Posts
2916Following
693Followers
1518Ars Technica
arstechnica@mastodon.socialMicrosoft makes Recall feature off-by-default after security and privacy backlash
Windows Hello authentication, additional encryption being added to protect data.
yossarian @ hushcon
yossarian@infosec.exchangeperiodic reminder: you cannot "pass" a security audit. anybody selling you a passable security audit is selling you a lie, and anybody selling you a product that has "passed' an audit is lying to you.
a security audit can uncover bugs, or not uncover bugs, and can (in the words of the recipient) demonstrate positive or negative qualities about the codebase. but it cannot be "passed" or otherwise *endorse* the product or program itself.
kaoudis
kaoudis@infosec.exchangeI would equate writing your own parsers for fiddly formats that lack formal single specification and may even require implementers to know the right undocumented or verbally passed down lore with doing your own gas plumbing.
If you’re a pretty competent plumber and can turn the gas on and off you could try it right? Somebody has to do it and they usually get it right. And you’ve fixed a leaky sink tailpipe once or twice in your day.
But should *you* as a non gas plumber? My vote is no, your house could explode or you could die of noxious gas inhalation if you get it wrong.
I would equate using FFI to shoehorn such parsers from, say C++ into your nice “safe” main codebase language to then using an inappropriate connector type to attach a new gas range to your DIY job.
Should you do it? My vote is no, please let someone who is trained to do it. *Could* you do it? Nobody laid down a personal challenge, mate.
David Chisnall (*Now with 50% more sarcasm!*)
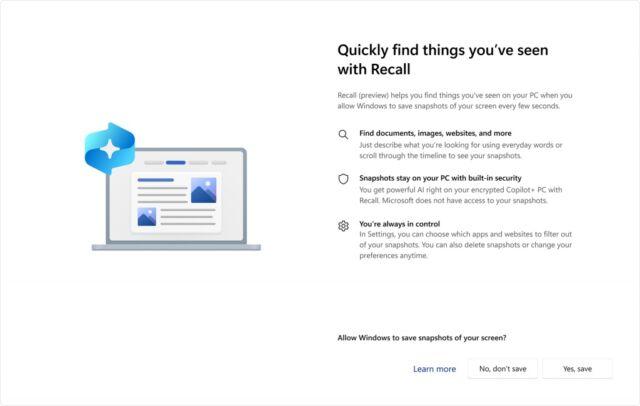
david_chisnall@infosec.exchangeThe worst thing about #recall is not that it's a security and privacy disaster, it’s that the root cause of the security problems is also the reason it will be completely useless.
Imagine that you are scrolling through some news aggregator or social media page and you spot something that’s interesting. You forget and then a few days later ask recall to find it for you. Recall has access only to screenshots and so will tell you ‘yes, that thing you found interesting, it was at http://mastodon.social’ and you will say ‘you are a total waste of battery life and I hate you’. It does not have access to the structure of the page, so it cannot extract the link to the specific post, it just does optical character recognition on the address bar. Most of the sites where it’s hard to find things do infinite scrolling, so knowing that ‘this thing was somewhere in this infinite-scrolling page’ is unhelpful.
If it had been designed as a solid piece of engineering, rather than a ‘please find a use case for this AI thing’ project, it would work more like Spotlight on macOS, exposing hooks for apps to provide structured data. Edge would extract the permalink fields and index them along with post content. If it had been designed like this, apps would be able to choose what to provide and so Edge could automatically skip any content of sites that you log into unless you opt in, and also opt out anything in a private browsing window. Office apps would be able to exclude files marked as sensitive (e.g. anything with PII or medical or financial data). The privacy implications would be much less bad, the performance would be better, and it would actually be useful.
This is fairly representative of a lot of the AI hype. By using machine learning, you can build something that could be done a lot better without AI. That’s not to say that there’s no use for ML models in such a system. Providing a feature extraction model for indexing would be useful, so I can search for ‘that paper I read that had a picture of an orange cat on the first page’ and it would be able to record ‘orange cat’ in the metadata for that picture when it indexed the PDF. It’s not the right foundation, because an existing off-the-shelf PDF parser can extract the table of contents and text with 100% accuracy, whereas ML-driven OCR on screenshots will fail if I’ve scrolled some of it off the window.
Prof. Sam Lawler
sundogplanets@mastodon.socialThe only feeling I have about starship is dread.
They want to use that to launch batches of HUNDREDS of Starlinks at once. And guess where all those Starlinks will end up? The pieces that don't make it to the ground will end up in our upper atmosphere, screwing up the stratosphere, the ozone layer, who knows what else because SpaceX isn't required to do any environmental assessments of this.
Shit. Maybe a good time to post this essay I wrote yet again: https://theconversation.com/an-astronomers-lament-satellite-megaconstellations-are-ruining-space-exploration-215653
abadidea
0xabad1dea@infosec.exchangeif you have a github integration that just started crashing, it's because the comment IDs have surpassed signed 32-bit range.
📣 Announcing the availability of:
- PHP 8.3.8
- PHP 8.2.20
- PHP 8.1.29
‼️ These SECURITY releases fix:
- Argument Injection in PHP-CGI
- Bypass in filter_var FILTER_VALIDATE_URL
- proc_open workaround Windows with escaping arguments for bat/cmd files
- openssl_private_decrypt vulnerability to the Marvin attack
Please upgrade ASAP.
Changelog: https://www.php.net/ChangeLog-8.php
Source: https://www.php.net/downloads
Windows: https://windows.php.net/download/
Nowhere Girl
gwynnion@mastodon.socialCompanies that bought a metric shit load of Nvidia processors want you to know how very badly you need a virtual assistant who spies on you and makes stuff up in order to justify it.
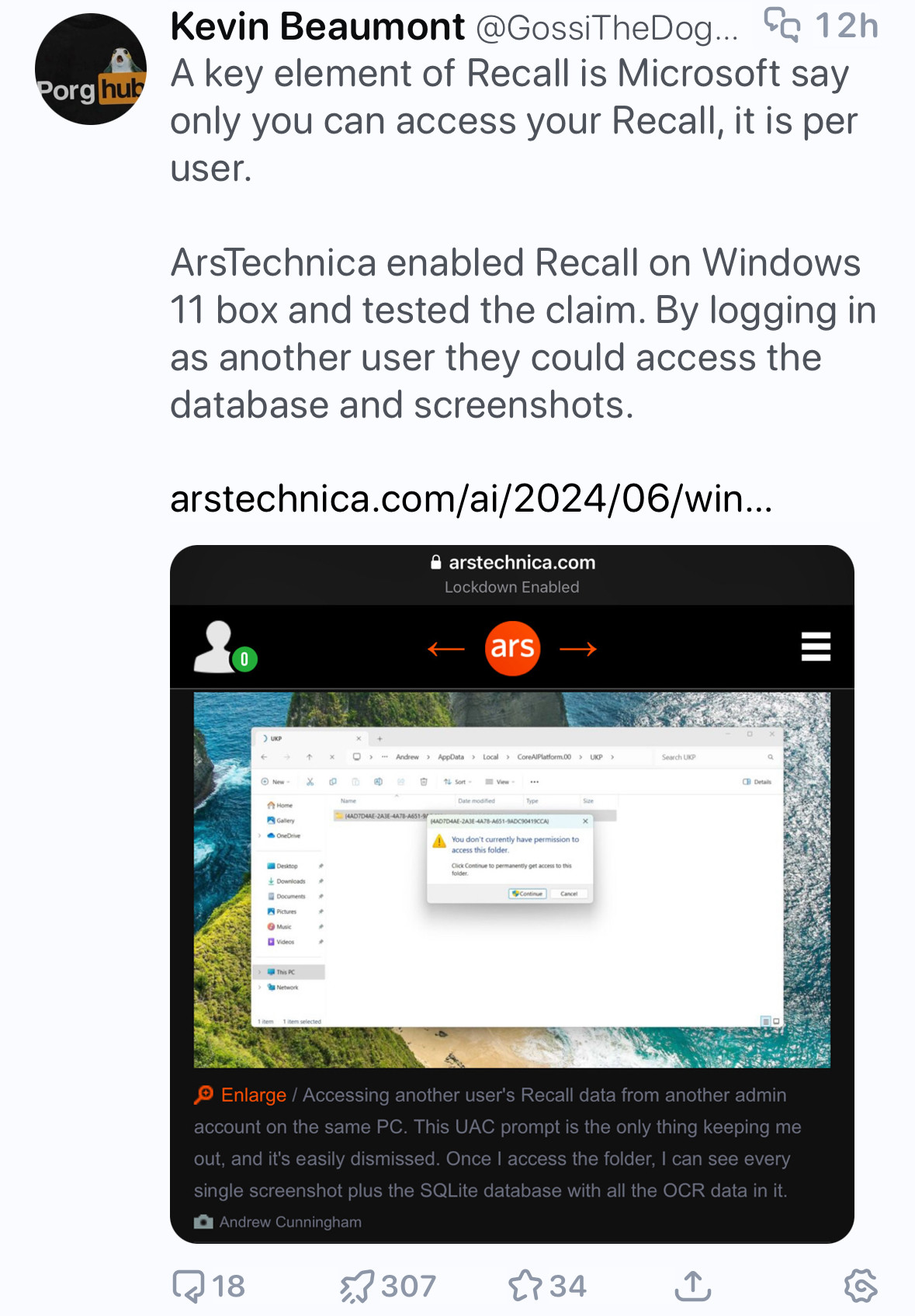
look i am not going to be a recall defender, nor am i a fan of the “uac is not a security boundary” bit, but this commentary seems… disingenuous. yes, your data is restricted to your user. yes, admins have full control over the machine meaning they can access your data. this shouldn’t be surprising. windows admin security boundaries are basically non-existent, i wish that wasn’t the case but that’s how it’s always been and will be for the foreseeable future
Virus Bulletin
VirusBulletin@infosec.exchangeAhnLab researchers warn about phishing HTML files attached to emails that prompt users to directly paste (CTRL+V) and run commands. https://asec.ahnlab.com/en/66300/
Alex Plaskett
alexjplaskett@bird.makeupOoh cool @travisgoodspeed has written a book on Microcontroller Exploits. Will certainly be adding this to my collection!
endrift 🏳️⚧️
endrift@social.treehouse.systemsAnyone have security contacts at Google? One of their IP addresses is spamming my ssh server, apparently as part of a botnet. Seems someone got compromised.
34.71.138.230 is the guilty party.
Michael Schneider
misc@infosec.exchangeI added disabling Recall to my HardeningKitty list:
https://github.com/0x6d69636b/windows_hardening
Disable Recall - User
[HKEY_CURRENT_USER\Software\Policies\Microsoft\Windows\WindowsAI]
"DisableAIDataAnalysis"=dword:00000001
Disable Recall - Machine (not yet official)
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\WindowsAI]
"DisableAIDataAnalysis"=dword:00000001
Asahi Linux
AsahiLinux@social.treehouse.systemsIntroducing Honeykrisp: the world's first conformant Vulkan® 1.3 driver for Apple Silicon.
Alec Muffett
alecmuffett@mastodon.socialHappy Birthday Whitfield Diffie, 80 years today!
https://alecmuffett.com/article/109902
#WhitfieldDiffie #encryption
Pentagrid AG
pentagrid@infosec.exchangeIt happened again. We accidentally broke another #hotel check-in #terminal. This time Mr O'Yolo triggered a problem, crashed the #Ariane Allegro Scenario Player and escaped the #kiosk mode, which enabled access to the Windows Desktop: https://www.pentagrid.ch/en/blog/ariane-allegro-hotel-check-in-terminal-kios-escape/ #itsecurity #infosec
Mari0n
pinkflawd@mastodon.social@recon is hosting BlackHoodie again this year, with a training on Reverse Engineering Ransomware brought to you by the incomparable Suweera DeSouza and Alex Delamotte. Registration is still open https://blackhoodie.re/Recon2024/ please share!
golang
golang@hachyderm.io🎉 Go 1.22.4 and 1.21.11 are released!
🔒 Security: Includes security fixes for archive/zip and net/netip
🔈 Announcement: https://groups.google.com/g/golang-announce/c/XbxouI9gY7k
⬇️ Download: https://go.dev/dl/#go1.22.4
Stilgherrian
stilgherrian@eigenmagic.net“MediSecure declares insolvency following massive data breach” https://www.cyberdaily.au/security/10665-breaking-medisecure-declares-insolvency-following-massive-data-breach