Posts
3180Following
705Followers
1561buherator
buheratorhttps://python.docs.hex-rays.com/classida__typeinf_1_1array__type__data__t.html#a9740d10e79d54aee5b4423adbe9a1881
jiska 🦄
jiska@chaos.social
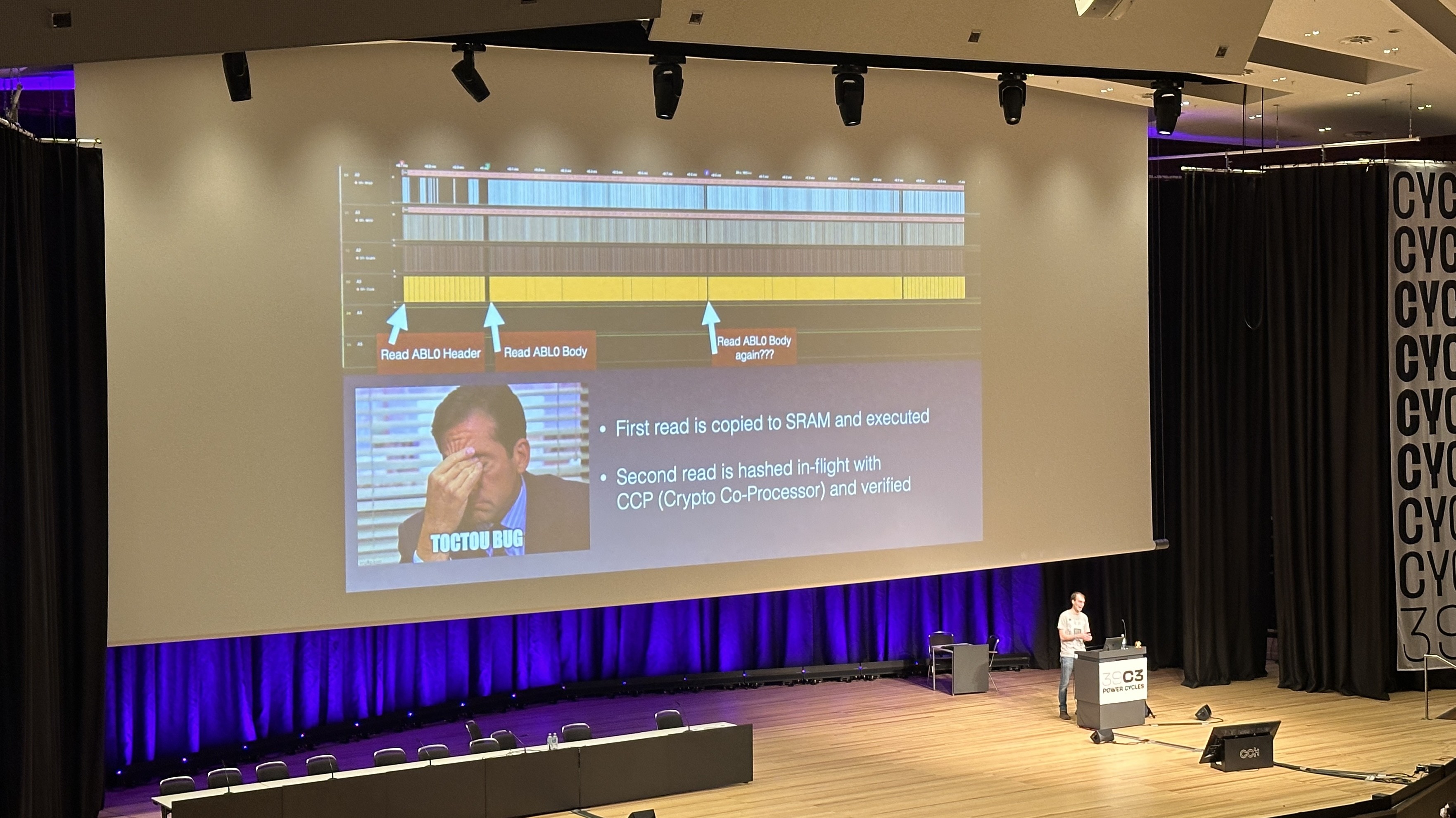
Want to know how Apple's Low Latency WiFi works?
Today, 3:40pm CET, Hall 1, #39c3.
More details: https://events.ccc.de/congress/2025/hub/event/detail/cracking-open-what-makes-apple-s-low-latency-wifi-so-fast
Stream: https://streaming.media.ccc.de/39c3/one
buherator
buheratorEven skeptics have to admit that LLMs are very good at natural language translation. @kagihq introduced a fast ("Standard") #LLM for its translation service that seems to fail miserably if you try to translate single words for less common languages:
https://kagifeedback.org/d/9373-standard-translation-is-unusable-for-hungarian
My point is that doing a dictionary lookup for all words (~1mil for English) could be done on a disposable vape in no time with better results, incl. clear indication of lookup failures, so you can fall back to your GPUs when needed.
⬡-49016 
49016@mastodon.catgirl.cloud
https://gpg.fail IS ONLINE
TALK VOD IS ONLINE (preliminary recording, not yet edited) #39c3
Jonty Wareing
jonty@chaos.socialThe worst part of Christmas, where everyone is at #39c3 and I am not
buherator
buheratorhttps://devblogs.microsoft.com/oldnewthing/20251225-00/?p=111914
(I use Linux and X11, usually none of my string makes it to the clipboard)
SkelSec
skelsec@bird.makeupI was away for a while, dropping my current side-project here.
Password cracking in your browser. Think of it as a mini-@hashcat it uses WebGPU to perform the cracking.
NT/LM/DCC/DCC2/MD5 currently implemented with bruteforce/mask/wordlist/hybrid attacks.
https://webcrack.octopwn.com/
Royce Williams
tychotithonus@infosec.exchangeRE: https://infosec.exchange/@zak/115793005915790340
This is a metaphor about cybersecurity products.
buherator
buherator"The operation was successful, the patient died"
Ivan Krstić
radian@bird.makeup🔺This is the first talk I've given in 6 years – featuring formal verification of post-quantum cryptography, the evolution of the Secure Page Table Monitor, a view into Memory Integrity Enforcement, updates to Apple Security Bounty… and a personal note.
https://bird.makeup/users/hexacon_fr/statuses/2002020791865532704
buherator
buherator- Sometimes struct member names are not returned. Sometimes!
- The first struct member is at offset 94489263476241, but amazingly the second one is at 8.
Just in case you wonder why I drink...
Edit: that weird value is somewhat random too, so I suspect a memory leak
Filippo Valsorda
filippo@abyssdomain.expertAt the https://gpg.fail talk and omg #39c3
You can just put a \0 in the Hash: header and then newlines and inject text in a cleartext message.
Won’t even blame PGP here. C is unsafe at any speed.
gpg has not fixed it yet.
Joe Grand
joegrand@chaos.socialDisobedience in Helsinki coming soon! #Disobey2026 https://disobey.fi/2026/
CCC VOC
c3voc@chaos.socialWe're happy to announce that the first recordings are now available at https://media.ccc.de/c/39c3!
^ta
buherator
buheratorhttps://starlabs.sg/blog/2025/12-2025-reflection/
#fail