Posts
3339Following
710Followers
1577buherator
buheratorMy 2c:
- Red Teams should be about the "difficult" things you mention at the end IMO. Spending resources on initial access is mostly pointless (from the client's perspective, finding 0d is always cool ofc) when a new blinky box exploit, leaked code signing cert, etc. is popping up every other week. IME many clients pay for (bad) initial access simulations because organizing assumed breach in-house is hard.
- A way to burst the bubbles you describe is to mandate scenarios based on real-world threat intel. But this works against intial access again, because RT's can't scale their R&D as black hats do (attack surface is clients vs the Internet).
raptor 
raptor@infosec.exchange
RE: https://mastodon.social/@XC3LL/115990518822402879
Very valuable insight if you are into #redteaming
Dissent Doe 
PogoWasRight@infosec.exchange
For researchers and those trying to disclose incidents responsibly or get help:
There is an international organization called FIRST.
From the FIRST Teams website:
"This is a list of the contact information for incident response teams participating in FIRST, the Forum of Incident Response and Security Teams. The teams are responsible for providing FIRST with their latest contact information for this page. The list is alphabetized by team name. All telephone numbers are preceded with the appropriate country code."
There are 829 teams listed. Some are government CERT teams, some are corporate incident response teams.
You might want to bookmark the site to speed up your attempt to contact these teams:
Cat 🐈🥗 (D.Burch) 

catsalad@infosec.exchange
@cR0w Fursuits are a natural evolution to working in server rooms
diyelectromusic
diyelectromusic@mastodon.socialI appear to have created a "sound card" for a 4-bit CPU.
As you do.
LaurieWired
lauriewired@bird.makeuptoday’s one-sentence horror:
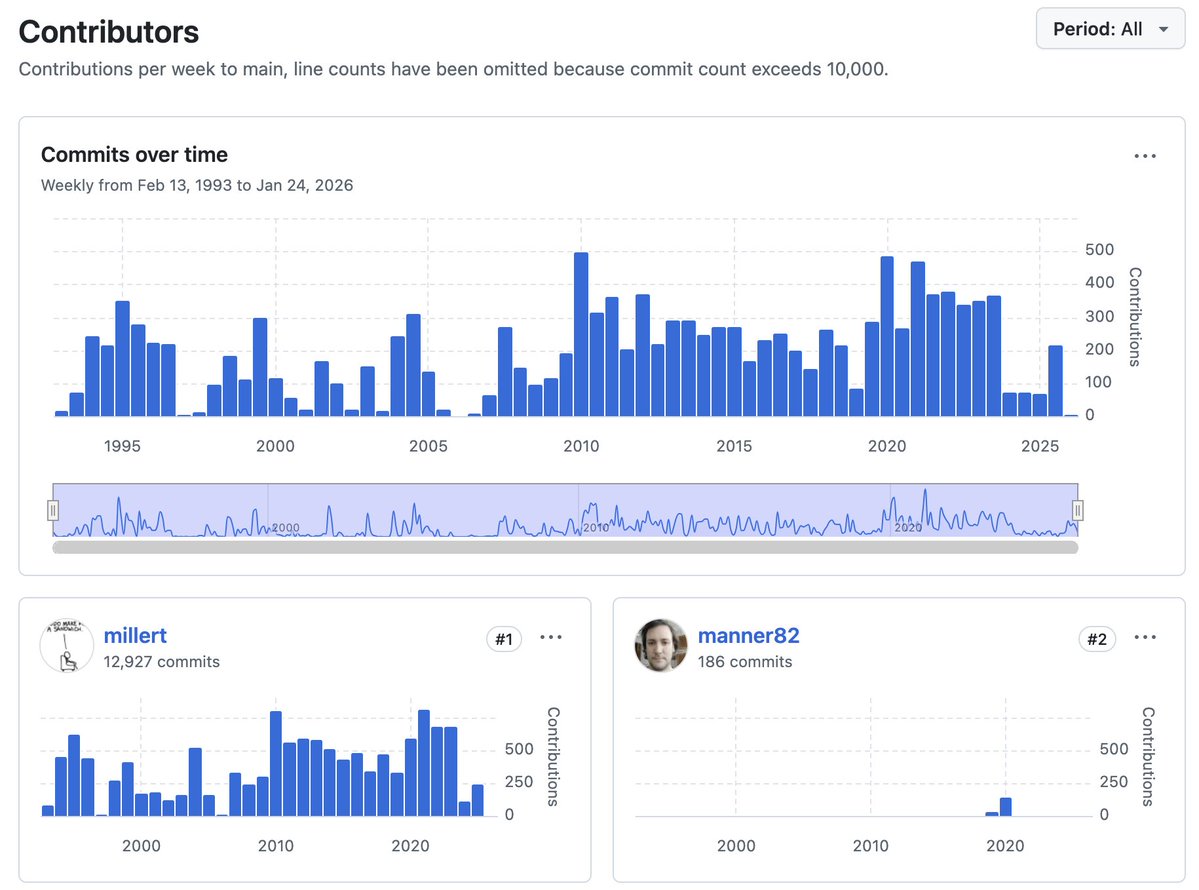
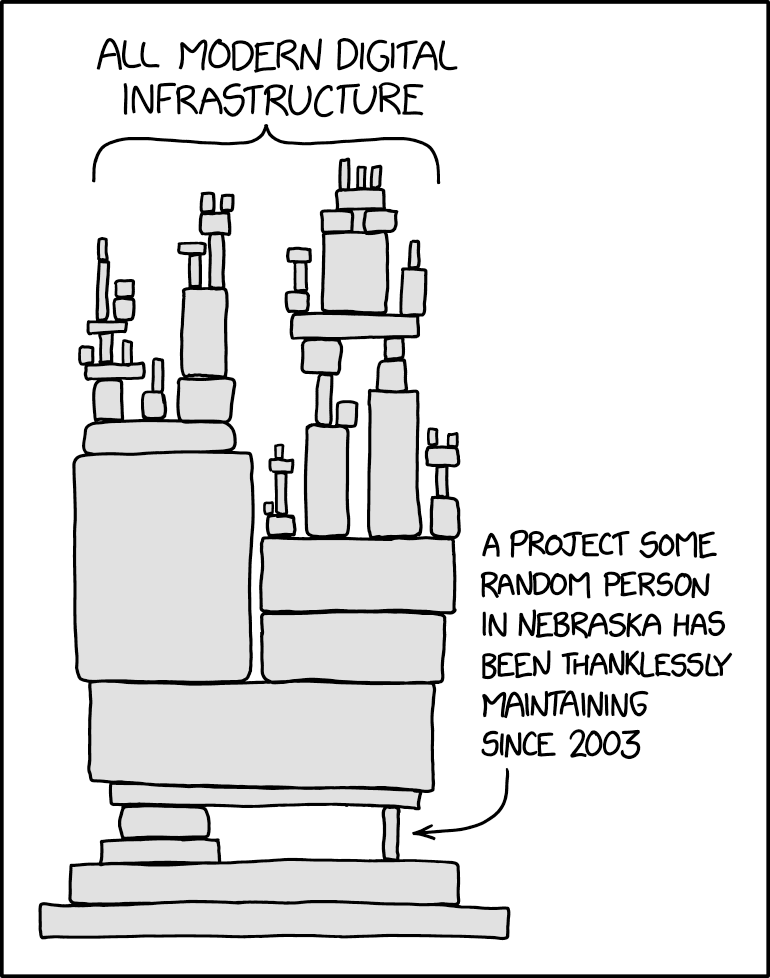
sudo has been largely maintained by a single person for ~30+ years
buherator
buheratorhttps://securityaffairs.com/187515/laws-and-regulations/doj-releases-details-alleged-talented-hacker-working-for-jeffrey-epstein.html
buherator
buheratorWhat’s the difference between SafeArrayAccessData and SafeArrayAddRef?
https://devblogs.microsoft.com/oldnewthing/20260126-00/?p=112016
A digression on the design and implementation of SafeArrayAddRef and extending APIs in general
https://devblogs.microsoft.com/oldnewthing/20260127-00/?p=112018
Why did I lose the data even though I called SafeArrayAddRef?
https://devblogs.microsoft.com/oldnewthing/20260128-00/?p=112021
How can I retain access to the data in a SAFEARRAY after my method returns?
https://devblogs.microsoft.com/oldnewthing/20260129-00/?p=112023
Why not store the SAFEARRAY reference count as a hidden allocation next to the SAFEARRAY?
https://devblogs.microsoft.com/oldnewthing/20260130-00/?p=112025
buherator
buheratorhttps://devblogs.microsoft.com/oldnewthing/20260127-00/?p=112018
buherator
buheratorhttps://github.com/finngineering/apxutil
SkelSec
skelsec@bird.makeupFinally had some time and llm subscription enough to refactor my asynchronous WinRM library awinrm.
It is based off of pywinrm, but has two key improvements: async and native (python) auth types including kerberos.
Available on Github and pip.
https://github.com/skelsec/awinrm/releases/tag/0.1.0
buherator
buherator[...]
Because the iPhone was in Lockdown mode, CART could not extract that device"
https://www.reddit.com/r/privacy/comments/1qsmy8g/fbi_was_not_able_to_extract_data_from_iphone_13/
buherator
buheratorIt appears Epstein attended DEFCON and/or BlackHat in 2013 and 2015, possibly 2016."
https://x.com/vxunderground/status/2017673353335542039
/via @vxunderground
buherator
buheratorhttps://scrapco.de/ghidra_docs/VERSION12/
(Note that the URLs changed recently so docs for both the latest version 11 and 12 are browsable)
buherator
buheratorhttps://blog.exploits.club/exploits-club-weekly-ish-newsletter-94-p20-vmware-bugs-expdev-with-llms-pixel-0-click-bugs-and-more/
buherator
buheratorhttps://www.openwall.com/lists/oss-security/2026/01/31/2
Yarden Shafir
yarden_shafir@infosec.exchangeRegistration is open to all RECon classes!
As usual, I’ll be teaching Windows Internals. This is the only time this year that the class is offered in North America 😊
And if windows isn’t your thing, there are lots of other great classes!
https://recon.cx/2026/en/training.html#trainingWindowsInternals
buherator
buheratorhttps://securelist.com/escan-supply-chain-attack/118688/
A threat that many people have warned about for a long time. A bit ironic to read this on Kaspersky's site...
h/t @zh4ck
Tim (Wadhwa-)Brown 
timb_machine@infosec.exchange
Interesting links of the week:
Strategy:
* https://www-tokio--dr-jp.translate.goog/thinktank/acd/acd-007.html - active defense in .jp
* https://www.cambridge.org/core/books/securing-democracies/stacking-up-for-resilience/EB2072FAE9F97CF41B568B1C4AAFC190 - building digital resilience ala India
* https://www.csis.org/analysis/civil-takedowns-missing-legal-framework-cyber-disruption - avoiding disruption when performing takedowns
* https://breakmeifyoucan.com/
https://sabsa.org/w105-sabsa-enterprise-security-architecture-principles/ - constructing a security architecture using SABSA principles
* https://www.ncsc.gov.uk/collection/how-to-prepare-and-plan-your-organisations-response-to-severe-cyber-threat-a-guide-for-cni - NCSC guidance on how to not get yourself in a panic
* https://home.treasury.gov/system/files/136/G7-CEG-Quantum-Roadmap.pdf - a roadmap for quantum
Standards:
* https://www.etsi.org/deliver/etsi_en/304200_304299/304223/02.01.01_60/en_304223v020101p.pdf - ETSI standards on AI in public life
Threats:
* https://ethz.ch/content/dam/ethz/special-interest/gess/cis/center-for-securities-studies/pdfs/before-vegas-cyberdefense-report.pdf - understanding .cn hackers in long form
* https://www.bitsight.com/blog/what-is-y2k38-problem - do you even 2038?
Detection:
* https://it4sec.substack.com/p/detect-rogue-cell-towers-for-50-who - hunting rogue radios
* https://www.detectionengineering.net/ - a nice news feed for detection engineers
* https://github.com/OpenTideHQ/.github/blob/main/profile/OpenTide%20White%20Paper.pdf - paper on OpenTIDE
* https://huggingface.co/datasets/CIRCL/vulnerability-cwe-patch - enriching bug classifications
* https://arxiv.org/abs/2402.15147 - mapping techniques
* https://www.huntress.com/blog/ldap-active-directory-detection-part-three - @huntress discuss AD's LDAP logs
* https://api.gcforum.org/api/files/public/upload/523c55f1-b24a-4824-a841-b513c2aca3bc_Practical-Threat-Detections.pdf - getting the most from your telco logs
Bugs:
* https://www.zerodayinitiative.com/advisories/ZDI-26-020/ - why are LLMs so quick to oopsie
* https://www.interruptlabs.co.uk/articles/when-nas-vendors-forget-how-tls-works - TLS is hard
* https://projectzero.google/2026/01/pixel-0-click-part-1.html - taking over the world, Pixel by Pixel
* https://projectzero.google/2026/26/windows-administrator-protection.html - @tiraniddo beats up admins
* https://whisperpair.eu/ - BTLE gets another bad report
* https://www.atredis.com/blog/2026/1/26/generals - exploiting games for fun, high scores and remote tank execution
* https://fortiguard.fortinet.com/psirt/FG-IR-26-060 - FortiCloud makes a splash
Exploitation:
* https://www.synacktiv.com/publications/pentesting-cisco-aci-lldp-mishandling - kicking Cisco's ACI tyres
* https://shazzer.co.uk/blog/distributed-fuzzing-crowdsourced-browser-testing - scaling browser fuzzing from @gaz
* https://dl.acm.org/doi/10.1145/3776743 - inferring grammar from parsing
* https://arxiv.org/abs/2601.01592 - breaking multi-model AI
Hard hacks:
* https://jyn.dev/remotely-unlocking-an-encrypted-hard-disk/ - picking the hard disk lock