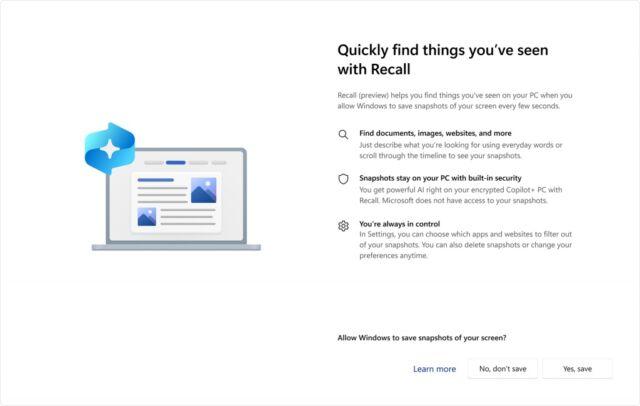
sassdawe@infosec.exchangeDid anyone realize that #MicrosoftEdge already had a #recall feature? 👀
Viss
Viss@mastodon.socialgood morning!
my talk from securityfest has been published!
if you have ~35 minutes and want to learn some stuff about adversarial defenses, have a peek!
https://www.youtube.com/watch?v=ShSR0c81h5U&ab_channel=SecurityFest
Google asks every app to have a Privacy Policy to be accepted in the Play Store. So, xScreenSaver had to write a privacy policy.
Here you go:
Zack Whittaker
zackwhittaker@mastodon.socialNEW, by me: Mandiant says cybercriminals stole a "significant volume of data" from Snowflake customers.
Mandiant and Snowflake say they've notified 165 affected customers so far that their cloud-stored data may have been stolen.
Mandiant said the threat campaign was "ongoing," suggesting more victims to come.
BleepingComputer
BleepingComputer@infosec.exchangeA proof-of-concept (PoC) exploit for a Veeam Backup Enterprise Manager authentication bypass flaw tracked as CVE-2024-29849 is now publicly available, making it urgent that admins apply the latest security updates.
/r/netsec
_r_netsec@infosec.exchangeUncovering a Critical Vulnerability in Authentik's PKCE Implementation (CVE-2023-48228) | Offensity https://www.offensity.com/en/blog/uncovering-a-critical-vulnerability-in-authentiks-pkce-implementation-cve-2023-48228/
Pentagrid AG
pentagrid@infosec.exchangeIf you want to protect your IT #infrastructure against #MITM attacks where an attacker bypasses domain verification to obtain valid certificates, you may want to use #CAA and #accountURI binding, which is easy to set up. https://www.pentagrid.ch/en/blog/domain-verification-bypass-prevention-caa-accounturi/ #hardening
Longhorn
never_released@mastodon.socialOn a random note, mink (rewrite in Rust) is open-source
note: it’s what’s used for cross trust domain boundaries communication on the AP, but (AP <->) Hexagon uses a completely separate IDL (compiled w/ QAIC)
Lukasz Olejnik
LukaszOlejnik@mastodon.social87-year-old writes to Financial Times. This is a real technological problem also for people with disabilities. Including me. Banking systems (and others) may make people's life miserable. And you know what? In case of an issue, I couldn't even make a phone call (when mandatory).
Brandon Falk
gamozolabs@bird.makeupLive now! Doing some Linux virtual memory manager experiments by using processes instead of threads! Maybe a custom allocator too! https://stream.bfa.lk/ . Also live on Twitch and YouTube :3
"Your personal information is very important to us."
Crowdsourcing snark! Dear Lazyweb,
Bbefore they will let me publish a new release of XScreenSaver on the "Play" [sic] store, Google, the most rapacious privacy violator on the planet, is insisting...
https://jwz.org/b/ykUc
Ars Technica
arstechnica@mastodon.socialMicrosoft makes Recall feature off-by-default after security and privacy backlash
Windows Hello authentication, additional encryption being added to protect data.
yossarian (1.3.6.1.4.1.55738)
yossarian@infosec.exchangeperiodic reminder: you cannot "pass" a security audit. anybody selling you a passable security audit is selling you a lie, and anybody selling you a product that has "passed' an audit is lying to you.
a security audit can uncover bugs, or not uncover bugs, and can (in the words of the recipient) demonstrate positive or negative qualities about the codebase. but it cannot be "passed" or otherwise *endorse* the product or program itself.
kaoudis
kaoudis@infosec.exchangeI would equate writing your own parsers for fiddly formats that lack formal single specification and may even require implementers to know the right undocumented or verbally passed down lore with doing your own gas plumbing.
If you’re a pretty competent plumber and can turn the gas on and off you could try it right? Somebody has to do it and they usually get it right. And you’ve fixed a leaky sink tailpipe once or twice in your day.
But should *you* as a non gas plumber? My vote is no, your house could explode or you could die of noxious gas inhalation if you get it wrong.
I would equate using FFI to shoehorn such parsers from, say C++ into your nice “safe” main codebase language to then using an inappropriate connector type to attach a new gas range to your DIY job.
Should you do it? My vote is no, please let someone who is trained to do it. *Could* you do it? Nobody laid down a personal challenge, mate.