Posts
3178Following
705Followers
1561buherator
buheratorhttps://www.dlp.rip/decorative-cryptography
"All encryption is end-to-end, if you’re not picky about the ends."
buherator
buheratorbuherator
buheratorbuherator
buheratorhttps://en.wikipedia.org/wiki/The_purpose_of_a_system_is_what_it_does
This is exactly what I've been trying to articulate re: cookie banners. The word of the regulation and intent is largely irrelevant to the effect it caused.
buherator
buherator(no I won't open an Issue/PR, let them figure out themselves...)
Kagi HQ
kagihq@mastodon.socialhackaday
hackaday@hackaday.socialGitHub Disables Rockchip’s Linux MPP Repository After DMCA Request
https://hackaday.com/2026/01/05/github-disables-rockchips-linux-mpp-repository-after-dmca-request/
hakan “ ”
”
hatr@infosec.exchange
"Die Zeit" reveals that German foreign intelligence, in a multi-year campaign, intercepted Barack Obama's phone calls while aboard Air Force One because the encryption was flawed. Angela Merkel didn't know about it.
https://www.zeit.de/politik/ausland/2026-01/bnd-barack-obama-air-force-one-angela-merkel
Joxean Koret (@matalaz)
joxean@mastodon.socialA Glimpse Into DexProtector
https://www.romainthomas.fr/post/26-01-dexprotector/
buherator
buheratorbuherator
buheratorbuherator
buheratorhttps://www.youtube.com/watch?v=_eem7AVAMpI&list=PLHu2EA4lxh3Yvaa5sr9TYM3ywzGFBbpR8
sen
sen@hachyderm.ioThis is my every-once-in-awhile post since I’m thinking about it today: if you have a lead on install media, an image of a dev/test system, etc. for the Dynix ILS (from the 1980s/90s), please reach out. No, it’s not on Internet Archive despite some things saying it is.
TorrentFreak
torrentfreak@defcon.socialAnna’s Archive Loses .Org Domain After Surprise Suspension https://torrentfreak.com/annas-archive-loses-org-domain-after-surprise-suspension/
buherator
buheratorhttps://medium.com/@Debugger/driver-power-state-failure-0x9f-tracking-a-stuck-usb-power-irp-to-focusriteusb-f82e93688a97?source=rss-3ba65b326b28------2
buherator
buheratorhttps://faith2dxy.xyz/2026-01-03/cve_2025_38352_analysis_part_3/
buherator
buheratorhttps://www.hoyahaxa.com/2026/01/rce-via-coldfusion-archive-car.html
Proteas
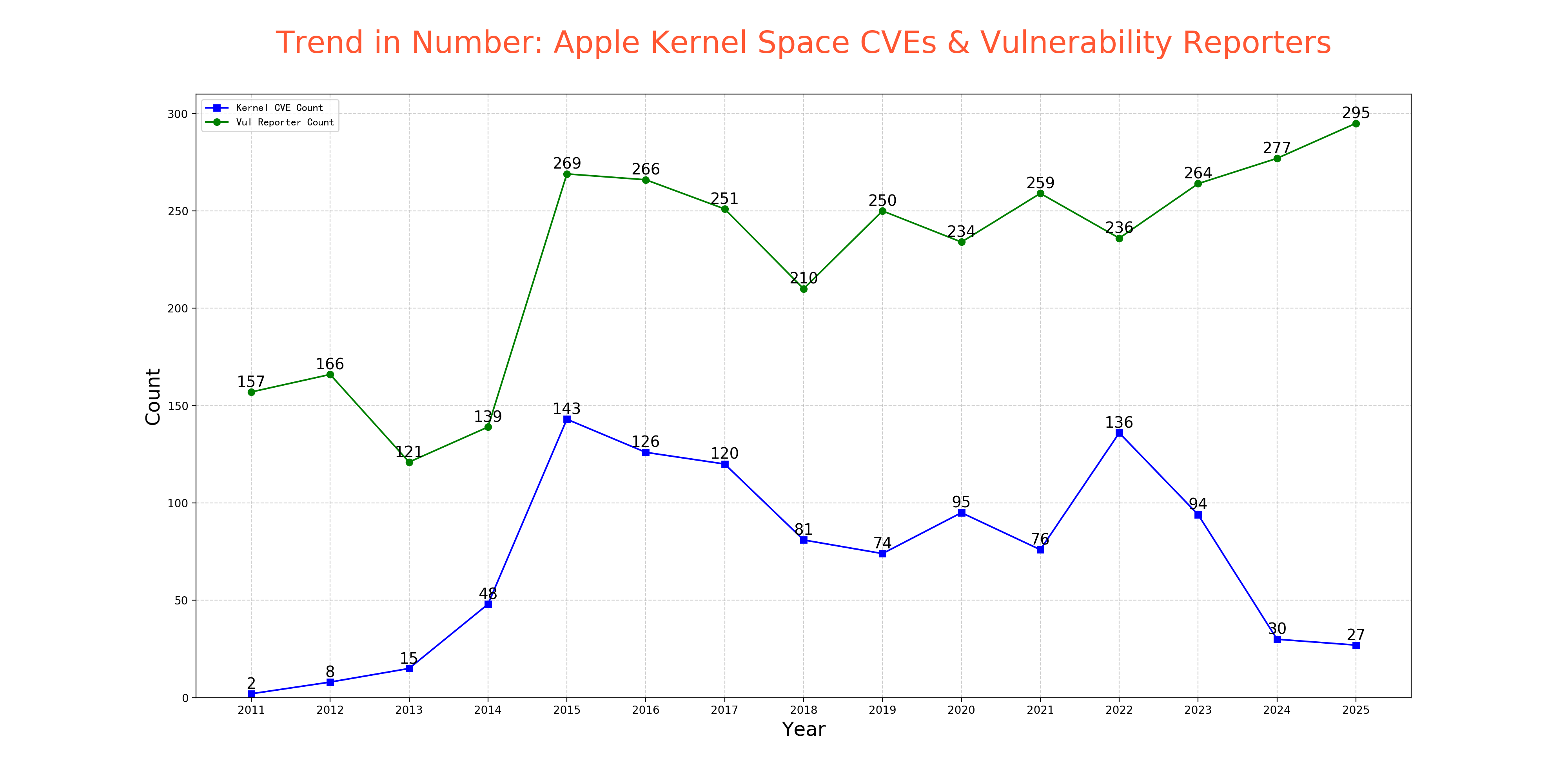
Proteas@infosec.exchangeTrend in Number: Apple Kernel Space CVEs & Vulnerability Reporters
The blue line represents the number of kernel CVEs, and the green line represents the number of vulnerability reporters across the entire Apple platform. Starting in 2022, the number of vulnerability reporters has been increasing, while the number of kernel CVEs has been decreasing.
Filippo Valsorda
filippo@abyssdomain.expertDo you have an idle cluster? Can you spare a couple core-years?
Help me bruteforce some test vectors for RSA key generation edge cases!
Here are the instructions, it's just a matter of running a single self-contained cross-compilable Go binary that will report the results autonomously.
https://gist.github.com/FiloSottile/19e7ceb1fdcdaa128f7d3319ad0939fa
x3r0x@arch# 
x3r0x@hispagatos.space
A German hacker known as "Martha Root" dressed as a pink Power Ranger and deleted a white supremacist dating website live onstage
This happened during the recent CCC conference.
Martha had infiltrated the site, ran her own AI chatbot to extract as much information from users as possible, and downloaded every profile. She also uncovered the owner of the site. She has published all of the data.
#CCC
https://media.ccc.de/v/39c3-the-heartbreak-machine-nazis-in-the-echo-chamber
Leak data:
https://okstupid.lol/