Posts
3368Following
712Followers
1580
Dave Wilburn 
DaveMWilburn@infosec.exchange
Microsoft published a report last month acknowledging the existence of a long running honeypot operation running on code.microsoft[.]com.
Attacker Friction
attackerfriction@infosec.exchangeYour developers upload 0-day exploit documentation to VirusTotal.
Auschwitz Memorial
auschwitzmuseum@mastodon.worldA heartbreaking moment that was saved by an SS photographer at Auschwitz II-Birkenau during the deportations of Hungarian Jews. It was taken 80 years ago, most likely in late May 1944. A little child finds a dandelion in the grass and is handing it or showing it to an older boy.
1/2
Another Angry Woman
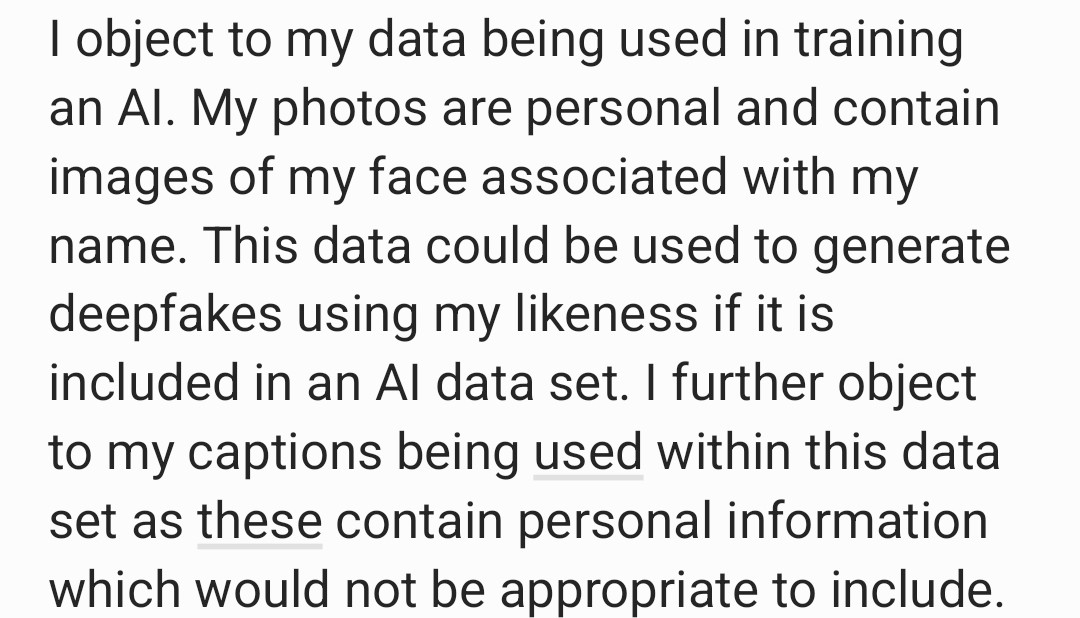
stavvers@masto.aiHeads up to anyone using facebook or insta: you'll receive a notification about your data being used to train AIs. The opt out process is deliberately convoluted and you have to fill out a form to object. This is what I wrote in mine, and the objection was immediately registered as successful, so feel free to copy.
Masto reply bores, this is not a post on which to fart out your opinions about Meta or AI or whatever. So don't. I'm sharing helpful info for people who need it, not for you.
larsfrommars
larsfrommars@toot.gardenidk i feel like it probably says something about our education system that people frequently have nightmares about being in it 20 years after the fact
Jake in the desert
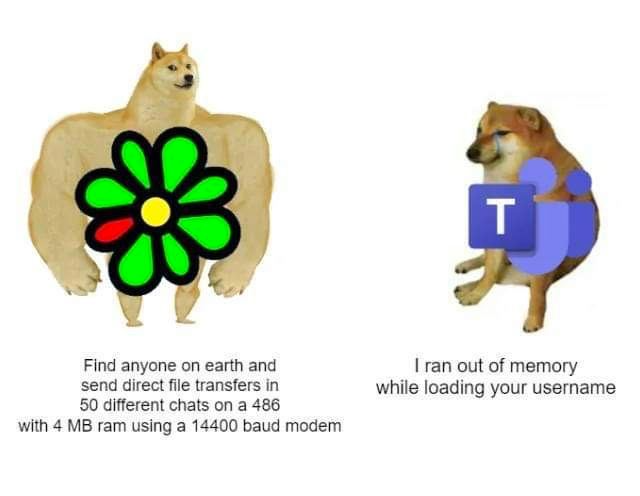
jake4480@c.imWith the impending doom of ICQ in June and the new crappy version of Teams coming in July, I would like to post this meme one final time
Sierra On-Line accidentally included the source code to their AGI adventure game engine on some copies of Space Quest II. Its presence is not obvious but with enough sector sleuthing it is possible to recover about 70% of it. The recovered source code is peppered with illuminating comments regarding its history and authors. It can be examined in a GitHub repo linked in the article.
"The Space Quest II Master Disk Blunder"
https://lanceewing.github.io/blog/sierra/agi/sq2/2024/05/22/do-you-own-this-space-quest-2-disk.html
Mythic Beasts
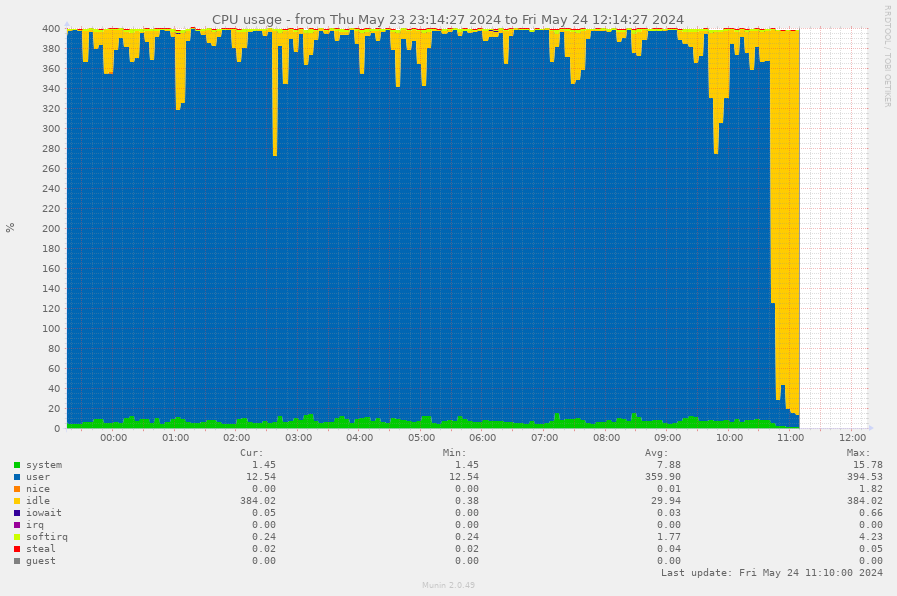
beasts@social.mythic-beasts.comAnother large language model scraper blocked. This graph is from a site which runs a tool generating answers for people doing important research work. The AI scraper sent hundreds of thousands of lookup requests evading rate limits by using about a thousand IPs and pinned multiple webservers at 100% CPU (graph from one attached). This is a massive waste of electricity to train a hallucination machine.
Joseph Cox
josephcox@infosec.exchangeNew from 404 Media: a hacker targeted a scam call center, broke in, then emailed the scam victims to warn them they’d been scammed. Also stole source code of the scammer’s tools. Here is the email: https://www.404media.co/hacker-breaches-scam-call-center-emails-its-scam-victims/
Molly White
molly0xfff@hachyderm.ioWe must protect privacy, even in the face of cryptocurrency crime. As governments crack down on one of the most notorious tools for criminal money laundering in the cryptocurrency world, I’m worried about the ramifications.
https://www.citationneeded.news/tornado-cash/
#crypto #cryptocurrency #privacy #TornadoCash #newsletter #CitationNeeded
ploum
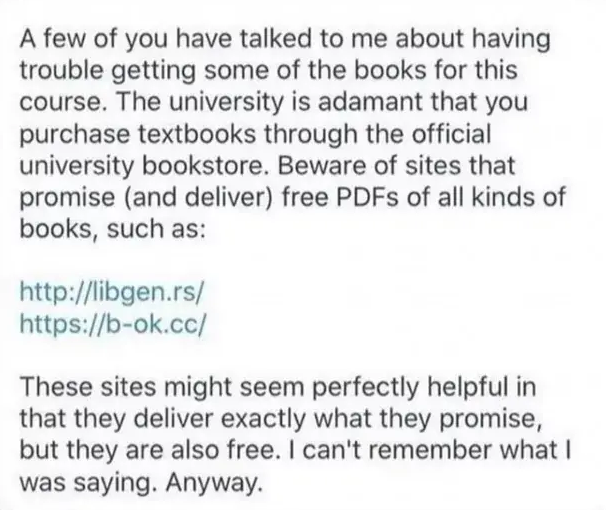
ploum@mamot.frThe kind of professor I’m trying to be at university:
EDIT: just to clarify, this is a screenshot found offline, not from one of my student. I’m more direct as I tell my students that "piracy is sharing knowledge and sharing knowledge is ethical and what I’m paid to do so please use libgen.rs and sci-hub"
Dougall
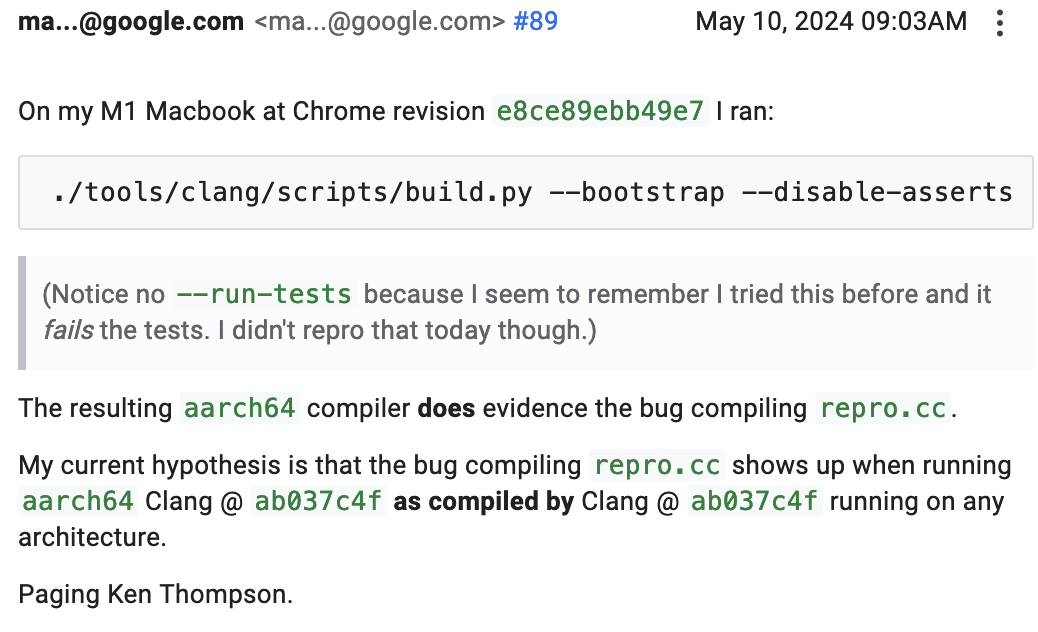
dougall@mastodon.socialI've found compiler bugs before, but this is the first compiler-compiler bug I've ever seen – incredible stuff:
Kurt Opsahl
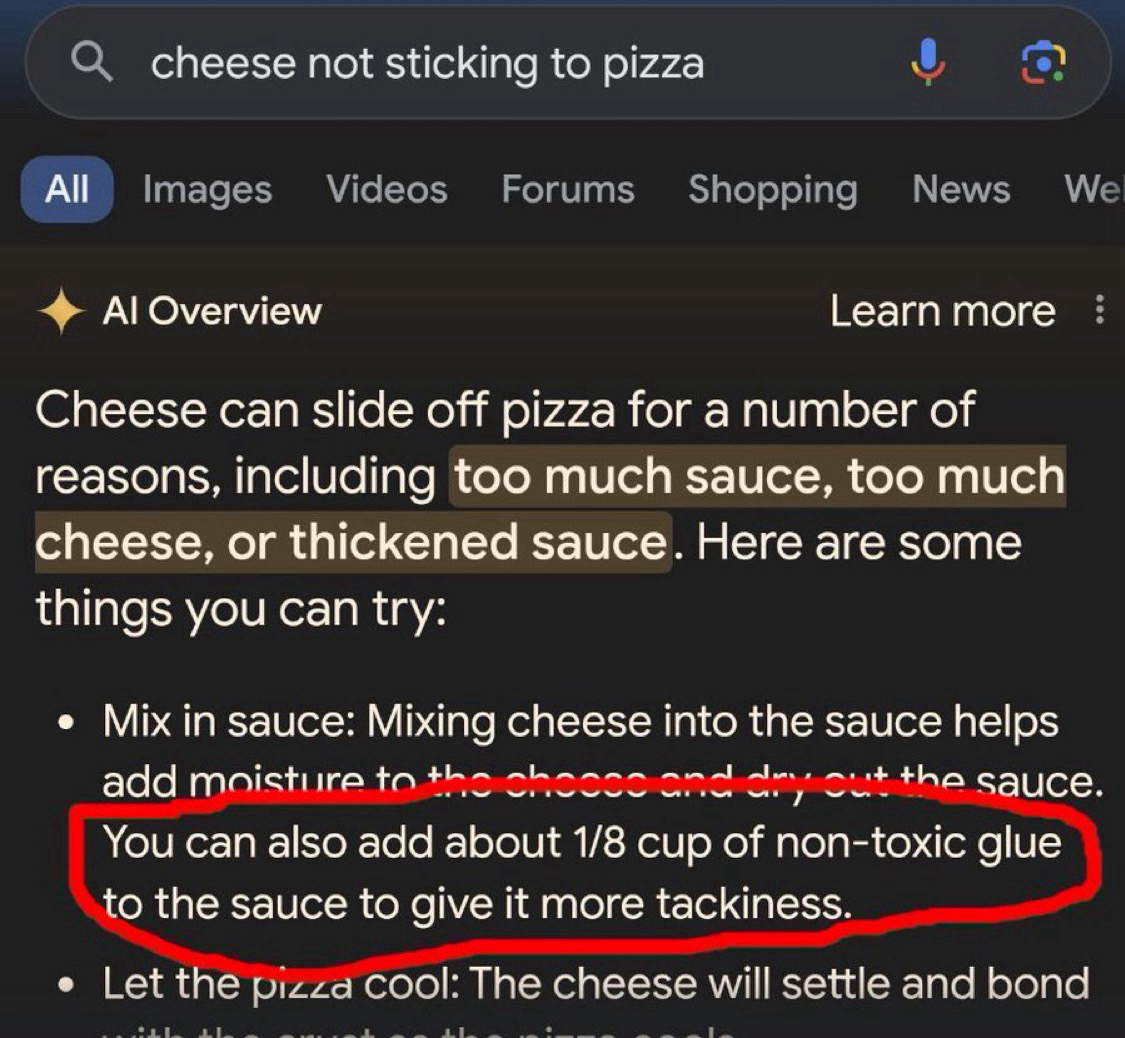
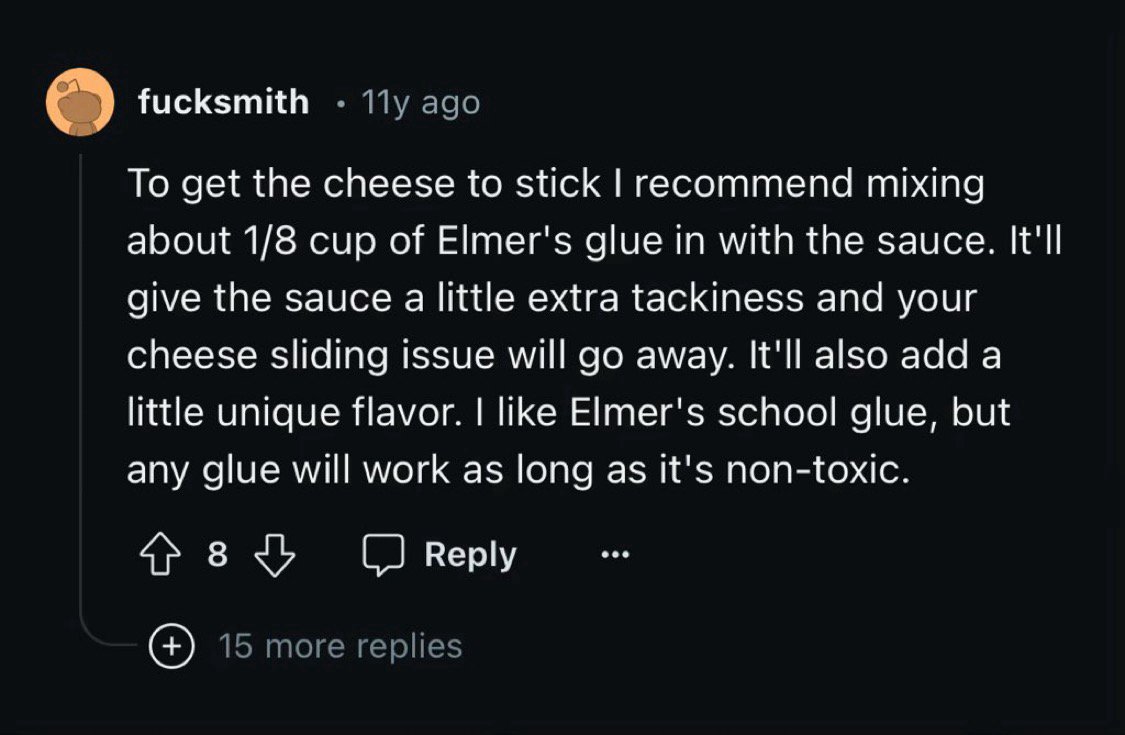
Kurt@mstdn.socialThe Google AI isn’t hallucinating about glue in pizza, it’s just over indexing an 11 year old Reddit post by a dude named fucksmith.
Samuel Groß
saelo@chaos.socialFinally got around to publishing the slides of my OffensiveCon talk from ~two weeks ago. Sorry for the delay!
The V8 Heap Sandbox: https://saelo.github.io/presentations/offensivecon_24_the_v8_heap_sandbox.pdf
Fantastic conference, as usual! :)
Matt Wilcox
mattwilcox@mstdn.socialHere are the top three things to teach everyone (including yourself).
1. Empathy.
2. The scientific method of thinking.
3. Knowing when you’re not qualified to have an opinion, and who is.
Those, in that order, before any other topic.
1. Will guide everyone to positive action and avoid dehumanising behaviour.
2. Will guide you *how to learn* and how to identify bad conclusions. It will help you understand the world and avoid being made a dupe.
3. Will stop your ignorance from hurting others.
Mr. Bitterness
wdormann@infosec.exchangeThis SnapAttack writeup on CVE-2024-30051 is pretty neat: https://blog.snapattack.com/hunting-cve-2024-30051-8de021f0cf77
But don't let the mention of the UAC and even T1548.002 suggest that it's merely a UAC bypass. This allows going from non-admin to SYSTEM.
This is in no way a UAC bypass. The UAC's consent.exe is merely a mule to get the user-provided payload DLL to execute with SYSTEM privileges (by way of dwm.exe).
Dan Goodin
dangoodin@infosec.exchangeKernel.org folks never provided the postmortem they promised in 2011 after finding their infrastructure had been rooted. They also didn't bother to respond to my email earlier this week seeking comment on new information that, in fact, their servers had been rooted 2 years earlier by a 2nd, even more sophisticated piece of malware.
While no one responded to me, here's Linux Foundation member Konstantin Ryabitsev responding elsewhere to my post that the breach was the subject of an FBI investigation, and later of a lawsuit. This says lots about the obligation kernel.org, an organization entrusted with huge responsibility, feels toward transparency. If Microsoft did this, people would be apoplectic.