Posts
3368Following
712Followers
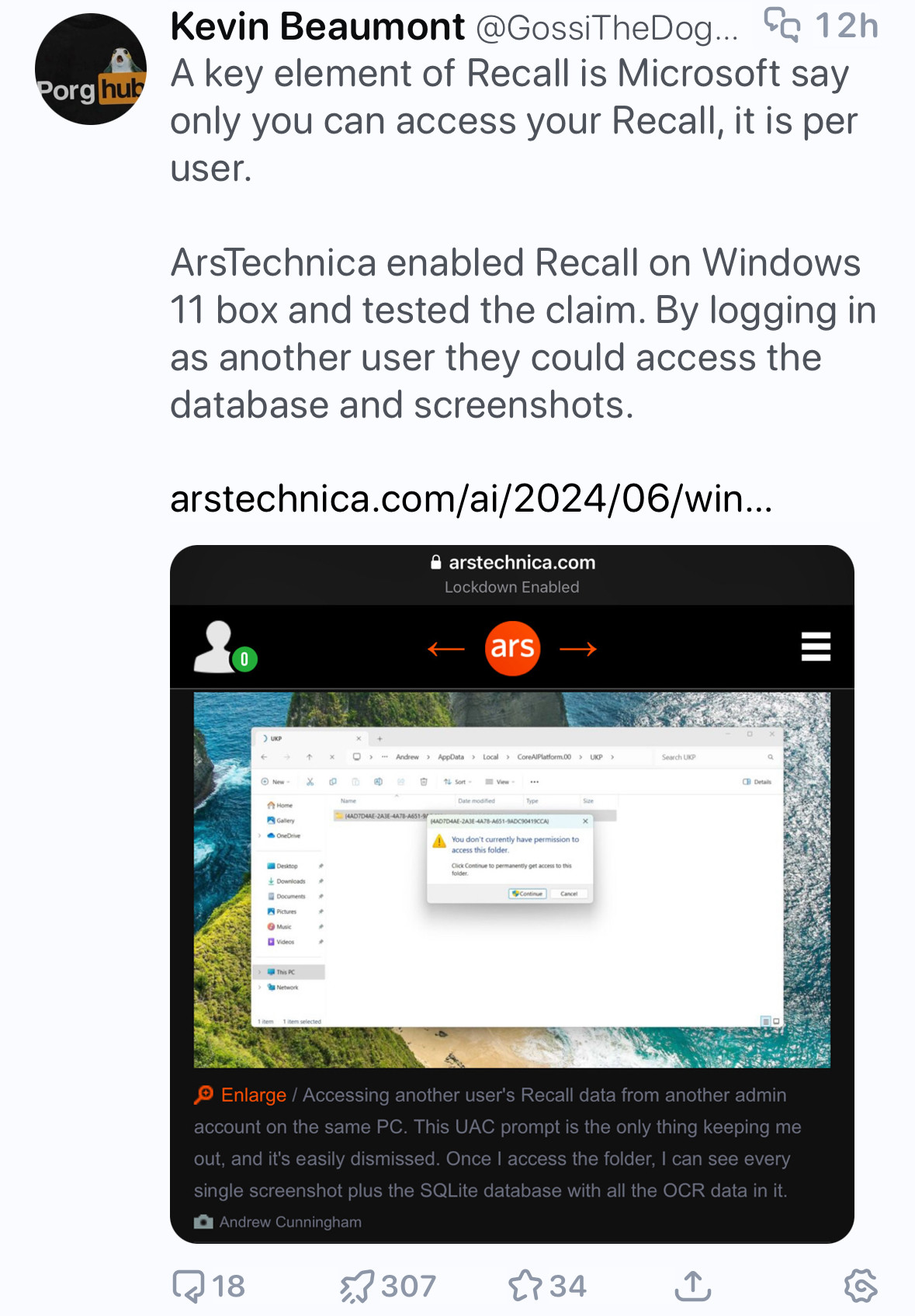
1580look i am not going to be a recall defender, nor am i a fan of the “uac is not a security boundary” bit, but this commentary seems… disingenuous. yes, your data is restricted to your user. yes, admins have full control over the machine meaning they can access your data. this shouldn’t be surprising. windows admin security boundaries are basically non-existent, i wish that wasn’t the case but that’s how it’s always been and will be for the foreseeable future
Virus Bulletin
VirusBulletin@infosec.exchangeAhnLab researchers warn about phishing HTML files attached to emails that prompt users to directly paste (CTRL+V) and run commands. https://asec.ahnlab.com/en/66300/
Alex Plaskett
alexjplaskett@bird.makeupOoh cool @travisgoodspeed has written a book on Microcontroller Exploits. Will certainly be adding this to my collection!
endrift 🏳️⚧️
endrift@social.treehouse.systemsAnyone have security contacts at Google? One of their IP addresses is spamming my ssh server, apparently as part of a botnet. Seems someone got compromised.
34.71.138.230 is the guilty party.
Michael Schneider
misc@infosec.exchangeI added disabling Recall to my HardeningKitty list:
https://github.com/0x6d69636b/windows_hardening
Disable Recall - User
[HKEY_CURRENT_USER\Software\Policies\Microsoft\Windows\WindowsAI]
"DisableAIDataAnalysis"=dword:00000001
Disable Recall - Machine (not yet official)
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\WindowsAI]
"DisableAIDataAnalysis"=dword:00000001
Asahi Linux
AsahiLinux@social.treehouse.systemsIntroducing Honeykrisp: the world's first conformant Vulkan® 1.3 driver for Apple Silicon.
Alec Muffett
alecmuffett@mastodon.socialHappy Birthday Whitfield Diffie, 80 years today!
https://alecmuffett.com/article/109902
#WhitfieldDiffie #encryption
Pentagrid AG
pentagrid@infosec.exchangeIt happened again. We accidentally broke another #hotel check-in #terminal. This time Mr O'Yolo triggered a problem, crashed the #Ariane Allegro Scenario Player and escaped the #kiosk mode, which enabled access to the Windows Desktop: https://www.pentagrid.ch/en/blog/ariane-allegro-hotel-check-in-terminal-kios-escape/ #itsecurity #infosec
Mari0n
pinkflawd@mastodon.social@recon is hosting BlackHoodie again this year, with a training on Reverse Engineering Ransomware brought to you by the incomparable Suweera DeSouza and Alex Delamotte. Registration is still open https://blackhoodie.re/Recon2024/ please share!
golang
golang@hachyderm.io🎉 Go 1.22.4 and 1.21.11 are released!
🔒 Security: Includes security fixes for archive/zip and net/netip
🔈 Announcement: https://groups.google.com/g/golang-announce/c/XbxouI9gY7k
⬇️ Download: https://go.dev/dl/#go1.22.4
Stilgherrian
stilgherrian@eigenmagic.net“MediSecure declares insolvency following massive data breach” https://www.cyberdaily.au/security/10665-breaking-medisecure-declares-insolvency-following-massive-data-breach
rev.ng
revng@infosec.exchangeEver wanted to feed the decompiled C code into source code analysis tools?
With rev.ng you can! 💪
We emits syntactically valid C code!
Here's a PoC did with Clang Static Analyzer. 😎
/r/netsec
_r_netsec@infosec.exchangeCVE-2023-48788: Revisiting Fortinet FortiClient EMS to Exploit 7.2.X https://www.horizon3.ai/attack-research/cve-2023-48788-revisiting-fortinet-forticlient-ems-to-exploit-7-2-x/
/r/netsec
_r_netsec@infosec.exchangeAttacking Android Binder: Analysis and Exploitation of CVE-2023-20938 https://androidoffsec.withgoogle.com/posts/attacking-android-binder-analysis-and-exploitation-of-cve-2023-20938/
Almond OffSec
AlmondOffSec@infosec.exchangeHow does F5's Secure Vault, its "super-secure SSL-encrypted storage system" work? Response in this article by team member @myst404
https://offsec.almond.consulting/deep-diving-f5-secure-vault.html
SSD Secure Disclosure
SSDSecureDisclosure@infosec.exchange🚨 New advisory was just published! 🚨
A vulnerability in the Linux kernel allows local attackers to escalate privileges on affected installations of Linux Kernel:
https://ssd-disclosure.com/ssd-advisory-linux-kernel-nft_validate_register_store-integer-overflow-privilege-escalation/
/r/netsec
_r_netsec@infosec.exchangeBoost Security Audit - Shielder https://www.shielder.com/blog/2024/05/boost-security-audit/