Posts
2477Following
663Followers
1487Dan Goodin
dangoodin@infosec.exchangeInfrastructure used to maintain and distribute the Linux operating system kernel was infected for two years, starting in 2009, by sophisticated malware that managed to get a hold of one of the developers’ most closely guarded resources: the /etc/shadow files that stored encrypted password data for more than 550 system users, researchers said Tuesday.
The unknown attackers behind the compromise infected at least four servers inside kernel.org, the Internet domain underpinning the sprawling Linux development and distribution network, the researchers from security firm ESET said. After obtaining the cryptographic hashes for 551 user accounts on the network, the attackers were able to convert half into plaintext passwords, likely through password-cracking techniques and the use of an advanced credential-stealing feature built into the malware. From there, the attackers used the servers to send spam and carry out other nefarious activities. The four servers were likely infected and disinfected at different times, with the last two being remediated at some point in 2011.
An infection of kernel.org came to light in 2011, when kernel maintainers revealed that 448 accounts had been compromised after attackers had somehow managed to gain unfettered, or “root,” system access to servers connected to the domain. Maintainers reneged on a promise to provide an autopsy of the hack, a decision that has limited the public’s understanding of the incident.
In 2014, ESET researchers said the 2011 attack likely infected kernel.org servers with a second piece of malware they called Ebury. The malware, the firm said, came in the form of a malicious code library that, when installed, created a backdoor in OpenSSH that provided the attackers with a remote root shell on infected hosts with no valid password required. In a little less than 22 months, starting in August 2011, Ebury spread to 25,000 servers. Besides the four belonging to the Linux Kernel Organization, the infection also touched one or more servers inside hosting facilities and an unnamed domain registrar and web hosting provider.
A 47-page report summarizing Ebury's 15-year history said that the infection hitting the kernel.org network began in 2009, two years earlier than the domain was previously thought to have been compromised. The report said that since 2009, the OpenSSH-dwelling malware has infected more than 400,000 servers, all running Linux except for about 400 FreeBSD servers, a dozen OpenBSD and SunOS servers, and at least one Mac.
Akshat Rathi
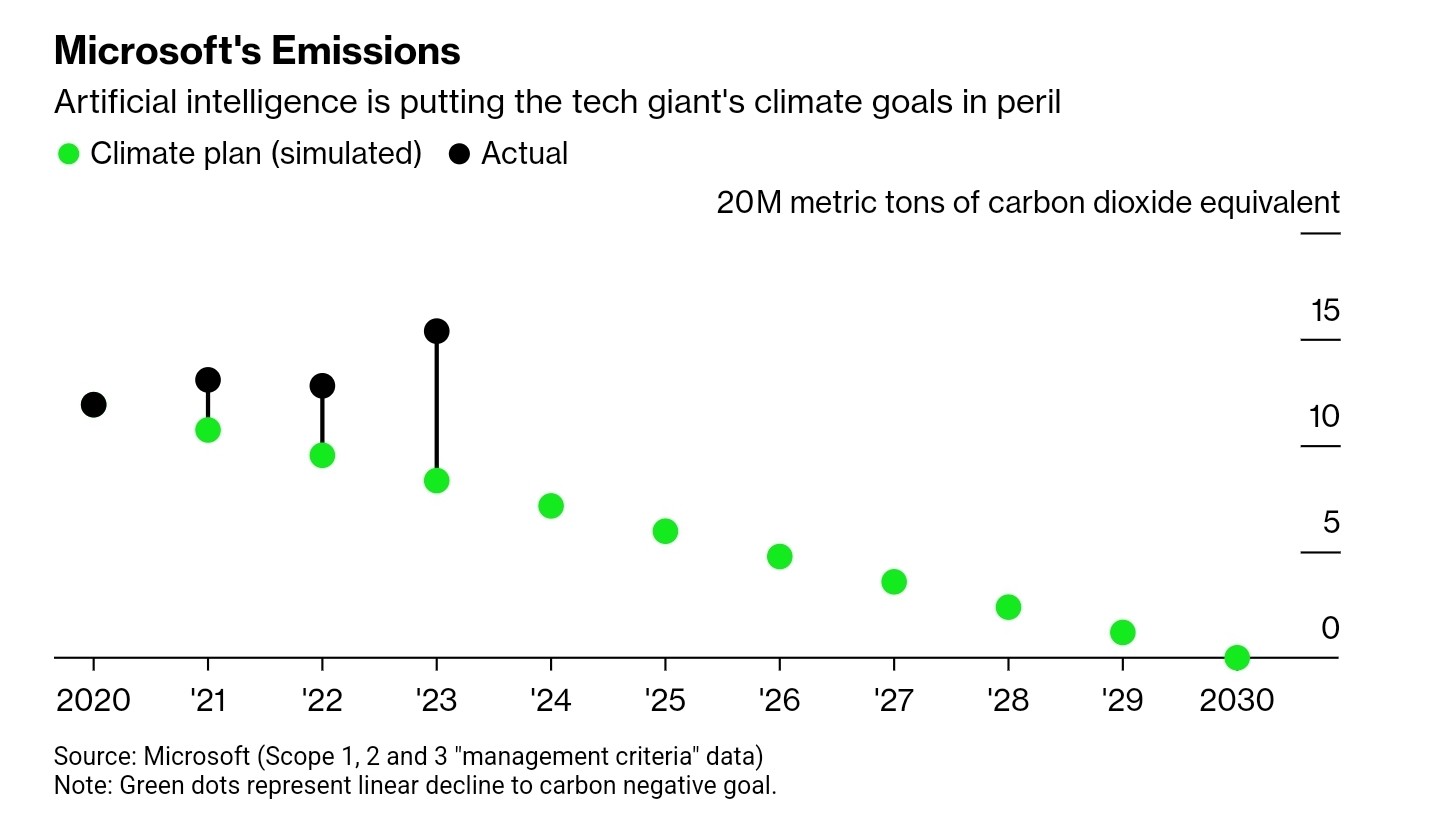
akshatrathi@mastodon.green2020: Microsoft sets goal to be carbon negative by end of the decade.
2023: Microsoft's emissions are 30% higher than in 2020.
Main cause? The relentless push to meet AI demand, which requires new data centers built out of carbon-intensive steel, cement, chips.
https://www.bloomberg.com/news/articles/2024-05-15/microsoft-s-ai-investment-imperils-climate-goal-as-emissions-jump-30
shellsharks
shellsharks@shellsharks.socialHey! I’m reviving my long-dormant #podcast, “The Shellsharks Podcast”. Exciting right?! In addition to the usual topics, i.e. "Infosec, Technology & Life", I'd like to spotlight awesome people from the #infosec community here on the #fediverse and discuss #indieweb and #personalweb topics. If that sounds cool or interesting, check out show page on my site where you can learn more.
https://shellsharks.com/podcast
Oh and the show is now on the Fediverse, powered by #Castopod. Follow @ShellsharksPodcast
bert hubert 🇺🇦🇪🇺🇺🇦
bert_hubert@fosstodon.orgYesterday I presented at the NL-NCSC / @SURF / @ACCSS symposium "Cyber Security & Society". According to Donald Tusk we are entering a new pre-war era, and I fear that he is right. I also fear that we do not have anything near a "war-time resilient" level of control over the IT infrastructures that our societies depend on utterly. We are sitting ducks & it is getting worse. Transcribed presentation, with slides, is here:
https://berthub.eu/articles/posts/cyber-security-pre-war-reality-check/
Alex
aclark@fosstodon.orgHey folks!
I'm the creator of Python @pillow & today is my birthday. Can I ask you for a favor?
I'm looking for a new role & I'd appreciate a boost. Check out my resume here:
I'm passionate about Python, open source & making a living with open source. What's the next move?
Thank you @willmcgugan for the nudge ❤️
Team KeePassXC
keepassxc@fosstodon.orgDebian Users - Be aware the maintainer of the KeePassXC package for Debian has unilaterally decided to remove ALL features from it. You will need to switch to `keepassxc-full` to maintain capabilities once this lands outside of testing/sid.
Silent Signal
silentsignal@infosec.exchangeWe are glad to announce that our #IBMi research will be presented at multiple prestigious conferences this June:
At @WEareTROOPERS we will show how pentesters can adopt their Windows/*nix experiences to the platform, and discover new vulnerabilities in native IBM i programs:
https://troopers.de/troopers24/talks/7sfsbf/
At @recon will dive deep into the architecture to understand its security features and present foundational tools for low-level research:
screaminggoat
screaminggoat@infosec.exchangeNational Health Service England (NHS): Possible Exploitation of Arcserve Unified Data Protection (UDP) Vulnerabilities
NHS England reports possible N-day exploitation attempts of Arcserve UDP following the release of proofs of concepts for 3 vulnerabilities:
- CVE-2024-0799 (9.8 critical) authentication bypass
- CVE-2024-0800 (8.8 high) path traversal vulnerability leads to arbitrary file upload
- CVE-2024-0801 (CVSS score pending) Denial-of-Service (DoS)
Tenable released proofs of concept: Arcserve Unified Data Protection 9.2 Multiple Vulnerabilities
Based on the timeline, active exploitation occurred during an unpatched window of 8 days (13-20 March 2024)
cc: @campuscodi
#CVE_2024_0799 #CVE_2024_0800 #CVE_2024_0801 #Arcserve #eitw #activeexploitation
bert hubert 🇺🇦🇪🇺🇺🇦
bert_hubert@fosstodon.org"Writing has been called the process by which you find out you don't know what you are talking about. Actually doing stuff meanwhile is the process by which you find out you also did not know what you were writing about." - from https://berthub.eu/articles/posts/a-2024-plea-for-lean-software/#trifecta
Hannah Kolbeck 🏳️⚧️
hannah@social.alt-text.orgHi friends,
The http://alt-text.org alt text library project needs a new leader, because I have brain cancer.
I would like to connect with the #accessibility dev community, something I have never figured out, probably in part for neurodivergence reasons. I want to hand the project off to a team or a leader if anyone is willing to take it over.
Github: https://github.com/alt-text-org
WIP MVP: a site designed for writing alt text with a private library: https://my.alt-text.org
Boosts appreciated
Kelly Shortridge
shortridge@hachyderm.iowent down to the hotel lobby to retrieve my dinner delivery in a yoga outfit + snuggly cardigan + face mask.
some men with #RSAC2024 lanyards exited the elevator as I re-entered; they turned back to look at me and one said (very loudly, very pointedly staring at me) to the other, “I was like, did you hire me a hooker?”
if you are a man attending #rsac, please shut that kind of shit down when your peers do it. let’s not let insecurity rule our #security industry.
Marco Ivaldi
raptor@infosec.exchangeIt was a pleasure to work with @RIOT_OS maintainers to contribute in making their RTOS more secure! https://infosec.exchange/@hnsec/112398919861504786
Foone🏳️⚧️
foone@digipres.clubThe way sentences containing the German character ß get longer when uppercased was specially designed to create memory problems in C programs doing string handling
Molly White
molly0xfff@hachyderm.iofinally made an "AI" category (https://www.web3isgoinggreat.com/?collection=ai) for @web3isgreat to capture all the disasters pertaining to AI-powered cryptocurrencies and cryptocurrency-powered AI
Amin Hollon 🏳
amin@alpha.polymaths.socialI'm proud to announce the launch of the public beta for Clew, my independent web search engine! 🎉🎉🎉
Try Clew: https://clew.se
Add to your browser: https://clew.se/add/
Clew maintains an independent index and is aiming to be a copyleft (APGLv3), self-hostable, privacy-respecting, customizable search engine which prioritizes independent creators/bloggers/writers and penalizes sites with ads and trackers.
Many features are yet to come. If you'd like to support Clew's development and server costs, you can donate to its Liberapay team: https://liberapay.com/Clew/
Boosts are very welcome, as is feedback of any kind!
Hazel Weakly
hazelweakly@hachyderm.ioAny sufficiently advanced systems thinking is indistinguishable from premature optimization
Street Art Utopia
streetartutopia@mastodon.onlineMedieval humor! 9 Astonishing Gargoyle Statues: https://streetartutopia.com/medieval-humor-9-astonishing-gargoyle-statues-a-blend-of-art-and-functionality-in-gothic-architecture/
-
Photo: At Abbey of Sainte Foy, Conques, France (c. 1107).
Kinda crazy that artificial intelligence needs the entire output of a nuclear reactor but actual intelligence can run on Twix bars and cocaine, for example.