Posts
3275Following
709Followers
1570Rust Language
rust@social.rust-lang.orgRust 1.93.0 has been released! 🌈 🦀✨
This release includes a new musl version for the *-linux-musl targets, adds support for #[cfg] inside asm!(), and adds [T]::as_array, VecDeque::{pop_front_if, pop_back_if}, Vec/String::into_raw_parts, fmt::form_fn, and more! ✨
Check out the blog post and release notes for all the details: https://blog.rust-lang.org/2026/01/22/Rust-1.93.0/
Soatok Dreamseeker
soatok@furry.engineerJWT {"alg": "let-me-innnnn"} vuln
https://pentesterlab.com/blog/cve-2026-23993-harbourjwt-unknown-alg-jwt-bypass
Trail of Bits
trailofbits@infosec.exchangeTEE security breaks down in predictable ways. In our December webinar, we showed exactly where.
Jules Drean from Tinfoil walked through their threat model, covering repositories, hardware configurations, and CVM images. Our security engineers, Paul Bottinelli and Tjaden Hess, dug into vulnerabilities they've found in production TEE deployments.
Watch the full recording: https://watch.getcontrast.io/register/trail-of-bits-top-tee-bugs-you-should-fix-before-your-audit?utm_source=socials
buherator
buheratorhttps://code-white.com/public-vulnerability-list/#authenticationserviceforceresetpassword-missing-authentication-in-smartermail
I'm curious about the story here!
ploum
ploum@mamot.frWhy there’s no European Google?
And why it is a good thing!
My answer to the European Commission "call for evidence on Open Source."
https://ploum.net/2026-01-22-why-no-european-google.html
#geminiprotocol link: gemini://ploum.net/2026-01-22-why-no-european-google.gmi
Kagi HQ
kagihq@mastodon.socialKagi is growing! We're seeking an experienced Product Designer to join our fully remote team. If you're passionate about our vision and meet the qualifications outlined below, we'd love to hear from you!
https://kagi.peopleforce.io/careers/v/178633-product-designer-uiux
/r/netsec
_r_netsec@infosec.exchangeCVE-2026-22200: Ticket to Shell in osTicket https://horizon3.ai/attack-research/attack-blogs/ticket-to-shell-exploiting-php-filters-and-cnext-in-osticket-cve-2026-22200/
alfie
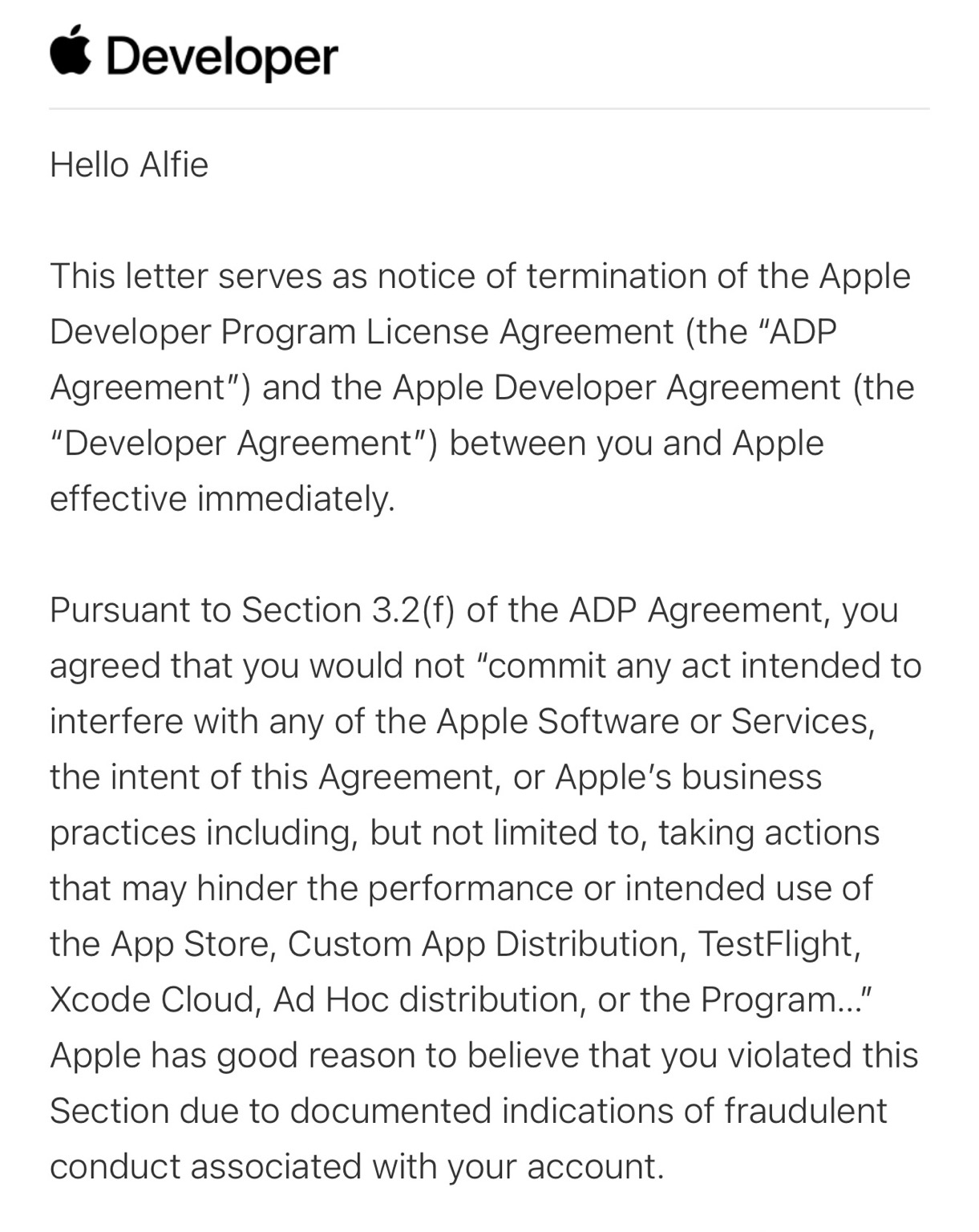
alfie@procursus.socialWe need legislation on sideloading ASAP. Yesterday, I learned the hard way that I’m not allowed to use my own personal, paid developer certificate to sign IPAs I want to install on my own personal device. Wow. 😬
Jerry 🦙💝🦙
jerry@infosec.exchangeGoogle released its plan for opting out of its AI https://youtube.com/shorts/qnBWMcKKkKE?si=MnLxFNzzX8n3JAEo
[realhackhistory@home]#
realhackhistory@chaos.socialI’ve written about the history of the word hacker and the word cracker, in French “hacker” is “pirate” and this little news clipping from L’Evangéline from May of 1980 shows that the word was in mainstream use earlier than hacker was in English. I think this is a story about the Dalton Gang.
buherator
buheratorRE: https://mastodon.social/@noybeu/115938255720880883
blasty
bl4sty@bird.makeuppov: you’re in the office at 3am on a Wednesday finally able to control the duty cycle of a pwm signal (and pondering your life choices)
buherator
buherator(Edit: I'm also pretty sure things are not great on Africa, it's just no one gives a shit...)
TrendAI Zero Day Initiative
thezdi@infosec.exchangeIn a highlight from Day One of #Pwn2Own Automotive 2026, @synacktiv targets the #Tesla infotainment system. #P2OAuto
https://youtube.com/shorts/DKYT-LrZmZs
buherator
buheratorhttps://exploit.az/posts/wor/
CVE-2025-48941
Sometimes the job interview just wants to gain code exec on your machine:
https://runjak.codes/posts/2026-01-21-adversarial-coding-test/
Local girl failed the coding interview:
I don't think they've got a job for me anymore now that I got their repos deleted⁉️
Tim (Wadhwa-)Brown 
timb_machine@infosec.exchange
Interesting links of the week:
Strategy:
* https://assets.publishing.service.gov.uk/media/696e0eae719d837d69afc7de/National_security_assessment_-_global_biodiversity_loss__ecosystem_collapse_and_national_security.pdf - biodiversity and national security
* https://www.gov.uk/government/publications/software-security-ambassadors-scheme - when you get summoned to number 10 for a nasty oopsie
* https://www.cjr.org/news/hannah-natanson-fbi-washington-post-raid-devices-seized-runa-sandvik-security-computer-phone-laptop-sources.php - how to blow whistles safely, is it even possible?
* https://www.bankofengland.co.uk/financial-stability/operational-resilience-of-the-financial-sector/2025-cbest-thematic - themes and trends from UK FSI red teaming under Bank of England's CBEST programme
Standards:
* https://aivss.parthsohaney.online/calculator - a stab at quantifying AI risk... not convinced it'll work but at least people are thinking about the problem
Threats:
* https://www.esentire.com/blog/new-botnet-emerges-from-the-shadows-nightshadec2 - yay, more C2
Detection:
* https://github.com/RustyNoob-619/100-Days-of-YARA-2026/blob/main/Rules%2FDay17.yara - always like a bit of nice YARA
* https://andpalmier.com/posts/abuse-ch-toolkit/ - tools for @abuse_ch
Bugs:
* https://seclists.org/oss-sec/2026/q1/89 - finally Linux telnetd gets an auth-pass feature
* https://sigma-star.at/blog/2025/12/unix-v4-buffer-overflow/ - CVE wen, an overflow in UNIX v4
* https://www.ibm.com/support/pages/node/7257143 - so you wanna pop a mainframe?
Exploitation:
* https://github.blog/developer-skills/github/codeql-zero-to-hero-part-1-the-fundamentals-of-static-analysis-for-vulnerability-research/ - hunting bugs with CodeQL
* https://sean.heelan.io/2026/01/18/on-the-coming-industrialisation-of-exploit-generation-with-llms/ - industrialising set $pc=0x41414141
* https://netaskari.substack.com/p/whats-in-the-box - pentesting in .cn
* https://cloud.google.com/blog/topics/threat-intelligence/net-ntlmv1-deprecation-rainbow-tables - GOOG launch rainbows, share Net NTLMv1 pot of gold
*
https://www.bsi.bund.de/SharedDocs/Downloads/DE/BSI/Publikationen/DVS-Berichte/passwortmanager_sicherheit_datenschutz.pdf - .de takes pop at password managers
* https://security.opensuse.org/2026/01/16/the-journey-of-auditing-uyuni.html - SuSE takes UYUNI for a space walk
Hard hacks:
* https://medium.com/@marcel.rickcen/no-tamper-alert-no-password-and-a-backdoor-root-access-on-a-pos-credit-card-payment-terminal-1ea32c73ca41 - what a POS
* https://neodyme.io/en/blog/drone_hacking_part_1/ - on and on, they drone
* https://blog.nns.ee/2026/01/06/aike-ble/ - sniffing scooter emissions
* https://lucasteske.dev/2025/09/running-code-in-pax-machines - this looks like payback
* https://web.archive.org/web/20160128030439/http://www.elemental.net/%7Elf/undoc/ - undocumented Cisco commands
Hardening:
* https://learn.microsoft.com/en-us/windows-server/identity/ad-ds/plan/delegating-administration-by-using-ou-objects - delegation in AD by OU
Nerd:
* https://rbanffy.github.io/fun-with-old-mainframes.github.io/fun-with-vm370.html - mmm, greenscreen
* https://openmail.one/ - OpenAI lawsuits ahoi!
watchTowr
watchTowr@infosec.exchangeEarlier this month, we reported a zero-day auth. bypass in the SmarterTools SmarterMail email solution.
Someone has reversed the patch (released on 15th Jan) and begun exploiting it in the wild.
Read our analysis and please, ASSUME BREACH + PATCH NOW.
daniel:// stenberg://
bagder@mastodon.social#curl is RFC 9116 compliant
https://curl.se/.well-known/security.txt
https :// curl.se / .well-known / security.txt