Posts
2970Following
697Followers
1544ahmethan
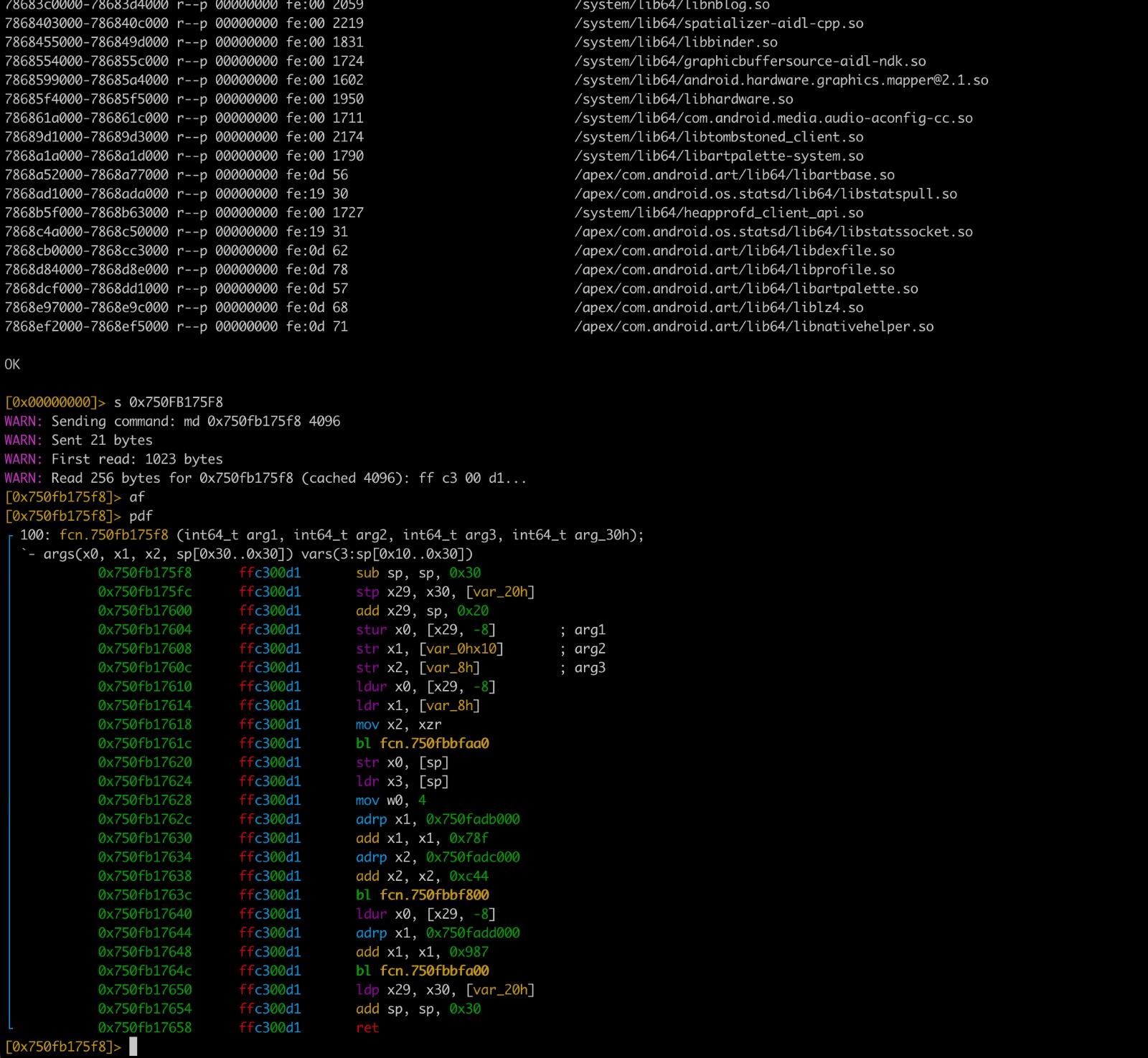
ahmethan@infosec.exchanger2renef - Renef IO Plugin for Radare2 released!
Github: https://github.com/ahmeth4n/r2renef
I built a small radare2 IO plugin to combine radare2’s powerful binary analysis features with Renef’s Android runtime instrumentation.
This allows you to use static analysis (disasm, analysis) together with runtime capabilities like hooking, memory and module operations in a single workflow, without constant context switching.
The project is still early, but already useful in daily Android reverse-engineering tasks.
Feedback and contributions are always welcome, especially from those working with radare2, Android, or low-level instrumentation👌
Socket
SocketSecurity@fosstodon.org🚀 Big News! Docker Hardened Images are now free! We’re partnering with @Docker to bundle Socket Firewall into supported images, adding supply chain protection during dependency installs and builds.
Details → https://socket.dev/blog/socket-firewall-now-available-in-docker-hardened-images
buherator
buheratorhttps://dozheiny.net/2025/12/17/be-careful-about-your-data-on-the-internet.html
#ReverseEngineering an Iranian dating app
James Forshaw 
tiraniddo@infosec.exchange
Project Zero have finally got around to updating the blog to something less blogger-esc, check it out at https://projectzero.google. To coincide with this momentous occasion I dug out the draft of my blog post about Windows Object Manager performance which became the basis of my article in PoC||GTFO #13 and updated it to see if it still worked in Windows 11. You can read it at https://projectzero.google/2025/12/windows-exploitation-techniques.html
Taggart
mttaggart@infosec.exchangeWowzers, another perfect 10 from Cisco on Secure Email Gateway, Secure Mail, and Web Manager. This one has:
- RCE
- No patch
- No workaround
- No public IoCs
This attack campaign affects Cisco Secure Email Gateway, both physical and virtual, and Cisco Secure Email and Web Manager appliances, both physical and virtual, when both of the following conditions are met:
- The appliance is configured with the Spam Quarantine feature.
- The Spam Quarantine feature is exposed to and reachable from the internet.
Recommendation is to reimage to a known-good config. Whatever that is, without indicators.
Good luck I guess??
mahaloz
mahaloz@infosec.exchangeDo LLMs actually help hackers reverse engineer and understand the software they want to exploit?
We ran the first fine-grained human study of LLMs + reverse engineering.
To appear at NDSS 2026.
Interested? Some quick findings in 🧵👇
Paper: https://www.zionbasque.com/files/papers/dec-synergy-study.pdf
Joseph Cox
josephcox@infosec.exchangeThis is a wild hack. a16z gave a million dollars to startup called Doublespeed. They use a phone farm to flood social media with AI generated influencers and ads. A hacker remotely broke into the phone farm, unmasking the AI influencers/fake accounts, gave us the data https://www.404media.co/hack-reveals-the-a16z-backed-phone-farm-flooding-tiktok-with-ai-influencers/
buherator
buheratorWladimir Palant
WPalant@infosec.exchangeI’m having some fun with VStarcam firmware, so why shouldn’t you? After downloading hundreds of their firmware updates I decided to document all these numerous proprietary formats. This even included figuring out a proprietary compression algorithm (not the one I asked about here a few days ago, that one is still a mystery).
https://palant.info/2025/12/15/unpacking-vstarcam-firmware-for-fun-and-profit/
buherator
buheratorWladimir Palant
WPalant@infosec.exchangeIs there actually a name for the development model where you don’t have a single codebase for all your clients/device model/whatever but rather fork the codebase whenever a new client/device model/whatever comes along? You then continue your development in the new codebase and occasionally cherry pick some of the improvements for the older variants of your codebase (of which you eventually accumulate dozens if not hundreds).
Joxean Koret (@matalaz)
joxean@mastodon.socialGames That Weren't: How can you possibly squeeze a 32-bit PlayStation CD ROM game into a small Game Boy Color Cartridge? Well, HotGen would attempt to do just that with a conversion of Resident Evil in mid-1999 and to make it as close as possible with similar 3D perspectives using scaled sprites.
buherator
buheratorhttps://github.com/v-p-b/sugardocy/blob/main/sugar-template.html
buherator
buheratorhttps://sugar-css.com/