Posts
2355Following
513Followers
1232Heretek of Silent Signal
buherator
buheratorhttps://nbviewer.org/github/microsoft/MSRC-Security-Research/blob/master/presentations/2024_05_OffensiveCon/OffensiveCon24_Booting_With_Caution_BDemirkapi.pdf?ref=blog.exploits.club
#OffensiveCon24
Not Simon 🐐
screaminggoat@infosec.exchangeMicrosoft out-of-band zero-day: CVE-2024-30060 - Security Update Guide
CVE-2024-30060 (7.8 high, disclosed 16 May 2024 by Microsoft) Azure Monitor Agent Elevation of Privilege Vulnerability with CWE-59: Improper Link Resolution Before File Access ('Link Following')
Is marked publicly disclosed, but Not Exploited, Exploitation LESS likely.
What privileges could be gained by an attacker who successfully exploited this vulnerability?
An authenticated attacker would be able to delete targeted files on a system which could result in them gaining SYSTEM privileges.
What actions do customers need to take to protect themselves from this vulnerability?
We released CVE-2024-30060 to help keep customers protected. Customers who have installed the latest updates, or have automatic updates enabled, are already protected. Customers who have disabled Automatic Extension Upgrades or would like to upgrade an extension immediately must manually update their Azure Monitor Agent to the latest version. For more information on how to perform a manual update, see Manage Azure Monitor Agent.
Dan Goodin
dangoodin@infosec.exchangeInfrastructure used to maintain and distribute the Linux operating system kernel was infected for two years, starting in 2009, by sophisticated malware that managed to get a hold of one of the developers’ most closely guarded resources: the /etc/shadow files that stored encrypted password data for more than 550 system users, researchers said Tuesday.
The unknown attackers behind the compromise infected at least four servers inside kernel.org, the Internet domain underpinning the sprawling Linux development and distribution network, the researchers from security firm ESET said. After obtaining the cryptographic hashes for 551 user accounts on the network, the attackers were able to convert half into plaintext passwords, likely through password-cracking techniques and the use of an advanced credential-stealing feature built into the malware. From there, the attackers used the servers to send spam and carry out other nefarious activities. The four servers were likely infected and disinfected at different times, with the last two being remediated at some point in 2011.
An infection of kernel.org came to light in 2011, when kernel maintainers revealed that 448 accounts had been compromised after attackers had somehow managed to gain unfettered, or “root,” system access to servers connected to the domain. Maintainers reneged on a promise to provide an autopsy of the hack, a decision that has limited the public’s understanding of the incident.
In 2014, ESET researchers said the 2011 attack likely infected kernel.org servers with a second piece of malware they called Ebury. The malware, the firm said, came in the form of a malicious code library that, when installed, created a backdoor in OpenSSH that provided the attackers with a remote root shell on infected hosts with no valid password required. In a little less than 22 months, starting in August 2011, Ebury spread to 25,000 servers. Besides the four belonging to the Linux Kernel Organization, the infection also touched one or more servers inside hosting facilities and an unnamed domain registrar and web hosting provider.
A 47-page report summarizing Ebury's 15-year history said that the infection hitting the kernel.org network began in 2009, two years earlier than the domain was previously thought to have been compromised. The report said that since 2009, the OpenSSH-dwelling malware has infected more than 400,000 servers, all running Linux except for about 400 FreeBSD servers, a dozen OpenBSD and SunOS servers, and at least one Mac.
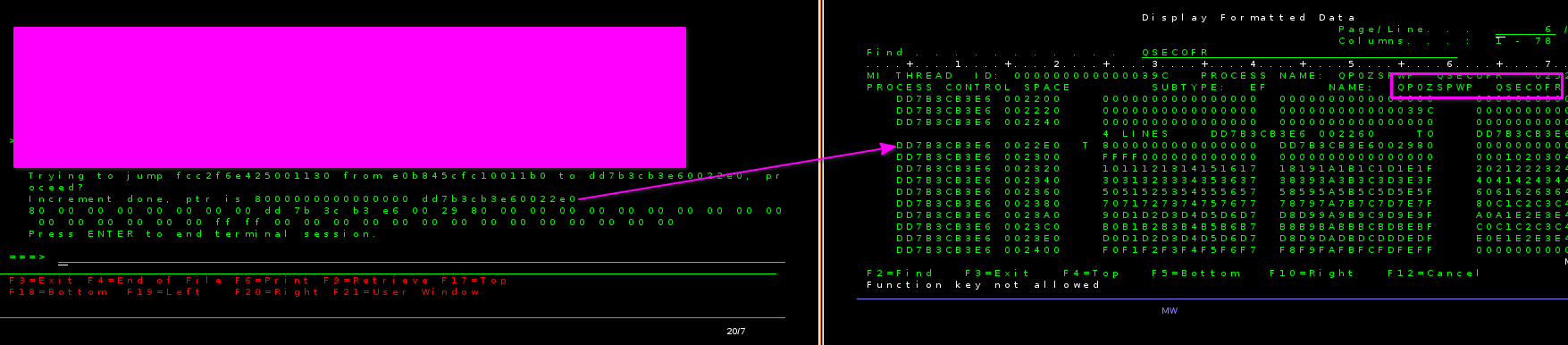
buherator
buheratorhttps://learn.microsoft.com/en-us/openspecs/windows_protocols/ms-smb/8b80e60b-7514-442b-baf4-eb785d0b0e2c
h/t @eckes
Akshat Rathi
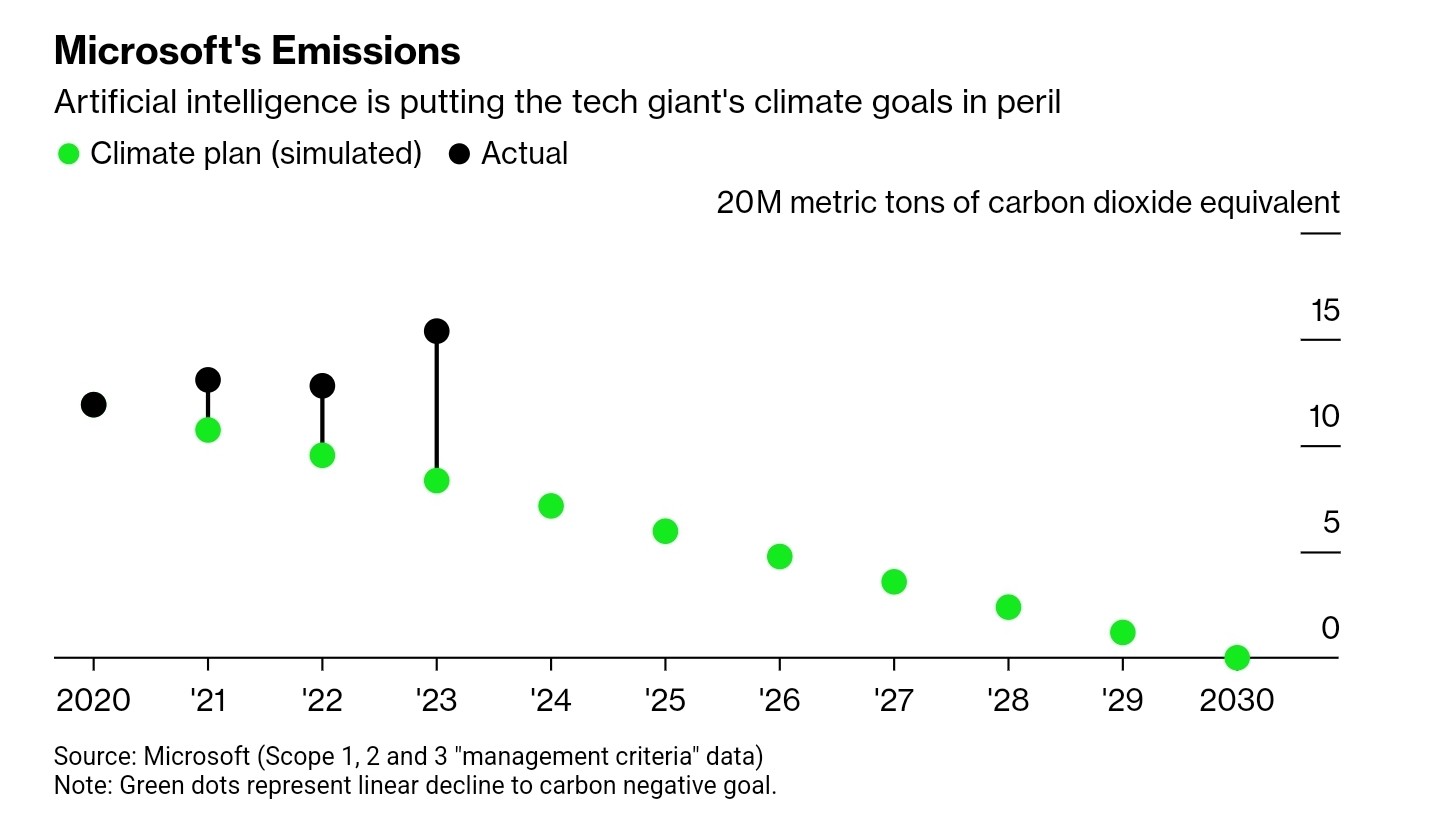
akshatrathi@mastodon.green2020: Microsoft sets goal to be carbon negative by end of the decade.
2023: Microsoft's emissions are 30% higher than in 2020.
Main cause? The relentless push to meet AI demand, which requires new data centers built out of carbon-intensive steel, cement, chips.
https://www.bloomberg.com/news/articles/2024-05-15/microsoft-s-ai-investment-imperils-climate-goal-as-emissions-jump-30
shellsharks
shellsharks@shellsharks.socialHey! I’m reviving my long-dormant #podcast, “The Shellsharks Podcast”. Exciting right?! In addition to the usual topics, i.e. "Infosec, Technology & Life", I'd like to spotlight awesome people from the #infosec community here on the #fediverse and discuss #indieweb and #personalweb topics. If that sounds cool or interesting, check out show page on my site where you can learn more.
https://shellsharks.com/podcast
Oh and the show is now on the Fediverse, powered by #Castopod. Follow @ShellsharksPodcast
AttackerKB
attackerkbTopic description: "** RESERVED ** This candidate has been reserved by an organization or individual that will use it when announcing a new security problem ..."
"CVE-2024-22026 is a local privilege escalation vulnerability in Ivanti EPMM (formerly MobileIron) server versions prior to 12.1.0.0, 12.0.0.0, and 11.12.0.1 ..."
Link: https://attackerkb.com/assessments/7f7b046e-eae8-4ef0-940e-eb49334c203e
buherator
buheratorbert hubert 🇺🇦🇪🇺
bert_hubert@fosstodon.orgYesterday I presented at the NL-NCSC / @SURF / @ACCSS symposium "Cyber Security & Society". According to Donald Tusk we are entering a new pre-war era, and I fear that he is right. I also fear that we do not have anything near a "war-time resilient" level of control over the IT infrastructures that our societies depend on utterly. We are sitting ducks & it is getting worse. Transcribed presentation, with slides, is here:
https://berthub.eu/articles/posts/cyber-security-pre-war-reality-check/
buherator
buheratorhttps://lcamtuf.substack.com/p/im-not-cheerleading-for-the-cisa
buherator
buheratorhttps://ha.cking.ch/s8_data_line_locator/
buherator
buheratorhttps://ssd-disclosure.com/ssd-advisory-d-link-dir-x4860-security-vulnerabilities/
buherator
buherator#OffensiveCon24 slides
https://www.openwall.com/presentations/OffensiveCon2024-Password-Cracking/
buherator
buherator#OffensiveCon24 slides
https://www.synacktiv.com/sites/default/files/2024-05/escaping_the_safari_sandbox_slides.pdf
buherator
buheratorhttps://hackyboiz.github.io/2024/05/12/pwndorei/newjeans-hyper-v-pt7/?s=09
Alex
aclark@fosstodon.orgHey folks!
I'm the creator of Python @pillow & today is my birthday. Can I ask you for a favor?
I'm looking for a new role & I'd appreciate a boost. Check out my resume here:
I'm passionate about Python, open source & making a living with open source. What's the next move?
Thank you @willmcgugan for the nudge ❤️